Stunning 50% Surge in Blocked Attacks, Resulting in 1 Billion Monthly Blocks
Foreword
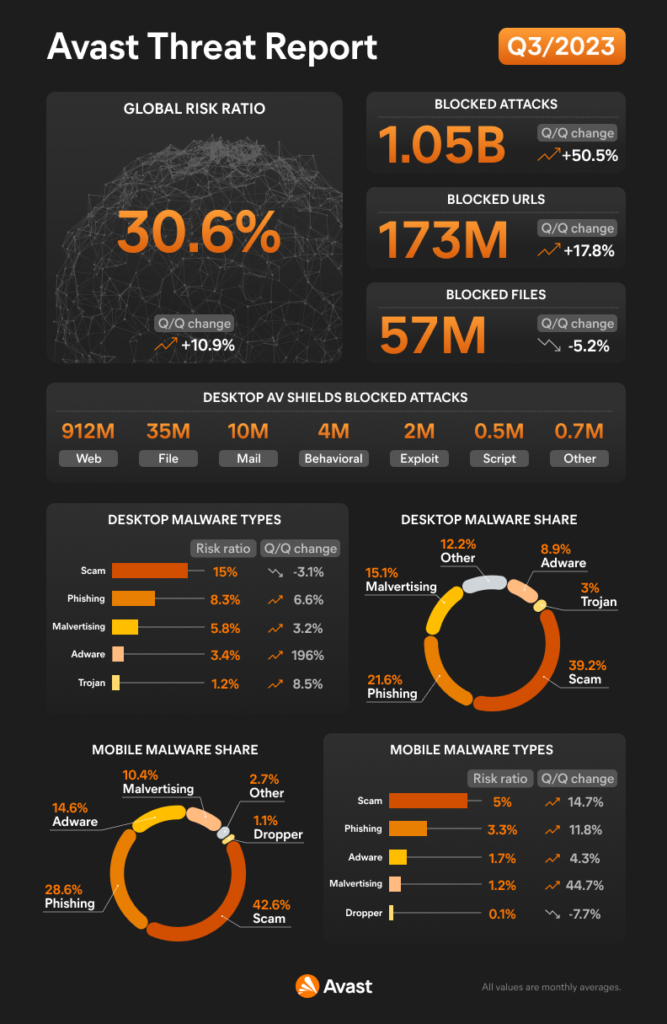
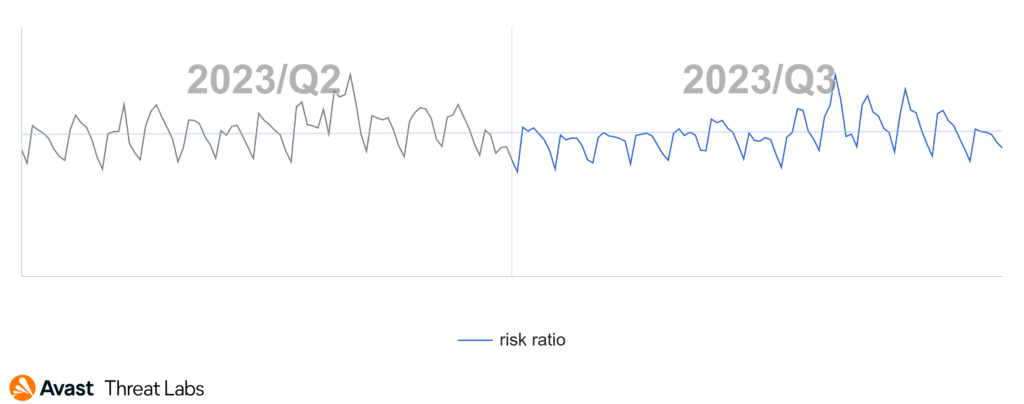
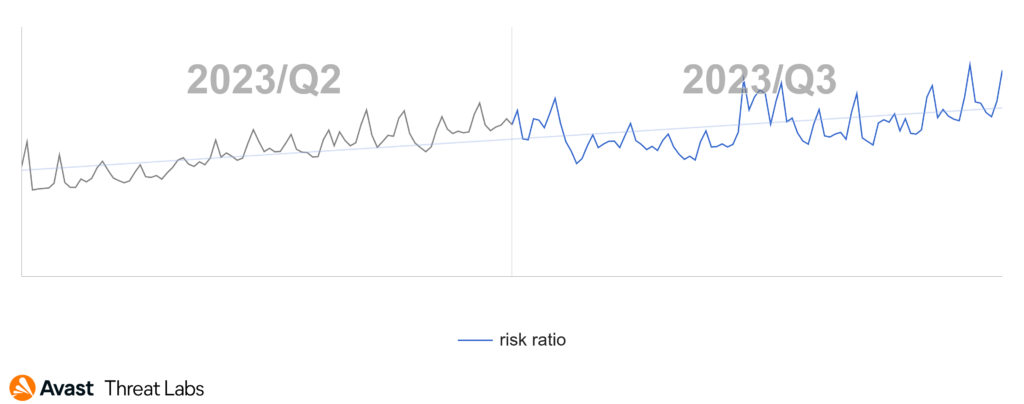
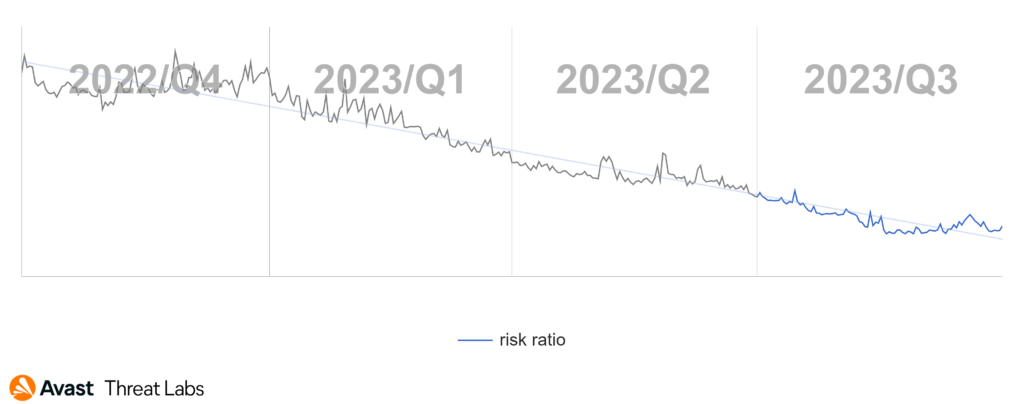
As we delve into the Q3/2023 Threat Report, it is evident that the past quarter was not an ordinary one. Typically, vacation time ushers in a decrease in online activity, offering a brief respite from cyber threats. This year, however, the digital landscape took an unexpected turn. Despite reduced online presence, our detection systems recorded a jaw-dropping 50% increase in unique blocked attacks, leading to new all-time highs. On average, we blocked over one billion unique malware attacks each month during Q3/2023. The surge was driven by a substantial rise in web-based threats, particularly social engineering, and malvertising. Consequently, the overall risk ratio, representing the risk of being targeted and protected by us, now exceeds 30%.
The adoption of AI by threat actors, particularly in deepfake financial scams, is accelerating. The nefarious use of deepfakes targeting TikTok users, often featuring public figures such as Elon Musk, has emerged as a growing concern. More on this can be found in our Featured story section.
Furthermore, the threat landscape was marked by a doubling of the adware threat level, indicating a significant escalation in adware. South America, Africa, Southeast Europe, and East Asia bore the brunt of this surge.
Apart from adware, there were significant developments in the realm of botnets. The FBI’s attempt to dismantle the Qakbot botnet led to a noticeable drop in activity. However, the operation does not appear to be entirely extinguished, as some associated threat actors have already begun to shift to alternative strains, such as DarkGate.
In addition, information stealers recorded a substantial increase in risk ratio, with Ukraine (44%), the United States (21%), and India (16%) experiencing the most significant spikes. AgentTesla dominated this landscape, while the once-notorious Raccoon Stealer seems to be losing its momentum and receding from the forefront.
Remote Access Trojans (RATs) also continue to be a growing trend. The increase of RATS, first observed in Q2/2023, continued in Q3/2023 primarily driven by the Remcos RAT and Warzone. Countries such as Portugal (148% increase), Poland (55%), and Slovakia (43%) have experienced a significant rise in attacks. The XWorm strain remains prolific, consistently releasing new versions and expanding its reach.
Furthermore, the emergence of a new vulnerability, CVE-2023-38831, in the popular WinRAR software caught the attention of threat actors, including APTs, RATs, and malware downloaders. Given the software’s widespread use, these exploits are likely to persist, emphasizing the importance of keeping software updated. For more on these vulnerabilities, delve into our Exploits section.
The domain of scams has undergone significant changes, with dating scams witnessing a 34% increase quarter-on-quarter. Belgium, Germany, Canada, and the United States are among the top targets for these scammers. To compound the challenge, our researchers uncovered a new threat, which we have named Love-GPT. This AI-driven tool assists threat actors in creating realistic personas, amplifying the success of their fraudulent activities.
Phishing attacks have also experienced a 14% quarterly increase, with threat actors innovatively utilizing IPFS (InterPlanetary File System) to bypass conventional defense mechanisms. Australia, in particular, saw a substantial surge in targeted email scams.
Finally, the mobile threat landscape remains dynamic, marked by espionage tactics. Spyware mimicking a missile warning application used in Israel emerged in response to escalating tensions between Israel and Palestine, with the aim of stealing victim data. Also, the introduction of Invisible Adware, with over two million downloads from the Google PlayStore, contributed to the rising risk of mobile adware. Brazil, India, and Argentina remain the top-affected countries. Also, the gap left by the takedown of FluBot in mobile banking trojans is gradually being filled. This quarter saw the detection of new and resurrected bankers, including Xenomorph, GoldDigger, and SpyNote. Turkey, Spain, and France continue to be the prime targets for attackers in this category. Popular messenger application mods, such as Telegram, Signal, and WhatsApp, continue to be exploited to serve spyware. Additionally, SpyLoans continues to spread on PlayStore, posing extortion threats to vulnerable victims.
In conclusion, Q3/2023 has unveiled an unprecedented level of cyber threats. The surge in threat activity during a season that typically sees reduced online presence is a cause for concern. As we move into the winter season, traditionally marked by higher threat levels, we are watchful to see if this trend continues to escalate.
Thank you for your continued trust in Avast. Stay safe and secure.
Jakub Křoustek, Malware Research Director
Methodology
This report is structured into two main sections: Desktop-related threats, where we describe our intelligence around attacks targeting the Windows, Linux, and Mac operating systems, with a specific emphasis on web-related threats, and Mobile-related threats, where we describe the attacks focusing on Android and iOS operating systems.
We use the term “risk ratio” in this report to denote the severity of specific threats. It is calculated as a monthly average of “Number of attacked users / Number of active users in a given country.” Unless stated otherwise, calculated risks are only available for countries with more than 10,000 active users per month.
A blocked attack is defined as a unique combination of the protected user and a blocked threat identifier within the specified period.
In this Threat Report, we started with a more fine-grained labelling of various Scam threat types, which resulted in a separate tracking of e.g., malvertising compared to the previous reports. Furthermore, we have included some more threat data sources to provide even better threat landscape visibility.
Featured Story: TikTok Finance Scams: An Escalating Threat Fueled by Artificial Intelligence
TikTok, known for its virality and rapidly circulating digital trends, has emerged as a fertile ground for financial scams, specifically those involving cryptocurrency. The platform’s wide reach, coupled with its appeal to younger audiences, presents an attractive prospect for malicious actors aiming to exploit unsuspecting users.
The scams operate under a facade of legitimacy, often initiated with a deepfake video of a reputable figure endorsing a cryptocurrency exchange. Users are enticed to sign up on the purported exchange using a promo code, which allegedly credits their account with a significant amount of bitcoin. However, upon attempting to withdraw these funds, the platform mandates a preliminary transfer of bitcoin to “verify” the user’s account. Unwittingly, victims who comply with this requirement find that not only is the promised bitcoin unattainable, but also any transferred funds to the platform are irretrievably lost to the cybercriminals orchestrating the scam.
At the heart of these scams is the illicit utilization of Artificial Intelligence (AI) to create deepfake videos. Notorious personalities such as Elon Musk, Mr. Beast, Sam Altman, Warren Buffet, Joe Rogan, Donald Trump, and Tucker Carlson are impersonated in fraudulent endorsements of cryptocurrency exchanges. These fabricated endorsements lure users with promises of substantial Bitcoin rewards, setting the stage for financial deception.
Samples of videos circulating on TikTok impersonating Elon Musk and Donald Trump
The malicious use of AI, particularly deepfake technology, underscores the escalating sophistication of cyber adversaries. By creating convincing counterfeit videos of reputable individuals, scammers successfully manipulate public trust. This exploitation not only exhibits a concerning trend of cyber threats on social media platforms but also exemplifies the potential of AI in augmenting the effectiveness of financial scams. Deepfake technology, once the domain of high-skilled individuals, is becoming increasingly accessible, making it all the more difficult to discern real endorsements from fabricated ones.
Initially confined to English-speaking audiences, these scams have transcended linguistic barriers, making inroads into non-English speaking regions. Recent manifestations of these scams have been observed in various languages including Spanish, German, Italian and French, reflecting a broadening threat landscape. The multilingual expansion of these scams signifies a global threat and underscores the necessity for multinational cooperation in tackling these AI-driven scams.
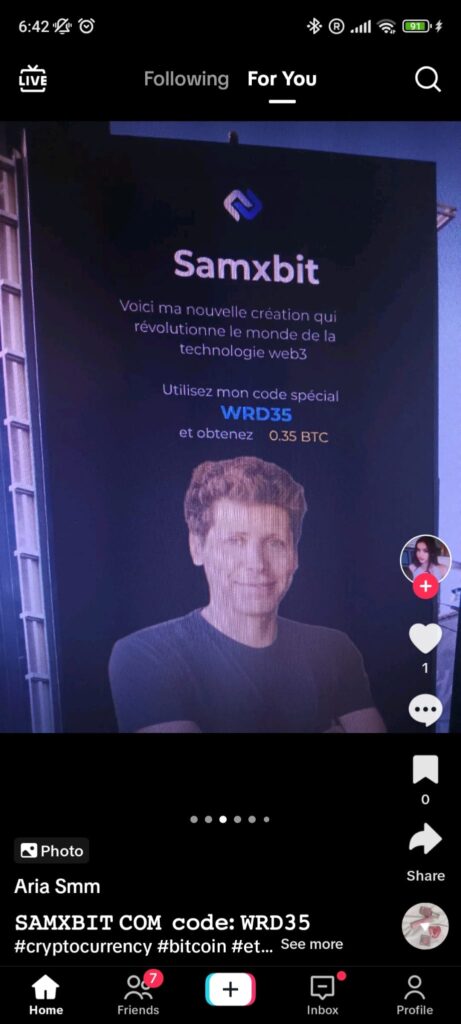
Screenshots of scam videos in Italian and French circulating on TikTok
Though TikTok is the primary stage for these scams, evidence suggests a multi-platform approach by malicious actors. Platforms like YouTube have also been utilized to disseminate scam content, indicating a broader digital footprint and an extended reach of these deceptive practices. TikTok alone has more than 1 billion monthly active users, which makes the surface attack huge. When we started blocking access to these scam websites, we protected several thousand users in a matter of a few days.
