Cybercriminals actively recruiting and paying people to support their malicious activities
Foreword
Three months have passed since we published the Avast Q2/2022 Threat Report and here we are again reviewing the cyber threat landscape via the Avast telemetry and Avast’s experts’ insights. I’m not sure about you, but Q3 passed very quickly for me, probably thanks to the summer holidays here in Europe.
Threat reports are often scary and intimidating, as they describe malware outbreaks and dramatic increases in attacks of various threat types. This report is different, though. We observed a decline in a vast majority of malware types in Q3/2022, which is positive. The common belief in the security industry is that malware authors take off over the summer, causing a decline in malicious activity. The drop in attacks is also caused by users spending more time offline, reducing the attack surface. The war in Ukraine and the recent mobilization of forces in Russia likely also played a part in the decline. It will be interesting to see how this trend will continue in the next quarter.
Despite fewer attacks in Q3/2022, this report still contains many highlights. Raccoon Stealer’s activity is like a rollercoaster ride, and it went rampant this quarter, spreading via cracked software. The other stealers, Formbook and AgentTesla, reminded us that Office macros are mostly dead, for now. Malware authors are instead abusing ISO and IMG formats on Windows. Coniminers are still one of the top malware types, and 70% of their attacks are deployed using web coinminers on infected pages. We’ve also seen a new botnet called Pitraix, which is, fortunately, not prevalent, at least for now. Unfortunately, we cannot say the same about the Warzone RAT, which significantly boosted its presence in various countries such as Hungary and New Zealand. Furthermore, adware on Windows significantly grew in Central, South, and Eastern Europe, and mobile adware is still the top threat targeting Android users.
In addition to the malware activity we observed, this report also describes how cybergangs are actively recruiting and paying people to support their criminal activities. The LockBit group was very active this quarter, beginning a bug bounty program and even offering $1,000 to anyone tattooing their logo onto their body. The NoName057(16) hacker group, desperate to continue DDoSing governments and businesses supporting Ukraine, started paying people to download their program and DDoS for them after their Bobik botnet C2 server was taken down (coincidentally after we published a blog post about them).
Keep safe and happy reading!
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into two main sections – Desktop-related threats, where we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems, and Mobile-related threats, where we describe the attacks focusing on the Android and iOS operating systems.
Furthermore, we use the term risk ratio in this report to describe the severity of particular threats, calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
We changed the threat labeling algorithm we use for our Threat Reports to ensure our data is even more accurate. As a result, the numbers appearing in this Threat Report should not be compared with those from our previous reports. We recomputed statistics from previous quarters to provide quarter-over-quarter comparisons in this Threat Report.
Desktop-Related Threats
Advanced Persistent Threats (APTs)
Among other threat actor groups, we continue to track Chinese threat actors, as well as a few groups in the Southeast Asia region and a Russian-speaking threat group. We gained new insights into their activities and campaigns, but their operations retain a similar modus operandi and targets. We continuously share our insights at cybersecurity conferences.
We recently presented our research on Operation Dragon Castling at Virus Bulletin 2022. This operation was facilitated by CVE-2022-24934, a zero-day vulnerability in WPS Office that enabled concealing execution of malware via the office suite’s update mechanism.
At the beginning of December, we will present our research on a huge operation in Southeast Asia in a talk titled "Hitching a ride with Mustang Panda" at the AVAR conference in December 2022. We presume a Chinese-speaking group called Mustang Panda is responsible for the operation due to the target selection and the toolset used.
Chinese-speaking Groups
LuckyMouse, a well-known Chinese-speaking threat group, known for targeting government agencies in Asia and the Middle East, attacked agencies in the United Arab Emirates, Taiwan, and the Philippines in Q3/2022. We found backdoors on infected machines, password stealers for Chrome, and open-source tools, like BadPotato, for privilege escalation. LuckyMouse uses a HyperBro backdoor loaded and decrypted by a sideloaded DLL. The attackers likely infected machines through a compromised server, where instead of the MiMi chat application, they inserted a backdoor. TrendMicro recently described LuckyMouse’s backdoor infection vector and the post-exploitation tools.
Southeast Asian Actors
At the beginning of August, researchers from Morphisec released a blog post describing changes in the yty malware framework, a well-known tool used by the Donot Team (also known as APT-C-35). Office documents containing malicious macros or a combination of RTF injection and the Microsoft Equation editor (CVE-2017-1182) vulnerability usually deliver the next stage to victims.
Our telemetry shows the group was most active in Pakistan, where we discovered DLL modules from yty’s framework on several infected machines in our user base. Malicious documents with the `.inp` extension are the source of infection. The infected victims installed outdated versions of Inpage software, a word processor for Urdu and Arabic languages widely used in the region. We believe the attackers are leveraging old known vulnerabilities in the Inpage software, as described by Palo Alto Networks. We assume the victims work for governmental institutions, based on the documents’ metadata and filenames.
Transparent Tribe, or APT36, is another group from the region we are tracking. They continue to attack victims in India and Afghanistan, as other researchers also reported. The group is believed to originate from Pakistan and focuses its activities on neighboring countries. The group infects victim PCs using spear-phishing and Office documents with malicious VBA macros dropping embedded obfuscated .NET-based executables into arbitrary paths in the `%ALLUSERSPROFILE%` directory. We identified that the executables belong to the CrimsonRAT strain, Transparent Tribe‘s custom malware used to access infected networks. The activity is analogous to what was described in greater detail by researchers from Cisco Talos and Fortinet.
Russian Actors
The Gamaredon group continues to be very active and tightly focused on Ukraine in Q3/2022, broadening its attacks on military and government institutions motivated by the Russian aggression in Ukraine. The overall number of attacks and general modus operandi has not changed since last quarter. Still, they introduced a few new tools to their toolset, including file exfiltration tools, various droppers, and new ways of distributing payloads and IPs of C&C servers. Our telemetry also shows the group targeted foreign embassies in Ukraine.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Jan Holman, Malware Researcher
Tomáš Zvara, Malware Researcher
Adware
Desktop adware rapidly accelerated at the end of Q3/2022. In the beginning and middle of the observed quarter, adware activity stabilized with a slight downward trend, as the graph below illustrates.
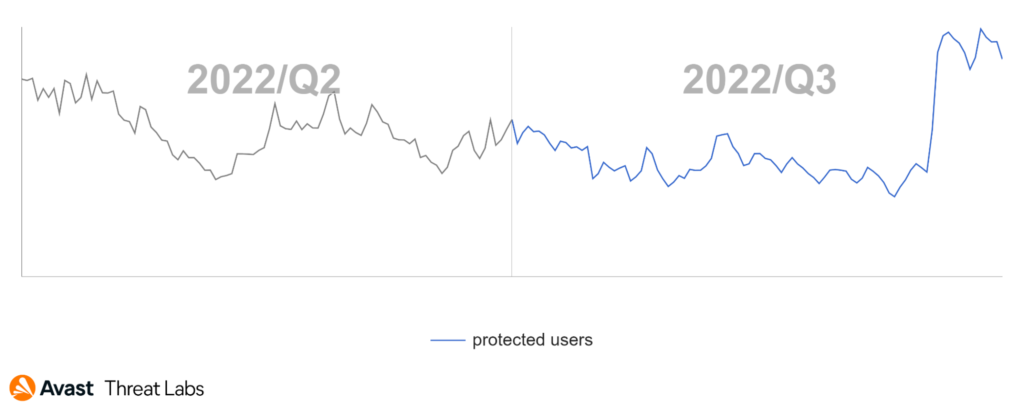
The peak at the end of Q3/2022 began on September 16, 2022. Adware activity significantly grew predominantly in Central, South, and Eastern Europe:
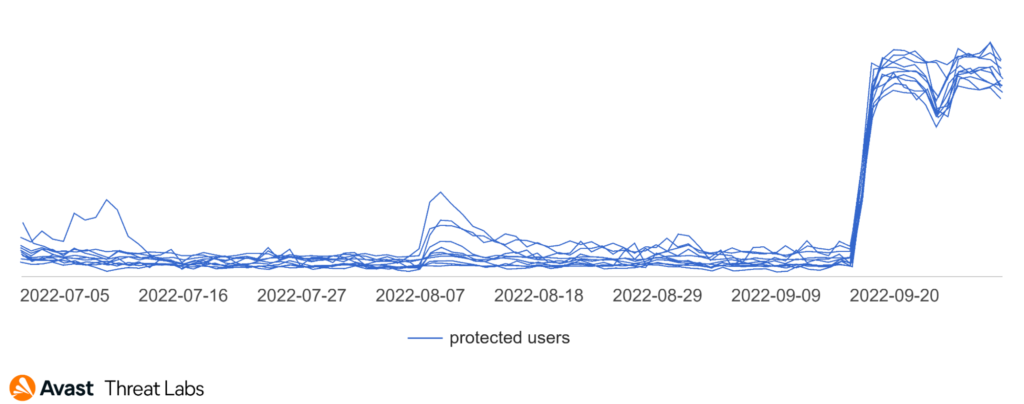
We identified an adware variant responsible for the peak in September. The adware called DealPly is a Chrome extension that modifies a new page design in the Chrome browser. The extension is called Internal Chromium Extension and has permission to replace newly opened tabs, read browsing history, change bookmarks, and manage apps, extensions, and themes in the browser.
The new tab can look similar to the screenshot below. The extension modifies advertising shortcuts and sends statistical and search information to attackers.

DealPly’s extension is not usually downloaded by users directly, but other malware installs it without the user’s knowledge and ensures its persistence, so they cannot remove the extension manually.
The adware we detected in the beginning and middle of Q3/2022 was adware on suspicious websites. This type of adware waits for a user to click on an arbitrary hyperlink and replaces the original link with one that redirects the user to advertising websites.
Here’s a list of ad servers:
- deshaici[.]net
- gapscult[.]com
- informeresapp[.]com
- mobile5shop[.]com
- naigristoa[.]com
- saumeechoa[.]com
- go.ad2upapp[.]com
The suspicious websites lure victims by offering prizes or free services; see the examples below. However, the redirections lead to websites with malicious content or pages that want contact or login information.
