Foreword
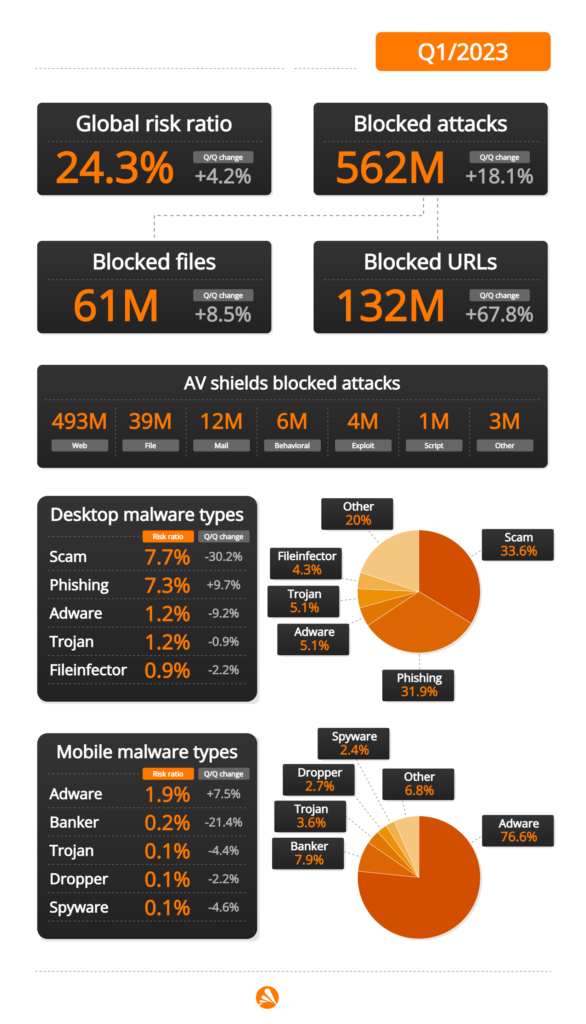
I’m thrilled to present the Avast Q1/2023 Threat Report, which provides a comprehensive overview of the latest cyberthreats and emerging trends in the security landscape. Our Threat Labs team has analyzed extensive data to identify and block the most significant risks to people across the globe, including the growing threat of social engineering attacks. In fact, two out of three of our detections during this quarter were phishing, scams, or related online threats, as can be seen from the infographics below.
In this edition of our Threat Report, our featured story presents the evolving tactics used by cybercriminals to infect users. We, for example, highlight the sharp increase in OneNote documents abuse by malware groups such as Qakbot, IcedID, Redline, and Emotet. These groups are continually adapting their tactics to evade detection and infect unsuspecting users with malware. Our analysis sheds light on this emerging threat landscape and provides insights on how users can protect themselves from these evolving tactics.
Information stealers remain one of the top threats, with an overall risk of infection increasing significantly by 22% compared to Q4/2022. This trend is particularly evident in Japan, which experienced an 86% increase in such attacks. Our team has also protected 333% more users from Raccoon Stealer activity, and this information stealer is now on par with the most popular information stealers, such as AgentTesla. Additionally, we discovered a new malware called NeedleDropper that is primarily used for distribution of these stealers.
East Asia, including Japan, Taiwan, and China, experienced a significant increase in adware activity this quarter. Additionally, the Russian DDosia project underwent a significant development, with 7,300 members now being involved in these malicious activities. Furthermore, coinminers continue to pose a threat in the Balkans, with a global shift from standalone miners like XMRig to webminers doing their dirty business in victims’ browsers.
The report also includes our latest efforts in combating ransomware, which involved the release of two new free decryption tools for the BianLian and MeowCorp (Conti offspring) ransomware families. In addition, we’ve seen some positive news about cybercriminal busts, particularly in Europe, targeting groups such as NetWire, DoppelPaymer, and Hive. The more cybercriminals that we can bring to justice, the better.
Moreover, several Remote Access Trojans (RATs) boosted their presence significantly, including Remcos, AsyncRat, and DarkComet, many of which had the help of the DBatLoader loader, particularly in the Czech Republic, Argentina, and Mexico, where the related risk ratio doubled this quarter.
Our researchers have been actively identifying zero-day exploits employed by threat actors in the wild. One such exploit was discovered in the highly popular MOBA game, Dota 2. In addition, vulnerabilities previously reported by our team in the last Threat Report have been increasingly exploited for the delivery of ransomware and spyware, both on desktop and mobile devices.
On mobile, adware continues its dominance, and it further grew in many countries, including India, Brazil, and Argentina, with MobiDash adware seeing over a 100% increase in protected users this quarter. Furthermore, mobile banking trojans continue to evolve and focus on instant payments, while machine learning is used to steal crypto wallet details.
Overall, I encourage you to read the full report to gain a deeper understanding of the latest security threats and trends. Our team is committed to providing you with the most up-to-date information and protection from these threats. Thank you for trusting Avast to keep you safe online.
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into two main sections: Desktop-related threats, in which we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems and include a special focus on web-related threats, and Mobile-related threats, in which we describe the attacks focusing on Android and iOS operating systems.
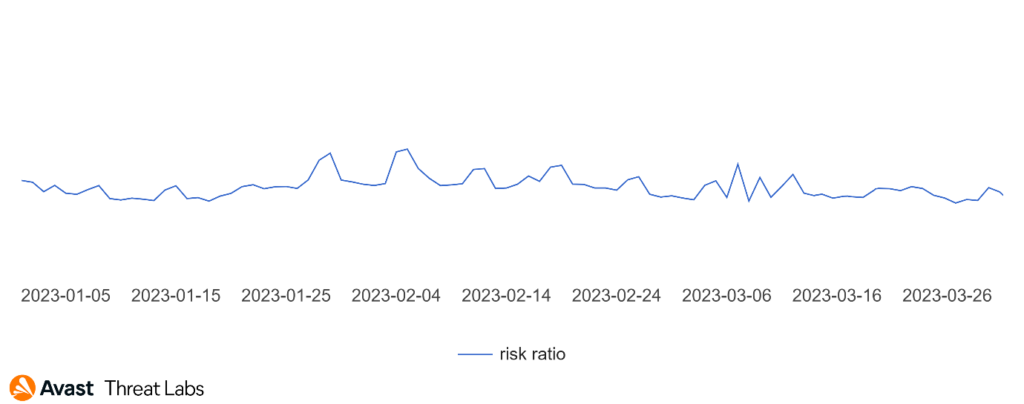
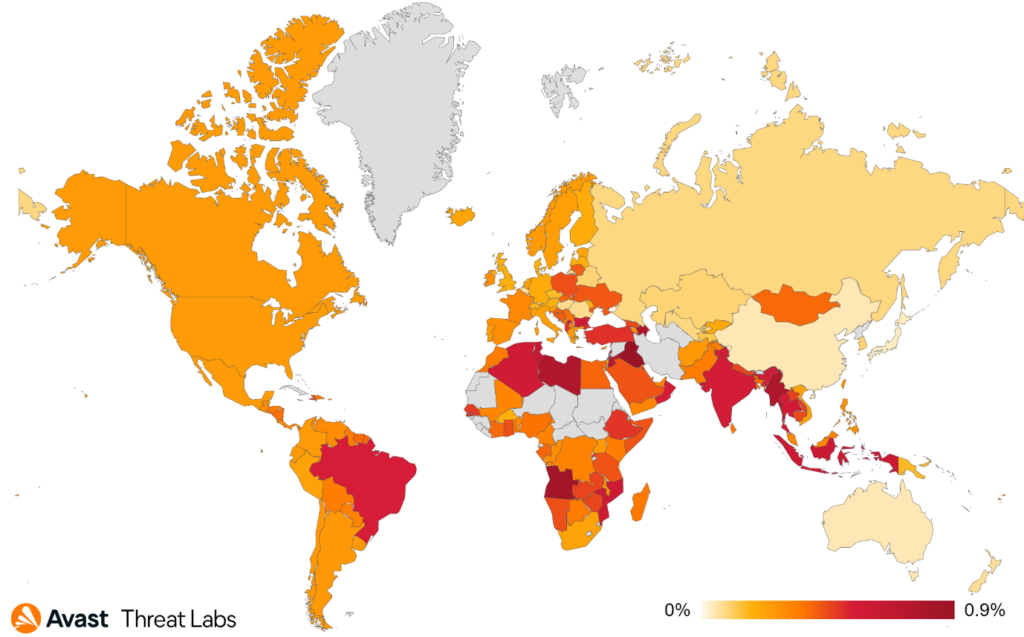
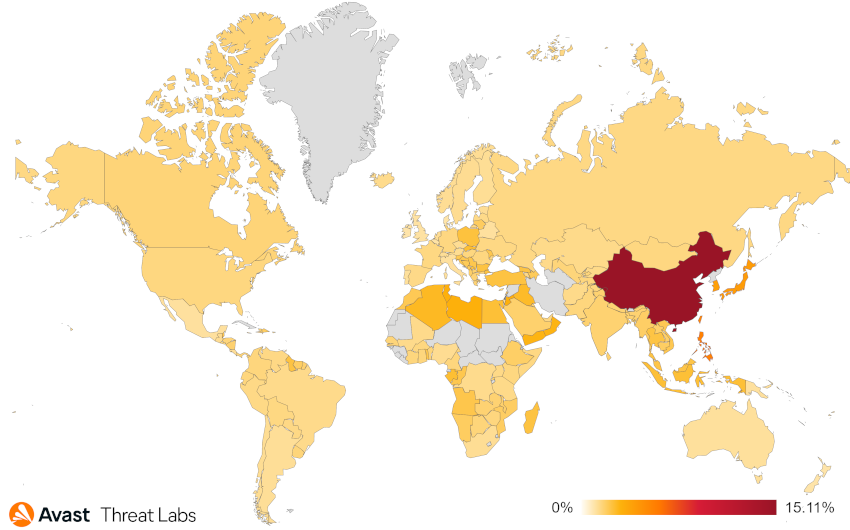
Furthermore, we use the term risk ratio in this report to describe the severity of particular threats, calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
Featured Story
New Malware Distribution Tactics
As cybercrime continues to be a lucrative business, cybercriminals are constantly seeking new ways to distribute malware and infect users. The recent change by Microsoft to block macros from files coming from the internet has caused criminals to explore alternative infection methods. Two of these emerging methods are detailed here:
New Attack Vector: Microsoft OneNote
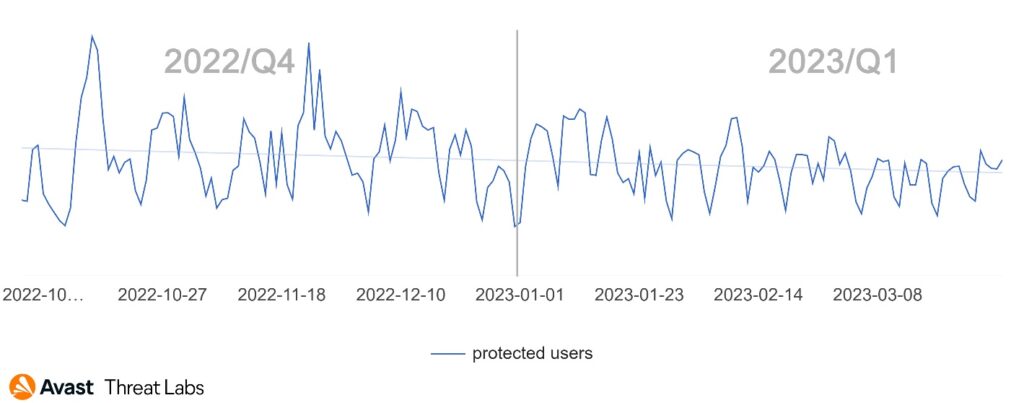
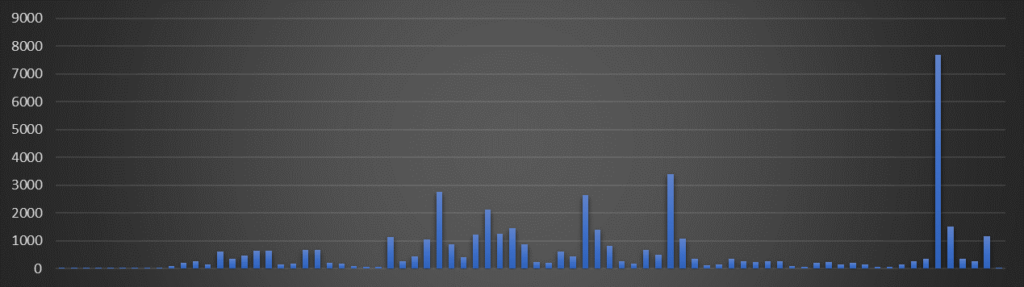
Microsoft OneNote, a note-taking application, has become a popular delivery method for malware. Cybercriminals attach disguised OneNote files to emails, and when a recipient opens the file, it can contain a script or code that downloads and installs malware onto their computer. Malware families spread via these campaigns include Qakbot, Raccoon, IcedID, AsyncRAT, and Redline, among others. The number of users that we’ve protected against these specific attacks has been increasing daily, highlighting the prevalence of this threat. We have protected more than 47,000 customers during Q1/2023 from this type of attacks, and the trend has only continued to increase over time:
Innovative Technique: Abusing Adobe Acrobat Sign