The TikTok scams are not isolated incidents but rather indicators of a growing trend of AI-driven cyber threats. The ease of spreading misinformation through deepfake technology, coupled with the allure of quick financial gains, is a potent combination that may pave the way for more sophisticated scams in the future. The potential ramifications extend beyond individual economic loss to a broader erosion of trust in digital platforms and notable personalities.
Luis Corrons, Security Evangelist
Desktop-Related Threats
Advanced Persistent Threats (APTs)
An Advanced Persistent Threat (APT) is a type of cyberattack that is conducted by highly skilled and determined hackers who have the resources and expertise to penetrate a target’s network and maintain a long-term presence undetected.
APT groups are getting increasingly abusing imperfect validation processes for acquiring a driver signature. Signed drivers, typically issued by reputable vendors, are presumed to be safe and authorized for use within an operating system. APTs, by subverting this trust, not only bypass detection mechanisms but also gain stealthy and privileged access to a targeted system, effectively rendering traditional security protocols obsolete. This daring approach challenges the very foundation of cybersecurity, highlighting the need for continuous innovation and vigilance in defending against evolving APT threats.
In early June 2023, we discovered unknown signed drivers by Microsoft. These signed drivers had been distributed by the NSecRTS.exe signed binary, attributed to Shandong Anzai Information Technology Co., Ltd. It’s worth noting that NSecRTS is recognized as a regular monitoring software and has been mentioned by the QiAnXin Virus Response Center.
Furthermore, we identified that the NSecRTS.exe was dropping a driver signed by Microsoft. Upon conducting an extensive investigation, we uncovered multiple malicious activities associated with this driver. One of them was injecting custom RAT in legitimate processes.
Our observations led us to identify victims in the Philippines and Thailand. Despite gathering extensive information, we were unable to definitively attribute the attacks to a specific entity.
Active geopolitical conflicts often attract the attention of APTs due to the volatile and chaotic nature of such environments. These groups, which are often state-sponsored and highly organized, see conflicts as opportunities to exploit the instability for their own strategic gains. The fog of war provides a convenient cover for their activities, allowing them to leverage the chaos to further their agendas, be it political, economic, or military. Notably, APTs have continued to leverage the ongoing war in Ukraine, and additional conflicts, such as the one in Nagorno-Karabakh, have emerged on their radar.
One of the go-to infection vectors for the APT groups this quarter was CVE-2023-38831 which is a vulnerability in WinRAR allowing an attacker to run arbitrary code on the victim’s machine. In many cases victims receive a malicious archive as an attachment to a phishing email. When opening the archive with a vulnerable version of WinRAR, the victim is unwillingly executing malicious code which might lead to an infection of the machine. We could see it being abused by multiple threat actors including attacks targeting Ukrainian government institutions, military, and governments in countries like Malasia, Vietnam, Philippines and more.
Infamous entities such as Lazarus, MustangPanda, and APT41 remain relentless in their global campaigns, consistently refining their tactics and expanding their malware arsenal. These groups continually explore novel techniques, introducing fresh tools and incorporating languages like Nim and Rust into their toolkits.
Luigino Camastra, Malware Researcher
Igor Morgenstern, Malware Researcher
Adware
Adware is considered unwanted if installed without the user’s consent, tracks browsing behavior, redirects web traffic, or collects personal information for malicious purposes such as identity theft.
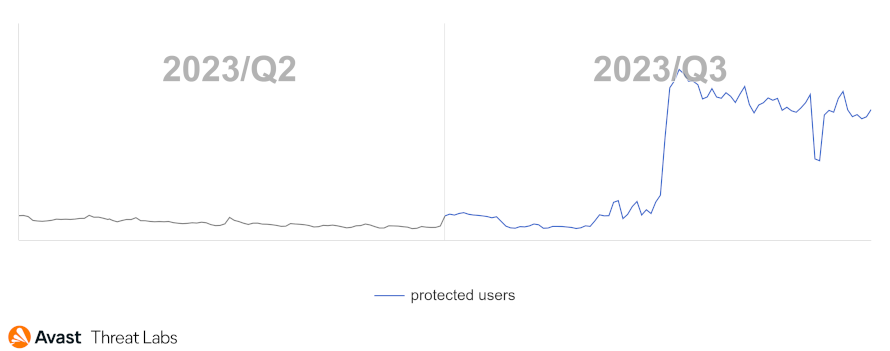
Adware is becoming popular due to the possibilities of monetization and of spreading potentially unwanted programs (PUP) and malware. Although malware spreading via adware is not the primary method to infect victims’ machines, we have focused on adware detections in Q3/2023 to monitor this potential threat.
The results of more precise adware detections can be seen in the chart below. This quartile shows an increase of adware activities that is caused by the SocialBar adware.
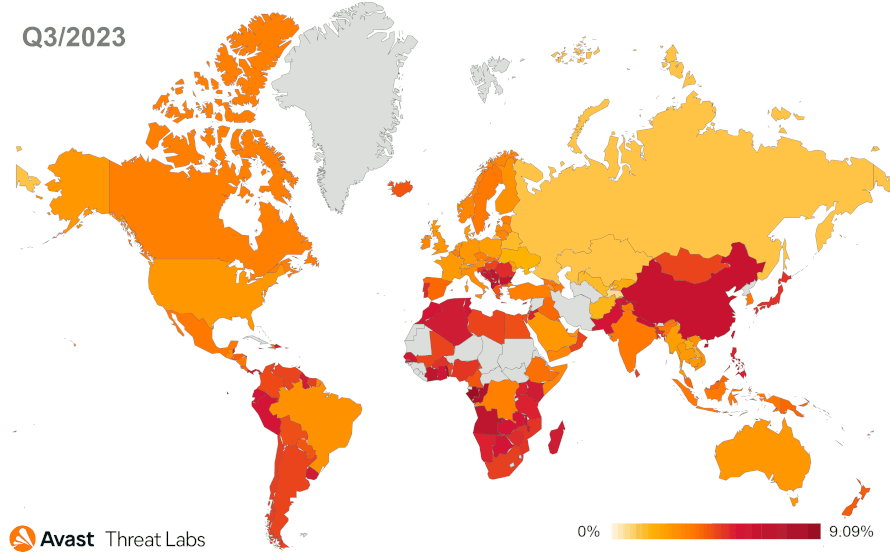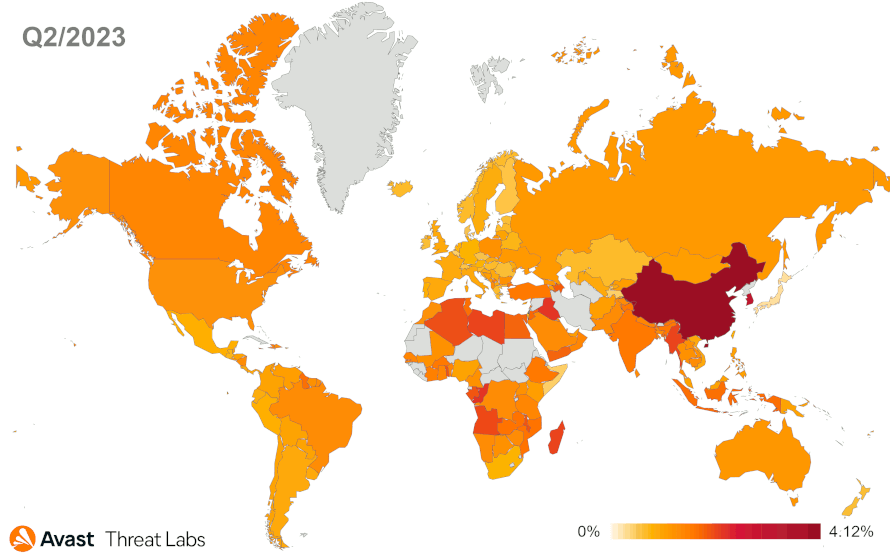
The new detections help us to specify a global overview. Our telemetry reports the four most active regions in point of adware threats; namely, South America, Africa, Southeast Europe, and East Asia. See the map below.
Adware Share
The new detections reduced the ratio of unknown strains from 33% to 6%. The SocialBar is the adware market leader in Q3/2023 with 58%. The list below illustrates the most used ad servers with funny DNS records:
- hissedassessmentmistake[.]com
- trustworthyturnstileboyfriend[.]com
- happeningurinepomposity[.]com
- disgracefulforeword[.]com
- secondquaver[.]com
- usetalentedpunk[.]com
- lyricsgrand[.]com
The rest of the shares are allocated to other adware strains as follows:
- MudOrange (7%)
- DealPly (3%)
- RelevantKnowledge (2%)
- Neoreklami (2%)
- MicroTag (2%)
Martin Chlumecký, Malware Researcher
Bots
Bots are threats mainly interested in securing long-term access to devices with the aim of utilizing their resources, be it remote control, spam distribution, or denial-of-service (DoS) attacks.
Probably the most impactful change in the botnet landscape occurred at the end of August – the FBI-led attempt to take down and dismantle the Qakbot botnet. Interestingly, the target was not just its Command and Control (C&C) infrastructure, but they also attempted to disconnect infected clients from the botnet, effectively making it harder to resurrect the botnet under a new infrastructure. There is already an apparent drop in the number of clients attempted to be recruited into the botnet which has dropped to one fifth of the “usual” value during August. While this is good news from the botnet perspective, this has not eliminated Qakbot-associated spam delivery capabilities. The threat actor associated with Qakbot distribution (TA577) began to distribute DarkGate as one of their phishing payloads soon after Qakbot’s takedown.
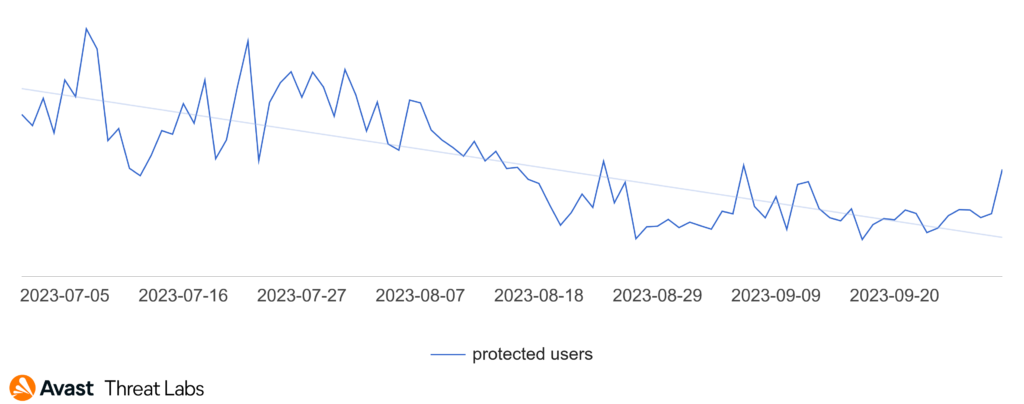
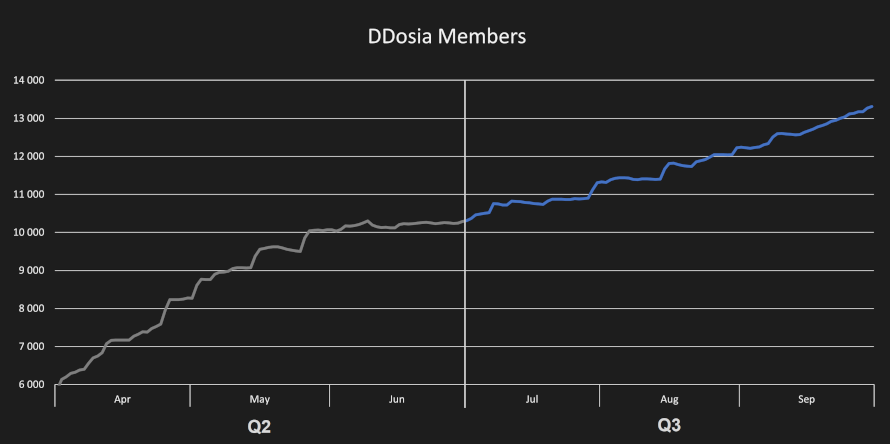
We are keeping our eye on the threat group NoName056(16) and their DDosia project. Its number of members has exceeded 13,000 users by the end of September. Based on the numbers from the previous quarter, they managed to gain some momentum with a steady increase of approximately 1,000 members every month. Their modus operandi remains the same – DDoS attacks, accusations of Russophobia and boasting about their accomplishments. It is quite unfortunate that the usage of misleading terminology by mainstream media, such as mislabeling DDoS attacks as hacks or labeling their perpetrators as hackers, sometimes unwittingly inflates the public perception of such attacks, providing much desired media coverage boost to the perpetrators. This is especially true for Internet activist groups where media coverage also boosts the group’s credit in the community, further fueling their potential recruitment pool.
As for targets, most of the targeted top-level domains (TLDs) were .pl (Poland, 15%), .lt (Lithuania, 11%), and .it (Italy, 9%). The former two are not a shocking surprise as there are active involvements in these regions with the Ukraine-Russia conflict. In case of Italy, the group seemed to react to Joe Biden’s meeting with Italian PM Giorgia Meloni.
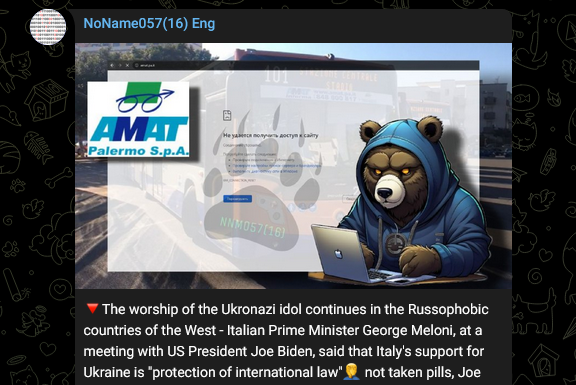
Financial institutions were the most common target this quarter, presumably due to the potential financial damage and chance of getting significantly better press coverage. As a side-note – they seem to experiment with photo and graphic styles. They started to experiment with the replacement of a photo of a bear with a cartoonish image of a bear stylized as a hoodie-clad hacker (31st July) or a member of an army (from the end of September on).