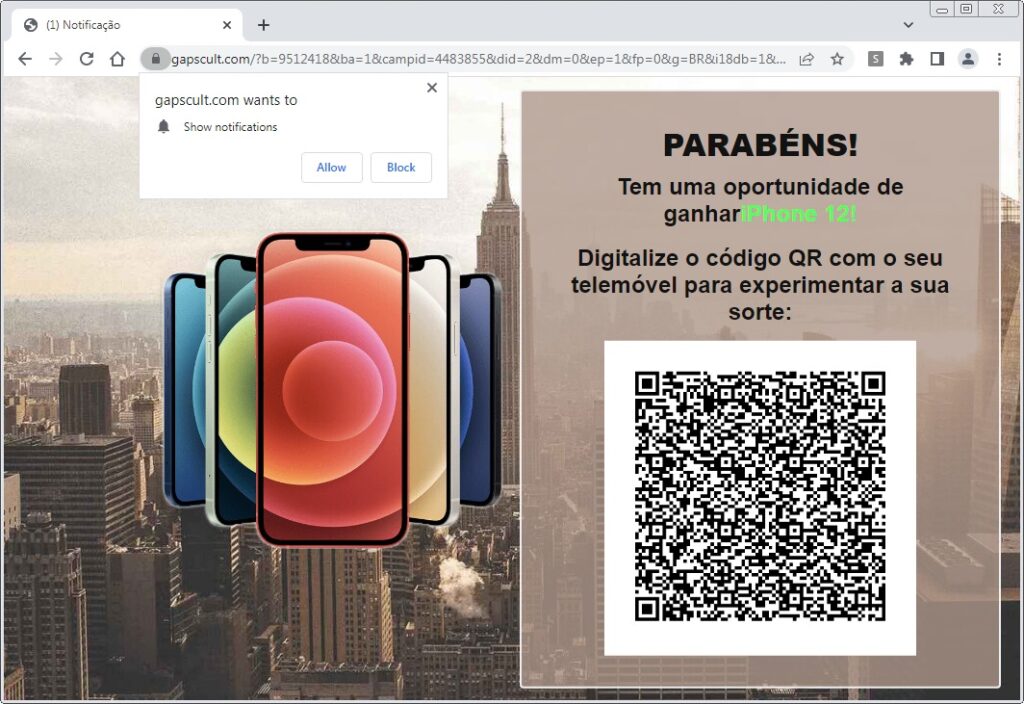
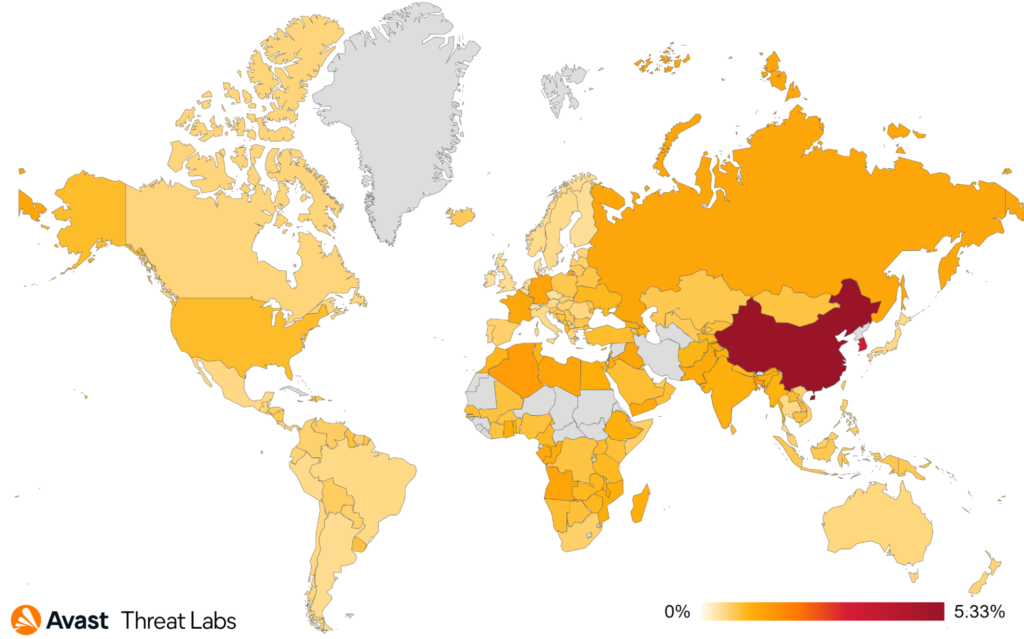
We monitored a noticeable decrease in the adware risk ratio for users in Brazil, the United States, the United Kingdom, Italy, Austria, and Switzerland. On the other hand, there was an increase in the risk ratio for users in Poland, Croatia, Latvia, and Hungary; see the map below.
In Q3/2022, more than 40% of the adware we saw was from various adware families. However, the clearly identified strains of adware are: DealPly, RelevantKnowledge, DownloadAssistant, and CloverPlus.
The most common adware threats for MacOS were: Bundlore, Pirrit, Spigot, Adload, and MaxOfferDeal.
Martin Chlumecký, Malware Researcher
Bots
The botnet landscape was rather calm in comparison to the previous turbulent quarters – no miraculous revivals or medialized takedowns. Nevertheless, botnet activity remained consistent, consistently dangerous. With Ukraine defending itself from Russian aggression and the Western World providing support to Ukraine, some Russian groups are utilizing their resources to attack organizations and infrastructure in Europe. There are also several other entrenched botnets and spambots plaguing our lives with their existence (and spam).
In our Q2/2022 Threat Report, we noted botnets experimenting with new formats of malicious attachments, such as ISO or IMG files. While these formats have some limitations on who can actually open them, based on the version of the used operating system, they are still gaining popularity in spite of the fact that the original motivation for their usage is no longer valid.
The pro-Russian group NoName057(16) remains very active. Their DDoS botnet Bobik is still attacking organizations in countries voicing their support for Ukraine or imposing sanctions on Russia. Their targets include both private institutions, such as news agencies or banks, and government institutions including courts, parliament, and police. Their attacks are retaliatory. The sites they target change depending on current events. For example, the group attacked sites belonging to the Finnish government after Finland announced their intention to join NATO in August. The group’s success rate (the number of sites they manage to take down vs. the number of sites they target) is 40%, based on our observations. Moreover, approximately 20% of the attacks they claim to be responsible for cannot be accounted for in their configuration files.
The main Bobik C2 server was taken down, after we published our blog post about NoName057(16), and the botnet stopped working. On August 15, 2022, the group announced they were recruiting for a new project, presumably to continue their DDoS attacks. They later opened a new group dedicated to their DDOSIA project, as reported by Radware. As of late-October, the Telegram group had 777 members. The project allows anyone to download a binary through which they can be identified and carry out DDoS attacks and in return, be awarded cryptocurrencies from the group. We have been monitoring DDOSIA’s configurations since August 1, 2022. The configuration file is updated four times a day, on average.
A new botnet called Pitraix is gaining a bit of traction on hacking fora. The botnet source code was originally hosted on Github and written in Go. Go has become a popular choice for smaller projects lately. For instance, Black Lotus Labs recently described another newish botnet written in Go. The botnet has P2P architecture relying on TOR for its communication. Rather unusual, the project was not framed as a security tool nor for educational purposes as is usual for similar projects.
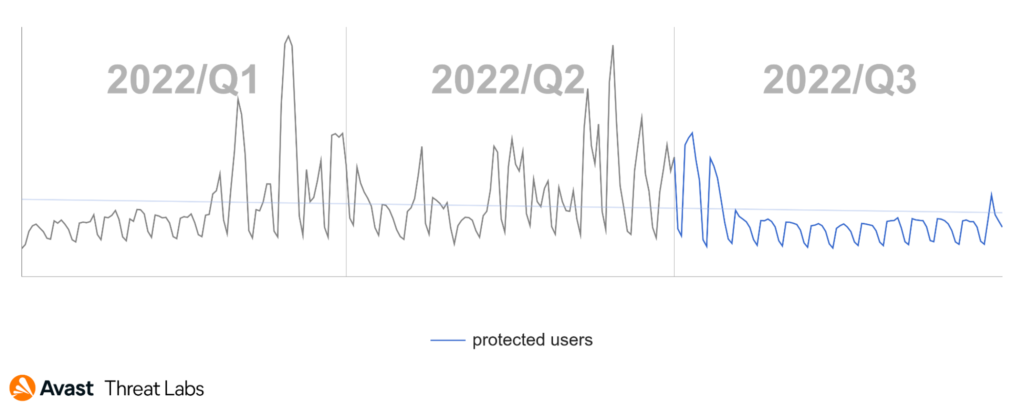
Overall, the botnet risk ratio is significantly lower than in the previous quarter, slowly getting back to the pre-war situation. We noticed a significant decline in Emotet’s activity, and a similar trend holds true for Tofsee. The only considerable outlier is MyKings. MyKings’ activity soared, with Ursnif trailing behind. Other botnet activity only slightly increased.
Currently, our data indicates that the following botnets (and their variants) are the most active in their recruitment:
- Phorpiex
- Emotet
- Tofsee
- MyloBot
- Nitol
- Dorkbot
- MyKings
- Ursnif
- Amadey
Adolf Středa, Malware Researcher
Coinminers
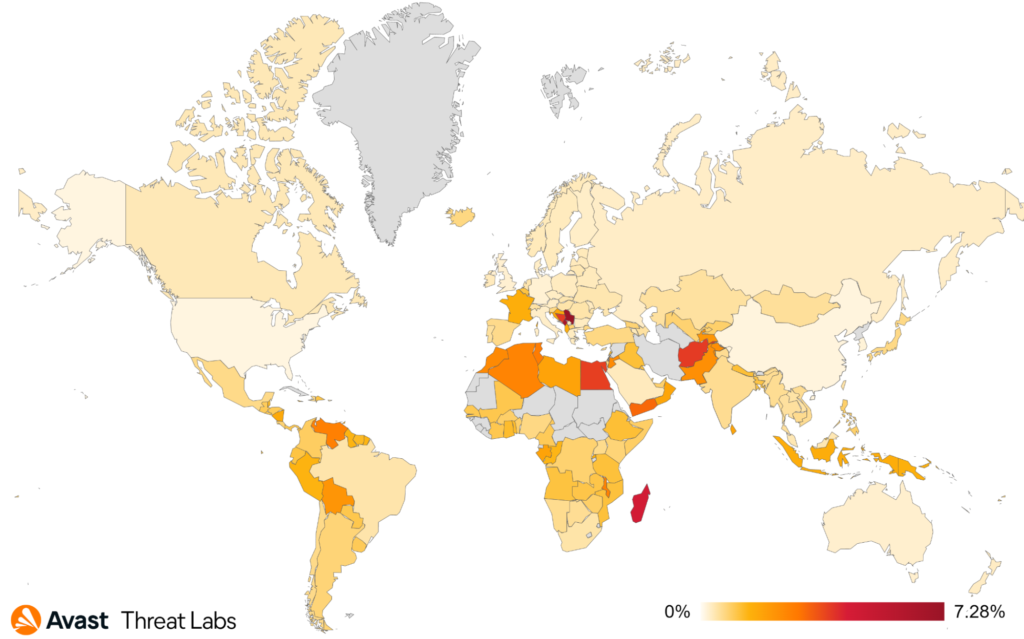
The value of cryptocurrencies is stagnating at long-time lows, but coinminers are still one of the most prevalent malware types we block in the wild. The number of coinminers we protected our users from in Q3/2022 decreased slightly (-4%).