Another original way to distribute malware was discovered through the abuse of Adobe‘s cloud service, Acrobat Sign. Cybercriminals are exploiting the email notification system by adding text with a malicious link to a document, which is then sent to the intended recipient from a legitimate Adobe email address. When the victim clicks on the link, they are redirected to a site where they are asked to download a ZIP file containing a Redline Trojan variant designed to steal passwords, crypto wallets, and more.
This abuse of Adobe Acrobat Sign to distribute malware is a targeted and novel technique that may become more popular among cybercriminals, as it can potentially bypass anti-malware filters and reach victims more effectively.
The ever-changing landscape of cybercrime highlights the importance of staying up–to date on the latest threats and protection strategies. Both Microsoft OneNote attachments and the abuse of Adobe Acrobat Sign demonstrate how bad actors are constantly adapting to new tactics in their efforts to infect users with malware.
Luis Corrons, Security Evangelist
Desktop-Related Threats
Advanced Persistent Threats (APTs)
An Advanced Persistent Threat (APT) is a type of cyberattack that is carried out by highly skilled and determined hackers who have the resources and expertise to penetrate a target’s network and maintain a long-term presence undetected.
APT groups continue to pose a significant risk to organizations and governments worldwide. One such group is Gamaredon, which has been known to target Ukraine. Gamaredon is a sophisticated cyber-espionage group that has been active since at least 2013. The group primarily targets Ukrainian government and military entities, as well as other organizations in the country. The group utilizes spear-phishing to gain initial access to their victims, and the use of Telegram and Telegra.ph services as a distribution channel for Command-and-Control IPs is a common practice for the group.
Another APT group that has been identified as operating across multiple regions is MustangPanda. This group primarily targets countries in the Asian region, including Myanmar and Cambodia. The group persists in utilizing the Korplug malware in conjunction with various other custom tools.
The Lazarus Group is a threat actor with links to the North Korean government. The group has been responsible for a range of high-profile cyberattacks in the past. Recently, they made the news with a supply chain attack through 3CX Phone System, which leveraged malware called TxrLoader. Avast users are protected from the malware being spread in this campaign.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Adware
Adware is considered unwanted if installed without the user’s consent, tracks browsing behavior, redirects web traffic, or collects personal information for nefarious purposes, such as identity theft.
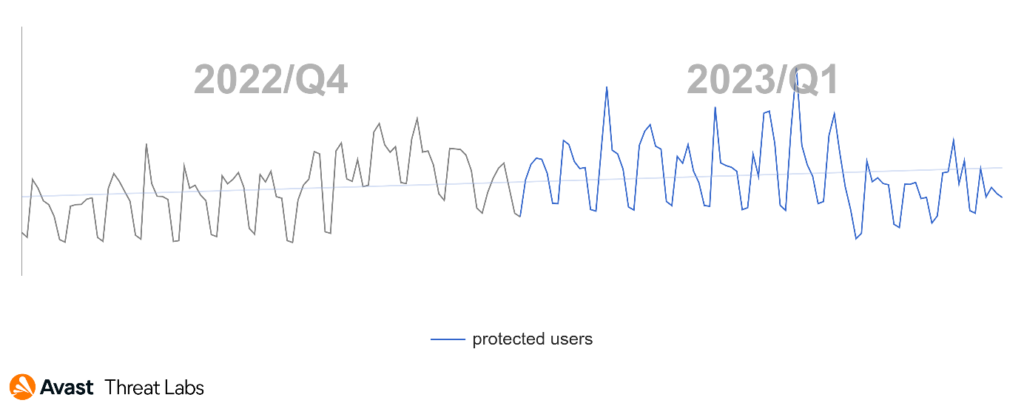
In Q1/2023, the trend of adware activities is stable, and we have observed no significant campaigns in this area, as the graph below illustrates.
The DealPly adware has recently built a dominant position in the adware landscape. The map below shows that DealPly‘s risk ratio has increased all over the world.
The risk ratio for all adware strains is slightly higher than in Q4/2022. The significant increase that we observed is adware activity in East Asia, namely Japan, Taiwan, and China. The complete risk ratio is illustrated in the map below.
Adware Market Share
The clearly identified market leader is still DealPly, which has a 15% share. We assign orders of lower magnitude shares to other strains as follows:
RelevantKnowledge(3%)DownloadAssistant(2%)BrowserAssistant(1%)
However, other unknown strains covered up 58% of the market share in Q1/2023. The dominant type of adware strains typically waits for a user to click on an arbitrary hyperlink and replaces the original link with one redirecting the user to advertising websites.
The table below illustrates a distribution of ad domains in the wild for this and the last quartiles. It is evident that the ad domains are dynamically rotated for each quarter to avoid detection by ad blockers.
| Q1/2023 | Q4/2022 |
saumeechoa[.]com (↑53%) | saumeechoa[.]com (2%) |
ptuvauthauxa[.]com (↓19%) | ptuvauthauxa[.]com (35%) |
oovaufty[.]com (↑16%) | oovaufty[.]com (8%) |
ninoglostoay[.]com (7%) | — |
go.ad2upapp[.]com (↓1%) | saumeechoa[.]com (2%) |
Unfortunately, the ingenuity of adware authors is getting better every quarter. Adware is often found on websites offering free software downloads or other products, and it’s a common tactic used by online spammers. We’ll describe detailed information about Web-based Adware in a separate section.
Adware has the potential to gain control over a system and execute malicious software like ransomware, spyware, RATs, and other threats. However, it should be noted that adware is generally more bothersome for users rather than truly dangerous.
Martin Chlumecký, Malware Researcher
Bots
Bots are threats mainly interested in securing long-term access to infected devices with the aim of utilizing their resources, be it remote control, spam distribution, or denial-of-service (DoS) attacks.
As the war in Ukraine progresses, hacker groups that are interested in the conflict continue to evolve. Notably, the DDosia project maintained by the NoName057(16) group underwent a significant development. Presumably as a reaction to various researchers tracking the project, the group implemented an authentication mechanism for the retrieval of targets. Moreover, we suspect that they started banning IP addresses that are suspected to be snooping on the network. The number of DDosia participants has progressed steadily, reaching around 8,500 members by the end of Q1/2023.
