Avast releases a MafiaWare666 ransomware decryption tool. MafiaWare666 is also known as JCrypt, RIP Lmao, BrutusptCrypt or Hades.
Skip to how to use the MafiaWare666 ransomware decryptor.
MafiaWare666’s Behavior
MafiaWare666 is a ransomware strain written in C# which doesn’t contain any obfuscation or anti-analysis techniques. It encrypts files using the AES encryption. We discovered a vulnerability in the encryption schema that allows some of the variants to be decrypted without paying the ransom. New or previously unknown samples may encrypt files differently, so they may not be decryptable without further analysis.
The ransomware searches special folder locations (Desktop, Music, Videos, Pictures and Documents) and encrypts files with the following extensions:
3fr 7z accdb ai apk arch00 arw asp aspx asset avi bar bat bay bc6 bc7 big bik bkf bkp blob bsa c cas cdr cer cfr cpp cr2 crt crw cs css csv csv d3dbsp das dazip db0 dba dbf dcr der desc divx dmp dng doc doc docm docx docx dwg dxg epk eps erf esm ff flv forge fos fpk fsh gdb gho h hkdb hkx hplg hpp html hvpl ibank icxs indd index itdb itl itm iwd iwi jpe jpeg jpg js kdb kdc kf layout lbf litemod lrf ltx lvl m2 m3u m4a map mcmeta mdb mdb mdbackup mddata mdf mef menu mkv mlx mov mp3 mp4 mpeg mpqge mrwref ncf nrw ntl odb odc odm odp ods odt odt ogg orf p12 p7b p7c pak pdd pdf pef pem pfx php pk7 pkpass png ppt ppt pptm