On January 25, 2022, a victim of a ransomware attack reached out to us for help. The extension of the encrypted files and the ransom note indicated the TargetCompany ransomware (not related to Target the store), which can be decrypted under certain circumstances.
Modus Operandi of the TargetCompany Ransomware
When executed, the ransomware does some actions to ease its own malicious work:
- Assigns the
SeTakeOwnershipPrivilegeandSeDebugPrivilegefor its process - Deletes special file execution options for tools like
vssadmin.exe,wmic.exe,wbadmin.exe,bcdedit.exe,powershell.exe,diskshadow.exe,net.exeandtaskkil.exe - Removes shadow copies on all drives using this command:
%windir%\sysnative\vssadmin.exe delete shadows /all /quiet - Reconfigures boot options:
bcdedit /set {current} bootstatuspolicy ignoreallfailuresbcdedit /set {current} recoveryenabled no - Kills some processes that may hold open valuable files, such as databases:
| List of processes killed by the TargetCompany ransomware | |
| MsDtsSrvr.exe | ntdbsmgr.exe |
| ReportingServecesService.exe | oracle.exe |
| fdhost.exe | sqlserv.exe |
| fdlauncher.exe | sqlservr.exe |
| msmdsrv.exe | sqlwrite |
| mysql.exe | |
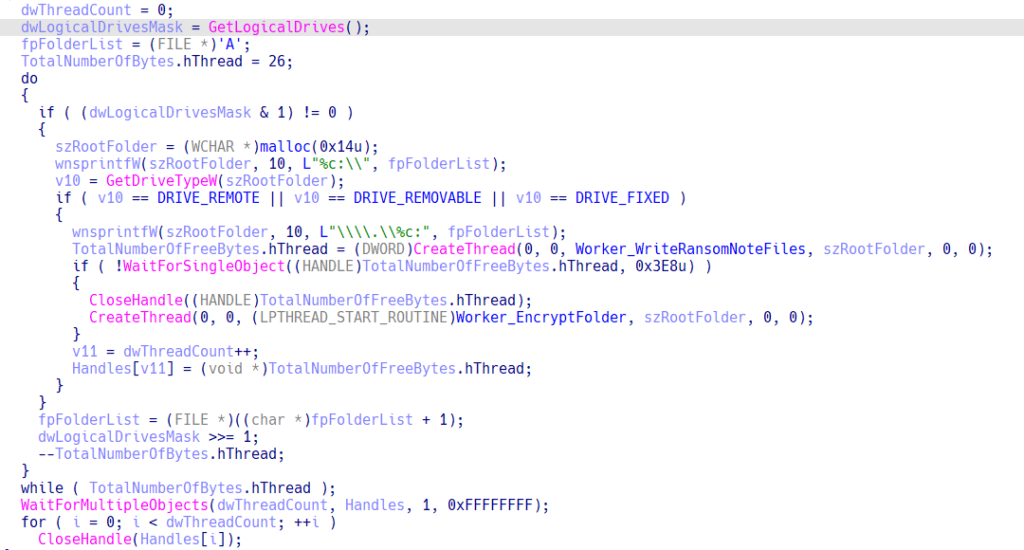
After these preparations, the ransomware gets the mask of all logical drives in the system using the GetLogicalDrives() Win32 API. Each drive is checked for the drive type by GetDriveType(). If that drive is valid (fixed, removable or network), the encryption of the drive proceeds. First, every drive is populated with the ransom note file (named RECOVERY INFORMATION.txt). When this task is complete, the actual encryption begins.
