Researchers from Avast have discovered a flaw in the cryptographic schema of the DoNex ransomware and its predecessors. In cooperation with law enforcement organizations, we have been silently providing the decryptor to DoNex ransomware victims since March 2024. The cryptographic weakness was made public at Recon 2024 and therefore we have no reason to keep this secret anymore.
DoNex and its Brothers
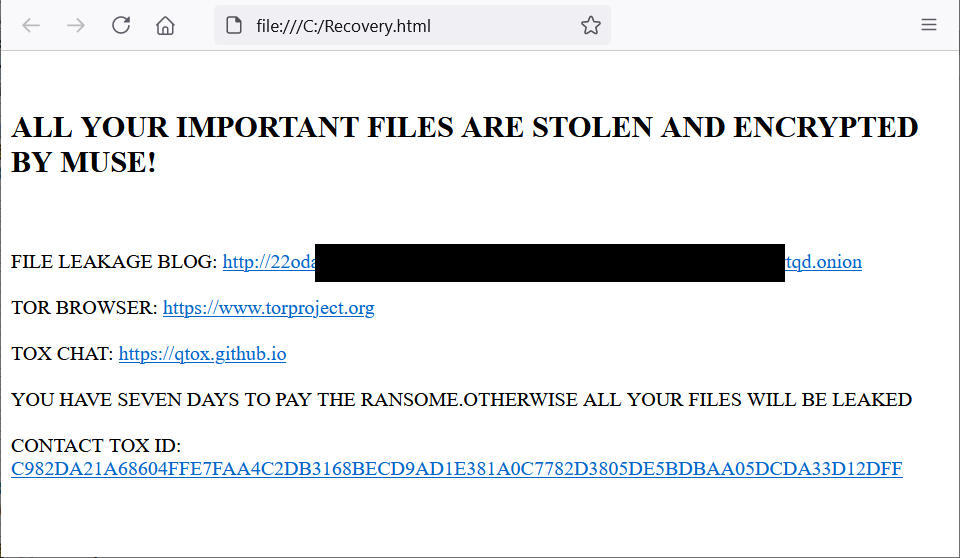
The DoNex ransomware has been rebranded several times. The first brand, called Muse, appeared in April 2022. Multiple evolutions followed, resulting in the final version of the ransomware, called DoNex. Since April 2024, DoNex seems