pptx pptx psd psk pst ptx py qdf qic r3d raf rar raw rb re4 rgss3a rim rofl rtf rw2 rwl sav sb sid sidd sidn sie sis slm sln snx sql sql sr2 srf srw sum svg syncdb t12 t13 tax tor txt upk vb vcf vdf vfs0 vpk vpp_pc vtf w3x wallet wav wb2 wma wmo wmv wotreplay wpd wps x3f xlk xls xls xlsb xlsm xlsx xlsx xml xxx zip zip ztmp
Encrypted files are given a new extension, which varies among the samples.
- .MafiaWare666
- .jcrypt
- .brutusptCrypt
- .bmcrypt
- .cyberone
- .l33ch
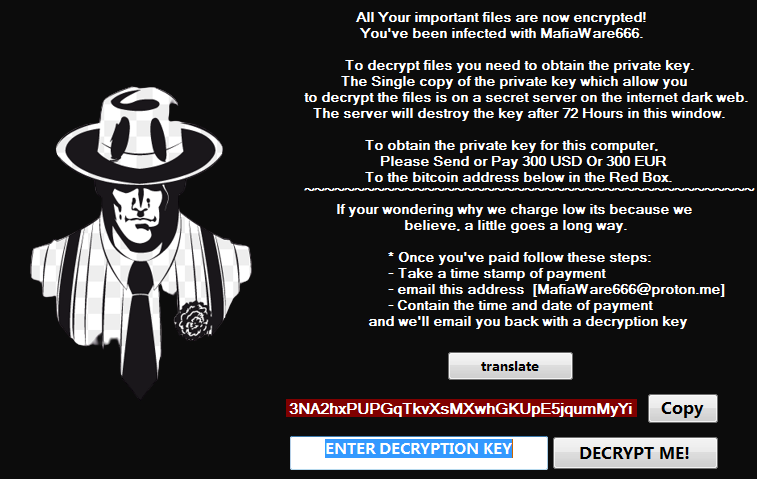
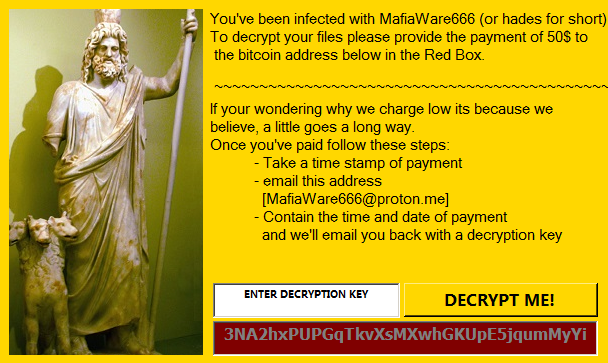
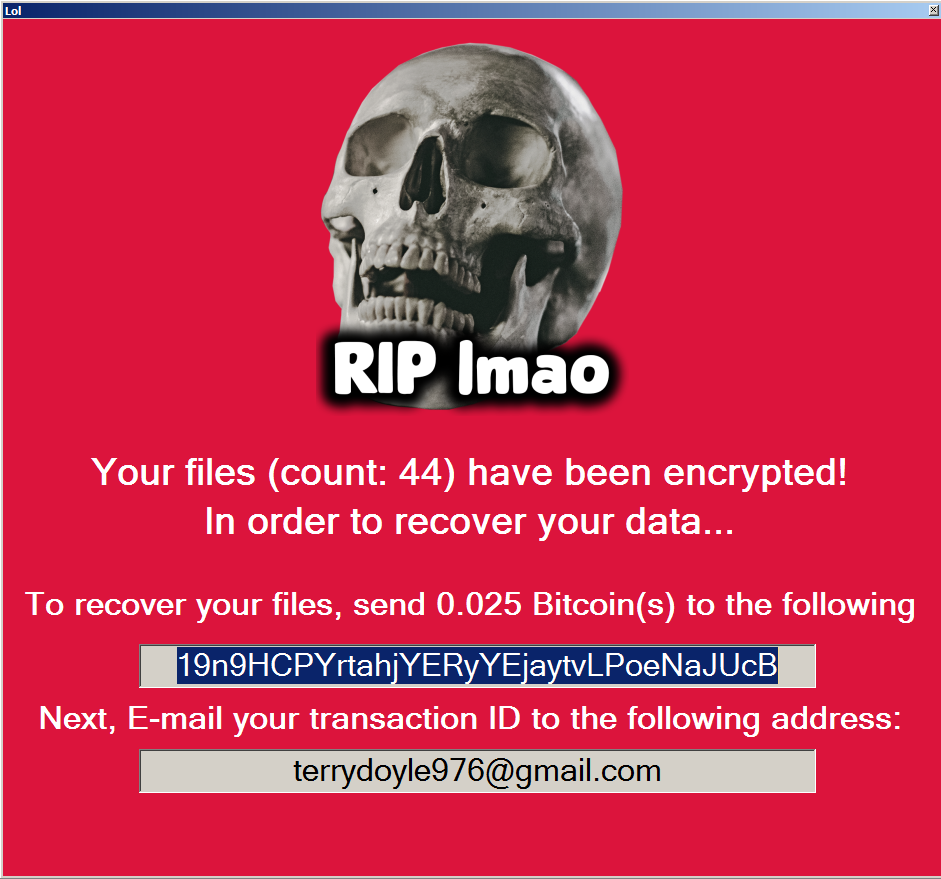
The ransomware displays a window with instructions explaining how to pay the ransom, once it completes the encryption process. The instructions tell victims to contact the attacker and pay them in Bitcoin. The ransom price is relatively low, between $50 – $300, although some of the older samples with different names demand much more, up to one Bitcoin, which is around $20,000 at the time of publishing.
Here are some examples of MafiaWare666 ransom notes:
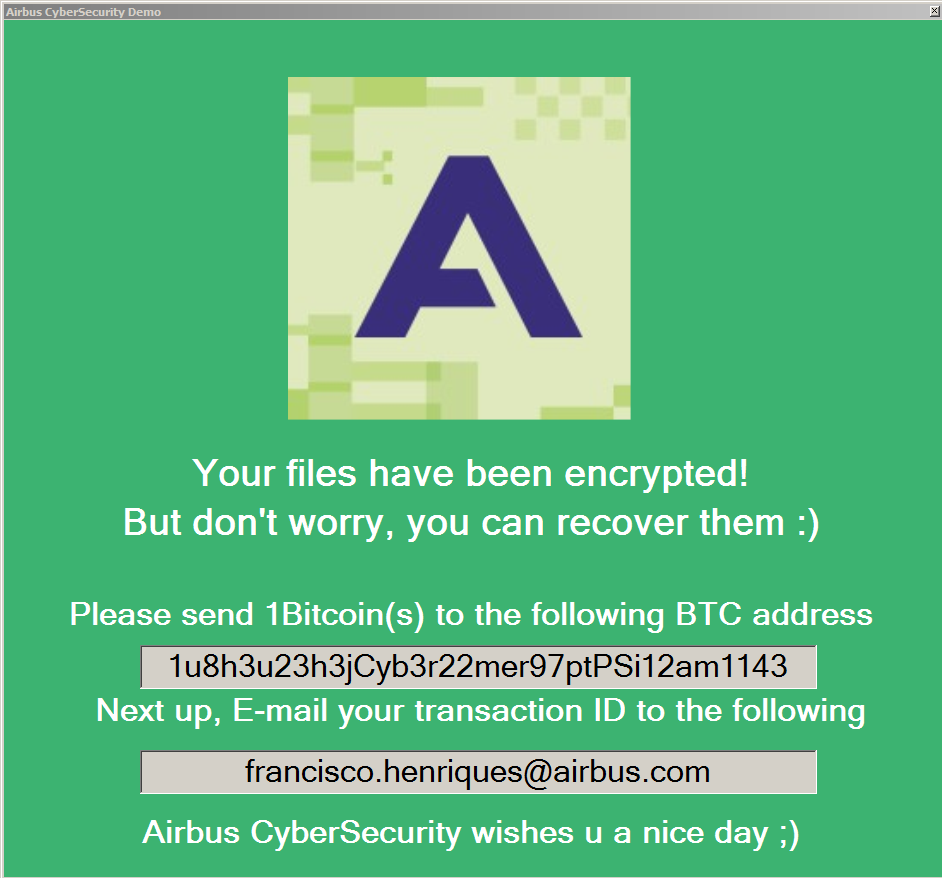
How to use the Avast MafiaWare666 ransomware decryption tool to decrypt files encrypted by the ransomware
Follow these steps to decrypt your files:
1) Download the free decryptor
2) Run the executable file. It starts as a wizard, leading you through the configuration of the decryption process.