As was already mentioned in the Featured story, since Microsoft announced its intention to curtail Microsoft Office macros, threat actors have been unusually creative in testing other payload types. We’ve seen them using ISO archives, Microsoft Office Template files, and HTML smuggling during the previous two quarters. This quarter’s new target is Microsoft OneNote, which has become rather popular with various threat actors – both distributors (such as Emotet) and “consumers” (Qakbot, IcedID, AsyncRAT and others) appear to be rather keen on it.
In comparison to the previous quarter with a huge Emotet campaign, this quarter has been rather calm, showing a slight decline in the risk ratio (-13% q/q). While many prolific families (such as Amadey, Qakbot or Twizt) went through notable increase in their prevalence, Emotet surprisingly wasn’t among those as it went through a significant decline in its activity. The open-sourced botnet BlackNET, whose popularity soared in the previous quarter, went through a decline bringing its prevalence closer to the numbers we were seeing half a year ago.
Adolf Středa, Malware Researcher
Coinminers
Coinminers are programs that use a device’s hardware resources to verify cryptocurrency transactions and earn cryptocurrency as a reward. However, in the world of malware, coinminers silently hijack a victim’s computer resources to generate cryptocurrency for an attacker. Regardless of whether a coinminer is legitimate or malware, it’s important to follow our guidelines.
After crashes of Silicon Valley Bank, Silvergate Bank, and Signature Bank in the US and Credit Suisse in Switzerland, cryptocurrencies experienced a slight resurrection in Q1/2023. Fortunately, the same cannot be said for coinminers that continue to decline in activity and even faster than previous quarters (-15% risk ratio).
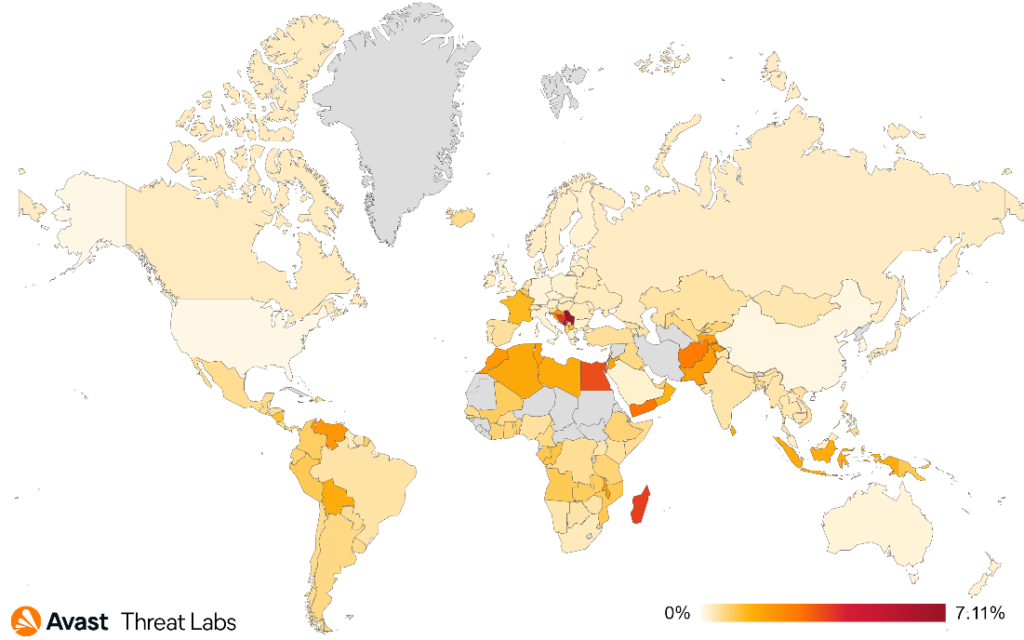
Following the last quarter, users in Serbia were once again most at risk of encountering a coinminer in Q1/2023, with a 7.11% risk ratio. The risk ratio of users in Montenegro was 5.94%, followed by Bosnia and Herzegovina with a 3.84% risk ratio, and Madagascar with 3.73%. In Q1/2023, Avast saw a high increase of coinminer activity in North Macedonia and Egypt, resulting in 81% and 12% increases in protected users, respectively.
Conversely, XMRig continues to drop. Its market share decreased by 13% in Q1/2023, now holding 16% in the total market. Similarly, VMiner lost 14% of its market share, making up 1.30% of the total market. On the other hand, other significant coinminers usurped more of the market – web miners (66.53% market share), CoinBitMiner (1.97%), FakeKMSminer (1.89%), and CoinHelper (1.27%).
The most common coinminers in Q1/2023 were:
- Web miners (various strains)
XMRigCoinBitMinerFakeKMSminerVMinerCoinHelper
Jan Rubín, Malware Researcher
Information Stealers
Information stealers are dedicated to stealing anything of value from the victim’s device. Typically, they focus on stored credentials, cryptocurrencies, browser sessions and cookies, browser passwords, private documents, and more.
Raccoon Stealer activity increased significantly in Q1/2023. We protected 333% more users compared to the previous quarter. Furthermore, according to our statistics, Raccoon is now on the similar activity levels as AgentTesla, RedLine, and FormBook, which are the most popular information stealers of all time. Due to this significant increase, the overall risk of getting infected by information stealers also increased quite significantly – by 22%.
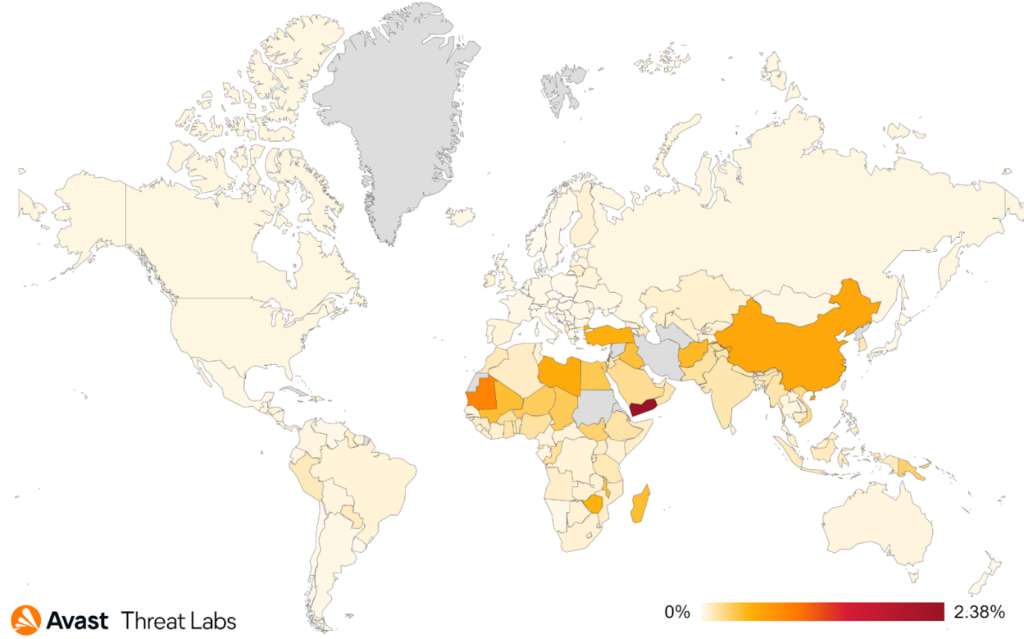
Similar to coin miners, information stealers were also more prevalent in Egypt, increasing the risk ratio by 53% (4.08% risk ratio). Individuals located in Yemen are still the ones with the highest risk of getting infected by information stealers (4.66% risk ratio). We also protected 149% more users in Saudi Arabia (1.45% risk ratio).
AgentTesla now holds 18.43% of the market share, increasing by 32% in comparison to the previous quarter. The activity of ViperSoftX also increased, as its market share rose by 69% and it now holds 2.21% of the information stealer market. On the other hand, FormBook and RedLine experienced a drop in activity, decreasing their market share by 40% and 28%, respectively.
The most common information stealers in Q1/2023 were:
AgentTeslaFormBookRaccoonRedLineArkeiFareitLokibotViperSoftX
NeedleDropper was a newly discovered dropper malware, mostly used for distributing information stealers like FormBook or AgentTesla. To avoid detection, the malware tries to hide itself by dropping many unused, invalid files and stores important data between several MB of unimportant data, and it also utilizes legitimate applications to perform the malicious activity.
MacStealer is a malware that targets MacOS users, primarily spreading through compromised .dmg packages. This malicious software collects personal information from various internet browsers, including passwords, cookies, credit card details, KeyChain database information, and cryptocurrency wallet data. The program stores this collected data in a ZIP file and sends it to remote servers, potentially exposing the victims to identity theft, financial loss, or other cyber threats.
Jan Rubín, Malware Researcher
Vladimír Žalud, Malware Analyst
Ransomware
Ransomware represents any type of extorting malware. The most common subtype is the one that encrypts documents, photos, videos, databases and other files on the victim’s PC. Those files become unusable without decrypting them first. For decryption tool, attackers demand money, “ransom”, hence the term ransomware.