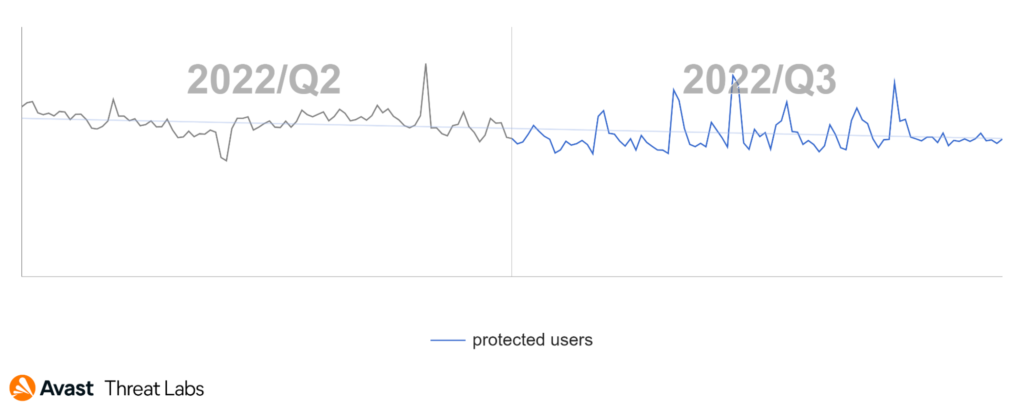
Users in Serbia were most at risk of encountering coinminers in Q3/2022, with a 7.28% risk ratio. The risk ratio for users in Madagascar encountering a coinminer was 4.55%, up slightly compared to the previous quarter. Users in Madagascar were among those most at risk of encountering coinminers. We also detected an increase in coinminer activity in Montenegro (6.59% risk ratio), as well as in Egypt where the risk ratio rose to 3.81% (+32% QoQ).
Web coinminers continue to lead, gaining even more market share in Q3/2022. Web coinminer activity increased by 6% and they now hold 70% of the coinmining market share. We observed an increase in KingMfcMiner detections and protected 45% more users from the miner in Q3/2022 compared to Q2/2022. CoinHelper’s activity also increased its market share by 9%.
XMRig remains the leading coinmining executable. However, XMRig activity dropped by 11%. According to our telemetry, XMRig holds 15% of the coinminer market share.
The most common coinminers in Q3/2022 were:
- Web miners (various strains)
- XMRig
- CoinBitMiner
- VMiner
- CoinHelper
- NeoScrypt
- FakeKMSminer
Jan Rubín, Malware Researcher
Information Stealers
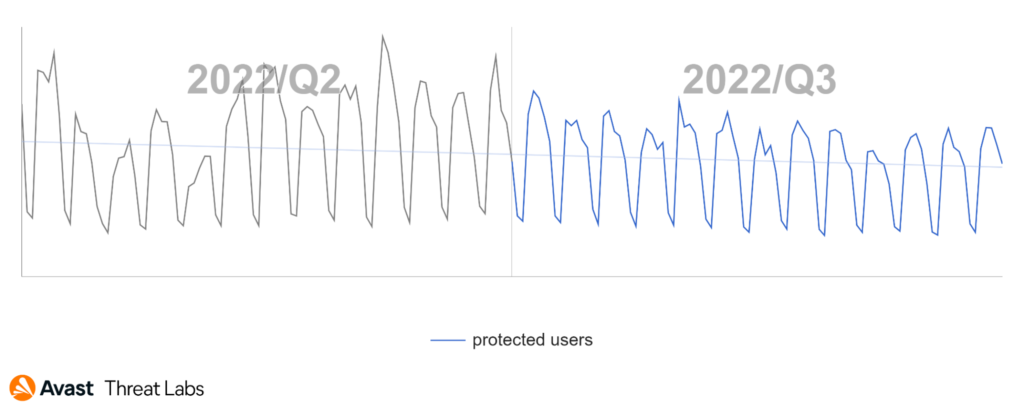
Raccoon Stealer activity went rampant in Q3/2022 following the malware’s announced return, which we reported in our previous report. We protected +370% more users from Raccoon Stealer in Q3/2022 vs. Q2/2022. Despite Raccoon Stealer’s growth, overall information stealer activity declined by 14% in Q3/2022.
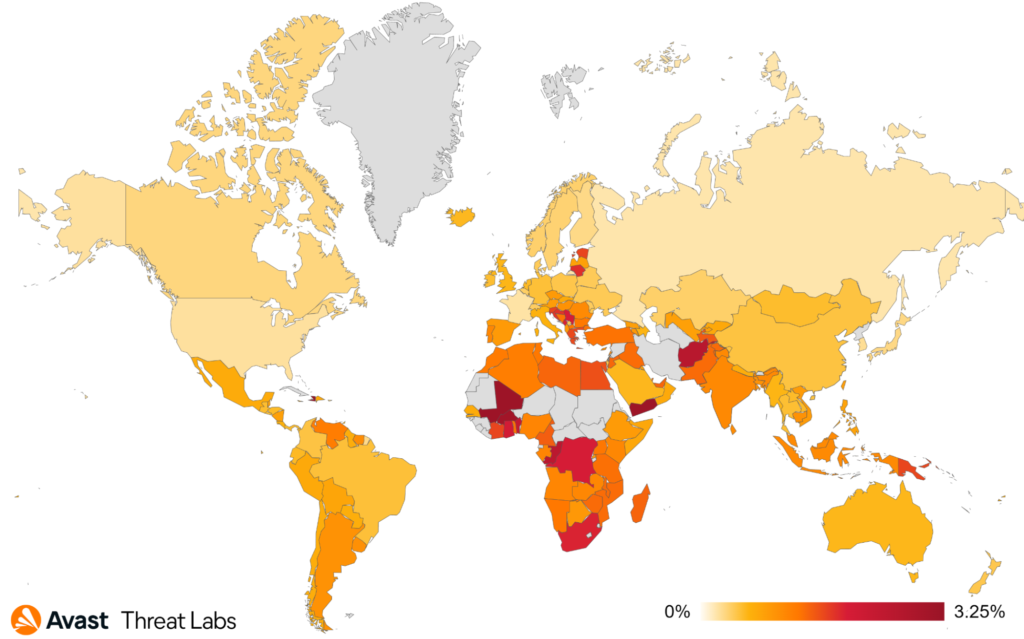
The countries where users are most at risk of encountering information stealers remained the same, for the most part, except for some countries in Africa, as can be seen in the heatmap below. Users in Mali encountered more information stealers (+14% risk ratio) than in Q2/2022, as did users in Yemen (+16% risk ratio) and Congo (+11% risk ratio). Further notable changes occurred in Brazil, where the information stealer risk ratio dropped by 24%. Avast’s presence in Brazil, where we saw a 28% drop in the number of users we protected from information stealers, is significant and is part of the reason we observed an overall decrease in information stealer numbers.
FormBook continues to be the most active information stealer in Q3/2022, further increasing its market share by 8%, gaining 26% of the overall information stealer market share. The market share held by other top information stealer strains declined in Q3/2022: Lokibot (-35%), RedLine Stealer (-17%), and AgentTesla (-4%). Raccoon Stealer and SnakeKeylogger, on the other hand, significantly increased their market share by 450% and 53%, respectively.
The most common information stealers in Q3/2022 were:
- FormBook
- RedLine Stealer
- AgentTesla
- Lokibot
- Raccoon Stealer
- SnakeKeylogger
Raccoon Stealer Reaches New Heights
We protected significantly more users from the second version of Raccoon Stealer at the beginning of Q3/2022.
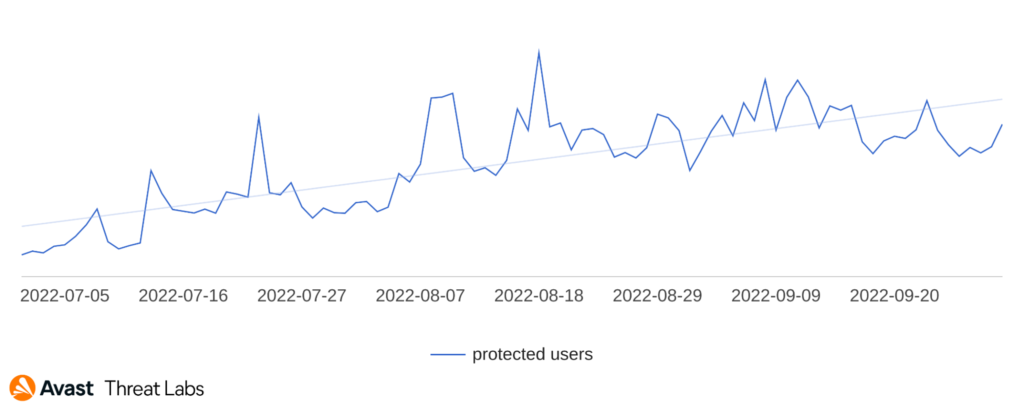
Raccoon Stealer mainly makes its way onto computers via “cracked” software. The archives through which Raccoon Stealer spreads promise cracked versions of software like Adobe Photoshop, Filmora Video Editor, and uTorrent Pro, but deliver Raccoon Stealer instead.
Raccoon Stealer not only steals data but is also capable of downloading and executing further malicious files, including miners and other stealers.
GuLoader Phishing Emails
We observed new phishing email campaigns rising in late August and September, mainly targeting users in Spain, the Czech Republic, Romania, and other countries. We protected over 26,000 users. The campaigns use ISO archive attachments containing new versions of GuLoader that drop AgentTesla or FormBook.

Discord Based Information Stealers Attacking Linux Users
We also observed some new malware families (i.ex. A new variant of Sshbru or ServerHijacker-B) written in Go programming language and abusing Discord Webhooks to leak information. These malware strains first identify or create an attack vector to hijack the system (i.ex. by enumerating the vulnerabilities in the LAN network of the victim, changing the password for root, and so on) and then get the public IP address which is leaked to the attackers via Discord Webhooks for a later intrusion. Computer access is likely to be sold on the black market.
Jan Rubín, Malware Researcher
Vladimir Martyanov, Malware Researcher
David Álvarez, Malware Analyst
Ransomware
Ransomware activity increased by nearly a quarter (+24%) in Q2/2022. In Q3/2022, ransomware activity stabilized, and slightly decreased. There were no peaks in ransomware activity in Q3/2022, as shown in the graph below, and is the reason for this decrease in risk ratio.