Exceptions
To keep the infected PC working, TargetCompany avoids encrypting certain folders and file types:
| List of folders avoided by the TargetCompany ransomware | |||
| msocache | boot | Microsoft Security Client | Microsoft MPI |
| $windows.~ws | $windows.~bt | Internet Explorer | Windows Kits |
| system volume information | mozilla | Reference | Microsoft.NET |
| intel | boot | Assemblies | Windows Mail |
| appdata | windows.old | Windows Defender | Microsoft Security Client |
| perflogs | Windows | Microsoft ASP.NET | Package Store |
| programdata application data | WindowsPowerShell | Core Runtime | Microsoft Analysis Services |
| tor browser | Windows NT | Package | Windows Portable Devices |
| Windows | Store | Windows Photo Viewer | |
| Common Files | Microsoft Help Viewer | Windows Sidebar | |
| List of file types avoided by the TargetCompany ransomware | |||||
| .386 | .cpl | .exe | .key | .msstyles | .rtp |
| .adv | .cur | .hlp | .lnk | .msu | .scr |
| .ani | .deskthemepack | .hta | .lock | .nls | .shs |
| .bat | .diagcfg | .icl | .mod | .nomedia | .spl |
| .cab | .diagpkg | .icns | .mpa | .ocx | .sys |
| .cmd | .diangcab | .ico | .msc | .prf | .theme |
| .com | .dll | .ics | .msi | .ps1 | .themepack |
| .drv | .idx | .msp | .rom | .wpx | |
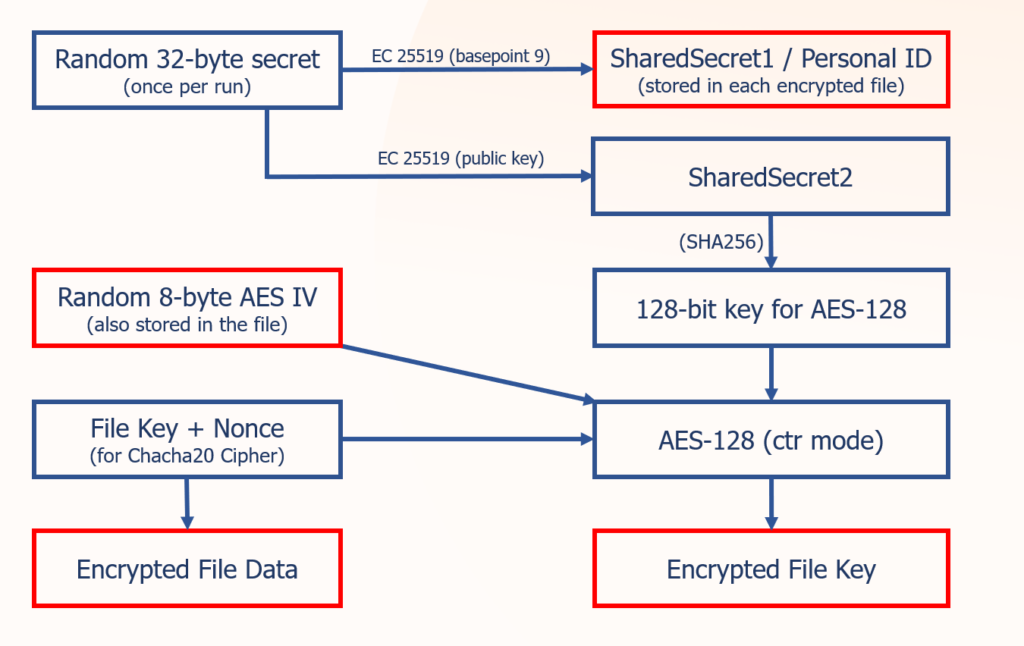
The ransomware generates an encryption key for each file (0x28 bytes). This key splits into Chacha20 encryption key (0x20 bytes) and n-once (0x08) bytes. After the file is encrypted, the key is protected by a combination of Curve25519 elliptic curve + AES-128 and appended to the end of the file. The scheme below illustrates the file encryption. Red-marked parts show the values that are saved into the file tail after the file data is encrypted:
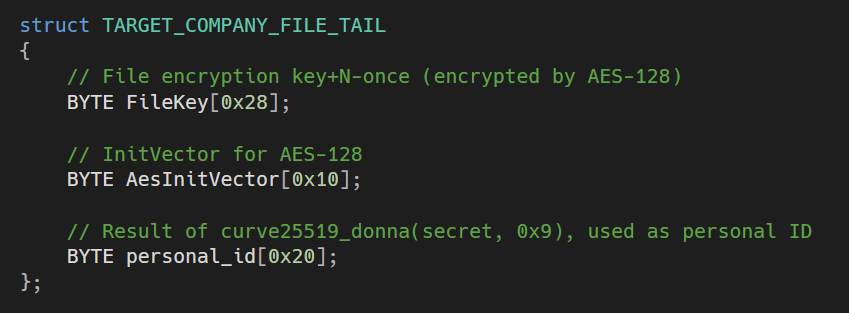
The exact structure of the file tail, appended to the end of each encrypted file, is shown as a C-style structure:
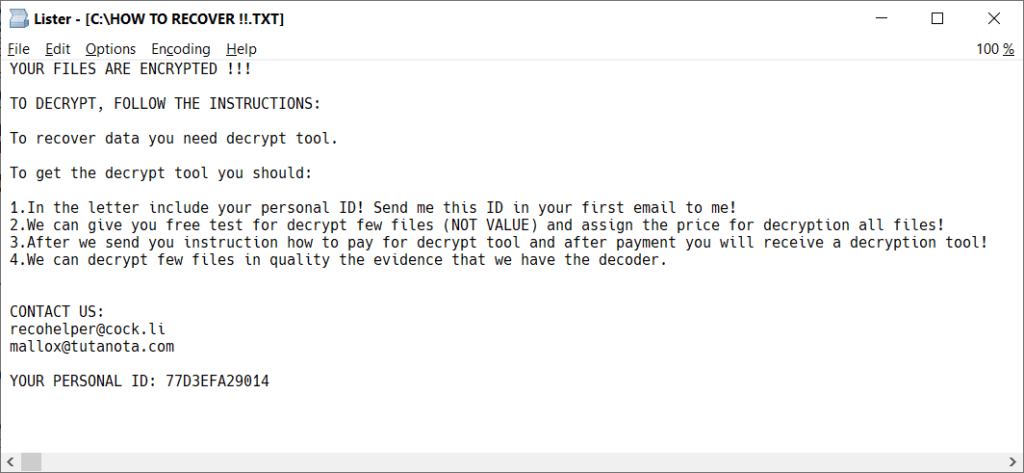
Every folder with an encrypted file contains the ransom note file. A copy of the ransom note is also saved into c:\HOW TO RECOVER !!.TXT
The personal ID, mentioned in the file, is the first six bytes of the personal_id, stored in each encrypted file.
