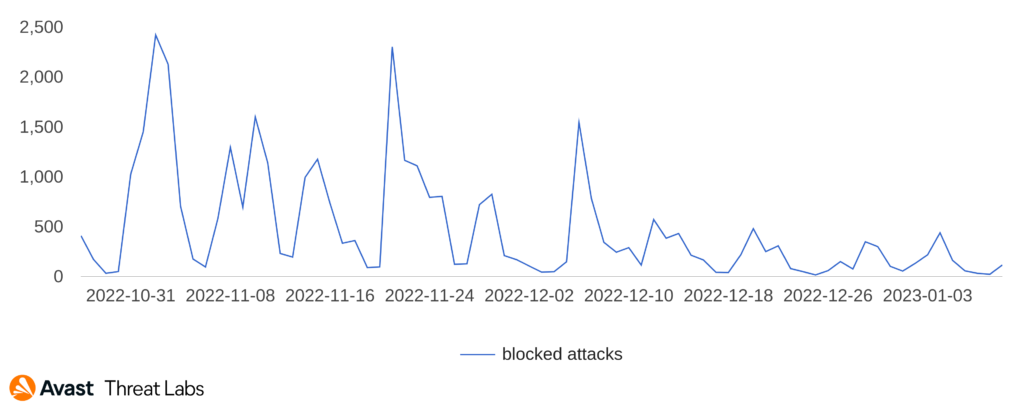
Since October 2022, we’ve been observing multiple malware types delivered via a new dropper strain that we are referring to as “NeedleDropper”. Its name references one of the ways the dropper stores data. NeedleDropper is not just a single executable, it carries several files which together create a malicious execution, extracting files to decrypt and inject malicious code. The malware tries to hide itself by dropping many unused, invalid files and stores important data between several MB of unimportant data, and also utilizes legitimate applications to perform its execution. NeedleDropper seems to be a new malware strain using the -as-a-service business model, and is sold on hacking forums to threat actors in order to hide the final payload. Thus far, we have blocked more than 30,000 attack attempts on Avast and AVG customers.
Analysis
NeedleDropper is a self-extracting archive that contains a modified AutoIt interpreter, obfuscated AutoIt script, and Visual Basic script, which is used for initial execution. All of this is bundled together with a couple of other files, some of which are used by the malware for its execution (this will be described later). All files are extracted inside a newly created directory inside the current user’s temporary directory. Newly created directory names usually follow the same pattern. The snippet below shows SFX commands (lines 4, 8, 12, 16) being hidden inside the unused text, invalid commands strings will be ignored and only the valid commands will be executed by a SFX archive.
Files
In this section, we’re going to describe key files inside the self-extracting archive, their purpose, and their content. All the files have unique randomly generated names and most of them also have a randomized extension.
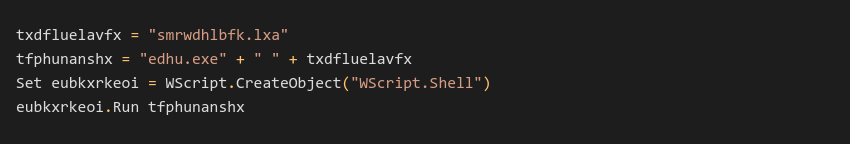
Visual Basic Script
The initial VBS script contains multiple lines of comments attempting to hide inside the payload. We’ve seen samples with several MB of comments nested inside them. The script launches a modified AutoIt interpreter with an LXA file as an argument.
Configuration File
The configuration file is an INI file which consists of several key-value pairs and many unused lines attempting to hide any configuration values. These values are frequently present inside S3tt!ng section.