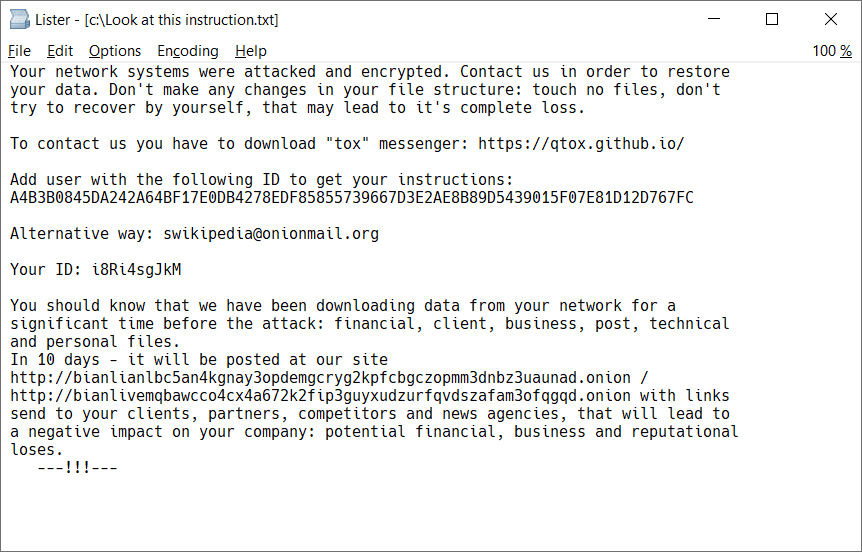
Unlike other threats, ransomware typically makes a point of letting the user know that they’ve been targeted by cybercriminals, often in a spectacular way – for example, by changing their desktop background or leaving ransom note text. Here is an example of such ransom note coming from BianLian ransomware:
In some cases, it may be possible to decrypt files without paying a ransom. If you ever suffer a ransomware attack, the ransom note may identify the exact ransomware strain that’s behind the attack. For example, the above-mentioned ransomware called BianLian can be decrypted using decryption tool that Avast released in January of 2023.
In case the ransomware cannot be decrypted, it’s important to archive all encrypted data, as there is always a chance that encryption keys will be published after the gang closes its business. Recently, this was the case with the MeowCorp ransomware, which is based on the leaked sources of Conti. Thus, we published it as Conti Decryptor in March 2023.
Speaking of Conti, the leaked sources are now also being used by the LockBit gang. This is the second time that the LockBit gang changed their encryptor – first, they introduced LockBit Black (based on BlackMatter) and have now switched to LockBit Green, with an encryptor based on the Conti source.
Sometimes, a ransomware gang closes their business, but not on their own volition; law enforcement may score in the battle against cybercriminals and seize the operation. As a recent example, Hive ransomware network was infiltrated by the FBI and Europol. Also, two members suspected to be members of the DoppelPaymer ransomware gang were arrested by joint forces of German Regional Police, Ukrainian National Police, and Europol.
When examining the ransom note image above, one can notice instructions on how to contact the attackers and how to send the payment. Typically, it is done by sending cryptocurrency (such as Bitcoin, Monero, or Ethereum) to a cryptocurrency wallet that’s owned by attackers. While the wallets themselves are anonymous, it is possible to track money transfers wallet(s) known to be associated with ransomware actors. According to Chainalysis, ransomware gangs received $457 million in 2022, a 40% drop from 2021 likely due to the fact that more companies now refuse to pay ransom.
Statistics
Here, we present ransomware statistics based on what we see in our userbase. WannaCry maintains its top position (18% market share) and is followed by STOP ransomware (15%). Lower in the ladder are Thanatos (3%), Hidden Tear (1%), Magniber (1%), and LockBit (1%). Overall, the absolute number of ransomware attacks bounced by Avast is slowly declining, as the ransomware authors are switching to targeted attacks that are less frequent than the mass attacks that we’ve seen in the past:
Ladislav Zezula, Malware Researcher
Jakub Křoustek, Malware Research Director
Remote Access Trojans (RATs)
A Remote Access Trojan (RAT) is a type of malicious software that allows unauthorized individuals to gain remote control over a victim’s computer or device. RATs are typically spread through social engineering techniques, such as phishing emails or infected file downloads. Once installed, RATs grant the attacker complete access to the victim’s device, enabling them to execute various malicious activities, such as spying, data theft, remote surveillance, and even taking control of the victim’s webcam and microphone.
After the continuous decline in the overall risk ratio observed over the second half of 2022, Q1/2023 is on par with Q4/2022. This is largely due to the Remcos strain, which has been very active in this quarter.
The increased activity of Remcos can be observed in most parts of the world. The overall increase in its market share among other RATs was by 60%. However, in the Czech Republic, Argentina, and Mexico, the increase was by more than 100%. We have frequently seen Remcos being spread by the DBatLoader loader. DBatLoader was also spreading Netwire RAT and FormBook information stealer, according to our data.
AsyncRat, DarkComet, and QuasarRAT also increased their market share by more than 30%. We now see AsyncRat and QuasarRAT active all over the world. AsyncRat is a little bit more active in Southeast Europe, Afghanistan, Pakistan, and Australia, while QuasarRAT is active in Latin America, Africa, and Turkey. DarkComet, on the other hand, seems to be limited mostly to Europe and the Middle East.
The most common RATs in Q1/2023 include:
HWormRemcosnjRATAsyncRatWarzoneQuasarRATNanoCoreNetWireLimeRATDarkComet
In an international law enforcement operation carried out by the FBI, the United States Attorney’s Office for the Central District of California, the Croatia Ministry of the Interior Criminal Police Directorate, Zurich Cantonal Police, Europol, and the Australian Federal Police took down the worldwiredlabs.com domain. A server hosting the NetWire RAT infrastructure was seized in Switzerland, and a suspected administrator of the website was arrested in Croatia. NetWire was sold through the website for prices ranging from $10 to $1,200.
Another arrest was made by law enforcement in Ukraine. The Khmelnychchyna Cybercrime Department, the regional police investigative department, and the SBU regional department arrested the developer of a RAT masked as an application for computer games. According to the report, this RAT infected more than 10,000 computers, and at the time of the search, the suspected developer had access to nearly 600 computers.
The ASEC analysis team discovered that the RedEyes (APT37, ScarCruft) group has been distributing a new malware named M2RAT. M2RAT is able to log keystrokes, leak/upload data to the attacker’s server, run processes, and capture screenshots. The report also mentions an information stealer that can communicate with the M2RAT. This stealer’s task is to steal data saved on mobile phones.
Researchers from Lumen discovered a campaign named Hiatus. One of the components delivered is the HiatusRAT which is similar to ZuoRAT (also previously discovered by Lumen) in that it also targets SOHO routers. Another component is a modified tcpdump tool. HiatusRAT can convert the infected router into a SOCKS5 proxy for the attacker as well as allow remote access to the device.
Ondřej Mokoš, Malware Researcher
Rootkits
Rootkits are malicious software specifically designed to gain unauthorized access to a system and obtain high-level privileges. Rootkits can operate at the kernel layer of a system, which grants them deep access and control, including the ability to modify critical kernel structures. This could enable other malware to manipulate system behavior and evade detection.
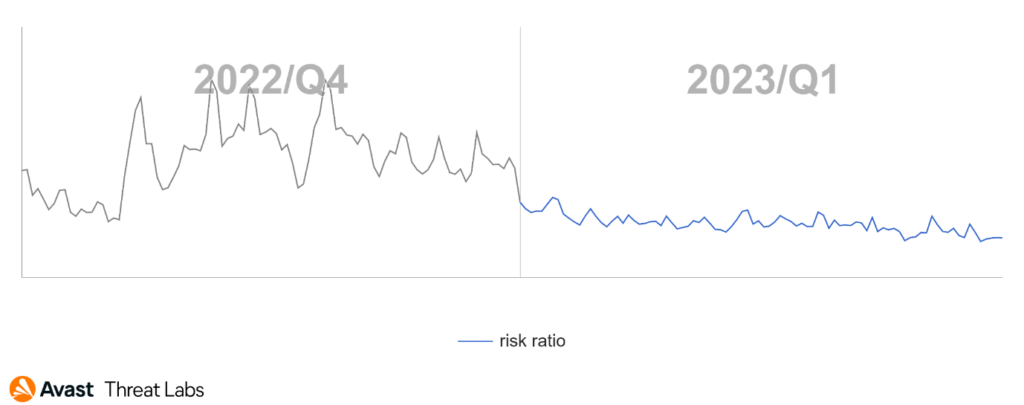
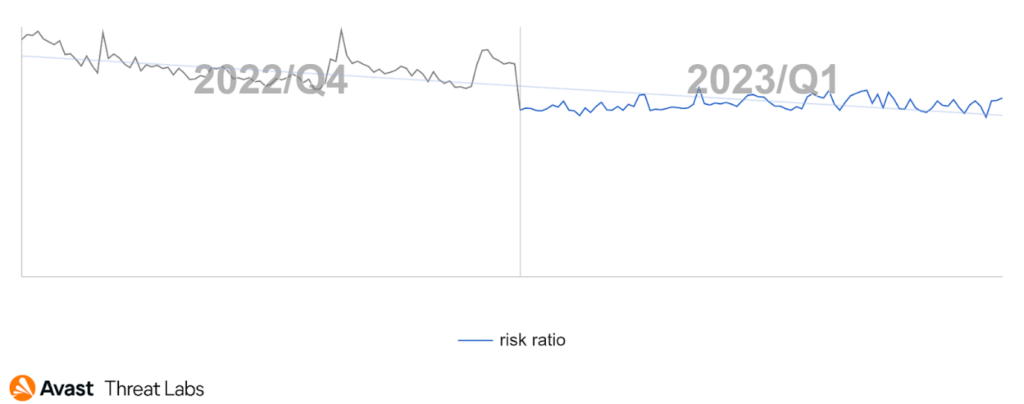
Rootkits are gradually being replaced by other and more effective tools to control systems. For this reason, we have also observed the downward trend of rootkit activities in Q1/2023, as is shown in the chart below.