to have stopped its evolution, as we have not detected any new samples since. Additionally, the TOR site of the ransomware has been down since that point. The following is a brief history of DoNex.
| Apr 2022 | The first sample of Muse ransomware |
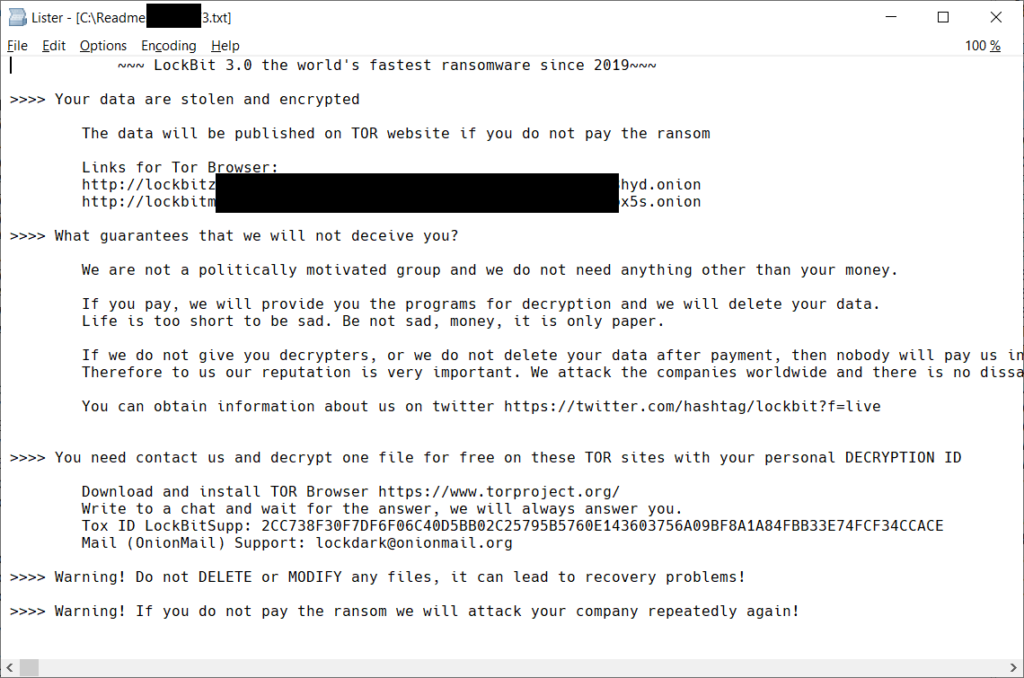
| Nov 2022 | Rebrand to fake LockBit 3.0 |
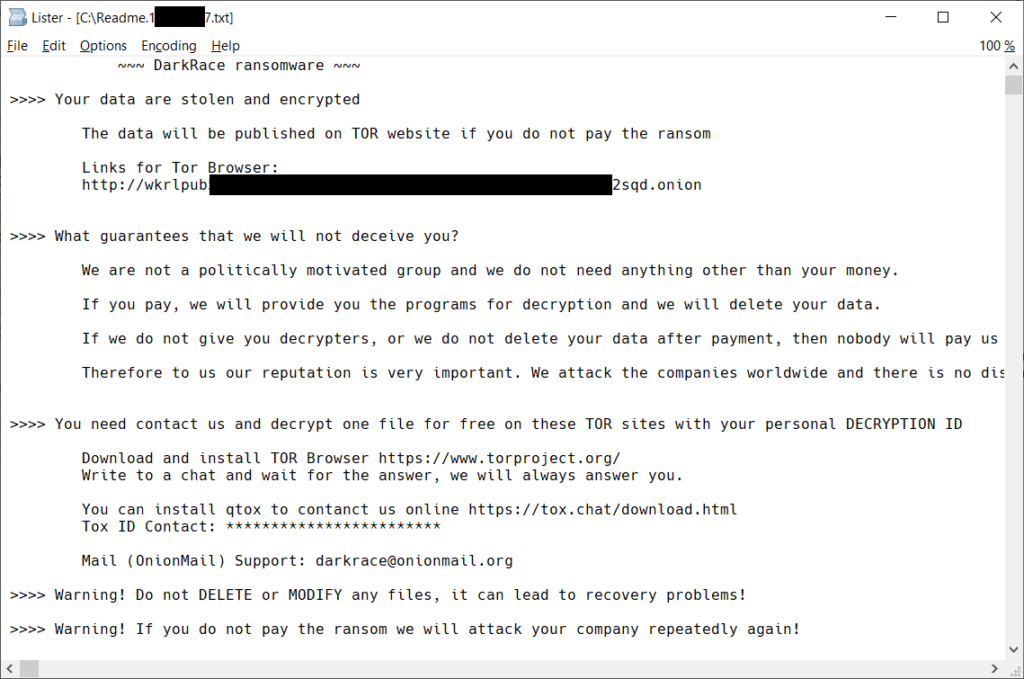
| May 2023 | Rebrand to DarkRace |
| Mar 2024 | Rebrand to DoNex |
All brands of the DoNex ransomware are supported by the decryptor.
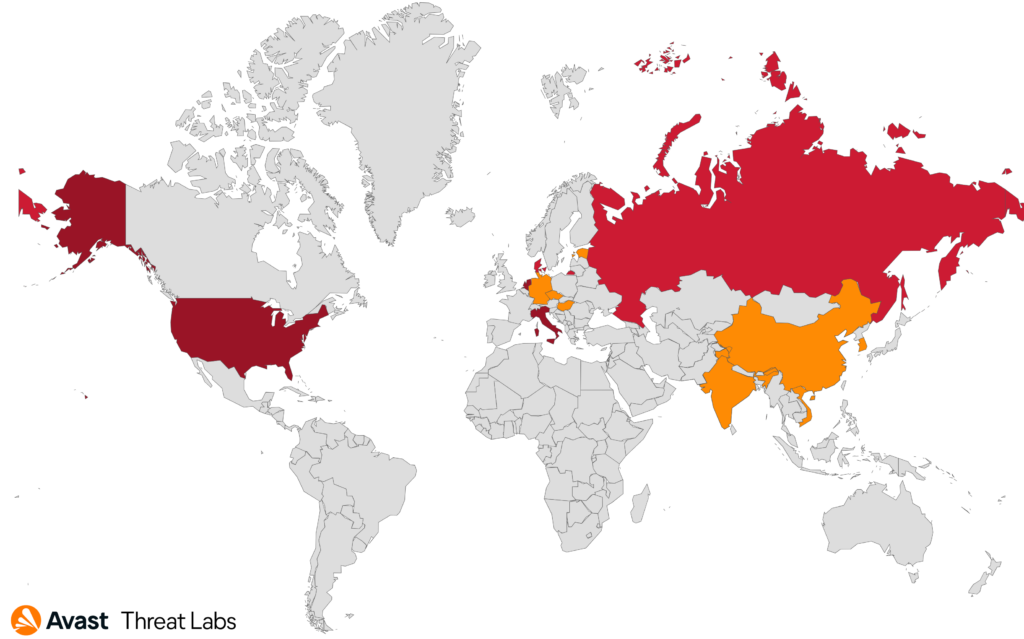
DoNex uses targeted attacks on its victims and it was most active in the US, Italy, and the Netherlands based on our telemetry.
