Avast Releases Decryptor for the Prometheus Ransomware. Prometheus is a ransomware strain written in C# that inherited a lot of code from an older strain called Thanos.
Skip to how to use the Prometheus ransomware decryptor.
How Prometheus Works
Prometheus tries to thwart malware analysis by killing various processes like packet sniffing, debugging or tools for inspecting PE files. Then, it generates a random password that is used during the Salsa20 encryption.
Prometheus looks for available local drives to encrypt files that have one of the following extensions:
db dbf accdb dbx mdb mdf epf ndf ldf 1cd sdf nsf fp7 cat log dat txt jpeg gif jpg png php cs cpp rar zip html htm xlsx xls avi mp4 ppt doc docx sxi sxw odt hwp tar bz2 mkv eml msg ost pst edb sql odb myd php java cpp pas asm key pfx pem p12 csr gpg aes vsd odg raw nef svg psd vmx vmdk vdi lay6 sqlite3 sqlitedb java class mpeg djvu tiff backup pdf cert docm xlsm dwg bak qbw nd tlg lgb pptx mov xdw ods wav mp3 aiff flac m4a csv sql ora dtsx rdl dim mrimg qbb rtf 7z
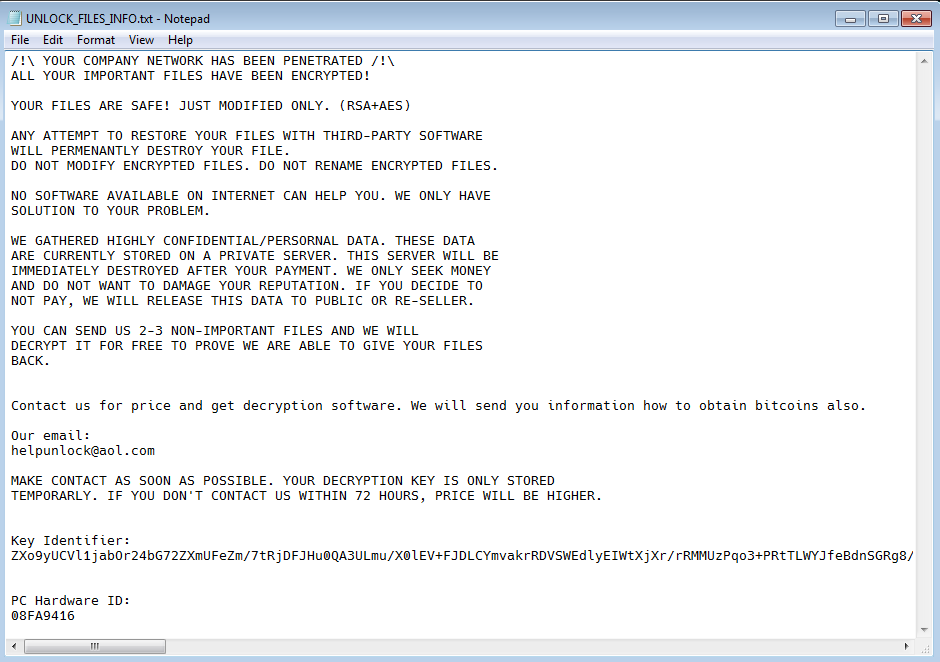
Encrypted files are given a new extension .[ID-<PC-ID>].unlock. After the encryption process is completed, Notepad is executed with a ransom note from the file UNLOCK_FILES_INFO.txt informing victims on how to pay the ransom if they want to decrypt their files.
How to use the Avast decryptor to decrypt files encrypted by Prometheus Ransomware
To decrypt your files, follow these steps:
- Download the free Avast decryptor.
- Run the executable file. It starts in the form of a wizard, which leads you through the configuration of the decryption process.
- On the initial page, you can read the license information, if you want, but you really only need to click “
Next”.