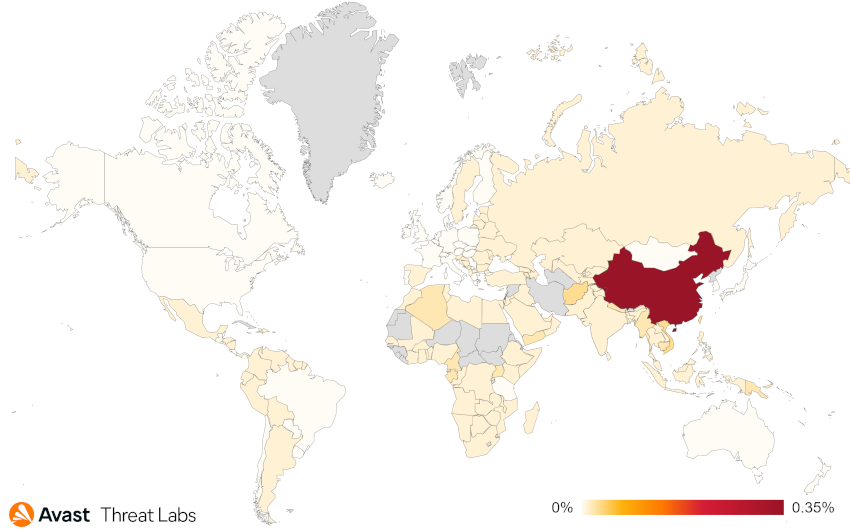
If we look at the risk ratio from the point of view of individual countries, China remains the dominant country in which the rootkit activities are the greatest.
Despite the downward trend in rootkit activities, the R77RK rootkit remains a dominant player in the rootkit market (28%) for its open-source policy and documentation. Although R77RK is not directly a rootkit that operates in the kernel mode, it provides the essential ability to modify the system behavior, typically hiding files, registries, processes, and so on.
In Q1/2023, we noticed no new release of R77RK that would affect the R77RK’s spread, which could have caused the declining trend. We will see whether R77RK keeps the majority in the wild in the next quarter.
The market share of the remaining four rootkit strains is approximately 20%, but these strains are relatively insignificant. To provide a comprehensive overview, the rootkit strains and their corresponding market shares are listed below:
Cerbu(7%)Alureon(7%)Perkesh(6%)ZeroAccess(3%)
In Linux operating systems, our data also indicates that rootkits are not a prevalent threat. On the other hand, Linux kernel rootkits are increasing in complexity. We detected Linux kernel rootkits using kernel space packers that can efficiently pass under the radar.
As presented at Botconf 2023, we keep tracking Syslogk Linux kernel rootkit and again found a new version that is integrated with a usermode bot. This is a bot that is not continuously running but stealthily started by the attacker via relatively complex magic packets. Such bot fakes a different service per sample allowing the attacker to connect to it and implements a proxy mode for sending magic packets to other infected machines faking legitimate Mozilla Firefox and Apache 2 network traffic.
Even if not prevalent, we consider it important researching these threats to protect our users from advanced attacks.
Martin Chlumecký, Malware Researcher
David Álvarez, Malware Analyst
Vulnerabilities and Exploits
Exploits take advantage of flaws in legitimate software to perform actions that should not be allowed. They are typically categorized into remote code execution (RCE) exploits, which allow attackers to infect another machine, and local privilege escalation (LPE) exploits, which allow attackers to take more control of a partially infected machine.
Exploits continue to represent a threat that is exceedingly difficult to protect against, with the rate of newly discovered vulnerabilities showing no signs of slowing down in Q1/2023. The January Patch Tuesday update fixed CVE-2023-21674, a vulnerability in ALPC that we discovered in the wild when it was used in an attempt to escape from the Chromium sandbox straight into the Windows kernel. A whopping number of four in-the-wild zero-days were discovered by Clement Lecigne of Google's Threat Analysis Group. Two of these exploits were used by spyware vendors in sophisticated exploit chains targeting both Android and iOS devices. Interestingly, one of these chains also exploited CVE-2022-3723, a type confusion in V8 that we reported to Google back in October 2022.
This quarter also showed that financially motivated cybercriminals do sometimes possess zero-day capabilities, once again disproving the common misconception that zero-days are a privilege of stealthy APT attackers. In February, a cybercriminal group attempted to deploy the Nokoyawa ransomware through a zero-day LPE exploit for CVE-2023-28252. One of the most interesting facts about this attack is that it was independently reported to Microsoft by three companies, indicating that there is perhaps a reason for why zero-days are not often used in such noisy attacks. Another example of financially motivated attackers stepping up their game are the Magniber ransomware threat actors using CVE-2023-24880 to bypass Microsoft SmartScreen. As we have researched Magniber and the Magnitude exploit kit extensively in the past, we were not in the least surprised that these attackers were able to devise such advanced bypass methods.
Finally, our research highlighted that malware could spread even through seemingly innocent activities, such as playing video games. We discovered that Dota 2, a highly popular MOBA game, was vulnerable due to its use of an outdated version of the V8 JavaScript engine. We have also found that an attacker took advantage of this vulnerability and exploited a smaller number of players of certain custom game modes. We have reported this vulnerability and it was fixed on January 12, making the game once again safe to play. However, as we have shown in our research blog, such vulnerabilities could have much more dire consequences, potentially endangering the millions of active Dota players.
Jan Vojtěšek, Malware Reseracher
Web Threats
Phishing
Phishing is a type of online scam where fraudsters attempt to obtain sensitive information including passwords or credit card details by posing as a trustworthy entity in an electronic communication, such as an email, text message, or instant message. The fraudulent message usually contains a link to a fake website that looks like the real one, where the victim is asked to enter their sensitive information.
Phishing continues to be a significant threat to consumers, and 31.98% of all attacks blocked by Avast this quarter were phishing attempts. Besides phishing threats, scams are a major threat with a share of 33.64% out of all attacks. These numbers combined show that two out of three detections now relate to social engineering. When comparing the recent phishing attack trends over the past few quarters, we observe a consistent and concerning increase in the appearance of phishing incidents.
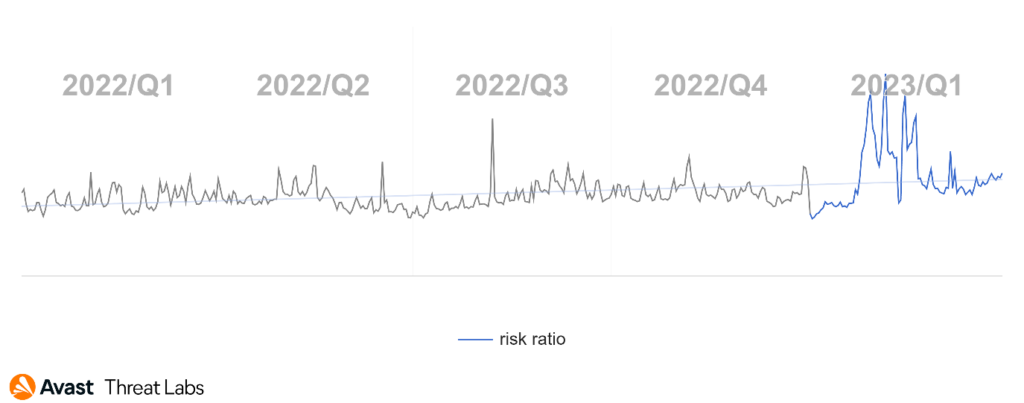
| Date | Phishing as % of all blocked threats |
| Q1/2022 | 22.85% |
| Q2/2022 | 22.54% |
| Q3/2022 | 24.44% |
| Q4/2022 | 25.91% |
| Q1/2023 | 31.98% |
The most significant jump occurred between Q4/2022 and Q1/2023, where the rate increased by more than 6 percentage points, from 25.91% to 31.98%, making phishing almost one out of three of all blocked threats. This upward trend highlights the growing threat that phishing poses to consumers.
Cybercriminals are continuously evolving their tactics and becoming more sophisticated in their methods, as Avast researchers have uncovered how cybercriminals are increasingly targeting users on secondhand shopping platforms like Vinted. In these cases, scammers posing as buyers exploit the excitement and urgency associated with making a sale to extract personal information, such as phone numbers or credit card details. They even interact in real time with their victims via WhatsApp posing as technical support agents.
The prevalence of smishing attacks has also contributed to the rising rate of phishing incidents, and it is becoming increasingly popular among cybercriminals due to its high open rate and the sense of trust that people place in text messages from seemingly reliable sources, like banks or government agencies. Smishing attacks often involve urgent messages that prompt victims to click on a link or provide personal information. Common smishing attack themes include financial alerts, package delivery notifications, tax alerts, charity scams, and lottery scams.
Tech Support Scams
Tech support scam threats involve fraudsters posing as legitimate technical support representatives who attempt to gain remote access to victims’ devices or obtain sensitive personal information, such as credit card or banking details. These scams rely on confidence tricks to gain victims’ trust and often involve convincing them to pay for unnecessary services or purchase expensive gift cards. It’s important for internet users to be vigilant and to verify the credentials of anyone claiming to offer technical support services.