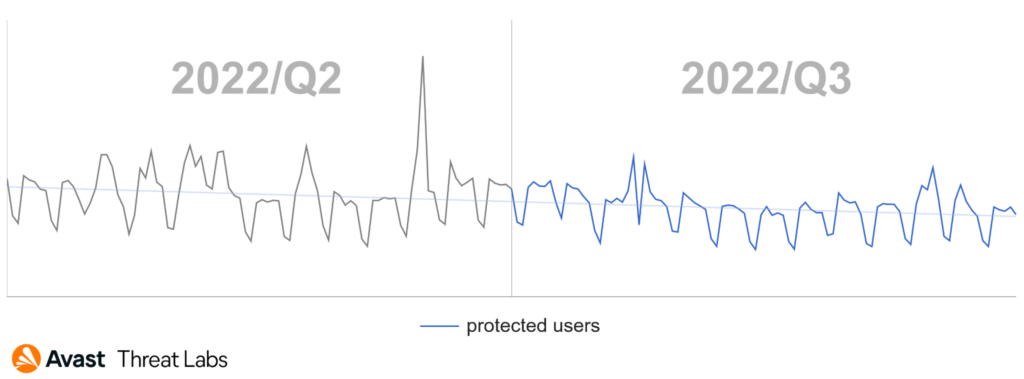
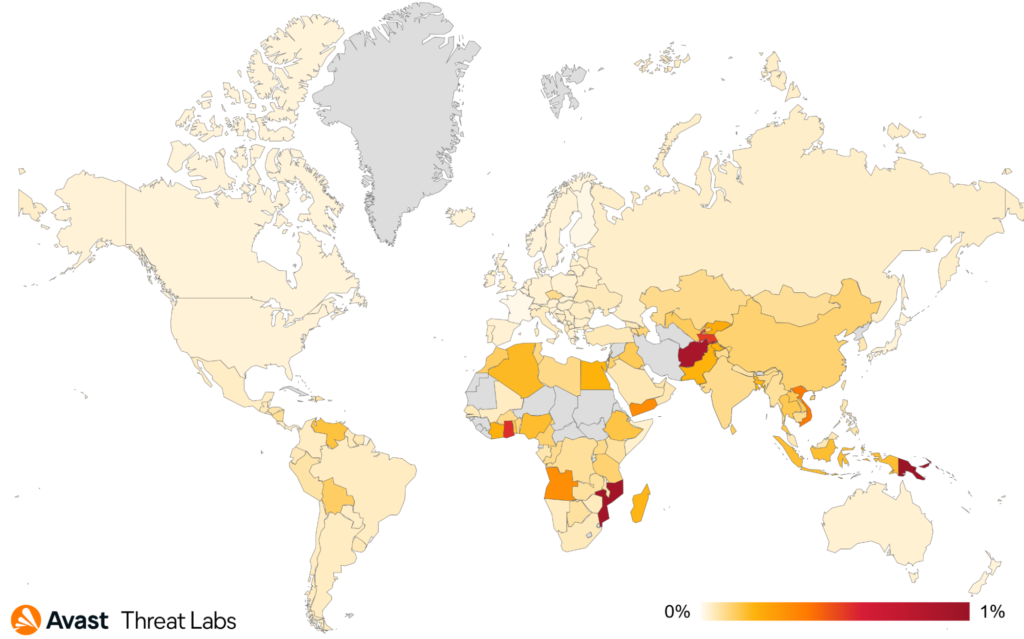
New countries are on top of the list of countries in which users are most at risk of encountering ransomware in Q3/2022:
- Papua New Guinea
- Mozambique
- Afghanistan
- Ghana
- Vietnam
The risk ratio for ransomware remained the same or slightly decreased in most countries in Q3/2022 (compared to the Q2/2022), but there are some outliers. The ransomware risk ratio increased by 70% in Vietnam, 49% in Thailand, 33% in Denmark, 16% in Canada, and 12% in Spain and Germany.
Here is a map of the ransomware risk ratio by country:
STOP, and WannaCry ransomware continued to be the most prevalent ransomware strains targeting our user base:
- STOP
- WannaCry
- Thanatos
- Sodinokibi / REvili (and its successors)
- Magniber
- LockerGoga
- Conti offsprings
- LockBit
Intermittent File Encryption
More and more ransomware strains now use partial (intermittent) methods of encryption (AtomSilo, Conti, BlackMatter, LockBit), to rapidly encrypt files. During a ransomware attack, file encryption needs to be quick to avoid user detection. The longer encryption takes, the higher the chances the potential victim notices the attack. A vigilant user may notice increased disk activity and check what’s going on. Also, the time needed to fully encrypt a collection of large files (such as movies or databases) may be significantly high.
CrySiS ransomware implemented partial encryption already in 2016, for example, but now more ransomware strains use complicated methods of partial encryption, and they are often configurable:
- Full Encryption: The file is fully encrypted. This is the “safest” method (from the point of view of the attackers) but can take a very long time, especially when encrypting movie files or large databases.
- Header only: The ransomware only encrypts the beginning of the file (up to a specified amount of bytes). This invalidates headers of most file types and renders them unrecognizable.
- Header + Tail: In addition to the file header, the header + tail method also encrypts part of the file end. This covers ZIP-like files (ZIP archives and MS Office files)
- Dot Pattern: The ransomware encrypts files by blocks – N bytes are encrypted, M bytes are left intact.
The methods described above can be combined, such as encryption of the file header and encryption of the rest using Dot Pattern encryption.
Multiple new ransomware strains emerged in Q3/2022, often attacking Windows, Linux, and ESXi servers. One of them was Luna ransomware, allegedly originating from Russia. Luna is written in the Rust programming language and can therefore be compiled for multiple platforms. Security researchers from Kaspersky confirmed all platform versions were built from the same source files.
Furthermore, ransomware authors continue innovating their ransoming techniques, and some recent attacks in the enterprise sector no longer involve file encryption, but data exfiltration followed by secure file deletion or corruption. In this scenario, companies depend on criminals to provide the original files after payment.
The LockBit Story
An interesting series of events involving the LockBit ransomware gang took place in Q3/2022. At the end of June, the gang behind the ransomware released a new version of the encryptor, code-named Black (because they copied it from the Black Matter ransomware gang). With this release, they announced a bug bounty program. Any bug or vulnerability reported to the gang will bring significant rewards. Reported bugs can be a weakness in the encryption process, a vulnerability in their website, or vulnerabilities in the TOX messenger or the TOR network. The juiciest reward (one million USD) is up for grabs and will go to the person who finds out the name of the affiliate boss.
In addition to the bounty program, the gang offered $1,000 USD to anyone who tattooed the LockBit logo on their body. The gang demanded video proof. According to photos posted to Twitter, some desperate people actually got the tattoo. We hope they got their reward and it was worth it…
The group paid a bounty reward of $50,000 to a person(s) who found a vulnerability in the encryption of large database files. They may pay more for bugs than others pay for RCE vulnerabilities, but they should consider paying their developers more. One of their developers got angry and leaked the builder of the cryptor. The package was briefly available on Github, but Github disabled it. The leaked package contained an RSA key generator and the builder of the ransomware+decryptor. With the leaked package, anyone could create their build of the ransomware and start a ransomware gang. Some seized the opportunity and did just that – the BlooDy ransomware gang, and TommyLeaks/School boys gang took the builder and made their own cryptors.
One of the LockBit gang’s victims is a security company called Entrust, which suffered a cyber attack on June 18, 2022. Shortly after the attack, the LockBit gang claimed they were behind the attack. Together with the ransomware attack, they also extorted Entrust’s internal data and threatened to leak it, if the company didn’t pay the ransom.
The leaked data (including legal documents, marketing spreadsheets, and accounting data) was published on the gang’s Tor sites. Nevertheless, the sites went offline shortly after due to a DDoS attack, believed to originate from Entrust. Entrust never confirmed they were behind the attack.
But the story didn’t end there. Following the (counter) attack, the LockBit gang announced they were back with new triple-extortion tactics – encryption, extortion, and DDosing. The group published a torrent with 342 GB of Entrust’s stolen data online. Furthermore, the LockBit gang announced they would strengthen their infrastructure to prevent future DDoS attacks.
This quarter was also the sixth anniversary of the NoMoreRansom initiative, which helps millions of victims of ransomware attacks. Avast is a partner and we recently added a decryptor for the MafiaWare666 ransomware.
Jakub Křoustek, Malware Research Director
Ladislav Zezula, Malware Researcher
Remote Access Trojans (RATs)
RAT activity, in most parts of the world, continues to decline, just like in previous quarters. In our Q2/2022 Threat Report, we speculated that RAT activity would continue to decline over the summer, and we were right.
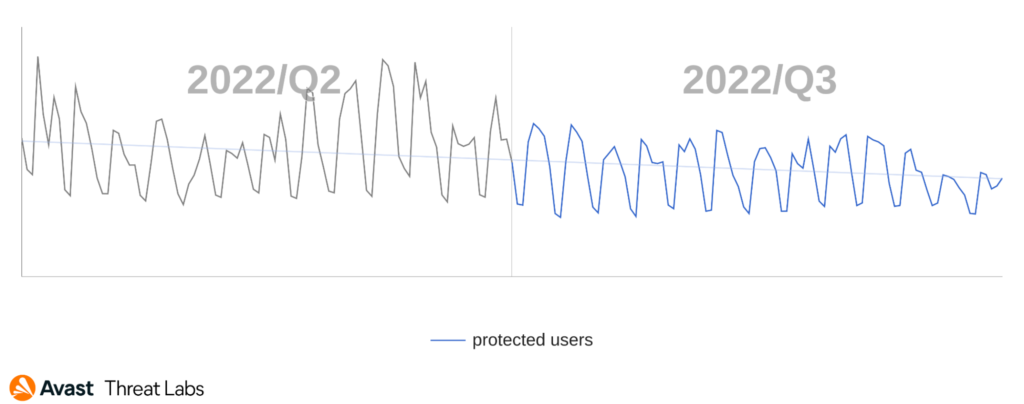
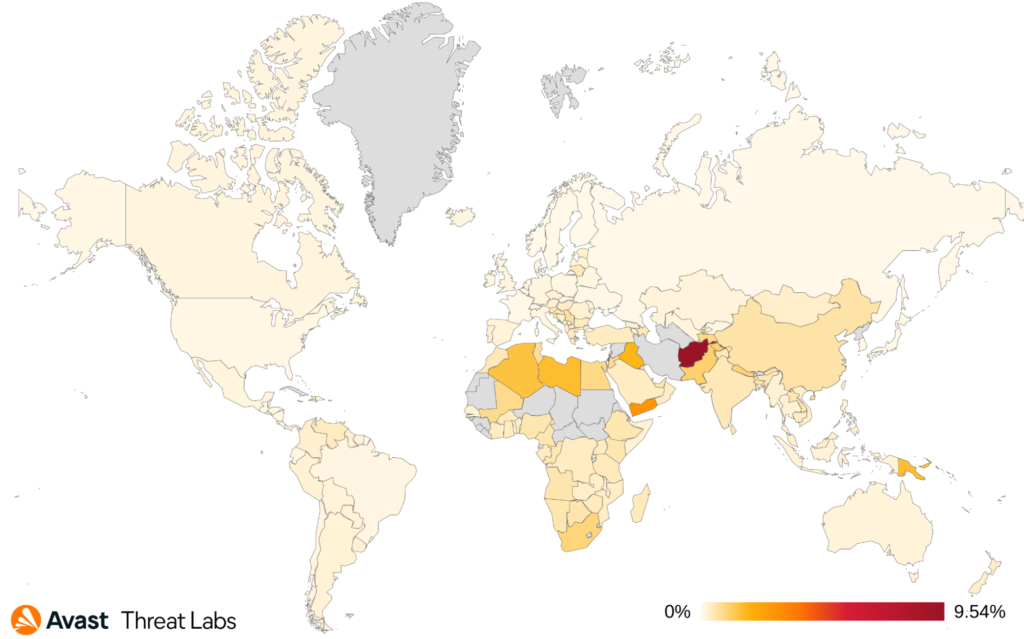
Users in Afghanistan, Yemen, and Iraq were most at risk of encountering a RAT in Q3/2022. RAT activity did however significantly increase in Hungary and New Zealand. The Warzone RAT is responsible for the increase in Hungary (+118%), the 59% increase in New Zealand is mostly due to Remcos and njRAT activity.
The countries where the risk ratio declined the most are: Spain (-36%), Canada (-31%), Czech Republic (-29%), and Slovakia (-28%). In our Q2/2022 Threat Report, we reported Japan as the country with the biggest increase in RAT attacks. In this quarter the number decreased, and Japan is among the safest countries together with Finland, France, and Switzerland.