Ransomware Encryption Schema
During the ransomware execution, an encryption key is generated by CryptGenRandom() function. This key is then used to initialize ChaCha20 symmetric key and subsequently to encrypt files. After a file is encrypted, the symmetric file key is encrypted by RSA-4096 and appended to the end of the file. The files are picked by their extension, and file extensions are listed in the ransomware XML config.
For small files (up to 1 MB), the entire file is encrypted. For files with size greater than 1 MB, intermittent encryption is used – the file is split into blocks and those blocks are encrypted separately.
Ransomware Configuration
Samples of the DoNex ransomware, and its previous versions, contain XOR-encrypted configuration, which contains settings of whitelisted extensions, whitelisted files, services to kill, and other encryption-related data. The following snippet shows a part of such configuration:
<?xml version='1.0' encoding='UTF-8'?>
<root>
<white_extens>
386;adv;ani;bat;bin;cab;cmd;com;cpl;cur;deskthemepack;diagcab;diagcfg;
diagpkg;dll;drv;exe;hlp;icl;icns;ico;ics;idx;lnk;mod;mpa;msc;msp;msstyles;
msu;nls;nomedia;ocx;prf;ps1;rom;rtp;scr;shs;spl;sys;theme;themepack;wpx;
lock;key;hta;msi;pdb;search-ms
</white_extens>
<white_files>
bootmgr;autorun.inf;boot.ini;bootfont.bin;bootsect.bak;desktop.ini;iconcache.db;
ntldr;ntuser.dat;ntuser.dat.log;ntuser.ini;thumbs.db;GDIPFONTCACHEV1.DAT;d3d9caps.dat
</white_files>
<white_folders>
$recycle.bin;config.msi;$windows.~bt;$windows.~ws;windows;boot;program files;
program files (x86);programdata;system volume information;tor browser;windows.old;
intel;msocache;perflogs;x64dbg;public;all users;default;microsoft;appdata
</white_folders>
<kill_keep>
sql;oracle;mysq;chrome;veeam;firefox;excel;msaccess;onenote;outlook;powerpnt;winword;wuauclt
</kill_keep>
<services>
vss;sql;svc$;memtas;mepocs;msexchange;sophos;veeam;backup;GxVss;GxBlr;GxFWD;GxCVD;GxCIMgr
</services>
<black_db>
ldf;mdf
</black_db>
<encryption_thread>
30
</encryption_thread>
...Code language: HTML, XML (xml)How do I know if I have been attacked by DoNex ransomware?
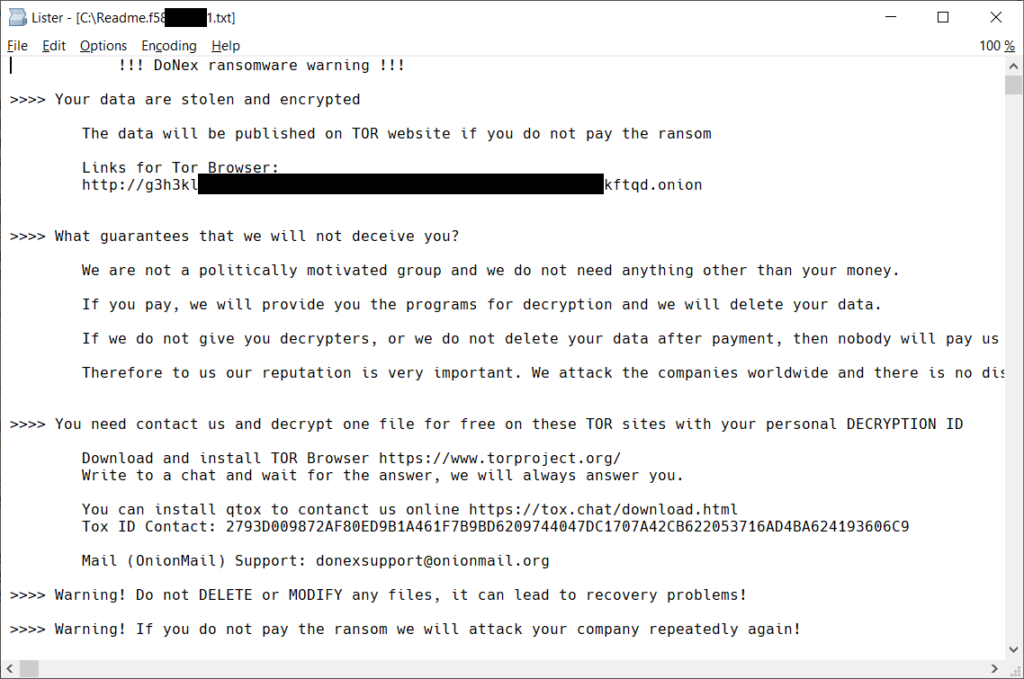
The simplest way to identify that you have been attacked by the DoNex ransomware is the ransom note. Different brands of the DoNex ransomware produce a different ransom note, but every version contains a note. That said, the ransom note layout of the Fake LockBit, DarkRace and DoNex ransomwares are very similar. Below you can see examples of each.
