TL;DR: Avast is starting the research project “Purple Dome” around the problem of file-less malware and complex attacks using Living Of the Land (LOLBins/LOLScripts) techniques. For this, we will simulate lots of things: Networks, attackers, defense systems.
Attacks on computer systems are constantly evolving. To be more flexible human operators sometimes get involved in the attacks. This is especially common for high value targets. As the human operator can use normal tools already installed on the target system, this can result in so-called “file less” malware.
These kinds of attacks started years ago. Malware-infected computers were connected together as botnets which the attackers could control remotely from their Command and Control Servers (C&C) . That was 95% malware and 5% human creativity. Currently we have hybrid attacks (like Trickbot) that automatically infect systems and perform their scripted attacks.
If those systems “look attractive” (i.e. larger companies with lots of money, valuable data that can be stolen for blackmail, broken backup systems that make ransomware attacks more effective) an operator gets involved to fully own the target for higher ransom. Those botnet operators cannot only use the features embedded in the malware files but also abuse basic OS features as well as admin tools and scripts that have already been installed by the companies’ admins for system management. This is called living off the land (LOL as in LOLBINs). The idea is to leave fewer traces and more deeply infect the systems. Some examples include hacking the Active Directory server and deleting the backups before encrypting the files for ransom.
This is nothing new, but the vector of this change is visible, and will continue. Security companies have already been adapting to these new attack vectors.
To get researchers involved to solve this problem, Avast is creating the spin-off project from the Avast AI research team, “Purple Dome”.
The project this blogpost is about
Purple Dome aims to create a simulated computer network based on a config file. We will pre-install some sensors. Then we will spin up some attacker virtual machines and have them run attacks on those systems. The take-away for us will be logs and information containing the traces the attackers left. Those logs can be analysed using machine learning techniques and this intelligence can later be turned into improved end user products.
The main benefits of this project will be that we can be flexible everywhere and we can:
- Try different target network setups
- Try different sensors and features
- Run different attack scenarios – including different TTPs
- Try different machine learning (ML) algorithms on the heaps of logs we will get
Everything must be fully automated. Because ML needs lots of input to identify the red flags that mark the attack.
If we are able to simulate different scenarios such as a company network, a small and medium business (SMB), a university network, a home office or a IoT connected smart home, we can better understand how attacks on them look.
Details
To automatically set up the target systems, we are using Vagrant (https://www.vagrantup.com). It is a very common automation system for Virtual Machines (VMs). It can create, run, stop and destroy those simulated computer systems. The whole system is quite flexible. For development and debugging we need this local version based on Vagrant. Beyond this there is also a cloud variant ready for large-scale deployment.
No matter which we are using: the system config can be tuned to simulate any target system you can imagine such as a normal home with different network connected devices or an office environment. After the configuration is written, we just execute our toolchain and see our simulated network come to life, just in time to be attacked (see next step).
Attacks are also defined in the configuration. They are typical attacks a hacker would make. The attacks are either run from a Caldera attacker (the “Scalable Automated Adversary Emulation Platform” https://github.com/mitre/caldera) or from a Kali Linux environment (https://www.kali.org/) both of which simulate an adversary with the tools they typically have. Both of these give plenty of options to attack the simulated network.
All these steps are necessary to harvest the results: the observations we do on the simulated systems. This will answer questions such as: how will those attacks look for sensors running on those systems, when can we be sure an attack is currently happening and start our countermeasures (like re-configuring the firewall to block the attacker)?
For these questions about sensors and decision logic, this is exactly the part where we will experiment, and we hope to be able to publish interesting results soon.
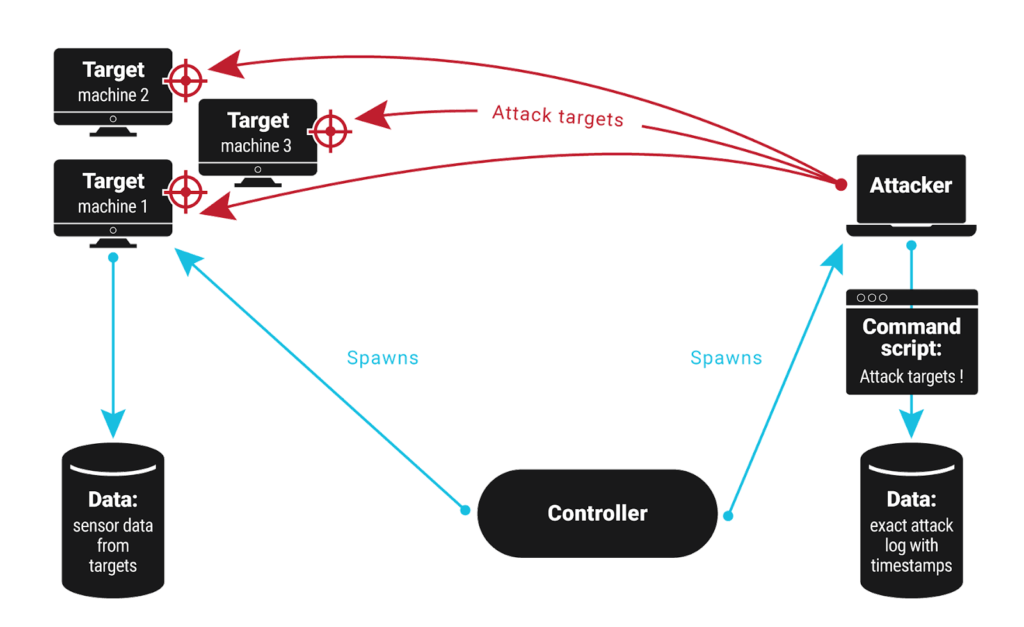
Below we show how this will work.