The most prevalent RATs in our user base in Q3/2022 were:
- HWorm
- njRAT
- Warzone
- Remcos
- NanoCore
- AsyncRat
- NetWire
- QuasarRAT
- DarkComet
- Adwind
The top strains mostly stayed the same. As already mentioned, we saw a rather large campaign spreading Warzone in Hungary. A Remcos campaign also hit most of Asia, and the Netwire RAT targeted users in South Africa with a campaign.
Other RATs with a significant increase in prevalence in Q3/2022:
- LimeRAT (+85%)
- SpyNet (+41%)
- BoubedzRAT (+40%)
While these RATs are not as prevalent, their prevalence increased considerably in Q3/2022. LimeRAT was mostly active in Africa and South Asia, while SpyNet was active in Brazil and the BoubedzRAT in Columbia.
We published a blog post about a RAT called Backdoorit written in Go in Q3/2022. Backdoorit mainly focuses on stealing Minecraft related files, Visual Studio, and IntelliJ projects.
Several new RATs appeared or were discovered during Q3/2022. ApolloRAT is a new and interesting RAT because of its use of Nuitka to compile Python source to C source as reported by Cyble. The set of features is quite common in the domain of RATs with the exception of “Prank” commands such as >rickroll. It uses Discord for its C&C communication.
CodeRAT appeared in Q2/2022. In Q3/2022 the developer publicly shared the code on GitHub, after being confronted by security researchers from SafeBreach. CodeRAT’s main goal is to monitor its victims’ social media activity and what they do on local machines. It features approximately 50 commands interacting with various parts of the operating system. It can also deploy other malware. The communication methods are also interesting, CodeRAT makes use of Telegram groups or a USB flash drive.
WoodyRAT was active for at least a year before it was discovered by Malwarebytes. The attackers make use of the Follina vulnerability to spread their RAT. According to the analysis, the malware can extract data from the infected computer, run commands and code, including injecting to other processes.
The Lazarus APT group added a new tool to their arsenal, as reported by Cisco Talos. This tool is called MagicRAT. MagicRAT is a relatively simple tool that can launch additional payloads, run arbitrary commands and manipulate files on infected machines. What makes it stand out is its use of the Qt Framework. Since MagicRAT does not have a user interface, the Qt Framework is likely used to increase the complexity of the malware and to make analysis harder.
Last but not least, the developer and seller of Imminent Monitor RAT SaaS was arrested by the Australian Federal Police. The RAT allows operators to spy on their victims via their webcam and microphone, among other things. According to the report the RAT has been sold to more than 14,500 individuals across 128 countries.
Ondřej Mokoš, Malware Researcher
Rootkits
Rootkit activity declined in Q3/2022, as shown in the chart below.
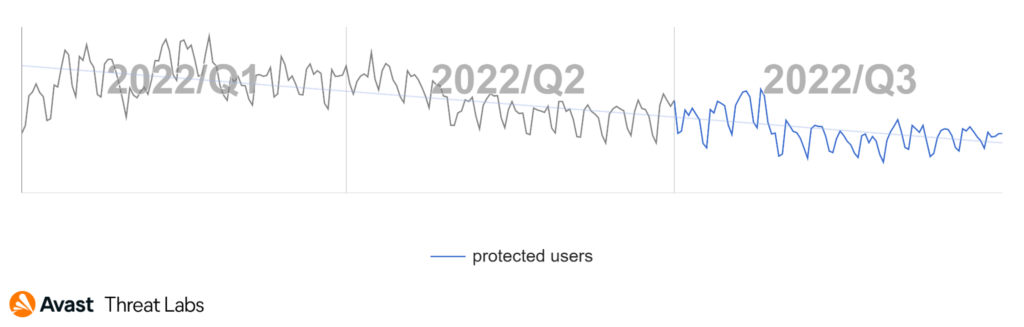
The distribution trend of rootkit strains continued as expected based on the previous two quarters (Q1/2022 and Q2/2022). The primary strain in Q3/2022 was the R77RK rootkit developed by the bytecode77 group. R77RK holds a 40% market share.
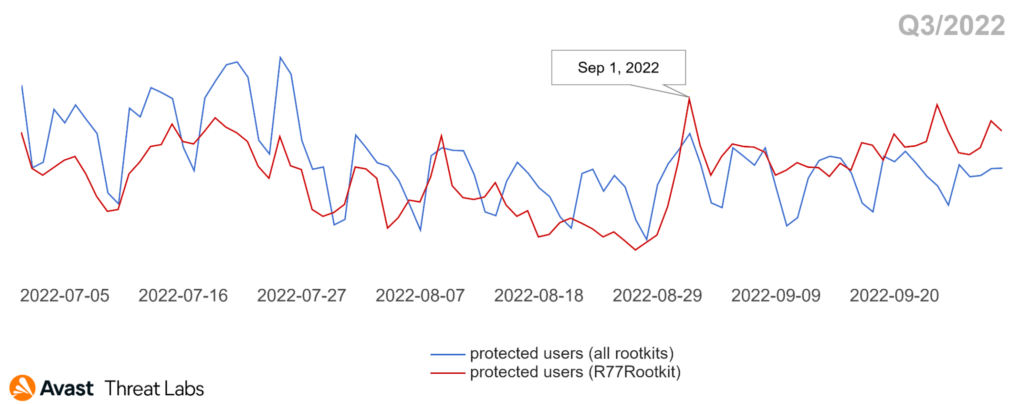
The chart above shows R77RK is a major rootkit, as its trend copies the overall rootkit trend in Q3/2022. The R77RK’s GitHub repository is still active. One notable correlation can be seen on September 1, 2022, when the authors’ released new functionality for R77RK. They implemented a rootkit activation via injection of a specific shell code. The release date corresponds with the peak; see the chart above.
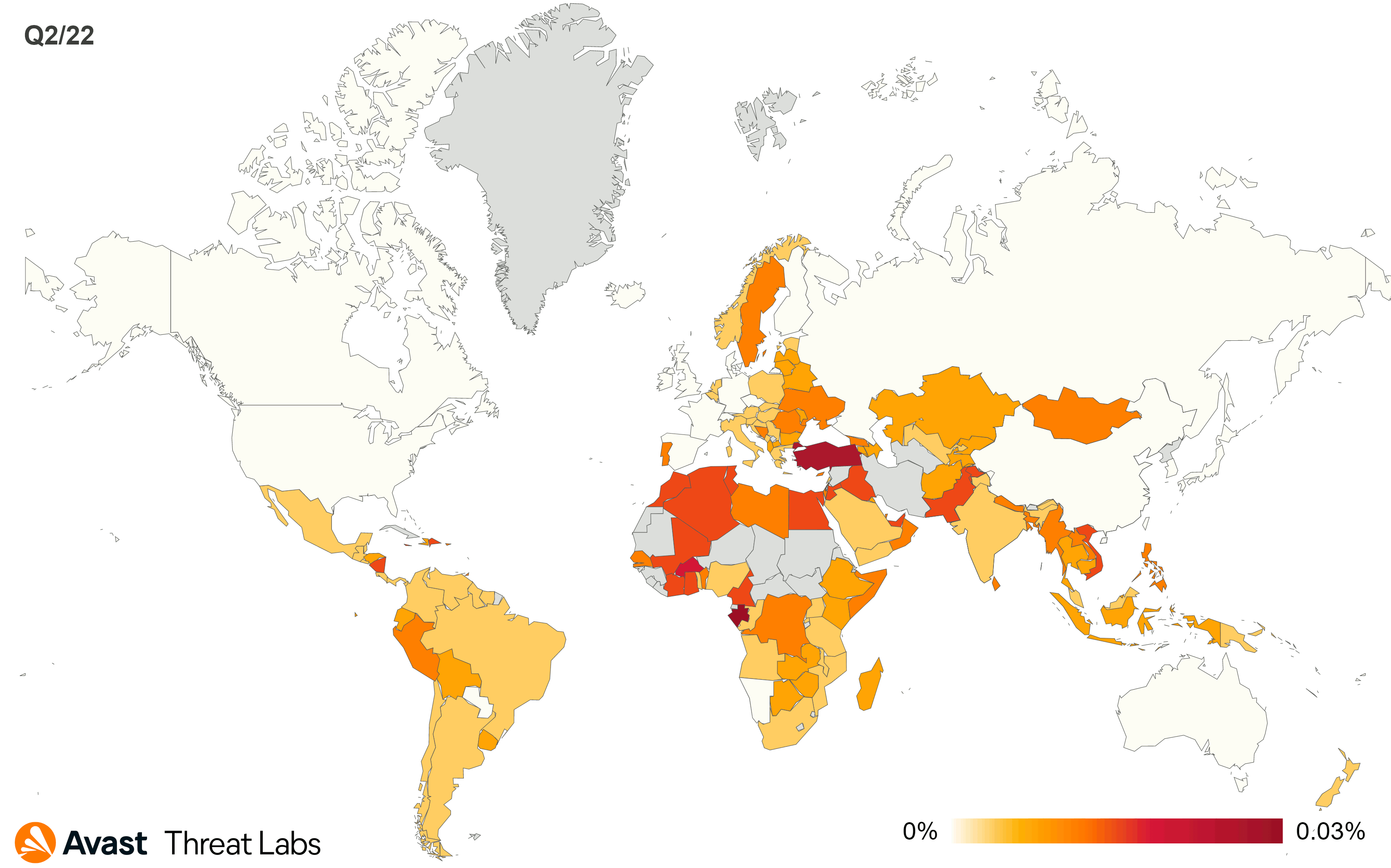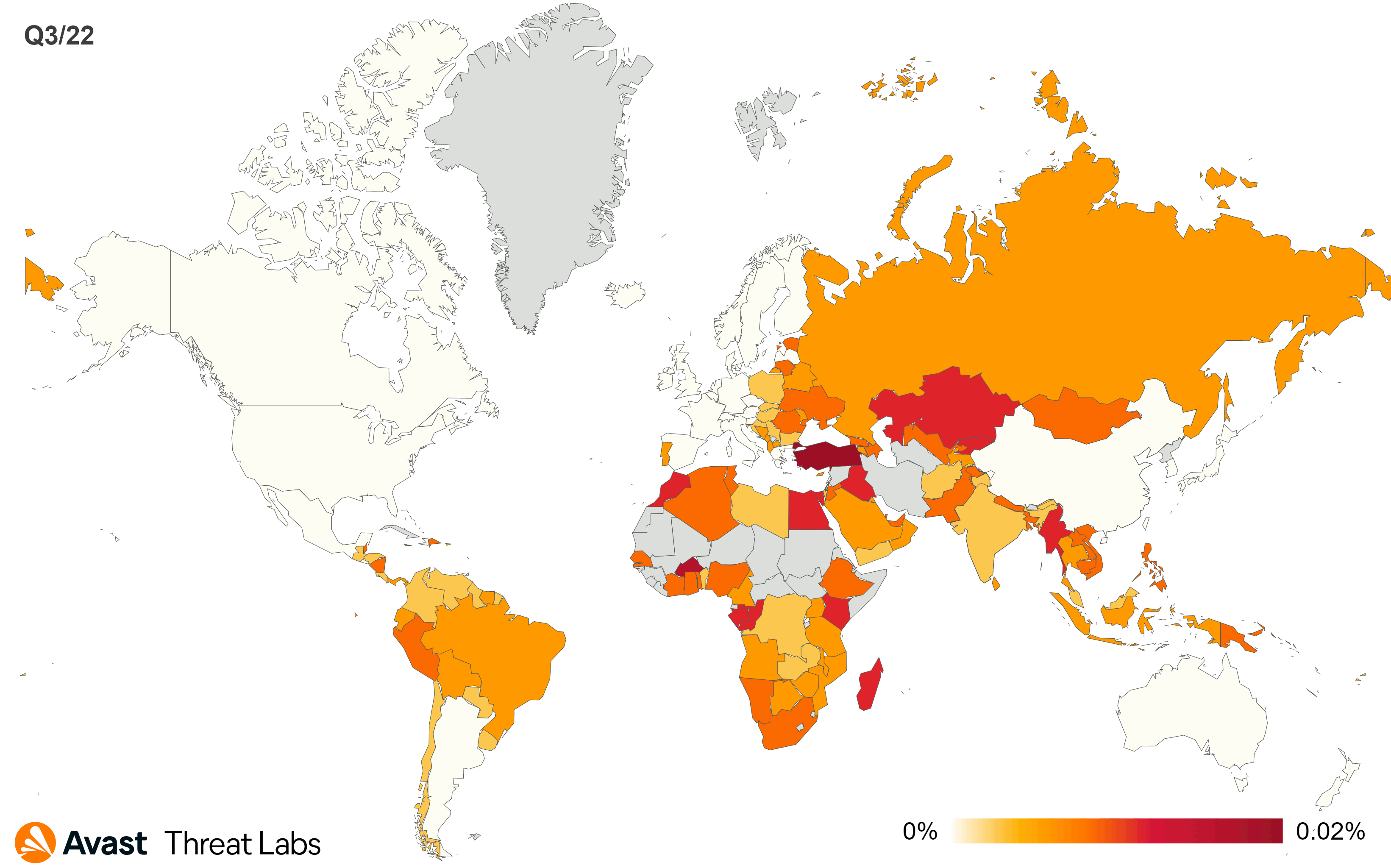
The map below animates R77RK’s activities moved to Eastern Europe and Northern Asia. On the other hand, Canada and the United States remain the least affected countries.