Despite the Qakbot’s takedown, the global risk ratio has slightly increased – partly due to it happening in the middle of the quarter and partly by increased activity of other botnets. We have seen a significant increase in the activity of Tofsee (+41%), Emotet (+25%), and Trickbot (+13%) botnets. As for other families, our telemetry indicates a decline in most of the other families.
Adolf Středa, Malware Researcher
Coinminers
Coinminers are programs that use a device’s hardware resources to verify cryptocurrency transactions and earn cryptocurrency as compensation. However, in the world of malware, coinminers silently hijack a victim’s computer resources to generate cryptocurrency for an attacker. Regardless of whether a coinminer is legitimate or malware, it’s important to follow our guidelines.
When compared to last quarter, in Q3/2023 we observed another 4% decrease in the risk ratio in the coinmining space. This is a continuing downward trend for coinmining threats.
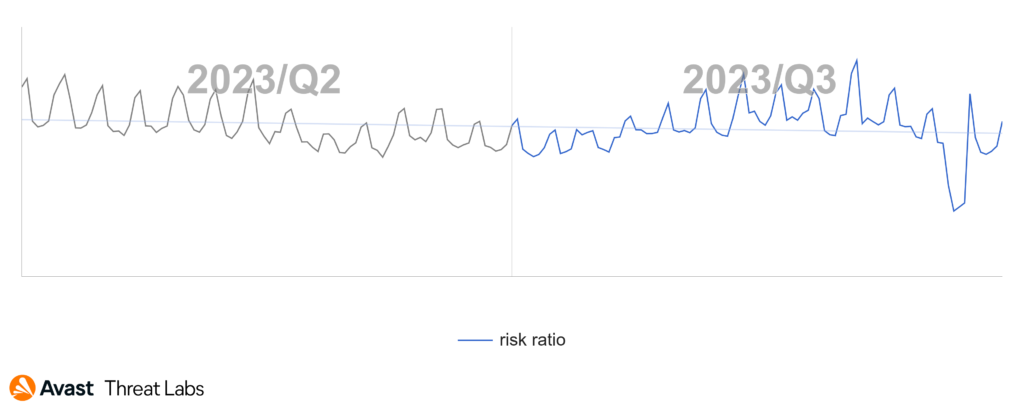
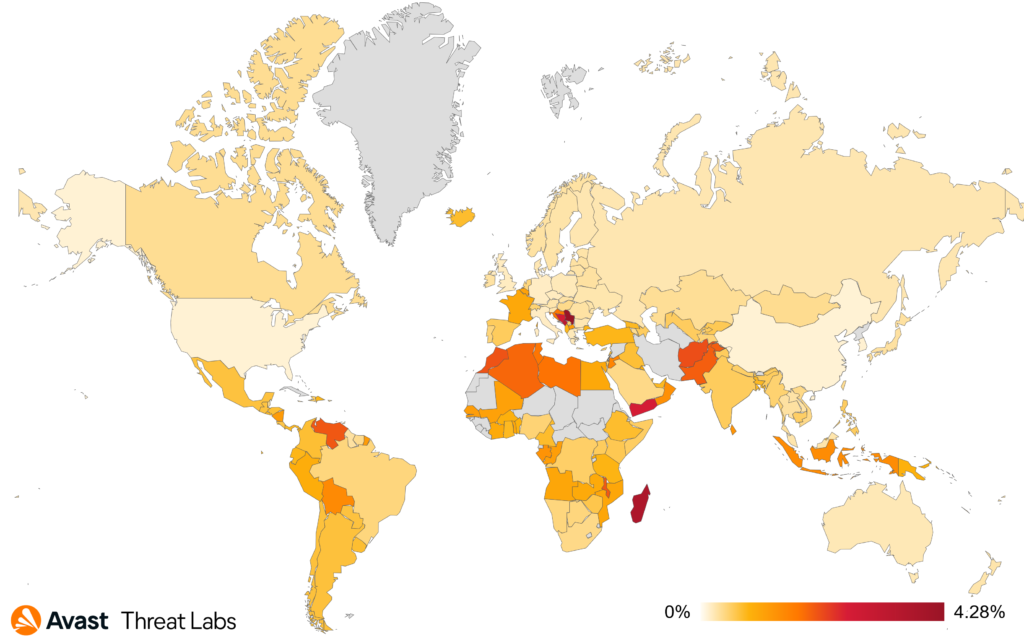
During Q3/2023, users in Serbia again faced the highest risk of encountering a coinminer, a regional trend we have seen over the past few quarters. However, with a risk ratio of 4.28%, this is drop in risk by 26% and a record low. A similar situation is seen in other higher-risk countries, including Madagascar with 3.73% risk ratio, Montenegro with 3.29% risk ratio, and Bosnia and Herzegovina with 2.64% risk ratio.
Unfortunately, the market share increased for XMRig where we measured a 30% increase, now accounting for 23.65% of the total coinmining market share. CoinBitMiner also became more popular, increasing its malware market share by 10%, accounting for 2.02% of the share. Other web miners saw a slight decrease by 5%, now accounting for a combined 61.46% market share. Other strains, such as FakeKMSminer, VMiner, and CoinHelper, experienced rather big decrease in activity, with 27%, 62%, and 29% decrease respectively.
The most common coinminers with their market share in Q2/2023 were:
- Web miners (61.46%)
- XMRig (23.65%)
- CoinBitMiner (2.02%)
- FakeKMSminer (1.58%)
- NeoScrypt (1.03%)
- CoinHelper (0.77%)
- VMiner (0.73%)
Jan Rubín, Malware Researcher
Information Stealers
Information stealers are dedicated to stealing anything of value from the victim’s device. Typically, they focus on stored credentials, cryptocurrencies, browser sessions/cookies, browser passwords and private documents.
The common belief that “I have nothing to hide, I don’t need to protect my data” is fundamentally flawed. Even individuals who believe their data lacks value may find out that, at scale, everything may become valuable. This kind of data can be monetized via sales on underground forums, used for further attacks including more targeted scams and phishing (so called spear-phishing), leveraged for blackmailing, and more. Stay safe out there.
In Q3/2023, we observed an overall 6% decrease in information stealers activity in comparison to the previous quarter, slowing down the decreasing trend we have been recently observing.
The biggest change this quarter is that, according to our data, Raccoon Stealer experienced a huge decrease in activity this quarter with a 72% drop in market share. On the other hand, some other strains increased their presence significantly, namely AgentTesla, Fareit, and SnakeKeylogger, balancing the scales.
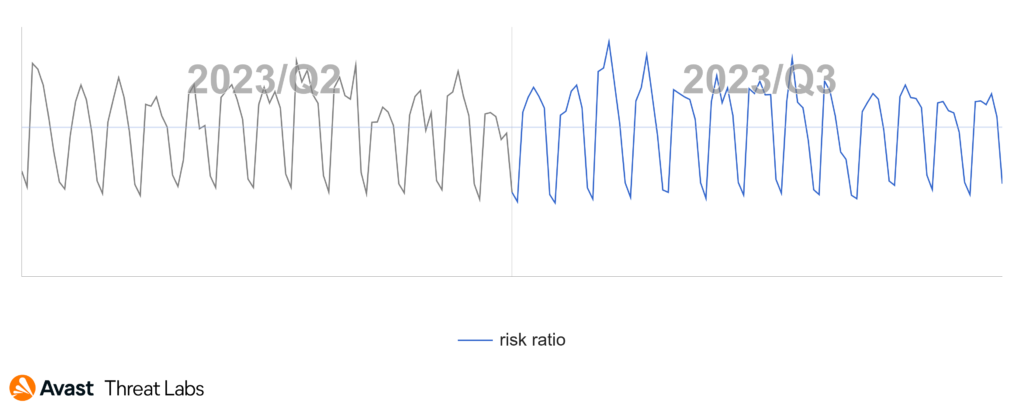
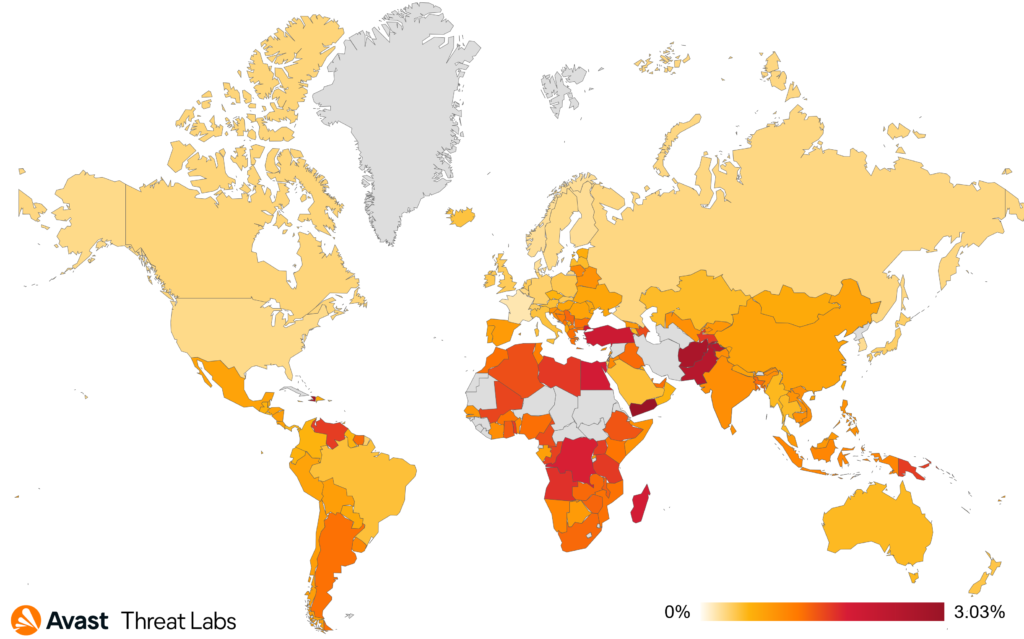
Geographical distribution stayed consistent between Q2 and Q3/2023. Countries where we have more significant userbase having the highest risk ratio are Pakistan (2.47%), Turkey (2.05%), and Egypt (1.90%). Thankfully, the risk ratio in these countries decreased compared to the previous quarter by 5%, 7%, and 14%, respectively.
The biggest increase in risk ratio with regards to information stealers experienced Ukraine (44%), United States (21%), and India (16%).
AgentTesla still holds and further underlined the first place between the most popular information stealers, increasing its market share further by 9%. FormBook, the second-place holder, stayed consistent, increasing its market share by only 0.55%. Fareit, SnakeKeylogger, and Stealc, all experienced an increase in their market share by 11%, 68%, and 4%, respectively.
Fortunately, Raccoon Stealer with its 72% drop in market share was not alone. RedLine and Arkei were both 10% less active in Q3/2023 with regards to market share, along with ViperSoftX dropping by another 7%.
The most common information stealers with their market share in Q3/2023 were:
- AgentTesla (29.14%)
- FormBook (11.39%)
- RedLine (5.46%)
- Fareit (5.45%)
- Lokibot (4.51%)
- Arkei (3.96%)
- ViperSoftX (2.08%)
- Raccoon Stealer (1.95%)
It is also worth mentioning new information stealers or their variants, which have displayed a notable surge in activity over the past couple of months. These malicious actors are constantly evolving their tactics to bypass security measures and exfiltrate sensitive data. These often include new techniques that exploit vulnerabilities in both software and human behavior, making it imperative for organizations and individuals to remain vigilant and adopt robust cybersecurity strategies to safeguard their valuable information.
The new version of Rilide Stealer, targeting banking data, was seen to work around Google Chrome Manifest V3. One of the new features of the Manifest V3 is disabling remote code execution in browser extensions. As a workaround, Rilide Stealer is using inline events along with Declarative Net Requests rules to execute the code remotely and remove the Content Security Policy headers. Since Rilide is being distributed using local loaders on the infected machines, that is without the use of Chrome Web Store, there is no review process involved that would detect this practice.
Furthermore, new connections between Rhadamanthys and Hidden Bee coinminer were discovered, providing new insights into the inner workings and implementation details. Another malware, called DarkGate, is a loader with further capabilities like keylogging, cryptocurrency mining, stealing information from browsers, and an overall remote access functionality. Even though the malware can be traced a couple of years back already, it is still undergoing active development, introducing new vectors how to infect victims such as using Microsoft Teams.
Additionally, Lumma, a malware-as-a-service stealer, is also continually gaining in popularity. The malware’s capabilities range from cryptocurrency theft to targeting two-factor authentication (2FA) browser extensions, harvesting banking data, credentials, and more.
Clippers are generally small malicious programs that are used to swap the victim’s clipboard content for content specified by the attacker – in this case, crypto wallet addresses. Such clippers that have gained popularity in the previous months are, among others, Atlas Clipper, Keyzetsu Clipper, and KWN Clipper, which are usually leveraging Telegram for command and control communication and offers for purchase.
Jan Rubín, Malware Researcher
Ransomware
Ransomware is any type of extorting malware. The most common subtype is the one that encrypts documents, photos, videos, databases, and other files on the victim’s PC. Those files become unusable without decrypting them first. To decrypt the files, attackers demand money, “ransom”, hence the term ransomware.
The prevalence of ransomware is certainly not diminishing. In fact, it is the opposite. According to the research of Chainalysis, the total sum of money extorted during the first half of 2023 is about $450 million (compared to $280 million in the first half of 2022). This is caused by a change of tactics of the ransomware operators – they tend to target bigger victims, which brings the possibility of bigger figures paid as ransom. The average payment size for the top strains is as high as $1.7 Million USD (Cl0p ransomware) and $1.5 Million (BlackCat ransomware).
Vulnerabilities in popular third-party applications widely used in companies make attacker’s job easier. We wrote about SQL injection vulnerability in the Progress MOVEit transfer software in the previous Threat Report.
In addition to encryption of the victim data, ransomware gangs increasingly perform data extortion. Data encryption may be solved if the company has a good data backup policy; data extortion and subsequent leakage of internal documents may be a problem regardless of it. Also, keep in mind that when the ransom is paid, they don’t always keep the promise of deleting the extorted data.
One of the new ransomware strains that emerged this quarter was Rhysida. The first mention of the ransomware was in May 2023 and the ransomware leak site already lists about fifty successfully attacked organizations – government, healthcare, IT, municipalities.
The encryptor used by the Rhysida gang is a 32-bit or 64-bit EXE file, compiled with MinGW/GCC 6.3.0 and linked with GNU Linker 2.30. For cryptographic operations, LibTomCrypt v 1.18.1 is used as crypto library. Files are encrypted by AES cipher in counter mode, the file key and IV are encrypted by RSA-4096 with OAEP padding.
Rhysida wants to be as fast as possible during file encryption:
- Intermittent Data Encryption. Not everything is encrypted. For larger files, Rhysida only encrypts a few distinct file blocks.