- We start with a controller:
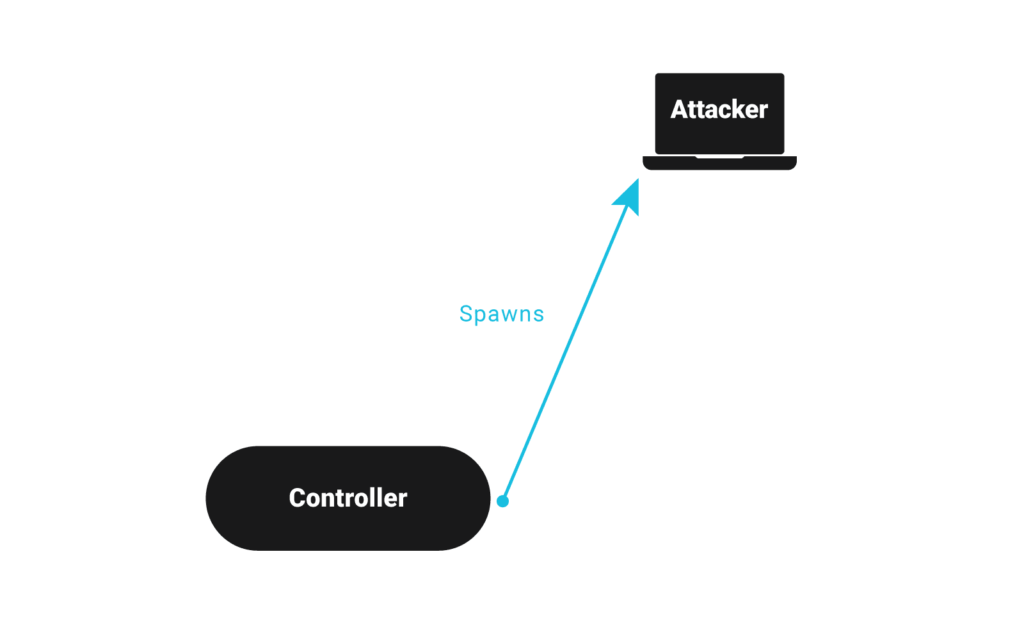
- The controller then starts the attacker
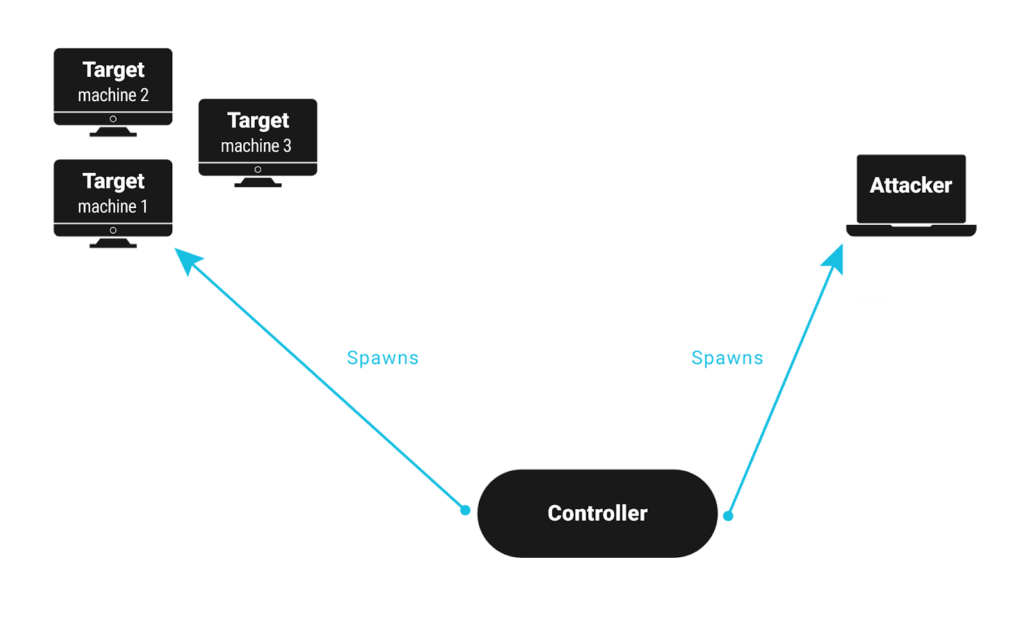
- Next, the controller starts targets
- The controller directs the attacker against the targets
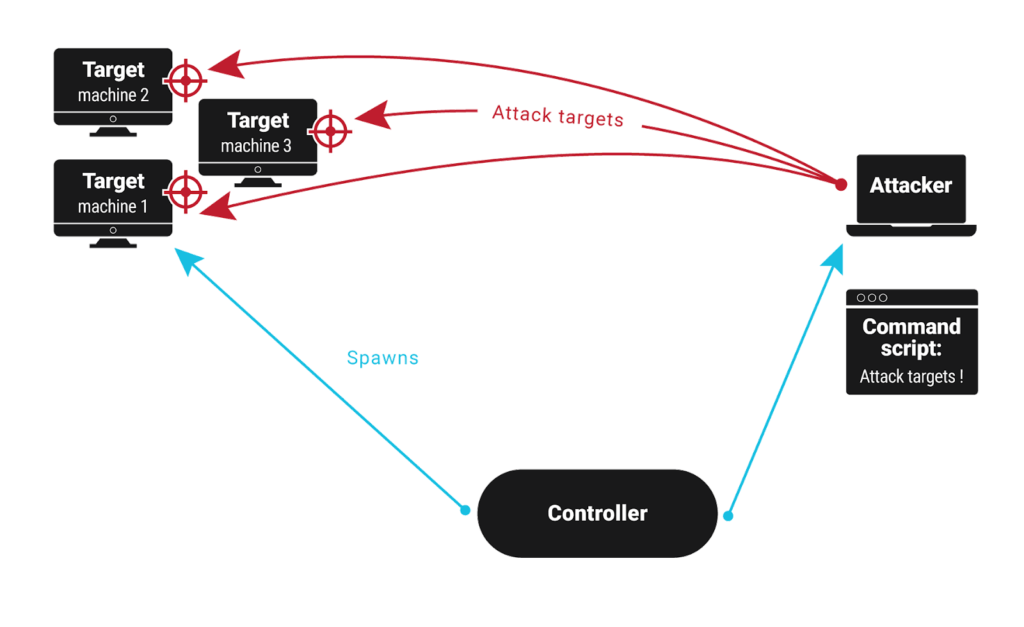
- Data is collected from the attacker and targets
- The data from the attacker and targets is used for machine learning (ML)
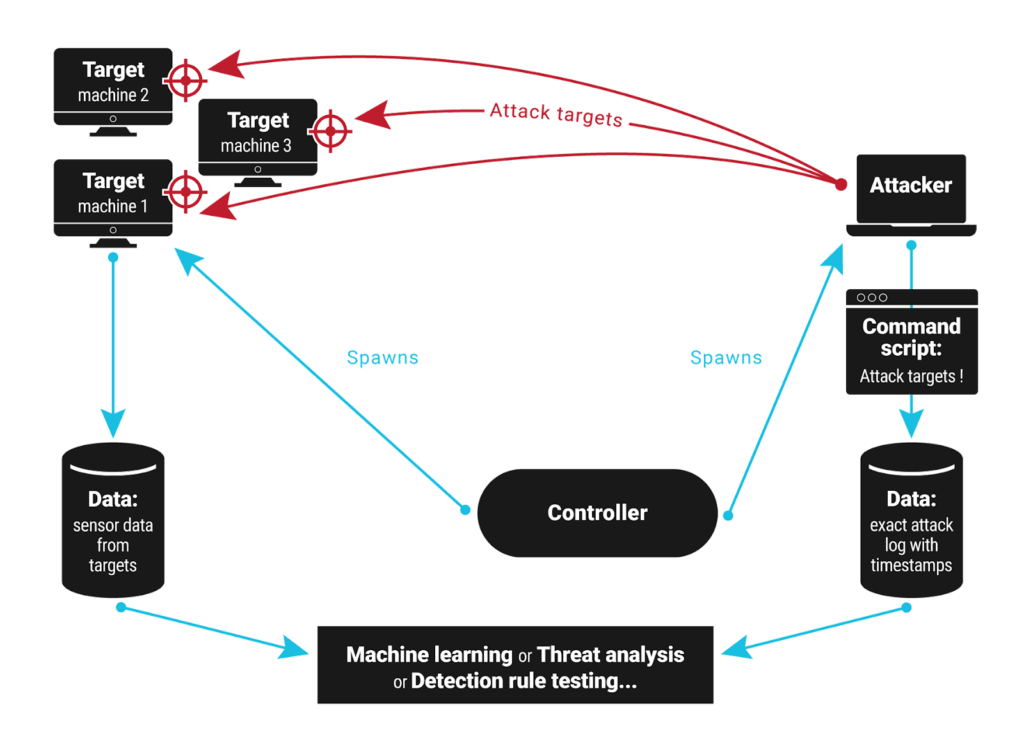
Outcomes
Other projects by this research department are already Open Source or are developed in cooperation with universities (https://github.com/CTUAvastLab/Mill.jl). I hope, we will see this tool in the public soon. But first, the code structure will have to stabilize a bit more.
Conclusion
In this posting, we’re announcing the beginning of Purple Dome. We will be following up this post with more information on how others in the research community can participate, and, eventually, we will share the results of our research.
For science !
Thorsten Sick