Another rootkit making rounds in Q3/2022 was Alureon, which steals credentials and credit card information by capturing the system’s network traffic. However, Alureon’s market share in the wild is only about 5%.
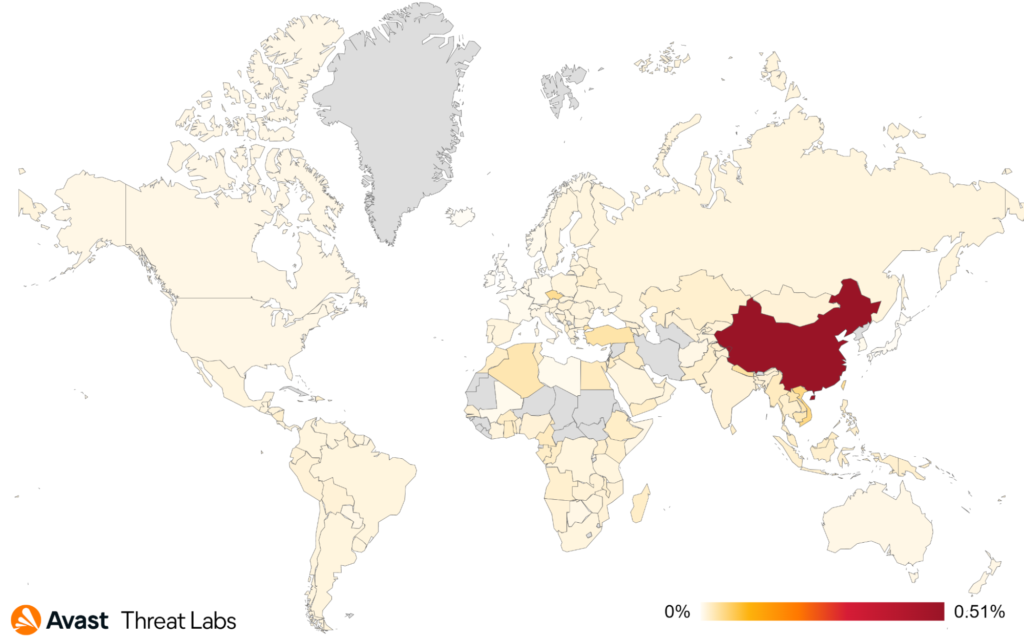
The global risk ratio of all rootkits is the same as in Q2/2022, and China remains the country in which users have the highest risk of encountering a rootkit. Q3/2022 confirmed that R77RK is still the most popular open-source rootkit in the wild.
Martin Chlumecký, Malware Researcher
Technical support scams
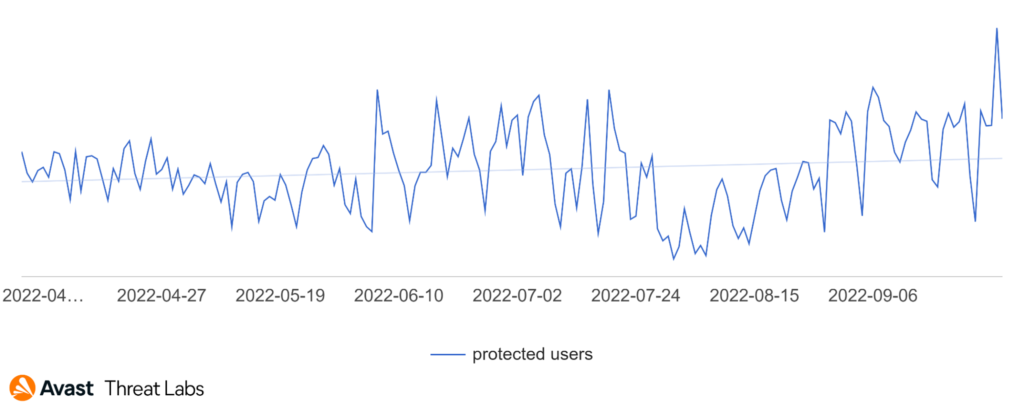
Technical support scams dipped at the end of July and the beginning of August. We assume the scammer community wanted to enjoy their summer break. This calm period lasted only a few weeks and ended at the end of August. Our September stats show more activity compared to July.
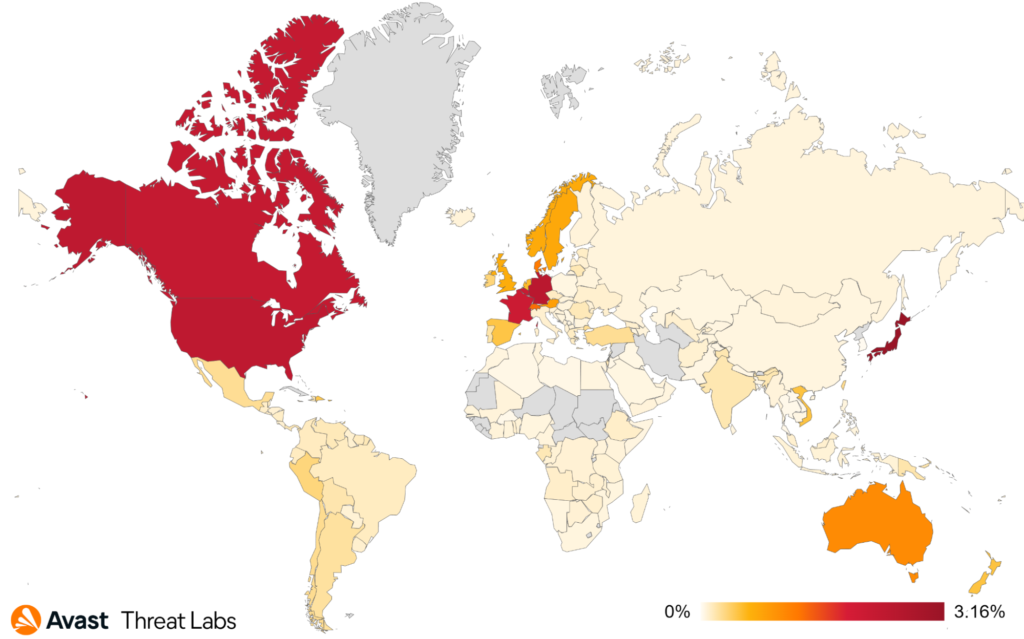
The top affected countries remained the same as in Q1 and Q2/2022. Users in Japan were targeted most, with a risk ratio of 3.16%, followed by Germany, the United States, and Canada, where activity slightly increased.
In Q3/2022, we registered hundreds of unique telephone numbers used in TSS scams. Here are the top 20 phone numbers:
| +1(888)-350-3496 | +1(888)-350-3495 |
| +1(833)-690-1082 | +1(833)-690-1085 |
| +1(833)-690-1079 | +1(844)-449-0455 |
| +1(888)-213-0940 | +1(866)-622-6692 |
| +1(844)-838-9290 | +1(833)-522-6669 |
| +1(817)-813-2707 | +1(844)-300-0063 |
| +1(844)-819-3386 | +1(866)-344-4412 |
| +1(877)-294-2845 | +1(888)-320-3547 |
| +1(805)-271-6246 | +1(888)-850-1320 |
| +1(877)-512-2485 | +1(844)-594-2674 |
Alexej Savčin, Malware Analyst
Vulnerabilities and Exploits
At the end of July, Microsoft published research about a private-sector offensive actor they refer to as KNOTWEED. KNOTWEED deployed a custom piece of malware, called Subzero, through a number of infection vectors, including zero-day exploits for Microsoft Windows and Adobe Reader. While the researchers were not successful in recovering the Adobe exploit, they found and patched CVE-2022-22047, a nasty bug used for privilege escalation.
Also noteworthy were new Microsoft Exchange zero-days (CVE-2022–41040 and CVE-2022–41082), discovered in the wild by GTSC Cyber Security. The exploits were strikingly similar to ProxyShell, an Exchange exploit discovered in 2021. As far as we know, the zero-days were only used in a limited number of targeted attacks, thus far.
Our own exploit research in Q3/2022 was mostly focused on Roshtyak, the backdoor payload associated with Raspberry Robin. Roshtyak uses CVE-2020-1054 and CVE-2021-1732, both Windows LPE exploits, to elevate privileges. Read our blog if you are interested in more details.
We also continued to track browser exploit kits, and we found PurpleFox, Rig, and Underminer to be active throughout the quarter.
The most frequently used exploit for MacOS was MacOS:CVE-2019-8900. A vulnerability in the Boot ROM of some Apple devices can be exploited by an unauthenticated local user to execute arbitrary code upon booting those devices.
Jan Vojtěšek, Malware Reseracher
Web skimming
In Q3/2022, the most common malicious domain used for web skimming attacks was hubberstore[.]com. Infected e-commerce websites, like sites selling event tickets, notebooks, and wine – mostly in Brazil, called code from the malicious domain. We protected nearly 20,000 users from the webskimmer in Q3/2022. In some cases, malicious code was present on an infected site, while in other cases, sites loaded additional code from hubberstore[.]com/app.js or a similar file name. The GET request exfiltrated payment details to the hubberstore malicious domain.