How to use the DoNex ransomware decryptor
1. Download the decryptor here.
2. Run the executable file, preferably as an administrator. It starts as a wizard, leading you through the configuration of the decryption process.
3. On the initial page, we have a link to the license information. Click the Next button when you are ready to start.
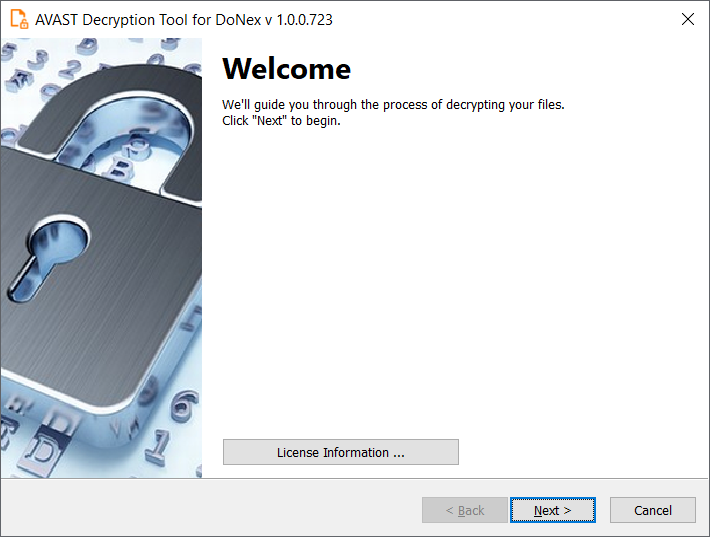
4. On the next page, the user is asked to provide a list of locations (drives, folders, files) that are to be decrypted. By default, it has a list of all local disk drives.
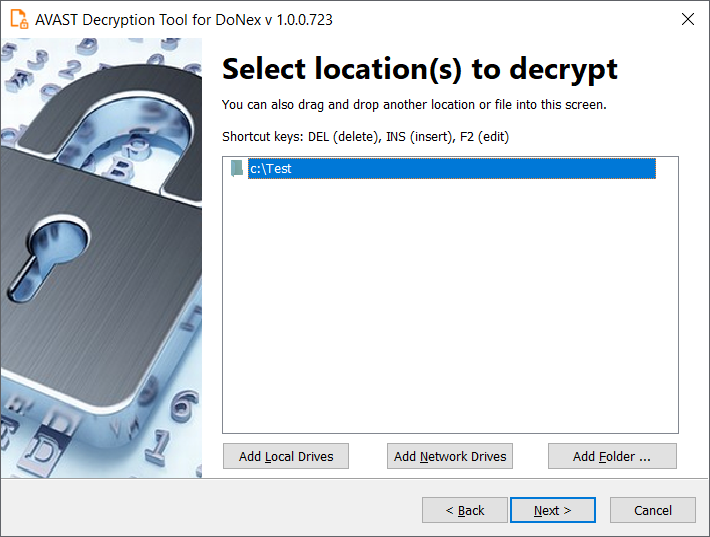
5. On the following page, you need to supply an example of a file in its original form and then one encrypted by any brand of the DoNex ransomware. Type both names of the files. You can also drag & drop files from Windows Explorer to the wizard page. It is extremely important to pick a pair of files that are as big as you can find. The largest file size that is decryptable by the tool equals to the file size of the encrypted file in the pair.