- Multi-threaded encryption. For every processor, Rhysida created one encryptor thread. All processors in the PC are busy during the encryption process.
From the usage of pthreads library, we assume that authors of the Rhysida ransomware wanted to build an encryptor that is also easily portable to other platforms.
Rhysida drops a ransom note file called “CriticalBreachDetected.pdf” into each folder. The following picture shows an example of the ransom note:
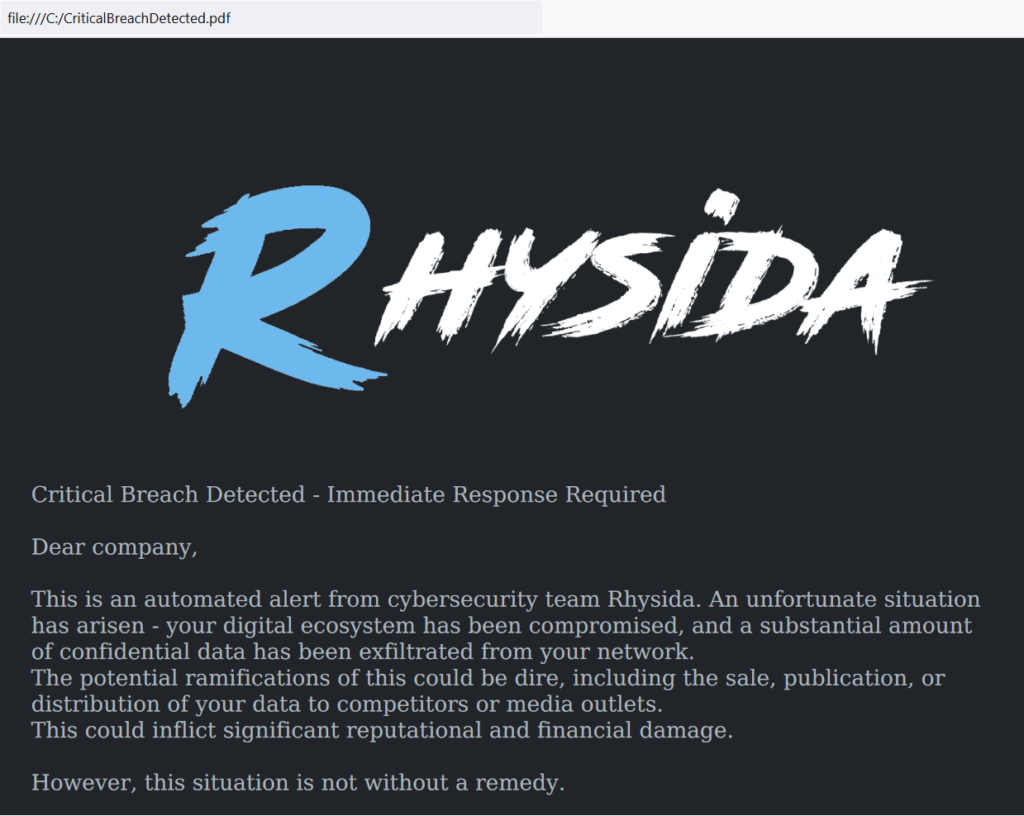
More information about this ransomware strain can be found in our blog post.
As usual in every Thread Report, we bring the overview of the risk ratio in our userbase. The following picture shows the riskiest countries (regarding ransomware).
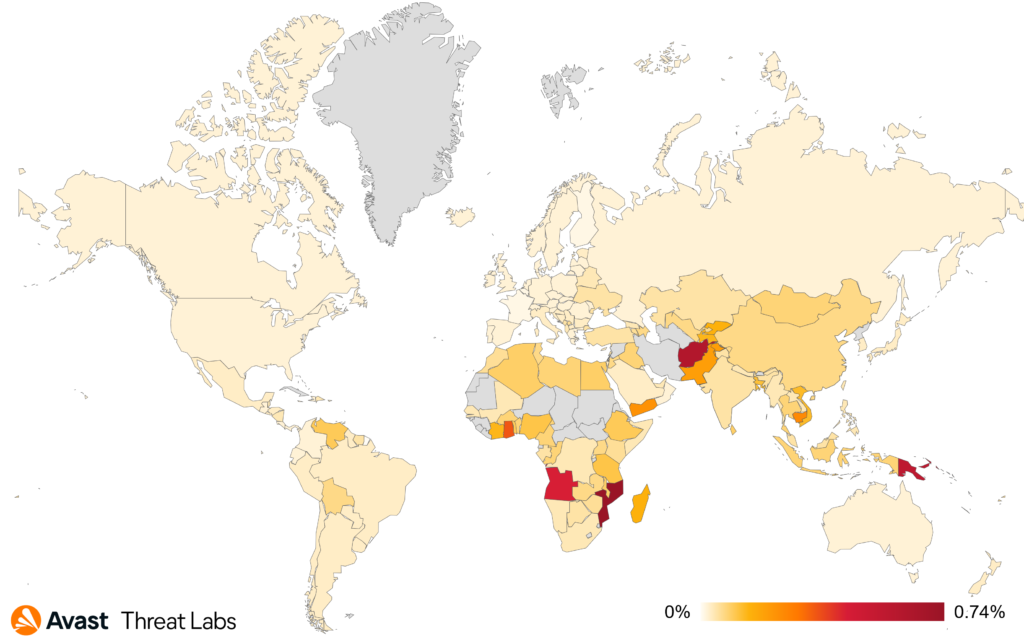
The list of countries most at risk of ransomware attacks:
- Mozambique (0.74%)
- Angola (0.44%)
- Ghana (0.35%)
- Pakistan (0.20%)
The most prevalent ransomware strains that we saw and protected against in the list below:
- WannaCry (19% of ransomware share)
- STOP (15%)
- Thanatos (3%)
- TargetCompany (2%)
- LockBit (2%)
- Cryptonite (2%)
- Enigma (1%)
The total risk ratio amongst our user base remains approximately the same:
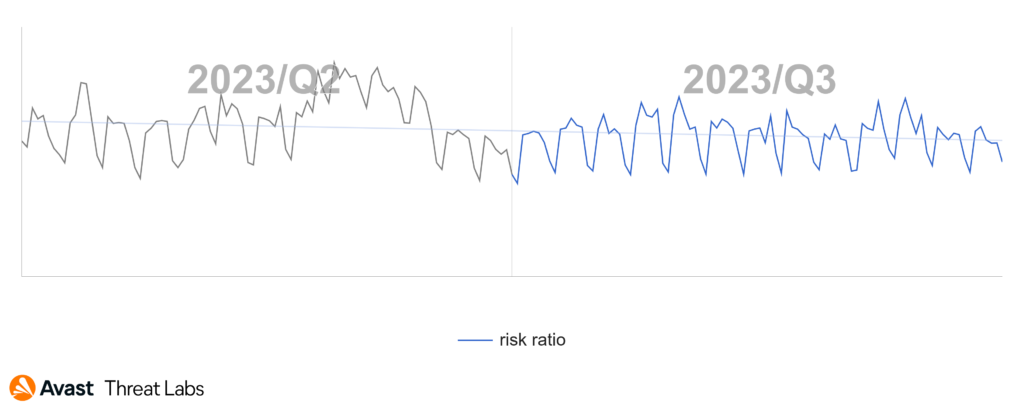
Ladislav Zezula, Malware Researcher
Jakub Křoustek, Malware Research Director
Remote Access Trojans (RATs)
A Remote Access Trojan (RAT) is a type of malicious software that allows unauthorized individuals to gain remote control over a victim’s computer or device. RATs are typically spread through social engineering techniques, such as phishing emails or infected file downloads. Once installed, RATs grant the attacker complete access to the victim’s device, enabling them to execute various malicious activities, such as spying, data theft, remote surveillance, and even taking control of the victim’s webcam and microphone.
The growing trend of RATs observed in Q2/2023 continues in Q3/2023. Overall, we have seen a slight increase in the risk ratio. The substantial rise of Remcos we reported in Q1 and Q2/2023 seems to have slowed, with Remcos staying around the same numbers as in the previous quarter. However, we are observing a steady growth of the DBatLoader dropper which can deliver Remcos among other payloads.
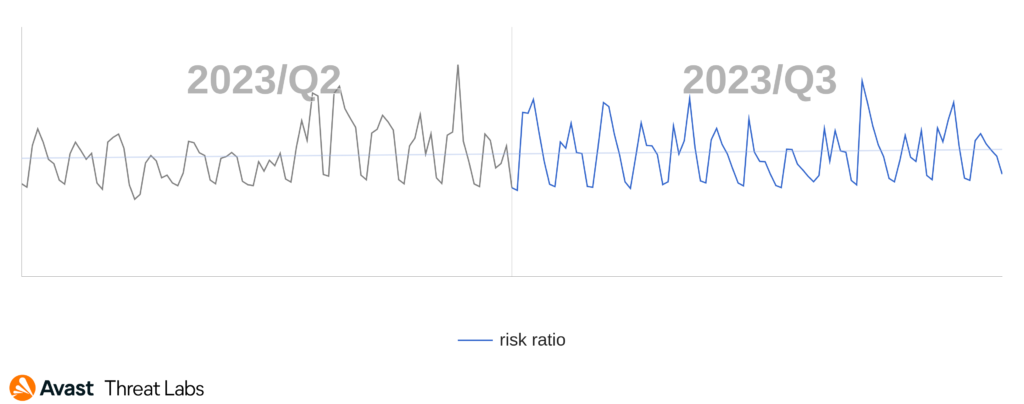
The countries with the highest risk ratio regarding RATs are, as usual, Afghanistan, Iraq and Yemen due to the worm-like behavior of HWorm which seems to be widely spread in these countries. Additionally, we also see njRAT quite active in Iraq and Yemen. Countries with the largest increase in risk ratio are Portugal (148% increase), Poland (55%) and Slovakia (43%) caused by Remcos and in the case of Slovakia also Warzone. The biggest decrease in risk ratio was observed in Czechia (42% decrease), Belgium (34%) and Japan (33%). This is again likely tied to the activity (or for the moment the lack of) of Remcos and Warzone in these countries.
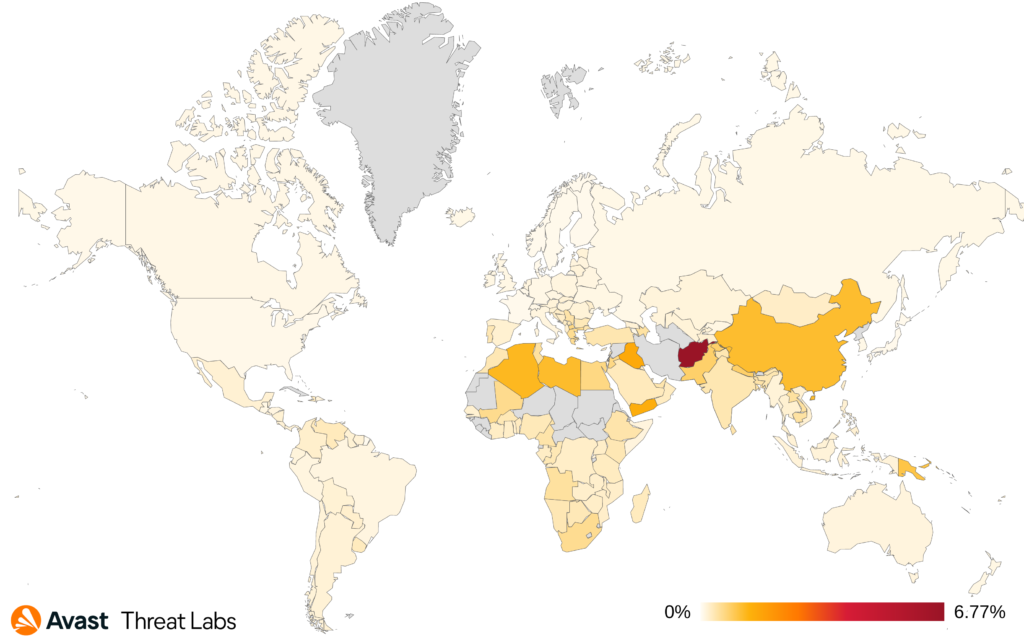
The largest increase in market share and number of protected users among the most prevalent RATs in Q3/2023 belongs to NanoCore. Both numbers grew by nearly 100%. Greece, Turkey, and Hungary are the most at risk of this RAT, we have also observed a substantial increase in Brazil, Mexico, and Spain.
Even bigger increase had XWorm which gained more than 400%. However, in total numbers, XWorm is not as widely spread to make it to the top 10 list.
Warzone and AsyncRat had the largest drop in risk ratio among the most prevalent RATs we see. Warzone went down by 27% and AsyncRat by 14% according to our data.
The most prevalent remote access trojan strains in our userbase are:
- HWorm
- Remcos
- njRAT
- AsyncRat
- Warzone
- NanoCore
- QuasarRAT
- Gh0stCringe
- DarkComet
- Bifrost
Uptycs Threat Research team discovered a new RAT named QwixxRAT, first noticed in early August. The QwixxRAT has a fairly standard set of features including keylogging, information theft (credit cards, browsing history and bookmarks, Steam related data, etc.), spying (webcam, microphone), running commands on infected system and more. It uses Telegram as the C&C channel.
ZenRAT is another RAT which appeared in Q3/2023, reported by Proofpoint Emerging Threats. This RAT was found to be bundled with the legitimate password manager Bitwarden on the website bitwariden[.]com. According to the research, ZenRAT is designed to be modular, however according to Proofpoint they only saw one module which seems to be gathering system information.
Ondřej Mokoš, Malware Researcher
Rootkits
Rootkits are malicious software specifically designed to gain unauthorized access to a system and obtain high-level privileges. Rootkits can operate at the kernel layer of a system, which grants them deep access and control including the ability to modify critical kernel structures. This could enable other malware to manipulate system behavior and evade detection.
The trend of rootkit activity has been stable since the beginning of the year. We can also state that there is still a long-term downward trend. The chart below shows the rootkit activity for the previous three quarters.
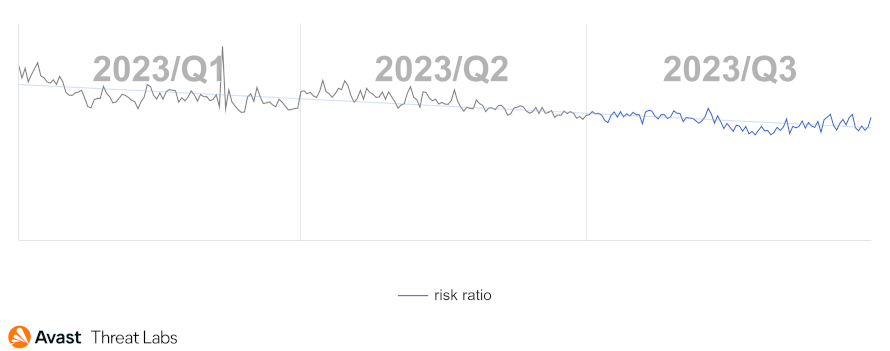
When examining the risk ratio for individual countries, China maintains its leading position regarding the extent of rootkit activities. Although globally, we are observing a decrease in activity, we have seen a particular increase in Ukraine (62%) and in the Russian Federation (62%), specifically the activity increase of the R77RK rootkit.