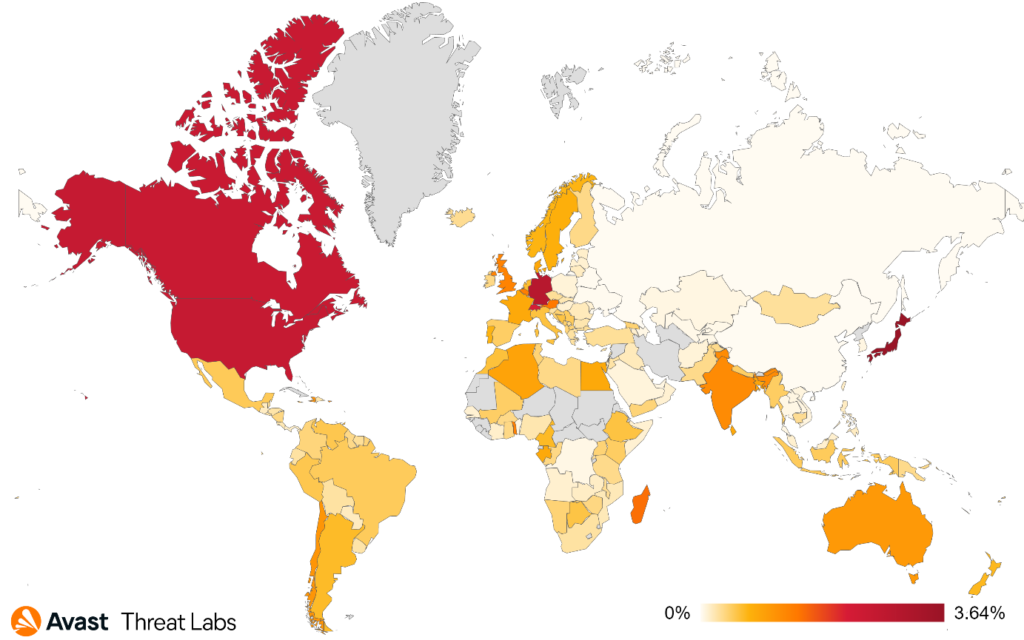
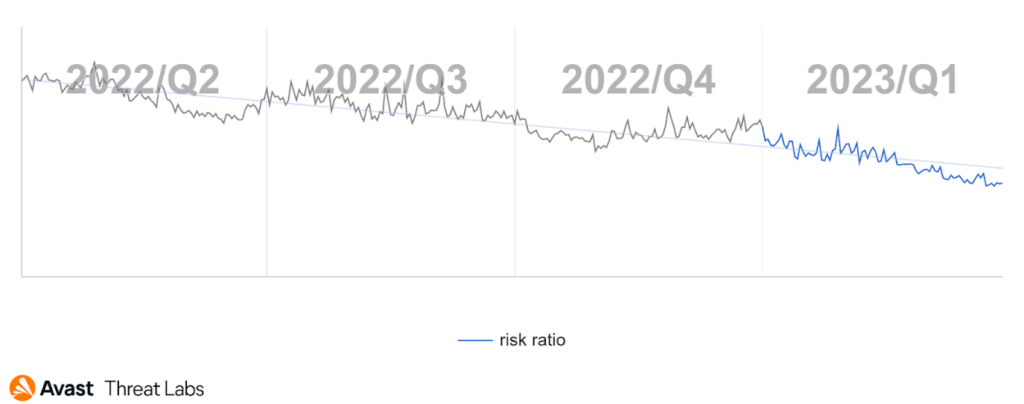
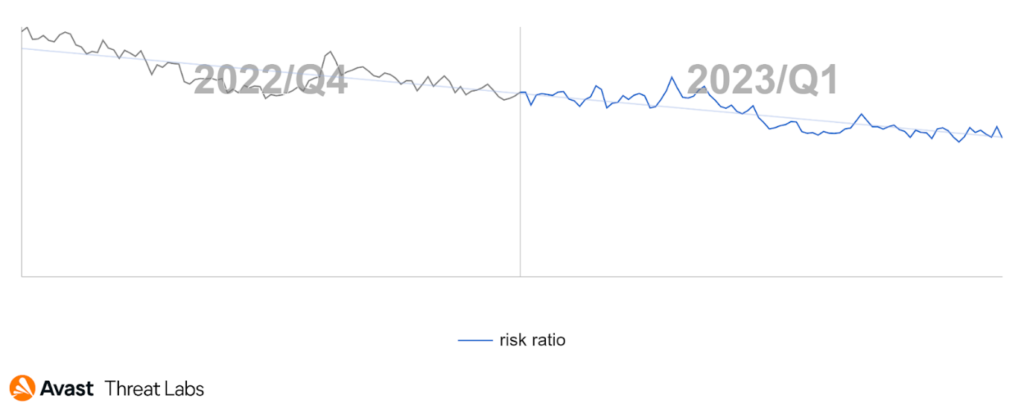
In the first quarter of this year, we have observed a significant decrease in the activity of technical support scams. This is good news for internet users who may have previously fallen victim to these types of scams. According to our data, the risk ratio of technical support scams has dropped considerably, indicating that scammers may be shifting their focus to other types of online fraud, such as refund and invoice scams, as is shown below.
Moreover, our data shows that the risk ratios for technical support scams in the following countries are as follows: Japan with 3.64%, Germany with 2.93%, the United States with 2.59%, Canada with 2.53%, and Switzerland with 2.18%. While these countries still have a higher risk ratio compared to other countries, the overall decrease in technical support scams is a positive development.
As always, it’s important for internet users to remain vigilant and be aware of potential online threats. By staying informed and taking precautions, such as not sharing personal information or downloading suspicious software, we can help keep ourselves and our personal data safe from cybercriminals.
Refund and Invoice Scams
Invoice scams involve fraudsters sending false bills or invoices for goods or services that were never ordered or received. Scammers rely on invoices looking legitimate, often using company logos or other branding to trick unsuspecting victims into making payments. These scams can be especially effective when targeted at businesses, as employees may assume that a colleague made the purchase or simply overlook the details of the invoice. It’s important to carefully review all invoices and bills before making any payments and to verify the legitimacy of the sender if there are any suspicions of fraud.
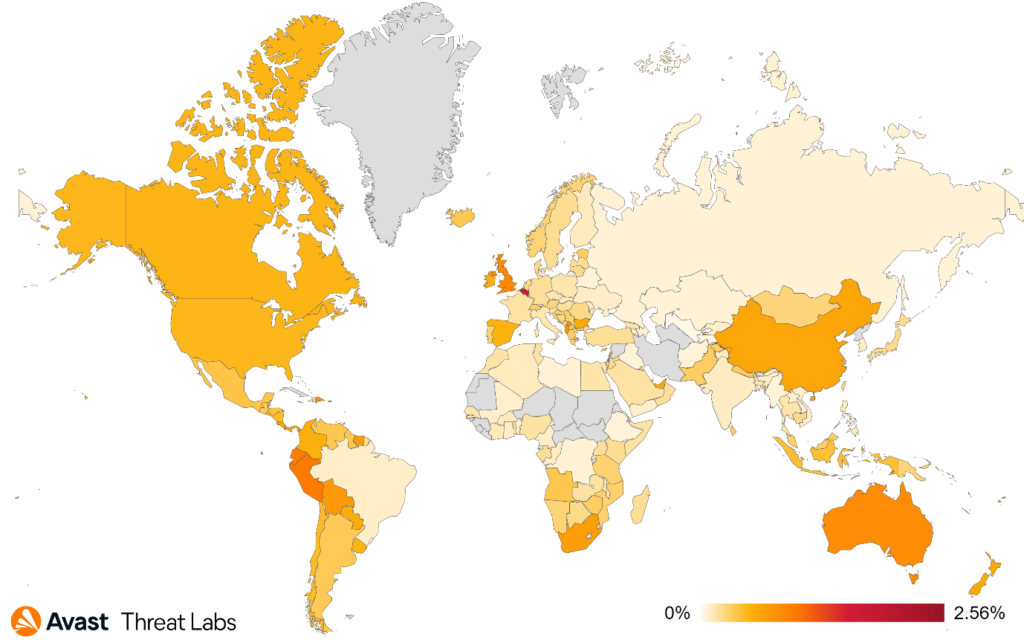
In Q1/2023, there was a significant increase in activity for invoice and refund scams. Recent data shows a 50% increase of risk ratio in Japan quarter over quarter, 26% in the United Kingdom, 21% in Canada, and 19% in the United States.
It’s important to note that these risk ratios may not fully capture the scope of the problem, as many scams go unreported or undetected. It’s crucial for individuals and businesses to remain vigilant when it comes to unsolicited invoices or refund requests as well as to take steps to protect themselves from these types of scams.
In conclusion, the increase in activity for invoice and refund scams in Q1/2023 highlights the ongoing need for cybersecurity awareness and education as well as the importance of taking proactive measures to protect oneself against these types of scams.
Web-based Adware
Web-based adware refers to malicious software or web pages that display unwanted advertisements in the form of pop-ups, banners, or redirects to third-party websites. Web-based adware can slow web browsing, potentially compromising user privacy and security.
In Q1/2023, web-based adware remained prevalent, with several notable examples. We have identified three basic adware types dominating this quarter.
Adult Content
The most significant adware type is an ad that entices users to click through video games with adult content where the users are guided via a few steps to “verify” their ages, select game characters, etc. If the user completes the verification process, the adware redirects the user to the ad server and displays questionable content.
Text Injection
Another non-negligible type is adware that injects a seemingly related text into specific paragraphs. A suspicious or infected webpage hides a simple JavaScript, injecting apparently related lines into the relevant section of the original text. The injected text contains a questionable URL and also waits for the user to click; see the example below.
Fake Win
The last dominant ad type is “winning pages” with different prices (cellphones, notebooks, etc.) conditioned by entering personal information, including payment cards, to “verify winners.” The victim usually has three attempts at an action like roulette or unwrapping packages. The victim always wins on the third attempt and is redirected to a page where they enter their personal data and possibly send a manipulation plot.
Alexej Savčin, Malware Analyst
Martin Chlumecký, Malware Researcher
Luis Corrons, Security Evangelist
Mobile-Related Threats
With another turbulent quarter in the mobile threats sphere behind us, we dive into an overview of our data and interesting new discoveries from across the industry. Banking trojans continue to evolve and appear to be focusing on instant payments. We also see cybercriminals using machine learning to steal crypto wallet details. Several 0-day exploits were chained together in a series of spyware attacks on both iOS and Android and a SMS stealer was made available on GitHub and used to target victims in Indonesia.
Here are the prevalent families of malware, coupled with insights based on our data to provide you with an overview of last quarter.