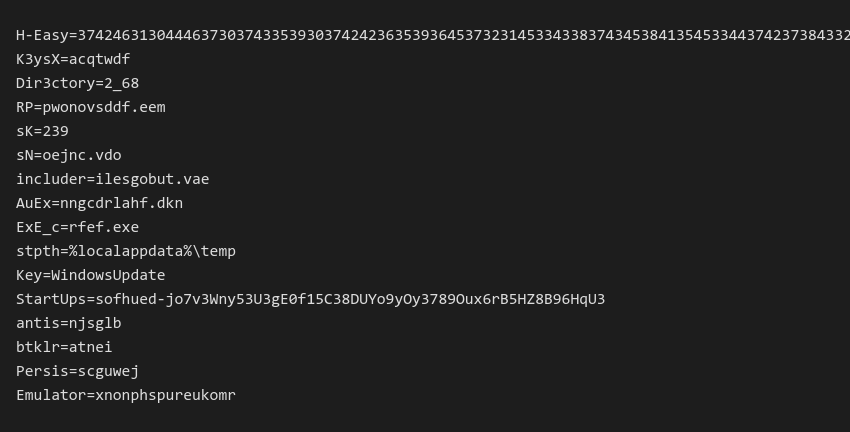
Frequently used key-values pairs and their usage:
K3ysX– key for final payload decryptionDir3ctory– working folder created inside “stpth” variableAuEx– obfuscated AutoIt scriptExE_c– AutoIt interpreterRP– encrypted payloadDelay– delay before the execution startsAntis– enables anti-analysis techniques, such as searching for processes which could indicate VM/sandbox (VMwaretray.exe,VboxService.exe,VBoxTray.exe, ..)StartUps– if not empty, malware will register NeedleDropper’s persistence under\SOFTWARE\Microsoft\Windows\CurrentVersion\Runregistry key based on the current user’s privileges. The registry key that is used by malware is obtained from theKeyinside the configuration file.
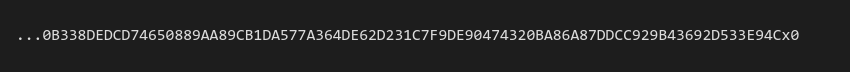
Payload
The payload file contains a one-lined reversed hexlified malicious payload. The whole string ends with …x0. Later versions of NeedleDropper move the payload from a separate file to the configuration between [Troj] and [FinTroj] sequence.
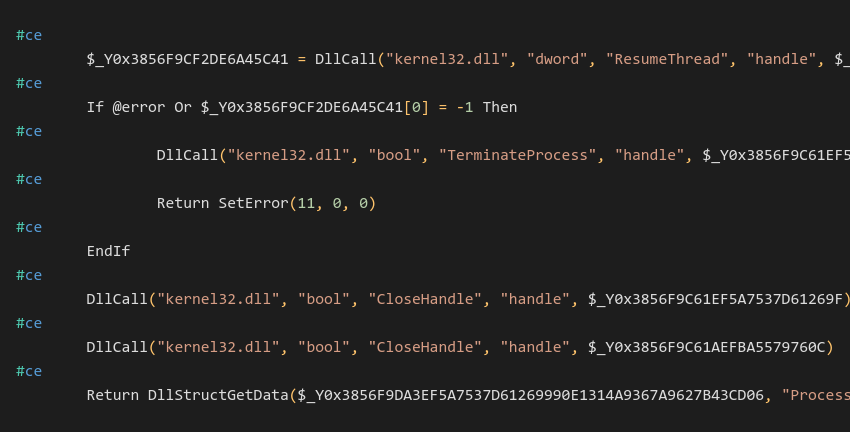
AutoIt script
The whole execution is done via AutoIt script which is passed as an argument to the AutoIt interpreter when malware launches. Code is hidden inside a large number of unused text lines. Malware places comments (#ce in this case) before each important line to determine what line should be interpreted as a code.
Payload Execution
The malware uses CryptoAPI to decrypt the final payload. It takes the decryption key from the configuration file and calculates its MD5 hash, which is used as a key inside a CryptDecrypt function that decrypts the malicious payload. After this, NeedleDropper spawns RegSvcs.exe in a suspended state and injects the payload via WriteProcessMemory, and resumes the suspended process which leads to the successful execution of the malware.
Infection Chain
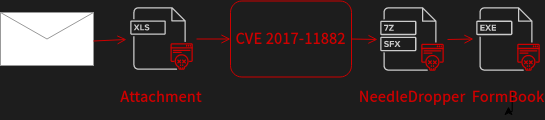
NeedleDropper doesn’t have one significant infection method; they often vary by sample. So far, we’ve noticed the dropper is primarily delivered via spam email attachments. As an email attachment, the malware is usually sent as an encrypted 7z file, or is part of a bigger infection chain starting with an Excel document, for example. However, NeedleDropper samples are also often shared via Discord or via OneDrive links. Due to various infection methods and different payloads, this malware seems to be a service to cybercriminals to hide their payloads.