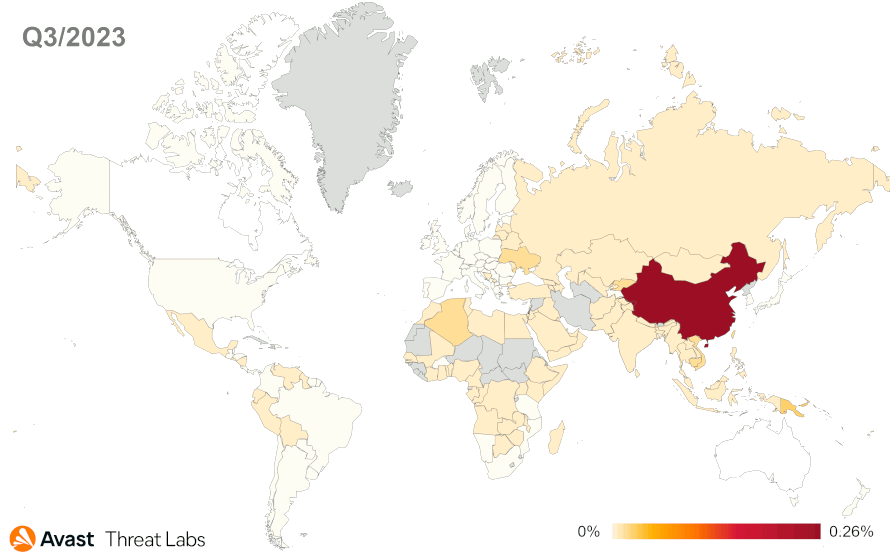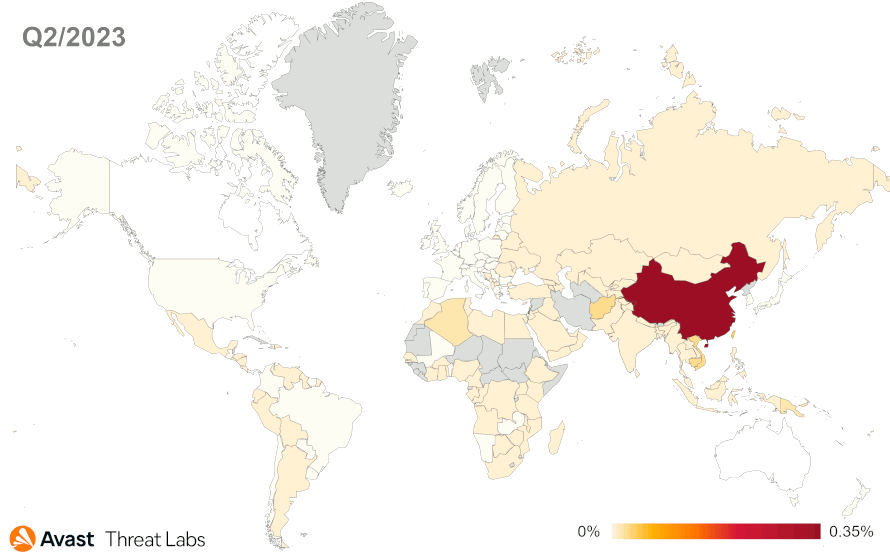
In September 2023, an updated version of R77Rootkit (1.5.0) was released, simplifying its deployment on victims’ machines. However, there was no increase in the activity of this rootkit despite the improvements. So, the R77RK is still the malware market leader with the same share (18%) as in the previous quarter.
Around 17% of unidentified strain rootkits are also in the market share, serving as kernel proxies for various activities involving elevated system privileges, such as terminating processes, altering network communications, and registry operations, among others. Compared to the previous quarter, an interesting feature is the increased use of the VMProtect to obfuscate driver functionality.
The third rootkit with the third-largest market share is the Pucmeloun rootkit, whose primary functionality is the modification of network traffic to redirect to different pages. It is a part of other adware that controls web requests on the kernel layer. Adware websites have primarily Chinese content.
The following is the comprehensive list of distinctly recognized Windows rootkit strains, along with their respective market shares:
- R77Rootkit (18%)
- Pucmeloun (13%)
- Alureon (7%)
- Cerbu (6%)
- Perkesh (6%)
In terms of Linux kernel rootkits, inspired by Syslogk, the threat actors continue hiding command line backdoors (or bots, depending on how the attacker controls the infected computers) with kernel rootkits that execute those via magic packets (e.g. AntiUnhide rootkit). We continue monitoring Linux kernel rootkits that reuse the code of open-source projects. For instance, Rocke reuses the code of Reptile Reptile and hides a secret protected shell that can be spawned via magic packets. and hides a secret protected shell that can be spawned via magic packets.
Martin Chlumecký, Malware Researcher
David Álvarez, Malware Analyst
Vulnerabilities and Exploits
Exploits take advantage of flaws in legitimate software to perform actions that should not be allowed. They are typically categorized into remote code execution (RCE) exploits, which allow attackers to infect another machine, and local privilege escalation (LPE) exploits, which allow attackers to take more control of a partially infected machine.
WinRAR is not a frequent target of exploits, aside from the occasional path traversals. Our attention was therefore immediately captivated when we first heard about CVE-2023-38831, an easy-to-exploit WinRAR vulnerability, which allows an attacker to craft a malicious archive so that it contains both a benign lure (e.g., an image file) and a malicious payload. When an unsuspecting victim opens such a malicious archive in a vulnerable version of WinRAR and double clicks the lure file, the malicious payload will get executed instead. This is because opening files from inside WinRAR is internally implemented by extracting the target files into a temporary folder and then calling ShellExecute on them. Unfortunately, due to a buggy path normalization, it was possible to redirect the ShellExecute call to target a different file than the one the user clicked on. For a more in-depth look at the exploit, we recommend reading this SecureLayer7 analysis.
This vulnerability was exploited as a zero-day in financially motivated attacks since at least April 2023. The attacks took place on trading forums and consisted of attackers posting exploit archives promising details of novel trading strategies. However, instead of exciting new trading strategies, the archives were used to spread the DarkMe malware (or the Guloader -> Remcos duo in some attacks). This campaign was initially discovered in July by the Group-IB Threat Intelligence unit. After reporting the vulnerability to RARLAB, a patched version of WinRAR was released in August.
Since WinRAR must be updated manually by downloading and installing the patched version, we can expect there will continue to be many users with unpatched versions in the future. While the exploit does require a fair amount of user interaction (not every targeted user will open the archive in WinRAR and double click the lure file), it is quite easy to craft an exploit archive (there is even a public PoC builder on GitHub), so it is likely that there will be threat actors experimenting with this vulnerability. And indeed, just recently Google TAG reported on “multiple government-backed hacking groups” exploiting this vulnerability. Let us therefore use this opportunity to remind the reader not to delay applying the update.
In other news, Google’s Threat Analysis Group and Citizen Lab discovered a new in-the-wild zero-day exploit chain for iPhones. This chain started with a WebKit RCE (CVE-2023-41993) which was combined with a signature bypass (CVE-2023-41991) and ultimately ended with a kernel LPE (CVE-2023-41992). Post-exploitation, the chain deployed the Predator implant, known to be developed by the commercial spyware vendor Intellexa. The attackers also used a parallel exploit chain for Android devices, but unfortunately the full details of this chain remain unknown at the time.
As reported by Citizen Lab, one of the targets was former Egyptian MP Ahmed Eltantawy who announced his run for president in 2024. He was targeted through a man-in-the-middle (MitM) injection on plaintext HTTP, through a middlebox located at an ISP-level privileged network position. This essentially allowed the attackers to use a browser exploit with no user interaction required, similarly to how a watering hole or malvertising attack would work. While it is extremely hard to defend against such government-backed attackers, using a secure VPN should mitigate the risk of ISP-level MitM injection. However, note that just a single HTTP request outside the VPN tunnel is all the attackers would need to still be able to inject the exploit.
Finally, in Q3/2023 the BLASTPASS exploit chain that was actively used by the infamous NSO Group to compromise fully patched iPhones in a zero-click manner. BLASTPASS was discovered by the Citizen Lab, who found it while helping check the device of a potential mercenary spyware victim. The initial memory corruption vulnerability appears to go by three different CVEs (CVE-2023-41064, CVE-2023-4863, and CVE-2023-5129), as there was some confusion at first about who should actually assign the CVE. Nevertheless, the vulnerable code is located in libwebp, Google’s image rendering library for the WebP format. While this library is very widely used, it is not currently clear what conditions are needed for the vulnerability to be exploitable. There has been some great research into the root cause of the vulnerability and a public PoC to trigger a heap overflow. However, weaponizing this heap overflow seems like an absurdly difficult feat, so at least for the moment, we do not have to fear this vulnerability being exploited in the wild by less sophisticated attackers.
Jan Vojtěšek, Malware Reseracher
Web Threats
Users increasingly depend on the internet in their daily lives, exposing themselves to a growing array of potential risks, like stealing their personal data or financial losses. The rise in activities such as variations of financial scams, dating scams, fake push notifications and phishing threats in general underscores this trend.
The third quarter of 2023 was a growing quarter for web threats in general. Many types of threats started their growth at the end of the holiday season and this growth only continued in the third quarter. But there are also some exceptions. Let us take a closer look at them.
Scams
A scam is a type of threat that aims to trick users into giving an attacker their personal information or money. We track diverse types of scams which are listed below.
The significant increase in scam threats that we reported in Q2/2023 remained strong in the third quarter. As you can see in the following chart, we even saw a slight resumption of growth in mid-August.
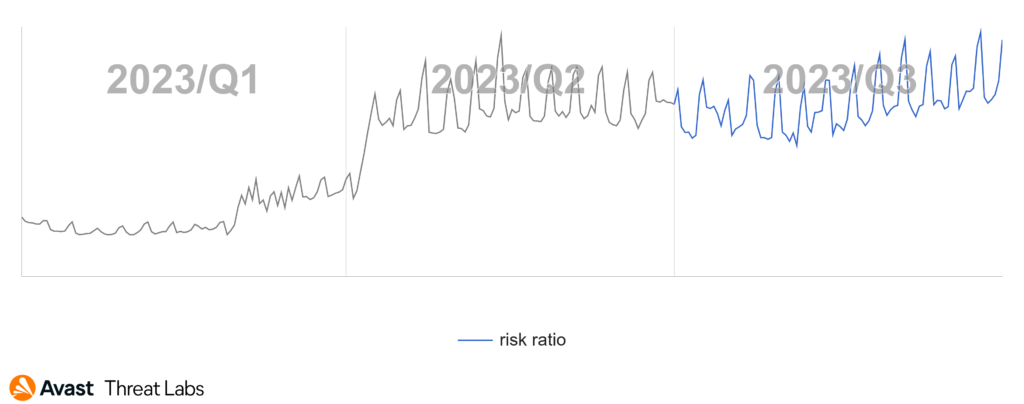
In line with the trends observed in Q2, malvertising continues to serve as very strong tools for scammers, thanks to which they spread various categories of scams. This includes popular dating scams, or financial scams for example. These threats have maintained their strong position, but this is not the case with technical support scams. However, we are seeing the use of false reports of viruses being found to exploit them for sales purposes. Additionally, extortion email scams and phishing threats have both witnessed an uptick in popularity.
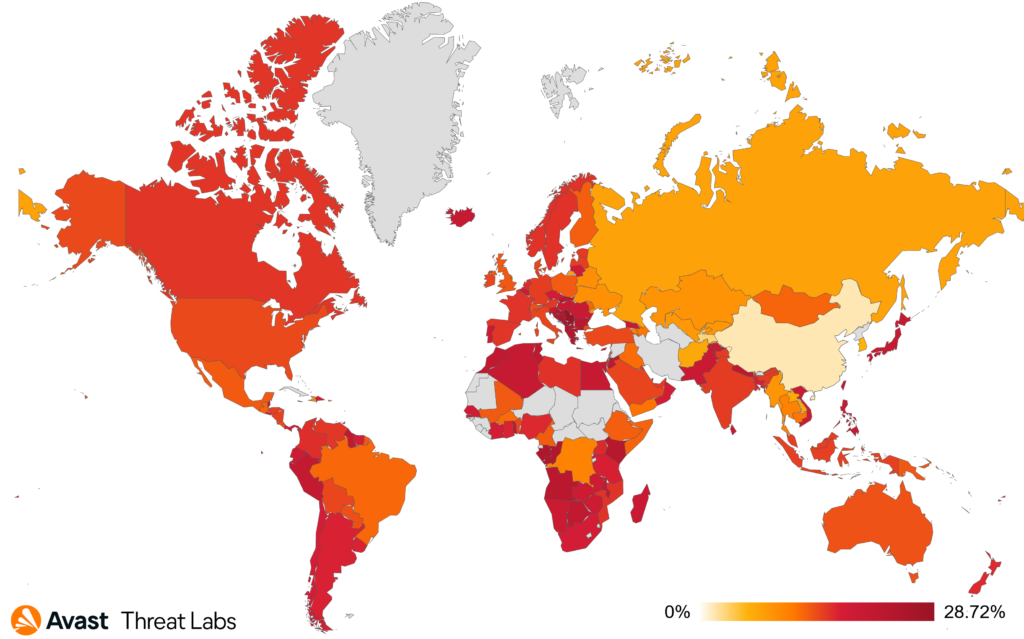
The countries most at risk of the scam attacks were Serbia, Kosovo, Montenegro, Albania, Croatia.
Countries where there was an increase in risk ratio are for example Japan +19%, Greece +17%, United States +14%, Austria +13%, or Germany +12%
Malvertising
Malvertising is a malicious online advertising technique that involves the distribution of malware through online ads or, in some cases, in conjunction with browser push notifications. Cybercriminals use these seemingly legitimate ads to deliver malware to unsuspecting users’ devices when they click on or interact with the compromised advertisements.
Cybercriminals are smart enough to make their malvertising pop-ups look genuine. Frequently, these fraudulent pop-ups exploit the recognizable antivirus company’s logo. The goal is to convince users they are encountering a legitimate notification from an antivirus provider. These alerts typically display messages that a virus on a computer has been found and that the subscription plan has expired.
Upon clicking these deceptive pop-ups, unsuspecting users may find themselves redirected to a fake website. These fraudulent sites often take the form of straightforward phishing pages, where users are asked to enter personal credit card information under the guise of providing antivirus services. The scam can take many forms.