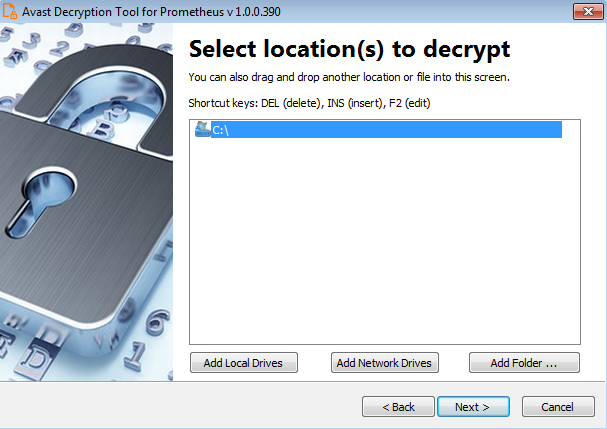
- On the next page, select the list of locations you want to be searched and decrypted. By default, it contains a list of all local drives:
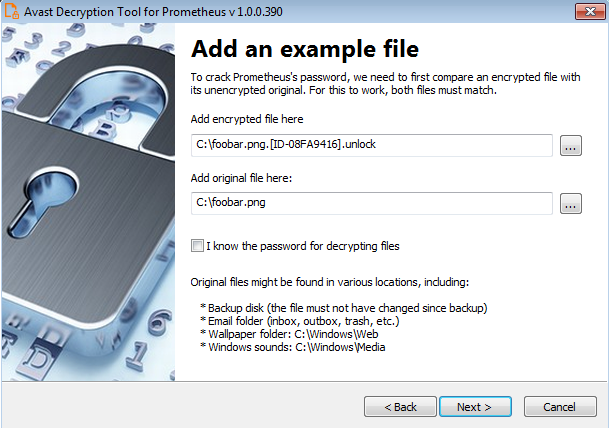
- On the third page, you need to provide a file in its original form and encrypted by the Prometheus ransomware. Enter both names of the files. In case you have an encryption password created by a previous run of the decryptor, you can select the “
I know the password for decrypting files” option:
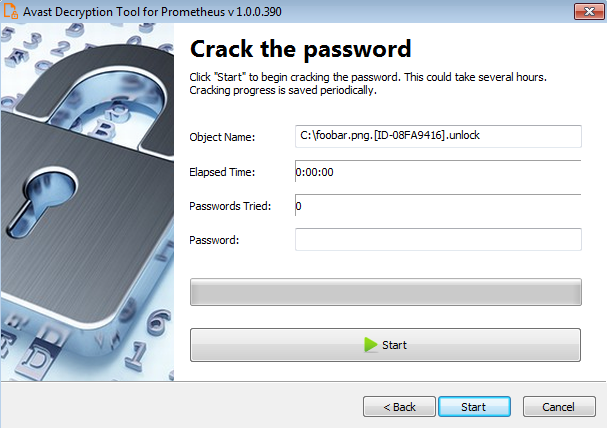
- The next page is where the password cracking process takes place. Click “
Start” when you are ready to start the process. During the password cracking process, all your available processor cores will spend most of their computing power to find the decryption password. The cracking process may take a large amount of time, up to tens of hours. The decryptor periodically saves the progress and if you interrupt it and restart the decryptor later, it offers you the option to resume the previously started cracking process. Password cracking is only needed once per PC – no need to do it again for each file.
- When the password is found, you can proceed to decrypt all encrypted files on your PC by clicking “
Next”.
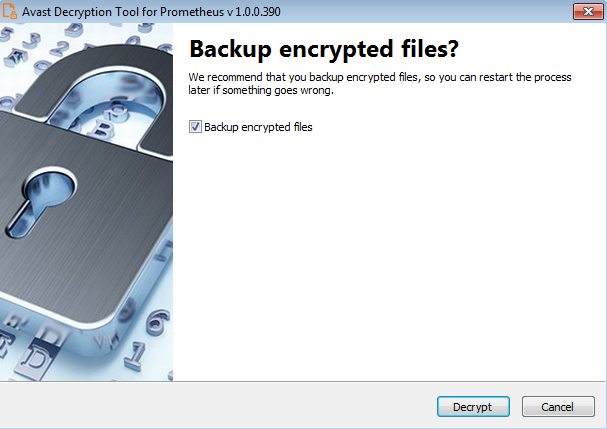
- On the final page, you can opt-in to backup encrypted files. These backups may help if anything goes wrong during the decryption process. This option is turned on by default, which we recommend. After clicking “
Decrypt”, the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
IOCs
| SHA256 | File Extension |
742bc4e78c36518f1516ece60b948774990635d91d314178a7eae79d2bfc23b0 | .[ID-<HARDWARE_ID>].unlock |