The email above contains an excel document that takes advantage of the CVE 2017_11882 vulnerability to drop the vbc.exe (NeedleDropper) file inside the C:\Users\Public directory. Vbc.exe is executed and drops its content into a temp directory. In this particular example, NeedleDropper decrypts the FormBook payload, which is injected into RegSvcs process and executed.
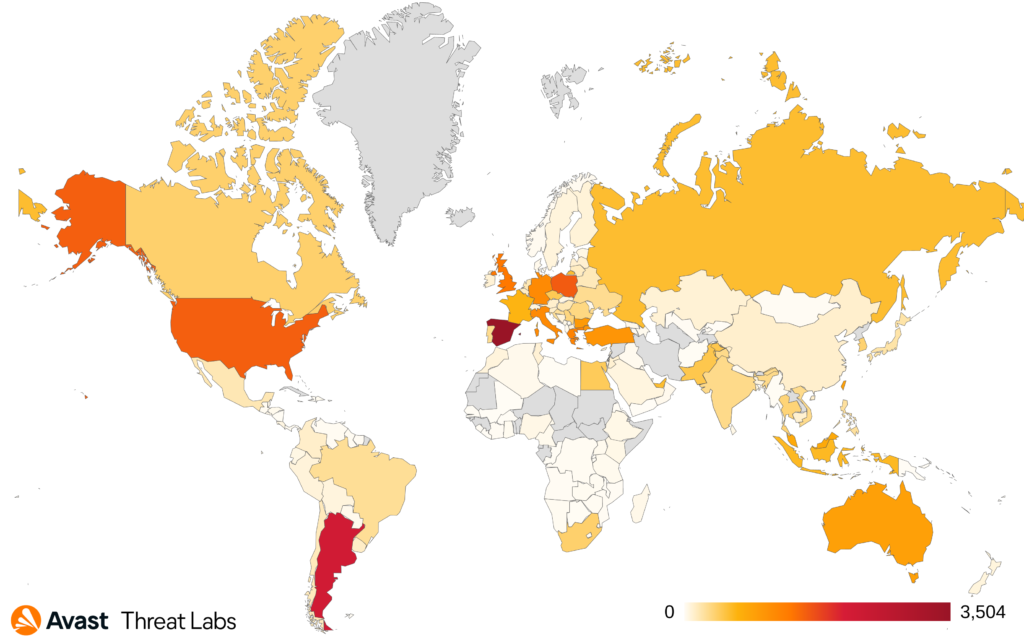
Distribution
The below images show the distribution of users Avast protected from NeedleDropper globally.
Conclusion
In this blog post, we described a new malware dropper which is often used by adversaries in their infection chain. Based on our current knowledge, we think that developers will modify the dropper in order to implement different methods which could avoid detection and stay attractive for others to use as a service. We predict NeedleDropper to start infecting more and more people in countries around the world with different, modernized payloads.
Indicators of Compromise
GitHub repository: Needle Dropper
| File name | SHA256 |
| NeedleDropper | 660eb5f2811753c24ecbd5c0e08c68d83d7eca1b2827ed90e2a5189ed61f3a5b |
| NeedleDropper | f7e52f120ab257e0d8e5021077b3370876be16469b76b6e0b6916486b3977bb3 |
| NeedleDropper | 06b02574925948a3f418ba2851f10585086a5f9b25d8f4e7de62dd52c6a56153 |
| NeedleDropper | e53e5e07b3165f507046c5992049a816bdd98969f10cc97a3d2bd010aea30b42 |
| NeedleDropper | 1b26f3213c07819cd61ed5e10b009ae5862cade4a3a403dcc6f6310485f6306b |
| Configuration file | 1d3078201c04bebc6595a2cc874530f1c2a5ff7201db4c8e43660808563c5a63 |
| Configuration file | dd7acb0d5e05d581148b614816f5450690f3fcc8ba4b3f00b5db1f3684570053 |
| Configuration file | 8713d873a8f4179a4079ea46a6ae45a538dc2f07cf7b09f28adc25eec45dc873 |
| Spam email | 01534a0f3e104b7cbafeeeaac3a0f0bf9d01e017c8a63964d81d0a30baee2916 |
This article is based on research made by Jan Blažek during work on his bachelor’s thesis.