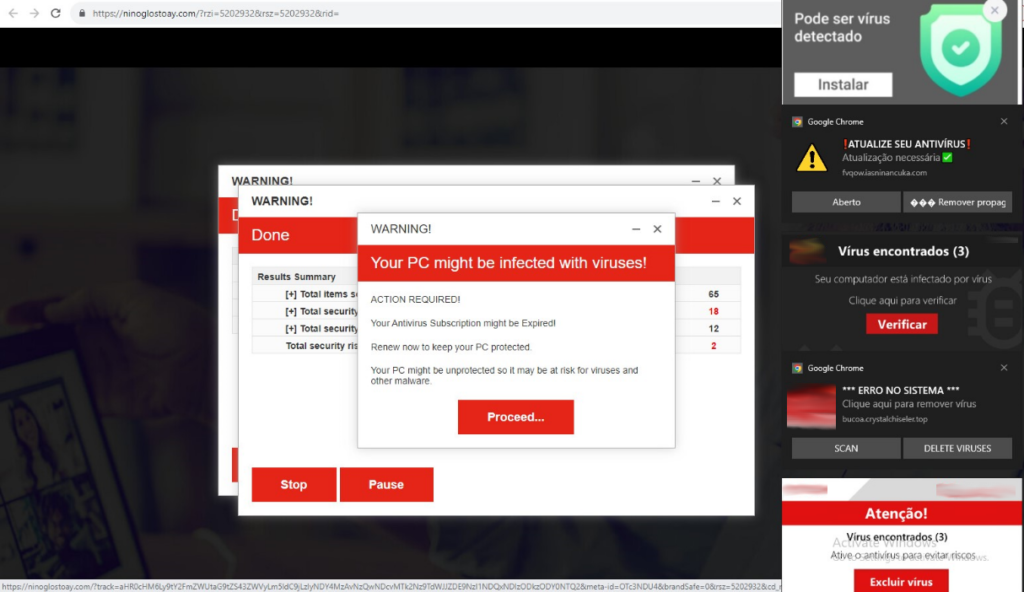
We have warned about malicious push notifications already in previous reports; this quarter is no exception. This method continues to remain popular with scammers as its effectiveness is still considerable, especially on mobile phones.
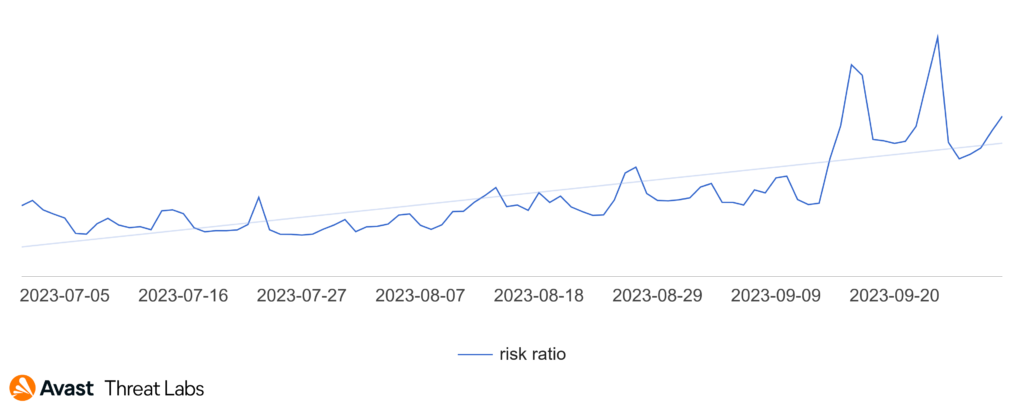
As you can see in the below chart, the holiday season has ended not just for students but also for threat actors as there is a substantial surge in the volume of threat detections during September. The graph below represents detection of several types of malvertising. Within the month of September, we observed two prominent spikes in malvertising activity.
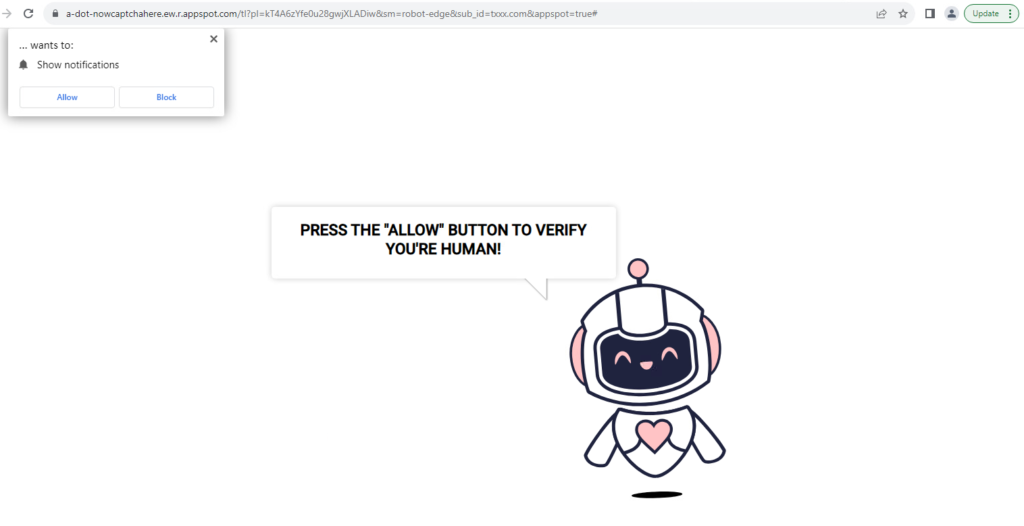
One of the most common examples of this malvertising was a page that fell into the push notification section that often appeared as part of a redirect chain. This page has multiple variations. The main purpose is to simply convince user to allow push notifications.
Push notifications can be especially effective on mobile devices, where they can also be disguised as system notifications, such as an unanswered call or a new text message.
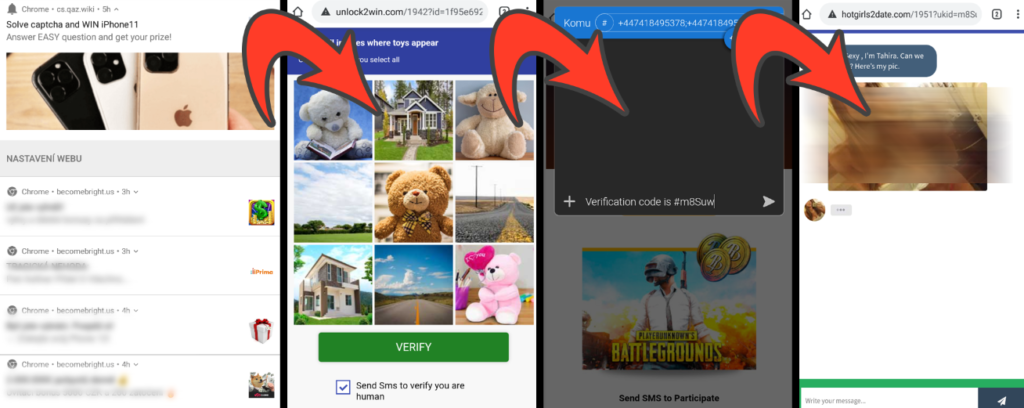
Push notifications are not the only powerful tool for scammers. We have reported many times that scammers like to use advertising space on popular social networks. This way of promotion is especially dangerous because many users consider their social platforms to be a safe and personal space. Scammers also design their ads to attract attention, often by using catchy text or the faces of famous personalities. Thanks to this, the success rate of these campaigns is quite high.
Another big advantage for scammers utilising social media ads is their ability to precisely target and tailor content to vulnerable users. Consequently, users may find their social media feeds full of these types of ads over time.
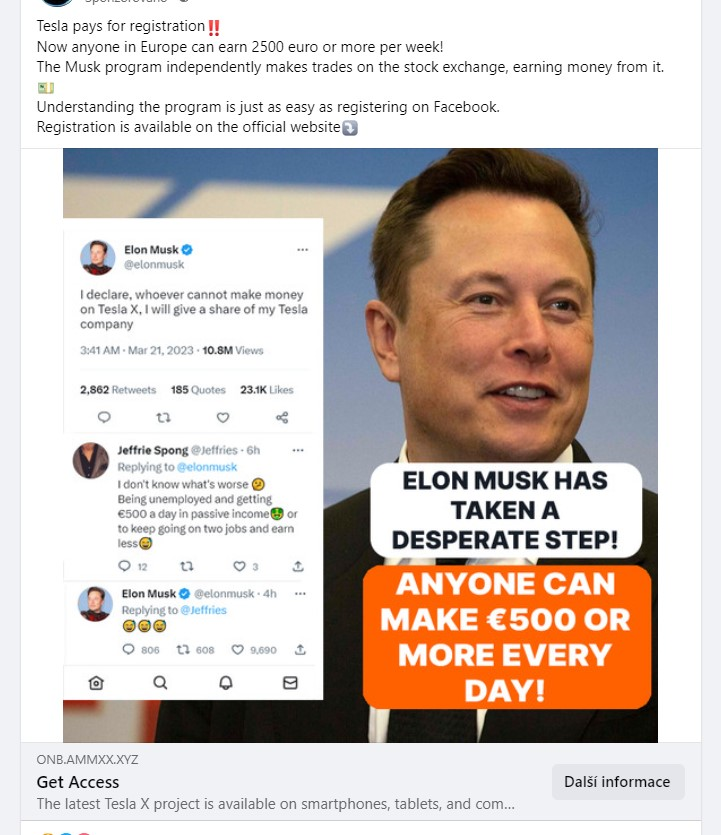
These above ad examples are from Facebook. In this case, these ads are part of a single fraudulent financial scam where scammers are trying to trick users into investing in an Elon Musk/Tesla project. After clicking on the ad, the user is redirected to a web page where they are informed about the great benefits and the certainty that this project is profitable.
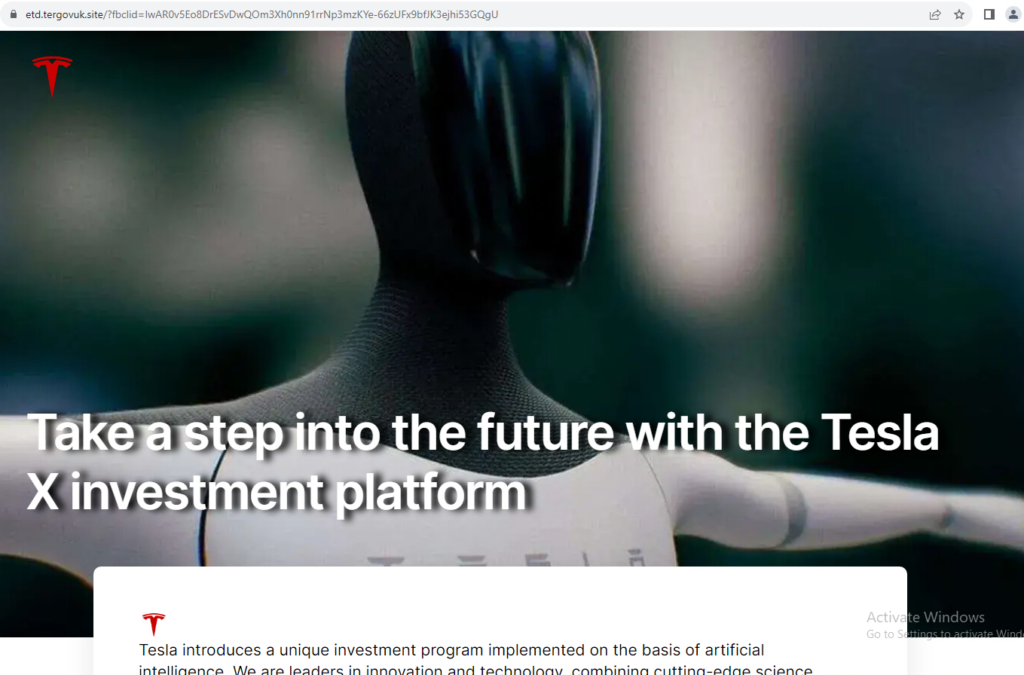
The aim of the scammers in this example is to give the impression of professionalism. Part of the scam is also an appeal to the unrealistic possibility of buying through an ‘automatic robot’ that invests itself and ‘automatically’ earns money.