Here are some examples of what the GET requests look like:
hubberstore[.]com/<infected-webpage-name>.php?&drac=<user-data-base64-encoded>hubberstore[.]com/chk/apicielo.php?chave=<user-data-plaintext>hubberstore[.]com/v2/search?public_key=<user-data-base-64>
A Czech e-commerce site called bohemiadrogerie[.]cz was also infected. In this case, the attackers inserted their payment form on the website. The image below shows what the site looks like with and without the fake payment form. After entering payment details, customers receive an error message: The selected payment method is currently unavailable, please try again. The page is then reloaded and displayed without the payment form.
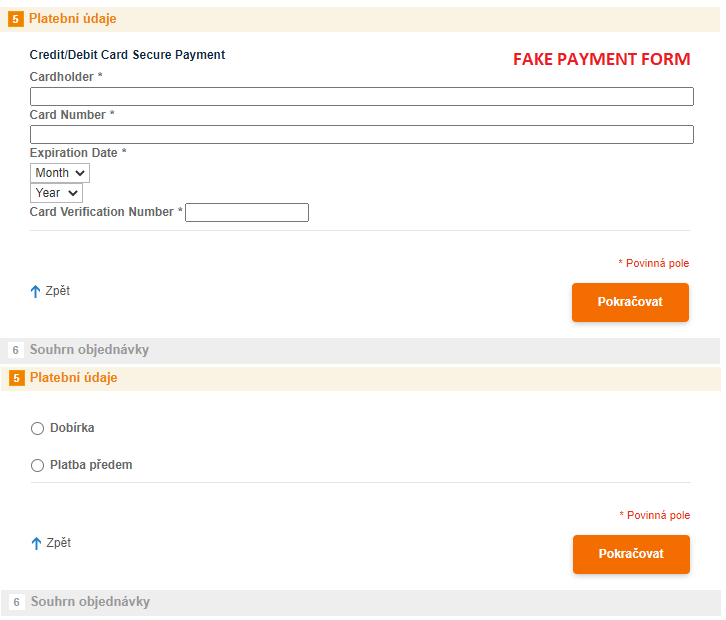
The skimmer on the Czech site uses a specific pattern ;function boms()in the malicious code. The same pattern was on the domain naturalfreshmall[.]com to host the malicious skimmer code, which we reported in our Q1/2022 Threat Report.
Attackers also exploited other legitimate sites, such as sites selling clothes, shoes, jewellery, furniture and medical supplies, to host their skimming code. Specifically, they used guyacave[.]fr, servair[.]com and stripefaster[.]com. Attackers exfiltrated payment details via the POST request to URLs like guyacave[.]fr/js/tiny_mce/themes/modern/themes.php and similar for the other domains. In some cases, the POST request was sent to the infected e-commerce site itself, indicating that the attacker has full access to the compromised sites. We protected nearly 17,000 users globally from this webskimmer.
In conclusion, there are still many long-term infected websites. Malicious code often remains on an infected website even after the exfiltration domain no longer exists.
Pavlína Kopecká, Malware Analyst
Mobile-Related Threats
Adware
Continuing the trend from previous years, adware was still the dominant threat facing mobile users in Q3/2022. This dominance brings intrusive advertisements, often paired with several stealth features. These combine to rake in money through advertisements for the adware creators while negatively impacting the user experience of mobile users worldwide.
HiddenAds and FakeAdBlockers continue to be the most prevalent adware families. They often use overlays to display advertisements to the user, even when using other applications on the phone. They may delay this activity by several days to confuse the user about the source of the intrusive advertisements. As per their name, HiddenAds can also hide their icon from the home screen, making it more difficult for mobile users to find the source of these frustrating ads.
Several new waves of HiddenAds made it onto the Google Play Store, such as Scylla, with added obfuscation but a similar set of features to previous HiddenAds strains. FakeAdBlockers continue to spread through fake games and applications downloaded from unofficial sources. Both families often come under the guise of games, camera filters, wallpaper apps, and keyboard themes, to name a few. It is advisable to avoid third-party stores and unknown websites when downloading applications, instead using Google’s Play Store while checking reviews and requested permissions.
Adware mostly affects mobile users in Asia, the Middle East, and South America. Brazil, India, Argentina, and Mexico again hold the top spots in the quarter, with increases in affected users in India and Mexico. The US holds fifth place, but we see a 25% decrease in affected users compared to last quarter. Adware is the most common mobile threat facing mobile phone users worldwide today.
Bankers
Cerberus/Alien keeps its top place in the banker sphere in Q3/2022, while Hydra and RoamingMantis finally surpass Flubot in terms of protected users. Following an eventful last quarter with the Flubot group disbanding by Europol, we finally saw a marked decrease of 50% in Flubot’s reach in Q3/2022. Considering Flubot dominated the banker sphere with its SMS phishing campaigns attacking users across Europe and the US, it is encouraging to see the positive effects of Europol’s actions.
Bankers still rely on established methods of infection and delivery, with SMS phishing being the favored approach. Several new droppers appeared on the Google Play Store, third-party stores, and forums, propagating known or slightly adjusted versions of existing bankers. Most recently, TrendMicro discovered the DawDropper dropper, which delivers a multitude of banker strains over the span of an extended period. We, therefore, believe it is a dropper service used by multiple banker strains, mitigating cost and effort for banker authors.
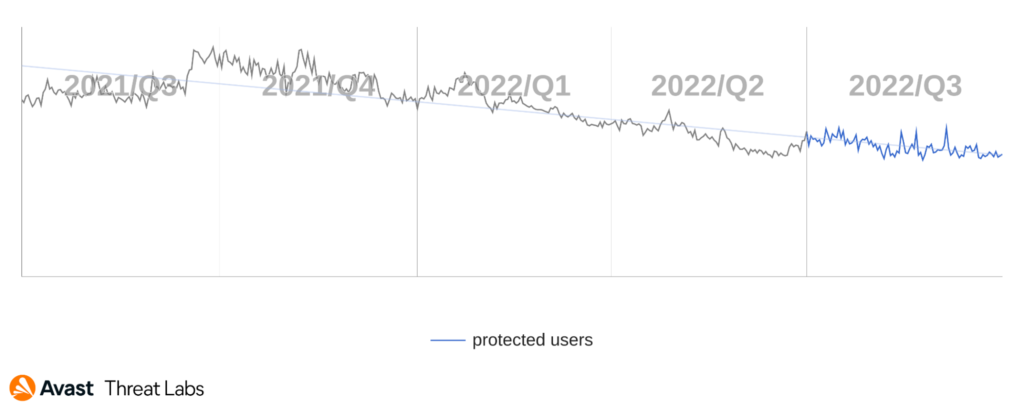
Interestingly, the number of protected users in Q3/2022 was slightly higher than last quarter. However, we continue to be on a long-term downward trend, as can be seen in the chart below. Flubot’s demise significantly contributed to this decline, as we’ve seen fewer banker-spreading campaigns since its disbanding.
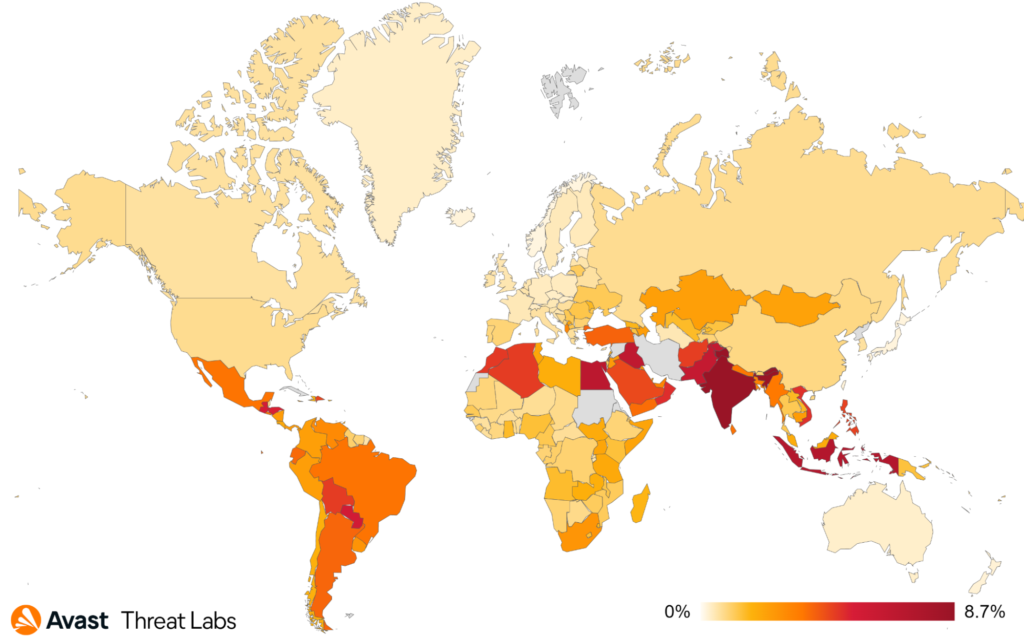
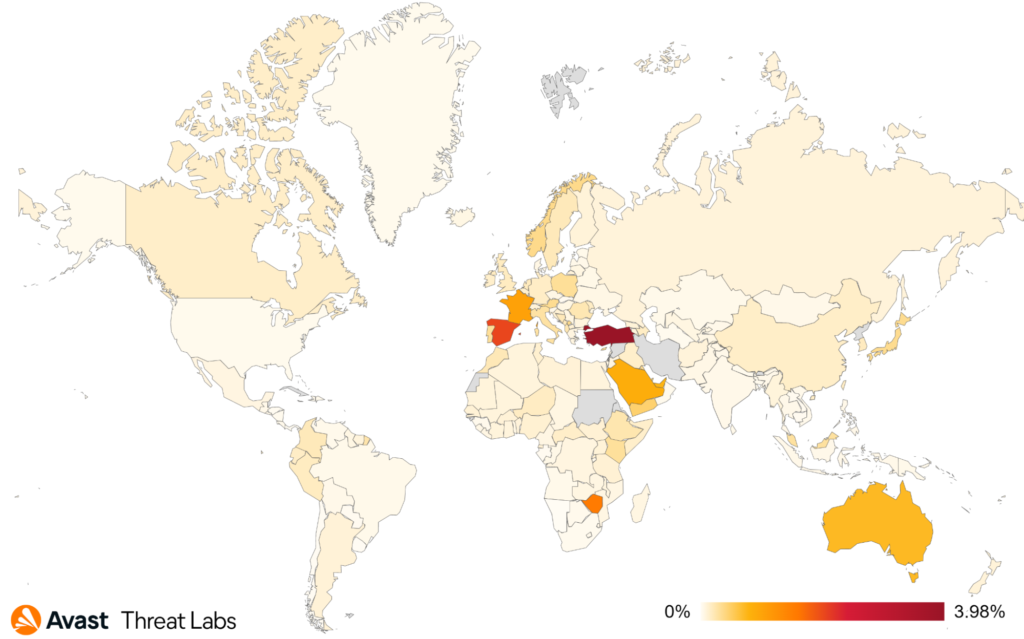
We saw some movement in the top affected countries in Q3/2022, with Spain, France, and Turkey coming in as the most targeted, while France shows a striking 70% increase in protected users. Contrary to this, we see a sharp decline in protected users in Italy, Germany, Australia, and the UK, up to a 40% drop.