How to use the Avast decryptor to recover files
To decrypt your files, please, follow these steps:
- Download the free Avast decryptor. Choose a build that corresponds with your Windows installation. The 64-bit version is significantly faster and most of today’s Windows installations are 64-bit.
- If you have 64-bit Windows, choose the 64-bit build.
- If you have 32-bit Windows, choose the 32-bit build.
- Simply run the executable file. It starts in the form of a wizard, which leads you through the configuration of the decryption process.
- On the initial page, you can read the license information, if you want, but you really only need to click “Next”
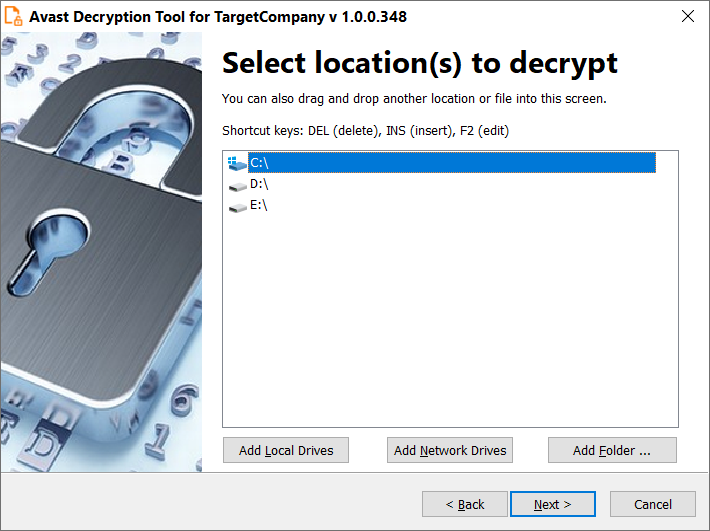
- On the next page, select the list of locations which you want to be searched and decrypted. By default, it contains a list of all local drives:
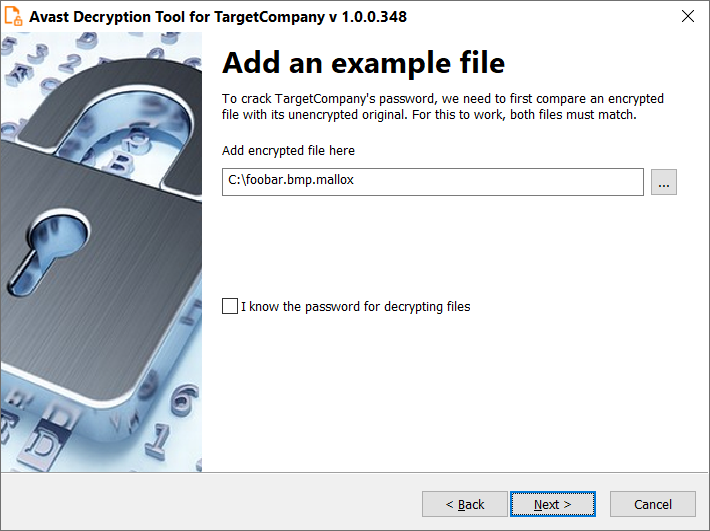
- On the third page, you need to enter the name of a file encrypted by the TargetCompany ransomware. In case you have an encryption password created by a previous run of the decryptor, you can select the “I know the password for decrypting files” option:
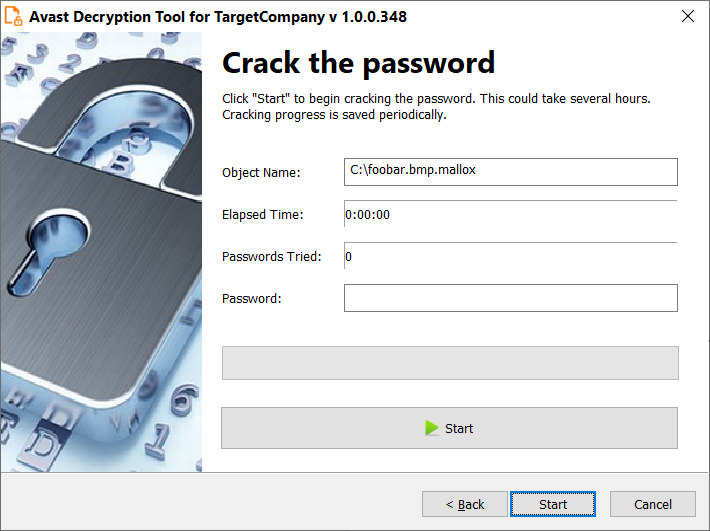
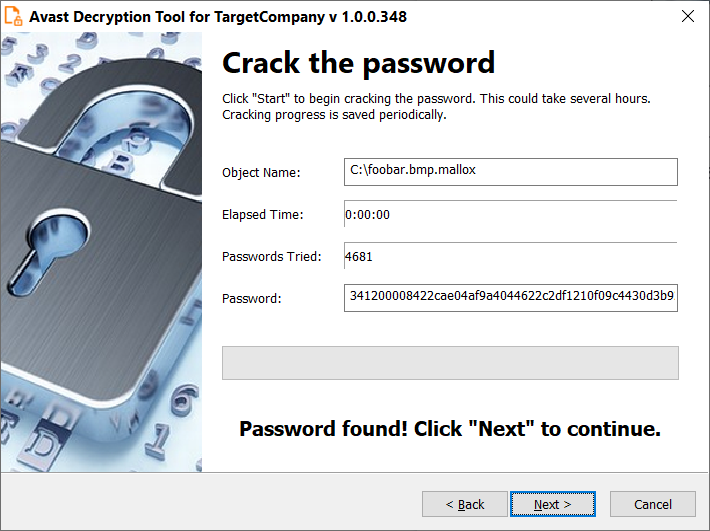
- The next page is where the password cracking process takes place. Click “Start” when you are ready to start the process. During password cracking, all your available processor cores will spend most of their computing power to find the decryption password. The cracking process may take a large amount of time, up to tens of hours. The decryptor periodically saves the progress and if you interrupt it and restart the decryptor later, it offers you an option to resume the previously started cracking process. Password cracking is only needed once per PC – no need to do it again for each file.
- When the password is found, you can proceed to the decryption of files on your PC by clicking “
Next”.
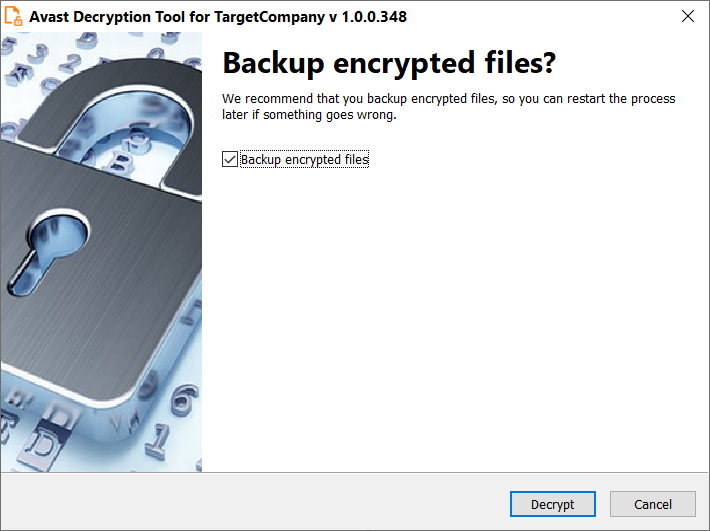
- On the final wizard page, you can opt-in whether you want to backup encrypted files. These backups may help if anything goes wrong during the decryption process. This option is turned on by default, which we recommend. After clicking “
Decrypt”, the decryption process begins. Let the decryptor work and wait until it finishes.