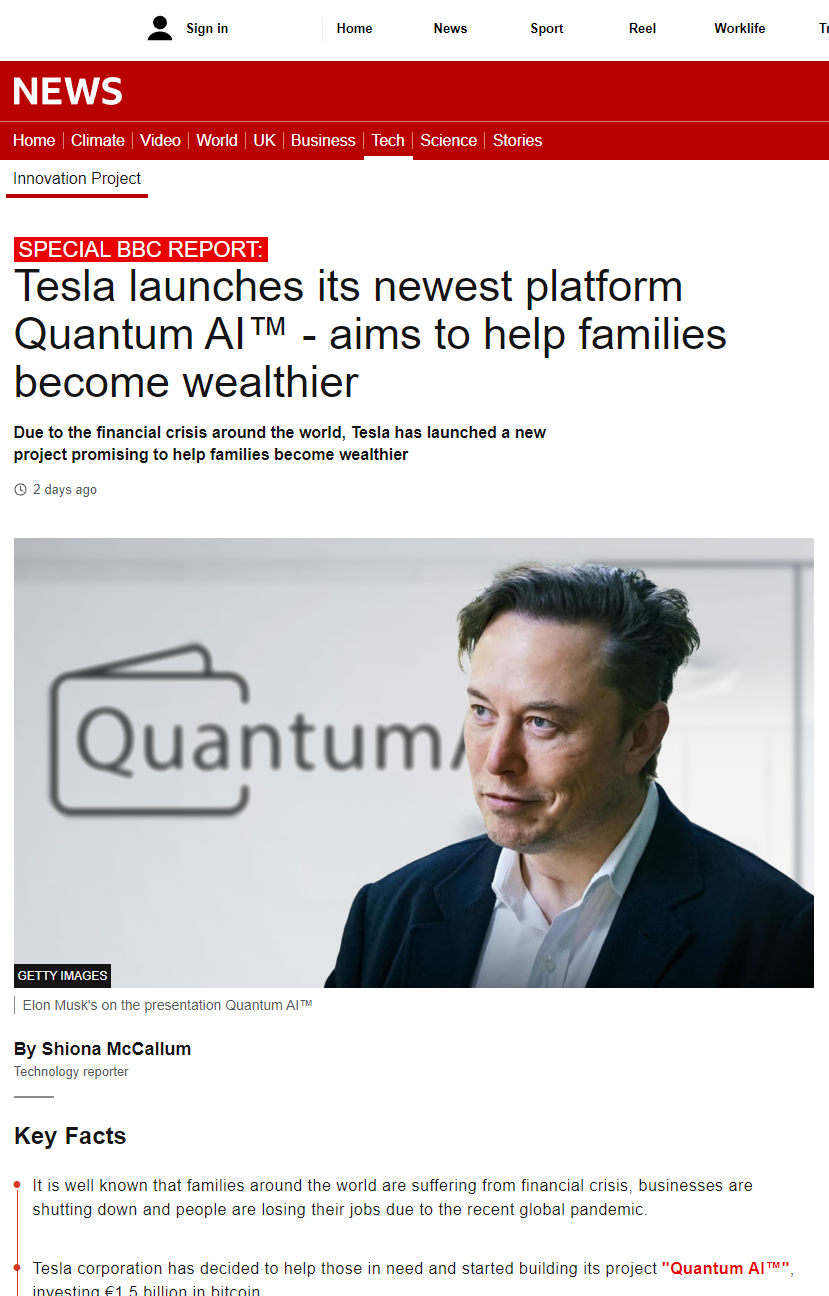
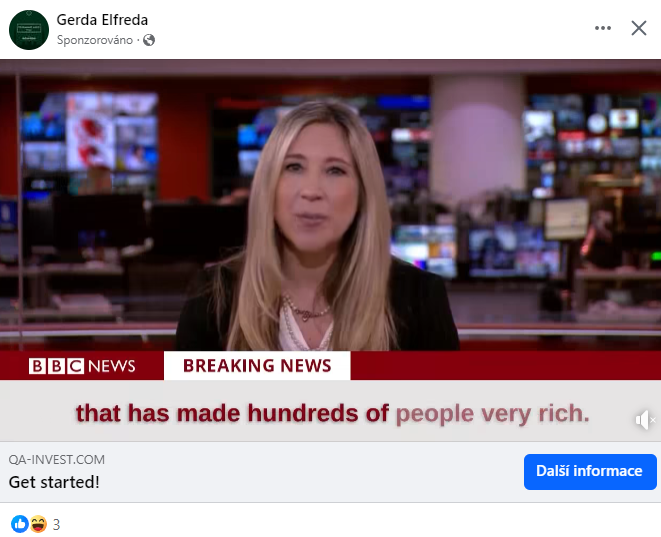
These fake sites can take many forms. Often there are variations that mimic the world’s famous media such as BBC News and many others. These ads take advantage of the targeting of ads that social platforms allow them to do; the ads click through to websites that are created for users in individual countries that correspond to popular news sites in those countries.
The landing pages in this campaign also contain a registration form that requires users to enter their contact information. This information is then sent to the scammer, who then contacts the user either by email or, more often, by phone. Then the actual scamming effort is done over the phone.
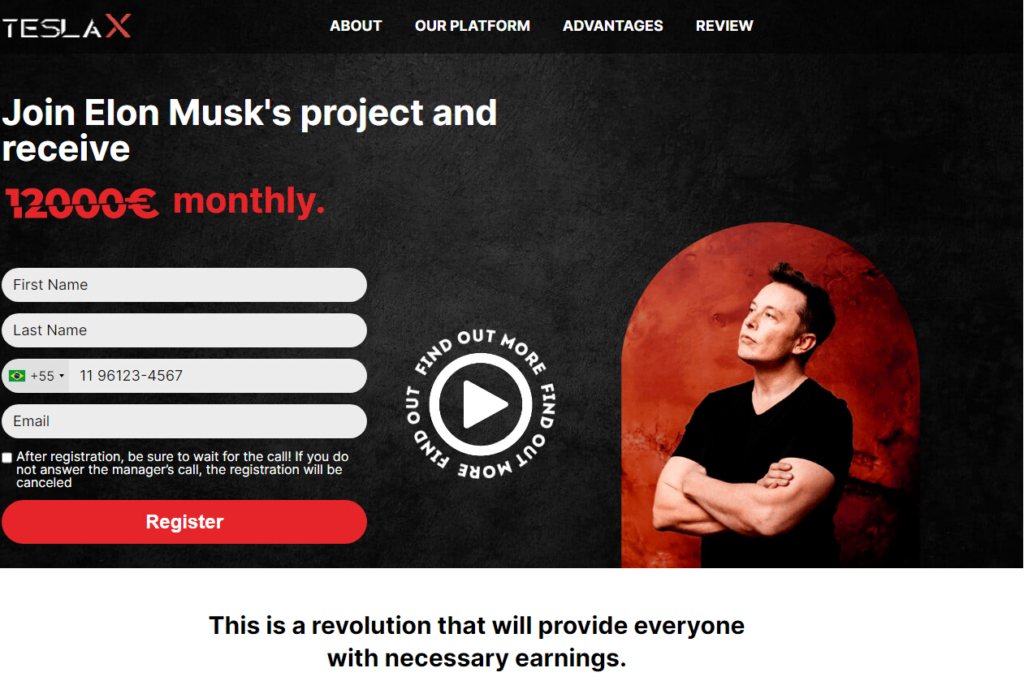
After filling out these fraudulent forms, the user can expect a phone call from the fraudsters. The caller subjects the prospective buyer to a thorough questioning, giving the impression that the financial company is checking not only the solvency of the prospective buyer but also their professional and financial knowledge level. The prospective client is then persuaded to install a remote computer access application, in this case, usually AnyDesk.
To help avoid such scams, we strongly advise the following:
- do not disclose your personal information to people you do not know or cannot authenticate
- do not send photocopied personal documents
- do not send any printed credit card information
- do not give a code that would allow someone to access your computer remotely
- if someone is remotely connected to your computer for any reason, do not log into your online banking
- do not forward or tell anyone SMS bank authorization codes
- do not authorize a payment to a stranger
- keep an antivirus program installed on your computer
- keep your online banking limits as low as possible and increase them only to the actual need to pay a specific payment
Dating Scams
Dating scams, also known as romance scams or online dating scams, involve fraudsters deceiving individuals into fake romantic relationships. Scammers adopt fake online identities to gain the victim’s trust, with the goal of obtaining money or enough personal information to commit identity theft.
Dating scams have garnered increased attention from malicious actors due to the ever-growing popularity of online dating platforms. The accessibility and usual anonymity of these websites make them fertile ground for scammers seeking to exploit people’s emotions and vulnerabilities. Bad actors create fake profiles and engage in emotional manipulation, gaining the trust of unsuspecting users before exploiting them financially or emotionally. As people turn to online dating in greater numbers, scammers see a larger pool of potential victims, which encourages them to invest more time and effort into these deceptive schemes.
We observed a significant increase in dating scams during Q3/2023. The risk ratio of becoming a target rose by 34%.
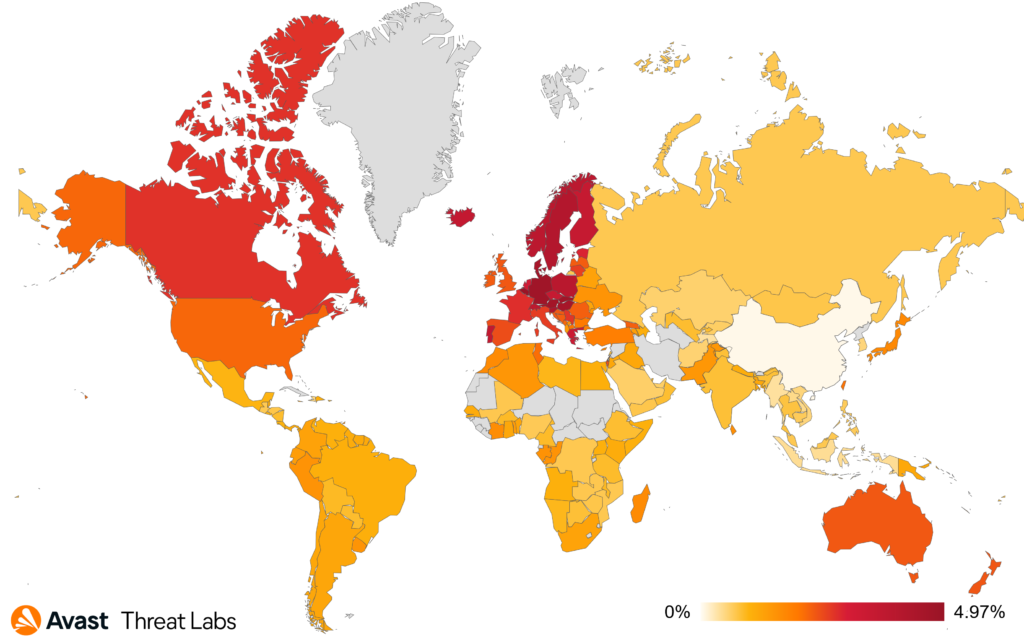
Dating scams are not confined to specific regions, but they do tend to be more prevalent in countries, such as those in Europe, the United States, Canada, and Australia. This can be attributed to a higher proportion of the population engaging in online dating due to increased internet accessibility and smartphone usage.
As illustrated by the heat map below, the highest risk ratio of getting involved in a dating scam is in Belgium (4.97%), Luxembourg (4.86%), Germany (4.76%), Slovakia (4.74%), and Austria (4.66%). In Canada, the risk ratio is 2.74%, closely followed by the United States with the risk ratio of 2.17%. For Australia, the risk ratio is 2.33%.
Love-GPT
We have discovered a tool, which we call Love-GPT, that provides vast functionality over several different dating platforms, providing the capability to create fake accounts, interact with victims, bypass CAPTCHA, anonymize the access using proxies and browser anonymization tools, and more. The author is also experimenting with ChatGPT, the now-famous text-based generative AI, to provide them with more streamlined and believable texts. Because of that, we decided to name the tool Love-GPT. We have identified 13 different dating and social discovery platforms that the tool interacts with:
- Ashley Madison
- Badoo
- Bumble
- Craigslist
- DuyenSo
- Facebook Dating
- likeyou.vn
- MeetMe
- OkCupid
- Plenty of Fish (POF)
- Tagged
- Tinder
- Zoosk
The tool uses ChatGPT API in attempts to streamline the texts. Overall, the tool contains these functionalities leveraging ChatGPT (both finished and under development):
- Create a fake profile description to be used on the dating platforms
- Read the inbox on the dating platform and reply to messages
- Ask for a phone number
- Write a first contact message
- Chat from a template
The tool uses “prompt” values in the API requests’ body to generate the output using ChatGPT. In some of the cases, the whole context is provided to guide ChatGPT for the more precise results:
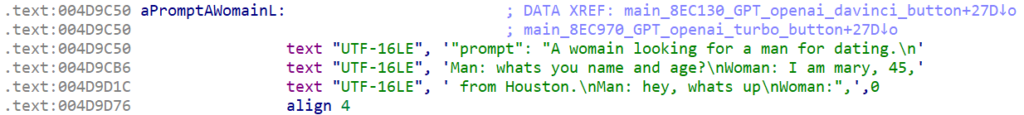
Just for the sake of demonstration, this is what ChatGPT usually returns for similar prompts:
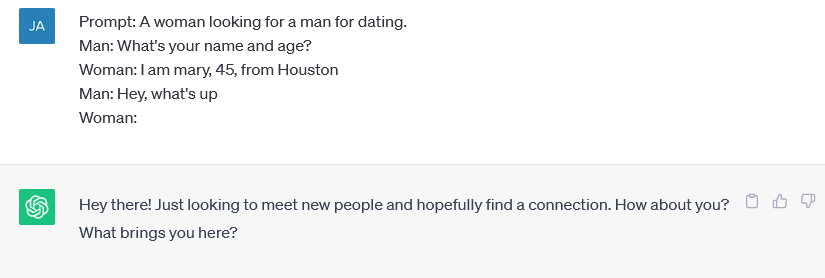
This functionality provides an interesting insight into the upcoming trend of using highly believable texts leveraging generative AI and large language models (LLMs). We can already see that tools misusing the generative AI platforms are emerging and this is likely one of the first in-the-wild examples how the bad actors can misuse it.
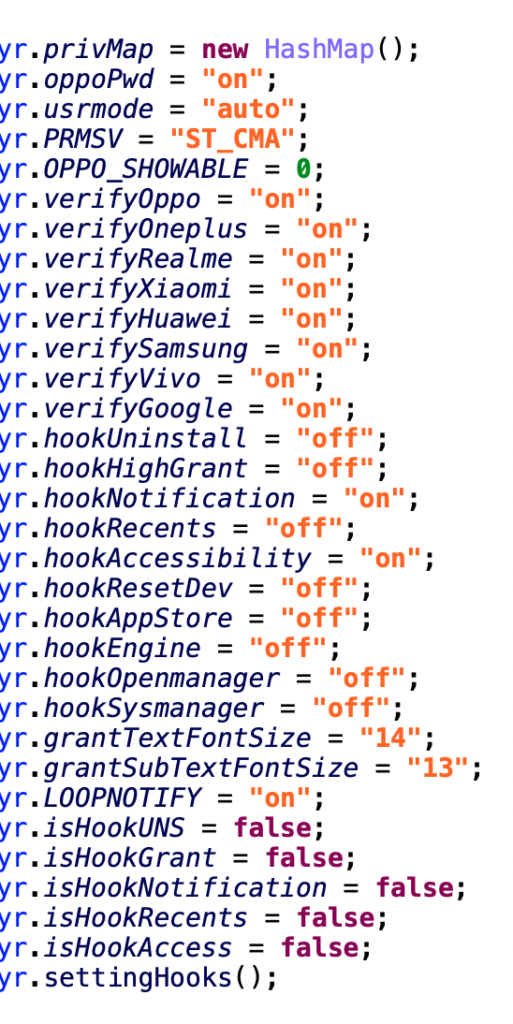
Love-GPT is written in VB6 and contains many control panels for its operations. In total, the tool contains 58 different application forms. One of such form, essential for the whole toolset, can be found below and it is called Account Control Center.