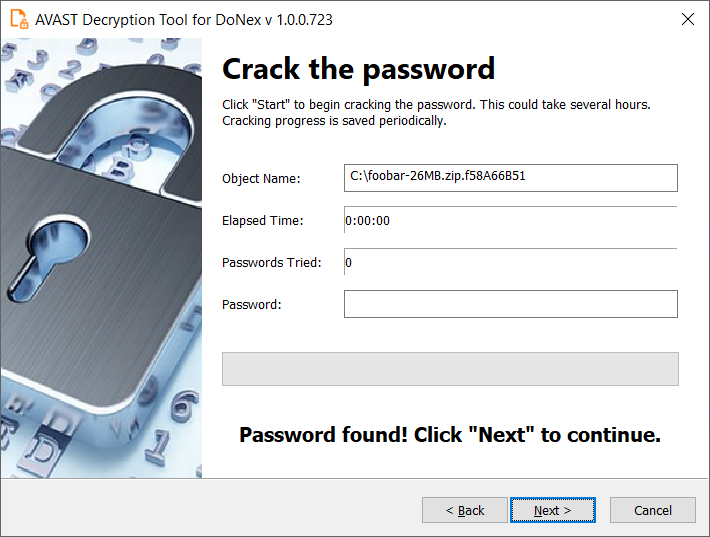
6. The next page is where the password cracking process takes place. Click Start when you are ready to begin. This process usually only takes a second, but requires a large amount of system memory. This is why we strongly recommend using the 64-bit version of the decryption tool.
Once the password is found, you can continue to decrypt all the encrypted files on your PC by clicking Next.
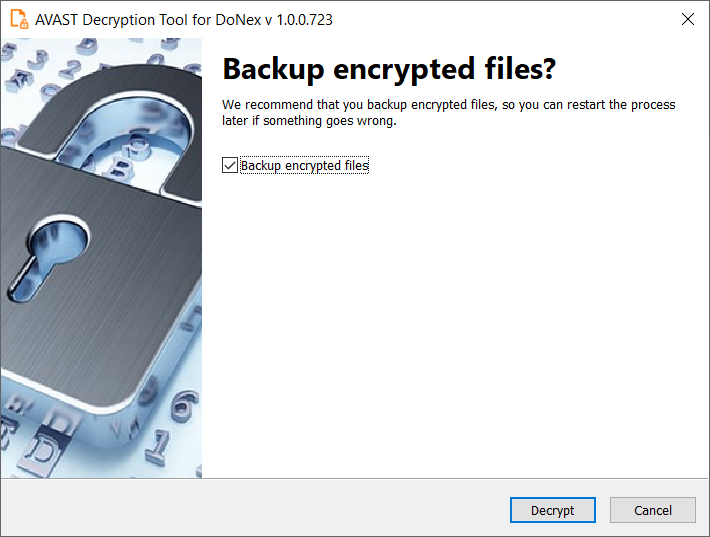
7. On the final page, you can opt-in to back up your encrypted files. These backups may help if anything goes wrong during the decryption process. This choice is selected by default, which we recommend. After clicking Decrypt the decryption process begins. Let the decryptor work and wait until it finishes decrypting all of your files.
Indicators of Compromise (IOCs)
| 9d5c4544bd06335c2ad2545b0d177218f84b77dd1834b22bf6a4cfe7e1de91fb | Muse |
| 04ed1a811b3594f55486a52ab81227089c178f5c73944a3a9665d7052c3b7df9 0ec61a80e61f56f460fc42e5d4f0accec2b04c8db98c28ed4534946214076f2a b9b4766d6b0e63f80d49e969fbd63ae90b0d1e487ef008b55c096bf46395d32e 2e397dcbcc630b492c01af9cb6033edd9c857e2881bead6956e43aefb16b6a21 91745d530a8304742b58890e798448de9fbe4ea0bc057f30ab0beb522b4bb688 2e1fd124f3e9fc238773e49bc971c882464a3686171d18ab2cd6c2859be138d1 | FakeLockBit 3.0 |
| 74b5e2d90daaf96657e4d3d800bb20bf189bb2cf487479ea0facaf6182e0d1d3 0e60d49a967599fab179f8c885d91db25016be996d66a4e00cbb197e5085efa4 | Dark Race |
| 0adde4246aaa9fb3964d1d6cf3c29b1b13074015b250eb8e5591339f92e1e3ca B32ae94b32bcc5724d706421f915b7f7730c4fb20b04f5ab0ca830dc88dcce4e 6d6134adfdf16c8ed9513aba40845b15bd314e085ef1d6bd20040afd42e36e40 | DoNex |