TrojanSMS
In Q3/2022 we observed a continuation of existing premium SMS scams which started late last year and a few older strains retiring. SMSFactory and Darkherring remain the main TrojanSMS offenders this quarter. UltimaSMS and GriftHorse have finally been eliminated, as their number of protected users plummeted to nearly zero.
These TrojanSMS families rely on premium SMS subscriptions or sending SMS messages to premium numbers to extract money from victims. Left undetected, these malwares can rack up expensive phone bills, which is why they often come with stealth features to avoid discovery, hiding the application icon and the sent SMS messages. In the worst case scenario, the user forgets about the application or cannot identify the culprit while their money is siphoned away.
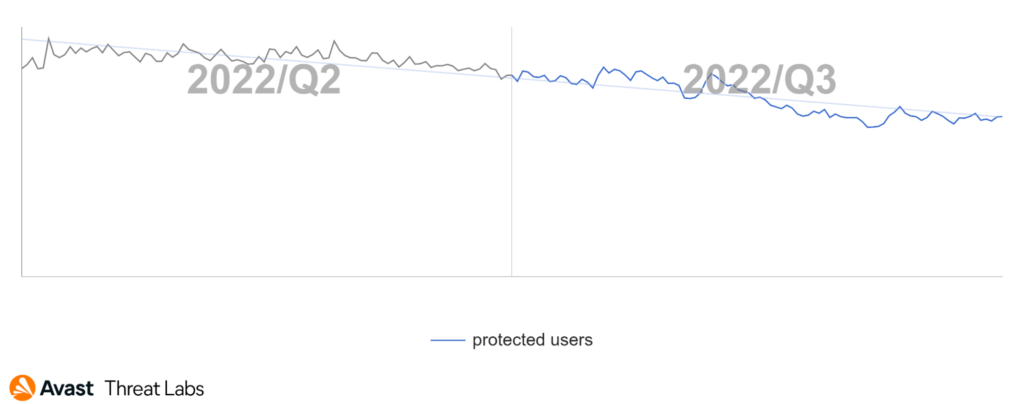
It is interesting to compare the methods of delivery of theseTrojanSMS strains. Families such as UltimaSMS, GriftHorse, and DarkHerring were distributed through the Google Play Store, and their numbers were in the tens of millions when discovered. However, following their discovery and takedown from the Play Store, these strains were nearly eliminated and no longer affected large numbers of users. On the other hand, SMSFactory, which uses pop-ups, malvertising, and fake app stores to deliver its payload, is still operating today, and we see a steady number of protected users still affected. While we observed some minor changes to the application and their C2 servers in the past few months, the malware and its functionality remain the same. SMSFactory accounts for over 60% of protected users this quarter, clearly dominating the TrojanSMS market.
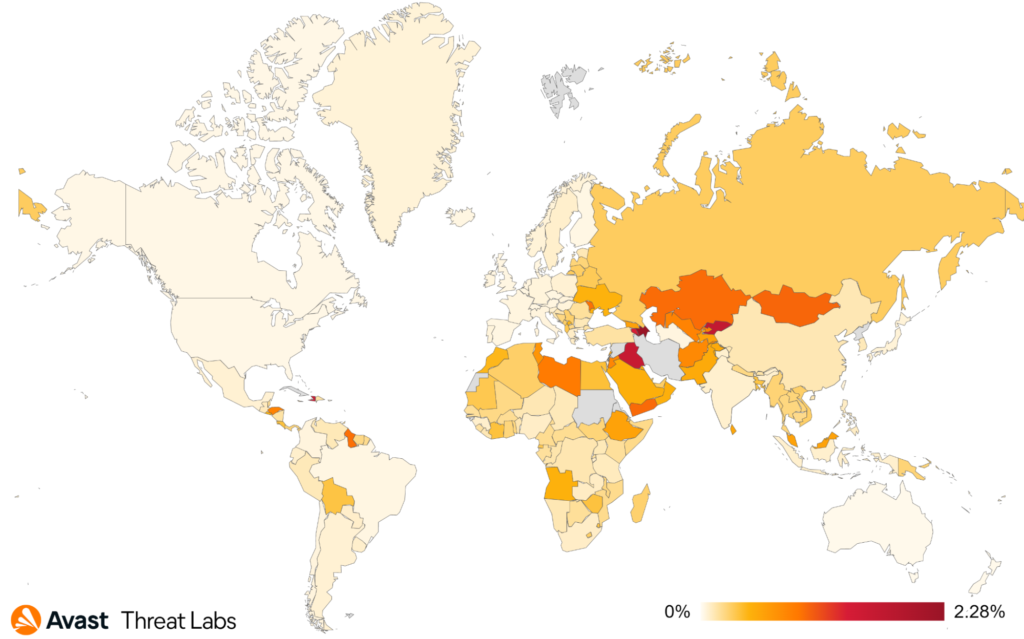
The distribution of protected users is similar to last quarter, with Brazil, Russia, Ukraine, Germany, and India holding the top spots. Azerbaijan, Kyrgyzstan. and Iraq show the highest risk ratio numbers.
With the exit of UltimaSMS and GriftHorse, as well as declining numbers for DarkHerring, the overall TrojanSMS trend is downward in Q3/2022. However, SMSFactory appears to be here to stay; hence we predict the numbers will maintain or slightly decline into the next quarter.
Spyware
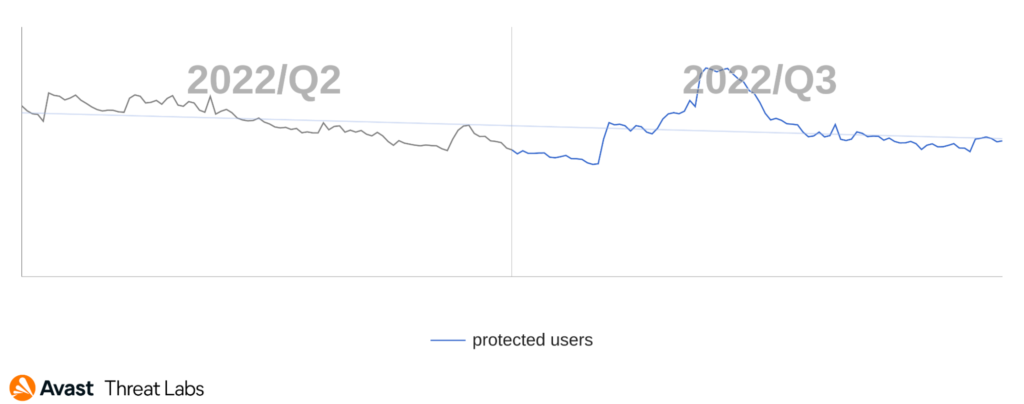
Spyware has been a persistent threat to users for the last several years. More recently, we tracked some spikes in activity in Q3/2022. Spymax leads with the most reach for several quarters now, while we observe Facestealer becoming a more persistent threat this year.
Spyware’s purpose is to spy on the user’s activity, including photos, messages, location, and other personal information. More recently, these malwares tend to look for login credentials, banking details, and even crypto wallet addresses. Spymax has accrued these features over the span of several years and often comes heavily obfuscated to evade detection. It imitates a variety of applications and made it onto the Google Play Store a few times during the Covid pandemic. FaceStealer, on the other hand, is rather new, appearing last year, with the ability to create convincing overlays to trick users into entering login credentials. According to our observations, and research conducted by Meta, these apps were reasonably successful in attacking users, often using the Play Store as a delivery method. The apps aim to steal logins initially only to social media platforms, but now also steal a variety of logins.
Of note is another form of Spyware we’ve seen more of in the last few quarters. These are malicious modified versions of popular messaging apps such as WhatsApp and Telegram. Numerous mods posted on forums, discord servers, and third-party app stores offer functionality not present in the original messaging applications, which is where malicious versions of these applications may spread. We advise users to avoid installing and using modded applications as there’s no guarantee that they are safe to use. There’s potential for personal information, photos, and messages to be stolen from user accounts. Malicious actors may even steal unique keys associated with the account, which may lead to loss of access to the account itself. Additionally, Whatsapp’s FAQ warns that unofficial applications or mods may lead to account suspension or a complete ban. We, therefore, advise users to only install messaging applications from official app stores.
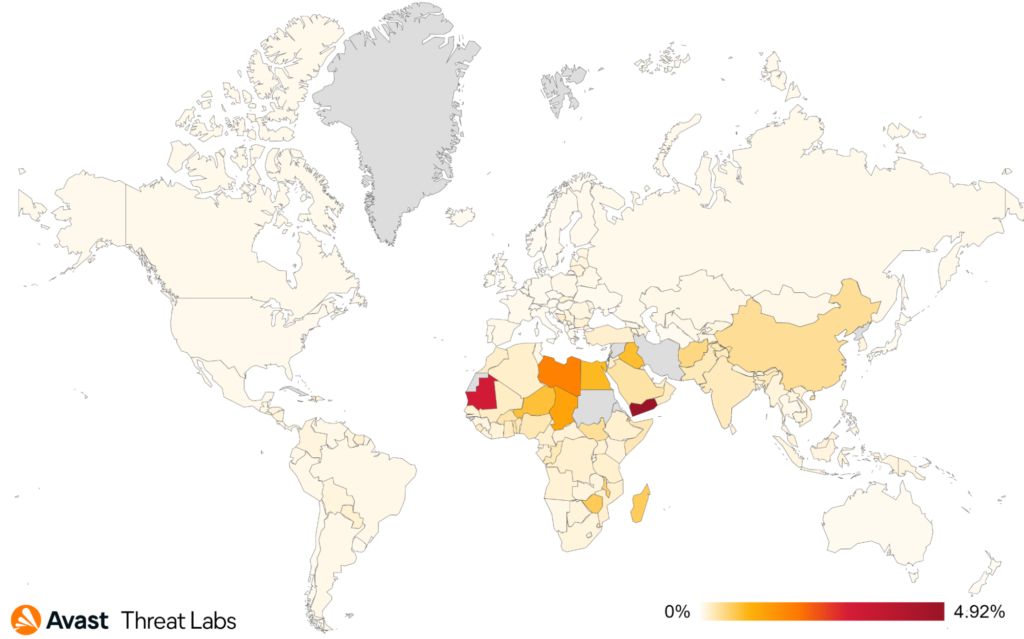
Spyware appears to have a relatively broad global distribution of affected users, with Brazil having the most affected users despite a 21% drop in Q3/2022. Following are India, Egypt, and the US, each with roughly a 10% increase in protected users this quarter.
We observed a downward trend last quarter. Still, it appears that new versions of FaceStealer bolstered the numbers of protected users this quarter. Overall, Spyware has been on the rise for the last two years.
Jakub Vávra, Malware Analyst
Acknowledgements / Credits
Malware researchers
Adolf Středa
Alexej Savčin
Daniel Beneš
David Álvarez
Igor Morgenstern
Jakub Křoustek
Jakub Vávra
Jan Holman
Jan Rubín
Jan Vojtěšek
Ladislav Zezula
Luigino Camastra
Michal Salát
Martin Chlumecký
Ondřej Mokoš
Pavlína Kopecká
Tomáš Zvara
Vladimir Martianov
Vladimír Žalud
Data analysts
- Pavol Plaskoň
Communications
- Marina Ziegler
- Stefanie Smith