Adware continues its dominance
Adware threats on mobile refer to applications that display intrusive out-of-context adverts to users with the intent of gathering fraudulent advertising revenue. This malicious functionality is often delayed until some time after installation and coupled with stealth features such as hiding the adware app icon to prevent removal. Adware mimics popular apps such as games, camera filters, and wallpaper apps, to name a few.
As has been the case for several years, adware continues to be the top threat facing mobile users in Q1/2023. The intent of adware is to serve intrusive advertisements to its victims with the aim of harvesting fraudulent advertising revenue. Stealth is often a key component in ensuring the adware remains on the victim’s device for as long as possible. This quarter we observed a continuation of previously used techniques, with some new strains with different approaches added into the mix.
HiddenAds continues to be the top strain affecting users worldwide. As per its name, it uses stealth to masquerade as another app or to hide its icon. Once hidden, it often waits for a preset amount of time before displaying intrusive full screen adverts to its victims. This way, victims are less likely to suspect the HiddenAds app. Some previous campaigns snuck back on the Play Store again in small numbers but were taken down shortly after their release. Some third-party app stores continue to serve older strains, such as Scylla or versions of LiveClick.
FakeAdBlockers takes the second spot in the adware category. Continuing to display adverts instead of blocking them, these adwares often disappear upon installation and waste no time in displaying advertisements. We observe FakeAdBlockers on third-party app stores and they’re also often served by pop-up messages from less reputable sites. These adwares often imitate games, wallpaper apps, utility apps, and others, with the aim of fooling the user into installing the app.
Interestingly, we saw a significant rise in MobiDash adware this quarter, with over a 100% increase in protected users. Mobidash is an older strain of adware which started as an advert SDK that was added to repacked apps. Once the repacked app was installed, the MobiDash SDK would wait for a time and then display aggressive adverts throughout the device while in use.
Since its creation, MobiDash has been used to repackage hundreds of thousands of apps that imitate a wide range of gaming, utility, and camera apps. These repackaged apps have been distributed through forums and third-party app stores.
Compared to the previous quarter, there has been a slight increase in the number of users protected from adware, with Mobidash‘s resurgence playing a role in this uptick. This comes even though no major adware campaigns have infiltrated the Play Store during the current quarter.
Asia, Europe, and America are the most likely continents to be targeted by adware. Brazil, India, Argentina, and Indonesia continue to be the countries with the most protected users. We have noticed an increase in the number of protected users across most countries. However, it is worth highlighting that in the United States, there has been a significant decrease in both the risk ratio and protected users, with a drop of over 25%.
Evolution of Bankers
Bankers are a sophisticated type of mobile malware that targets banking details, cryptocurrency wallets, and instant payments with the intent of extracting money. Generally distributed through phishing messages or fake websites, Bankers can take over a victim’s device by abusing the accessibility service. Once installed and enabled, they often monitor 2FA SMS messages and may display fake bank overlays to steal login information.
Bankers continue to thrive, as they introduce several evolutions and improvements to existing strains, along with some newcomers entering the market this quarter. Despite this ongoing activity, we have seen a decline in the number of users needing protection, continuing the trend observed over the past few quarters. Cerberus/Alien and Hydra maintain their top spots, while Coper climbs to 3rd place with a significant 67% increase in protected users, surpassing RoamingMantis and Flubot.
Instant payment platforms remain a prime target for bankers this quarter, following their misuse by BrasDex last quarter. PixPirate, a new banker strain discovered by Cleafy, targets Brazil and utilizes the Pix instant payment platform to extract money from victims. Xenomorph has also updated its functionality to include instant payment extraction capabilities; combined with a cookie stealer, this allows the banker to automate the entire money extraction process without operator intervention. Given the growing popularity and availability of instant payment platforms, it is likely that other banker strains will adopt these techniques in the near future.
A new banker strain worth noting, discovered by TrendMicro, is TgToxic. This strain targets Asia through an elaborate phishing campaign that employs fake websites, compromised social media groups, and instant messages from the threat actors. TgToxic utilizes a gesture automation framework, enabling it to read and replicate user inputs. Combined with login extraction capabilities, the malware can send crypto payments using its hijack script without requiring user interaction. Victims may face difficulties in removing TgToxic, as it actively attempts to prevent removal via the accessibility service.
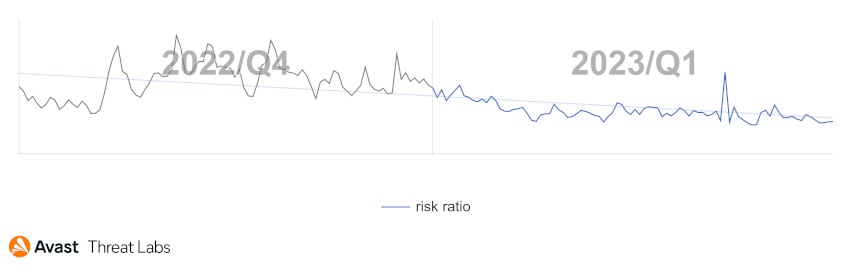
The long-term downward trend in the banker sphere continues according to our data. Similar to last quarter, we observe a 23% decline in protected users this quarter compared to last quarter.
In this quarter, Turkey has moved into the top spot for the highest number of protected users, overtaking Spain, followed by France in third place and Brazil in fourth. Both Brazil and Turkey experienced a slight increase in protected users, while France saw a significant drop of over 50% and Spain lost more than 25% of protected users.
Spyware and 0-days
Spyware is used to spy on unsuspecting victims with the intent of extracting personal information such as messages, photos, location, or login details. It uses fake adverts, phishing messages, and modifications of popular applications to spread and harvest user information. State backed commercial spyware is becoming more prevalent and is used to target individuals with 0-day exploits.
Spying on unsuspecting victims continues to be a prevalent issue, as our data indicates that spyware maintained its negative impact throughout this quarter. Spymax leads the pack over the last three months, accompanied by reports of trojanized messaging apps using machine learning to steal cryptocurrency, as well as multiple zero-day attacks targeting both Android and iOS devices.
Spymax remains largely unaltered, primarily aiming to extract personal information such as SMS, contact lists, location, and even live streaming the screen in some newer versions. More recently, it has targeted bank details, login credentials, and even crypto wallet information, blurring the boundaries between spyware and banker families. Fake advertisements, malicious redirects, and various phishing methods continued to facilitate Spymax‘s distribution this quarter. Facestealer and malicious messenger mod apps followed closely behind Spymax in the spyware category
ESET has discovered a new strain of trojanized messenger apps that target cryptocurrency wallets and related messages, affecting both Android and Windows devices. The messenger apps contain built-in clippers that allow for extraction of sensitive information such as crypto wallet recovery phrases, in some cases using machine learning to extract text from screenshots of recovery phrases.
Additionally, the malware can swap cryptocurrency wallet addresses in sent messages, resulting in fraudulent transactions being redirected to a different wallet than intended. Some versions were also bundled with remote access trojans. The spyware was distributed through fake messenger advertisements, which directed users to copycat websites serving the malware. As advised in the previous quarter, users should download apps from official sources and avoid using mods for messenger apps to stay safe.
In recent years, there has been growing awareness and coverage of government-backed attacks utilizing commercial spyware. Regrettably, this trend persists in the current quarter, as Google has reported multiple zero-day attacks targeting both iOS and Android users. One chain of exploits was disseminated through SMS package delivery phishing, using a malicious link to trigger the exploit. On iOS, this led to the delivery of the Predator spyware payload, while on Android, a zero-day discovered by Avast was used to deliver spyware onto victims’ devices. Subsequently, users were redirected to the official page, leaving them unaware of the events that had transpired.
Another chain of exploits targeted UAE users via the Samsung mobile browser, delivering C++ written spyware that focused on popular messaging apps and browser activity extraction. Users are strongly encouraged to keep their devices updated with the latest patches to mitigate the risks posed by these exploit chains.