3) On the initial page, you can read the license information if you want, but you really only need to click “Next”
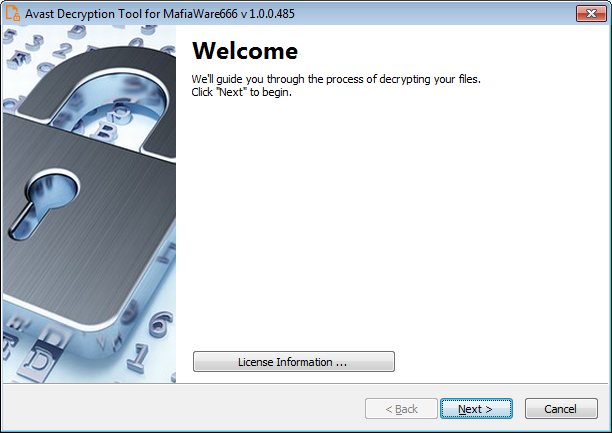
4) On the next page, select the list of locations you want to be searched and decrypted. By default, it contains a list of all local drives:
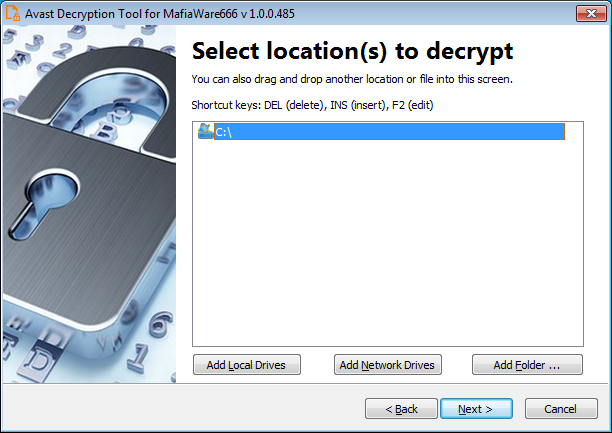
5) On the third page, you need to provide a file in its original form and encrypted by the MafiaWare666 ransomware. Enter both names of the files. If you have an encryption password created by a previous run of the decryptor, you can select “I know the password for decrypting files” option:
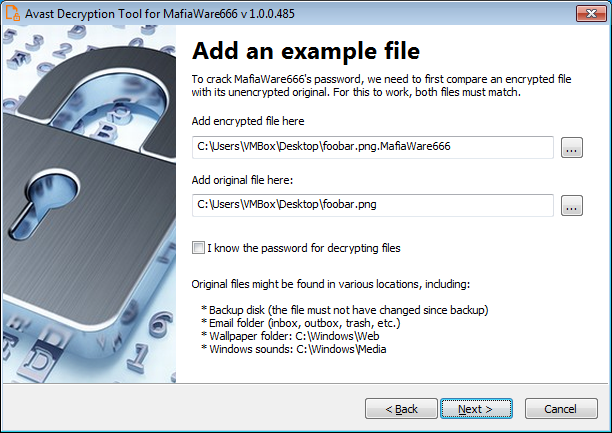
6) The next page is where the password cracking process takes place. Click “Start” when you are ready to start the process. The password cracking process uses all known MafiaWare666 passwords to determine the right one.
7) Once the password is found, you can proceed to decrypt all the encrypted files on your PC by clicking “Next”.
8) On the final page, you can opt-in to backup your encrypted files. These backups may help if anything goes wrong during the decryption process. This option is on by default, which we recommend. After clicking “Decrypt” the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
Indicators of Compromise (IoCs):
IoCs are available at https://github.com/avast/ioc/tree/master/MafiaWare666.
.MafiaWare666
6e91c9b5d052842093c6c292ec8224755d376aba6172d94faa241d8b192cb265
73d8e7baa073997d060ecf826b533263cf857a89b36a5fea809b7dbfc70b2d25
8324172e89866ed7122a9518bdc07e07ec2d173462dbbe2ff030fb408bc18123
.jcrypt
89ebe17b6dbb9dac780a4e2fe38da0261fa671cc79f4fe07cb9d26d9c0e447d2
979962e2d9f64ee15854e6df908627c90ab85a0a346c11656df46d3130459dc9
.brutusptCrypt
8c1a97f84caa9d58940d936a1c79c1c8d5fb791e1b3cac9fda22d195d3aeaea9
.bmcrypt
5d4ba2e6cc18dc509e73f3ceeea82a83ca252d07444a6b669947d31f60c6dfb8
.cyberone
ee376851cb318f77b9c8b715a09c5c0ce11043f679bb39fa5b5d67242c1c3bb9