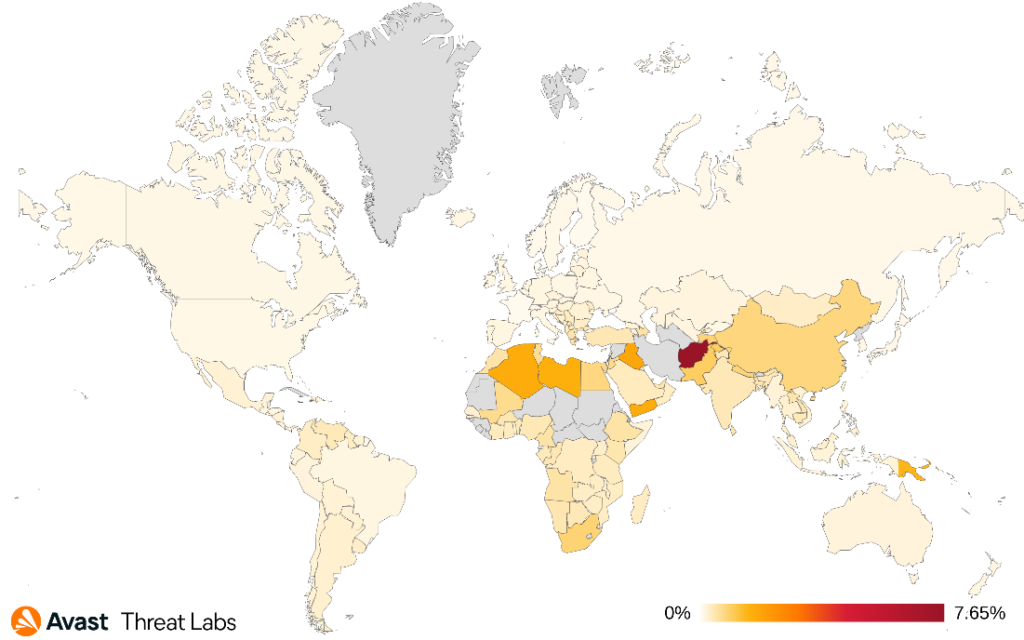
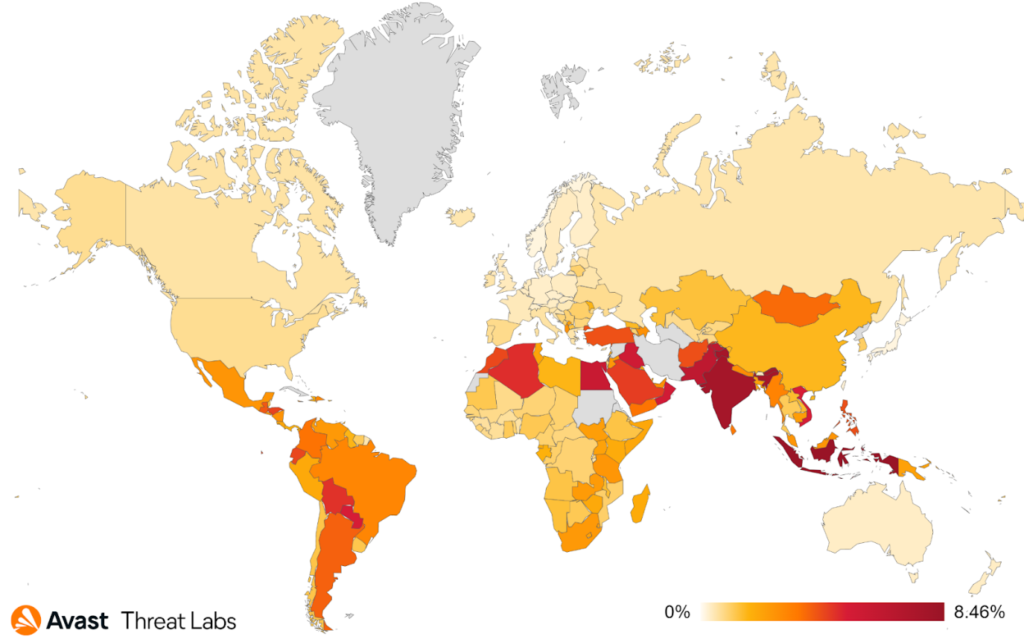
In this quarter, Brazil had the highest number of protected users, while Turkey experienced a significant increase and secured second place. They are followed by India, the United States, and Egypt. According to the data visualized on the map, users in Yemen continue to be at the greatest risk of encountering spyware.
Spyware is experiencing a gradual decline, similar to the trend observed last quarter. Although several new strains of spyware were discovered in the previous quarter, the overall numbers do not indicate an increase. Zero-day attacks are not expected to have a significant impact on the number of protected users, as they are often used sparingly and target specific individuals.
TrojanSMS Steals the Show
TrojanSMS is a type of malware that focuses on exploiting premium SMS or subscriptions to extract money from victims, some versions may also steal SMS messages. It usually comes with stealth features with the aim of hiding on victim devices and siphoning money unnoticed. Fake app stores and pop ups often distribute this type of malware.
In this quarter, two primary strains, Darkherring and SMSFactory., affected the most users. Older strains of previously prevalent TrojanSMS disappeared entirely last quarter, while a new TrojanSMS emerged this quarter, poised to evolve and expand its reach. Generic SMS stealers or senders have also increased their presence.
The TrojanSMS family comprises a diverse range of malware capable of stealing SMS messages, subscribing users to fraudulent premium services, or sending premium SMS. Often featuring stealth mechanisms to avoid detection and removal, these applications can wreak havoc on a victim’s mobile bill if not discovered promptly.
Darkherring is on the rise again, similar to the previous quarter when its distribution increased through third-party stores and other methods. A few applications were spotted on the Play Store, but they were removed shortly after being reported. In contrast, SMSFactory lost 50% of its impact compared to last quarter, indicating a declining strain. No significant changes to its functions were observed this quarter.
A TrojanSMS stealer called SMSEye is worth noting, as it has its own dedicated GitHub page, enabling other malicious actors to use it. The stealer initially emerged last quarter, with its second version appearing this quarter. Cyble reported that it was used to target an Indonesian bank through a phishing campaign to distribute the malware to users. SMSEye sends stolen SMS messages to a Telegram bot, in this case targeting user login credentials. Test versions of this malware have been observed featuring other bank and delivery service logos, suggesting the likelihood of more sophisticated uses for this stealer in the future.

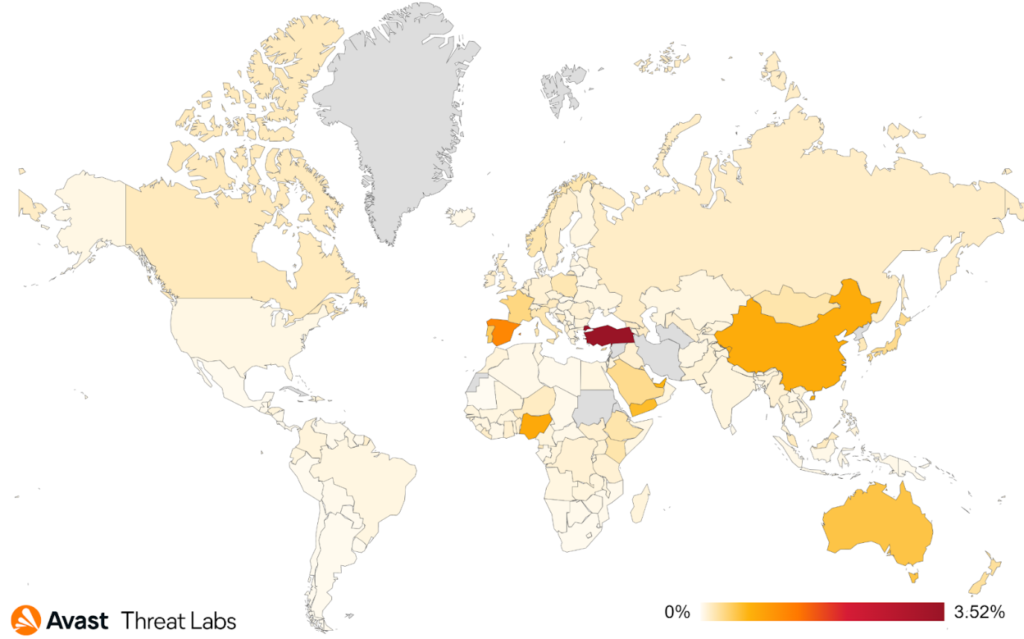
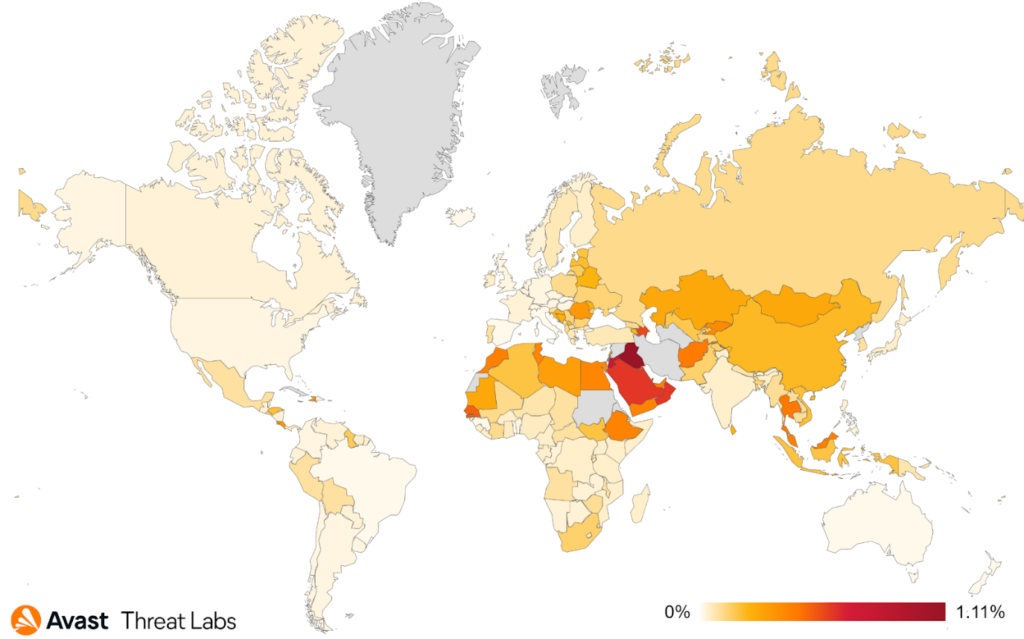
This quarter, we observe intriguing shifts in the distribution of TrojanSMS by protected users among countries. Poland claims the top spot, followed by Egypt, Brazil, and Mexico. Poland experienced a significant increase in protected users, while both Egypt and Brazil saw a decrease in protected users this quarter. As illustrated in the map below, Iraq and Jordan have the highest risk ratios for TrojanSMS.
Consistent with the previous quarter, we observe a steady decline in the number of affected users this quarter. The exit of UltimaSMS and Grifthorse, along with the gradual decline of SMSFactory, contribute to this decrease. However, the introduction of SMSEye may potentially help maintain these numbers in the upcoming quarter.
Jakub Vávra, Malware Analyst
Acknowledgements / Credits
Malware researchers
Adolf Středa
Alexej Savčin
David Álvarez
Igor Morgenstern
Jakub Křoustek
Jakub Vávra
Jan Rubín
Jan Vojtěšek
Ladislav Zezula
Luigino Camastra
Luis Corrons
Martin Chlumecký
Ondřej Mokoš
Vladimír Žalud
Data analysts
Filip Husák
Pavol Plaskoň
Communications
Emma McGowan
Grace Macej
Marina Ziegler