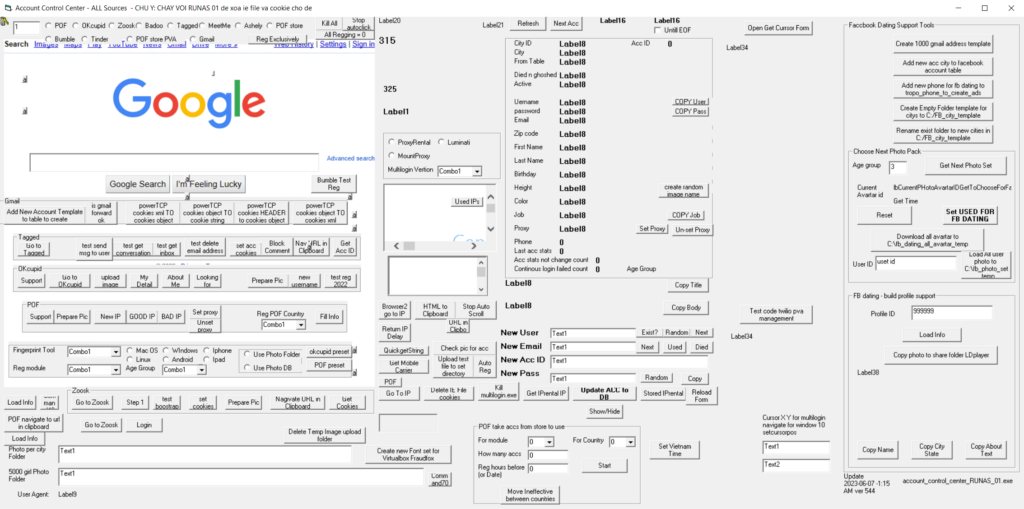
With this artillery, Love-GPT stays under the radar because no one can effectively distinguish connections coming from this specific tool and other regular users accessing the platforms. If you are interested in more technical details, check out our detailed analysis on Decoded.
Tech Support Scams
Tech support scam threats involve fraudsters posing as legitimate technical support representatives who attempt to gain remote access to victims’ devices or obtain sensitive personal information, such as credit card or banking details. These scams rely on confidence tricks to gain victims’ trust and often involve convincing them to pay for unnecessary services or purchase expensive gift cards. It is important for internet users to be vigilant and to verify the credentials of anyone claiming to offer technical support services.
The graph below demonstrates that there was no change for Q3. The downward trend from Q2 continued in the following quarter.
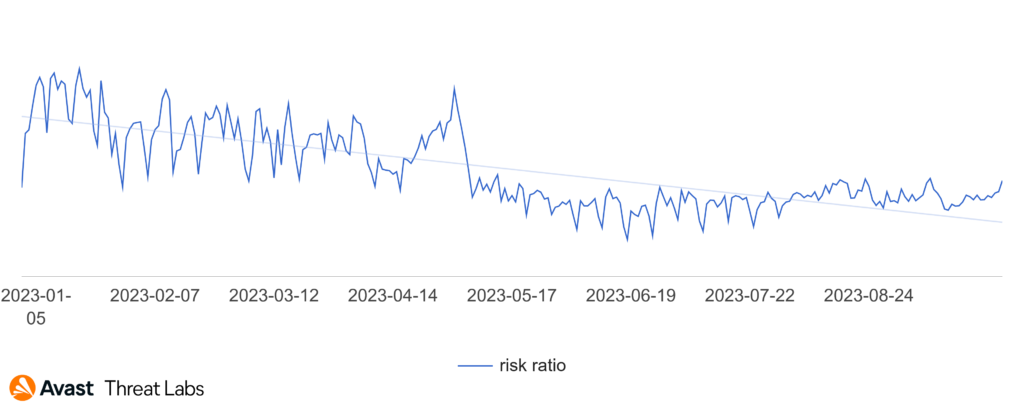
Despite overall downward trend, a notable shift has been observed in the context of detection ratios among different countries. Compared to the previous quarter we have a change in terms of countries with the highest risk ratio. Japan came in second and was surpassed by Germany, Canada saw a big drop when it was surpassed by both the US and Switzerland.
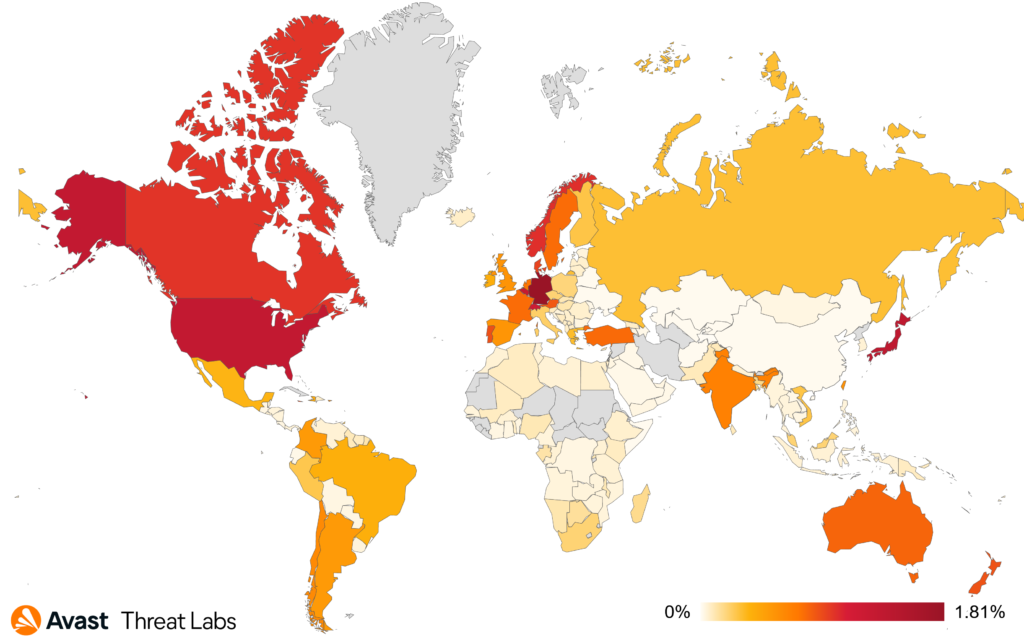
| Country | Risk ratio |
| Germany | 1.81% |
| Japan | 1.37% |
| United States | 1.33% |
| Switzerland | 1.19% |
| Canada | 0.99% |
Even though we have seen a decline for this threat since the beginning of the year, the tech support scam still remains a global threat. Which is very effective, especially for inexperienced users.
For all the years we have been monitoring tech support scams, the design of the site has barely changed. The main goal is to block the browser in such a way that the user is motivated to pick up the phone and call the provided phone number.
On following example, you can see the German variant. At the same time, Germany had the highest risk ratio in the third quarter despite the overall general decline.
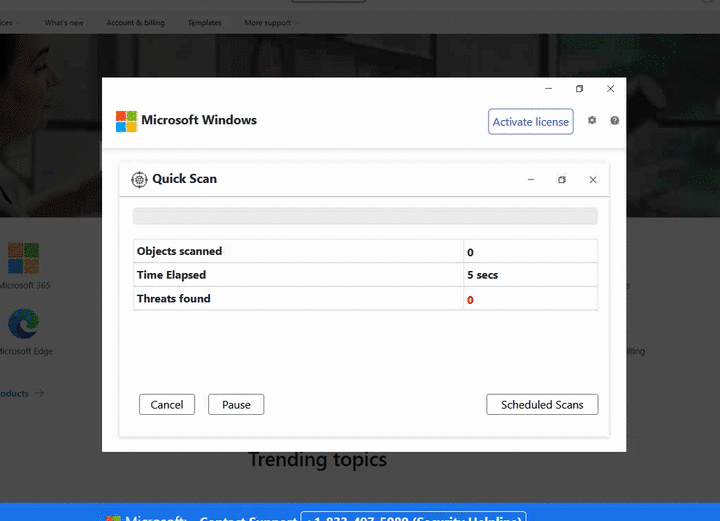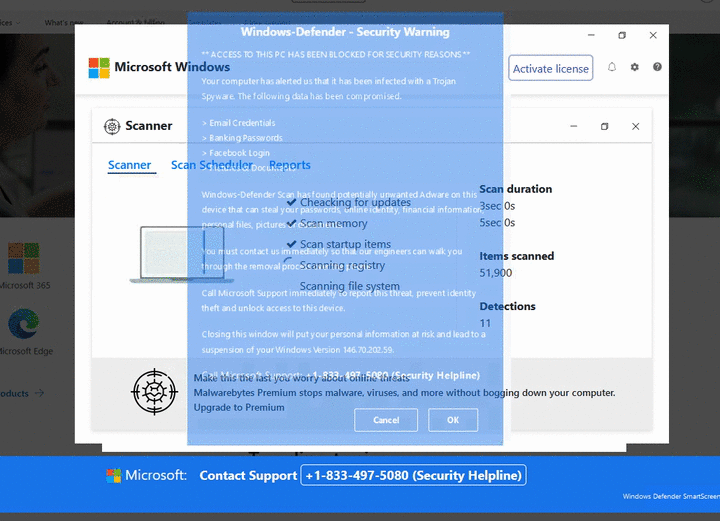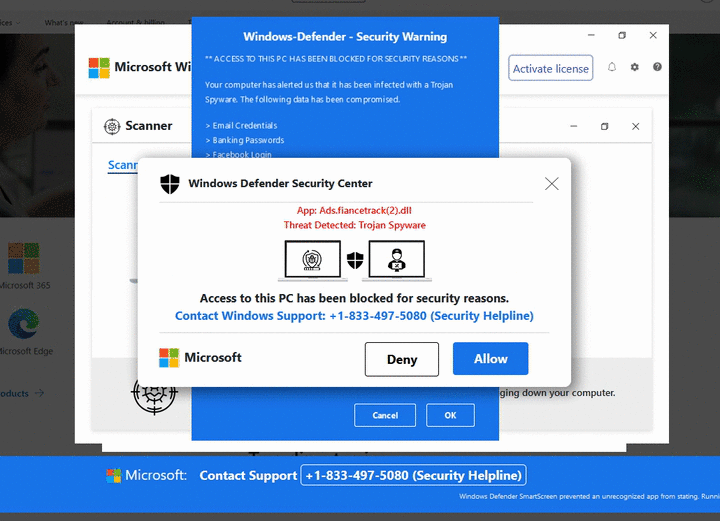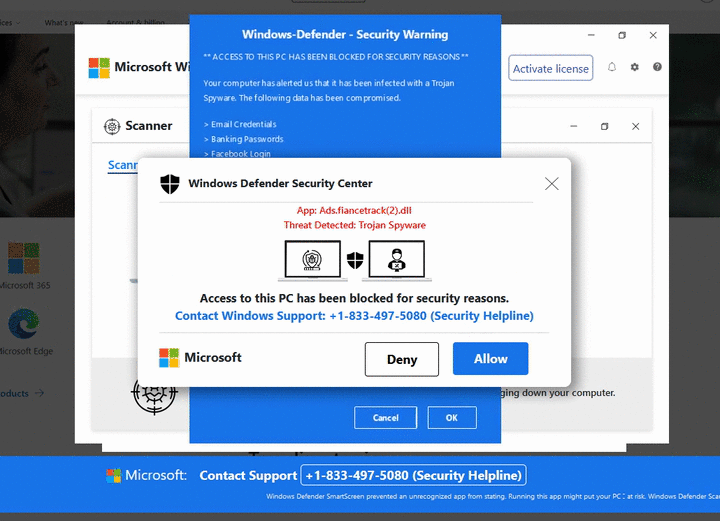
The appearance of the pages is not the only clearly recognizable sign. The URL composition of these scams is no less interesting. It is often possible to recognize the type of campaign and its focus. Sometimes they even contain scam phone numbers as seen in the following illustration.
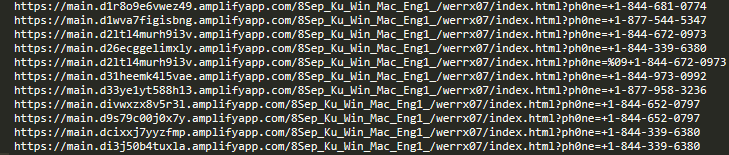
Refund and Invoice Scams
Invoice scams involve fraudsters sending false bills or invoices for goods or services that were never ordered or received. Scammers rely on invoices looking legitimate, often using company logos or other branding to trick unsuspecting victims into making payments. These scams can be especially effective when targeted at businesses, as employees may assume that a colleague made the purchase or simply overlook the details of the invoice. It is important to carefully review all invoices and bills before making any payments and to verify the legitimacy of the sender if there are any suspicions of fraud.
In Australia, the past quarter has been an exception to the otherwise consistent trend, with a significant spike and sudden rise in email-targeted scams. Notably, the rise in protected customers in Australia surpassed even that in the US, which is traditionally at the top of the list. The number of threats we monitored in other regions mainly stayed at very similar numbers compared to previous quarters.
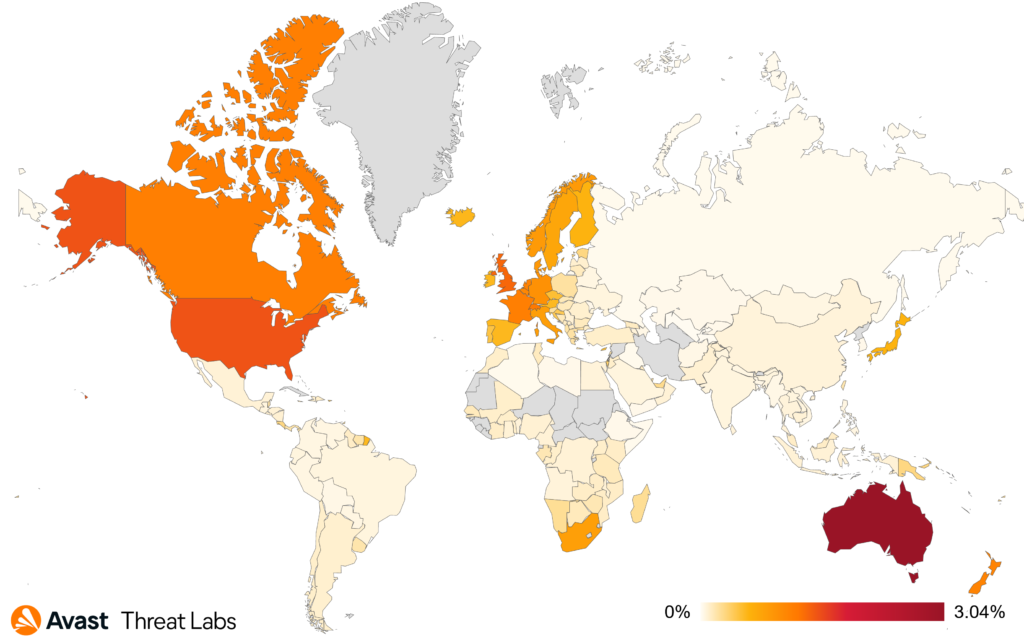
The highest uptick we observed was primarily due to the rise in Australia. Additionally, we noticed that smaller peaks usually occur at the beginning of the working week. This is when people generally sift through their mailboxes, and their vigilance may be lowered because of the larger volume of data they have to process. Therefore, one takeaway is that it definitely helps to take your time and sift through your emails in a peaceful manner, as rushing may increase the chance of falling victim to a scam.
In this quarterly report, we have chosen to spotlight a sample predominantly prevalent in Australia, as it experienced a nearly 30% increase compared to the previous period. This example was selected for its demonstration of many features increasingly noticeable in various other types of scams. The points we will mention should improve your ability to spot similar scams. Below is a breakdown of this deceitful email:
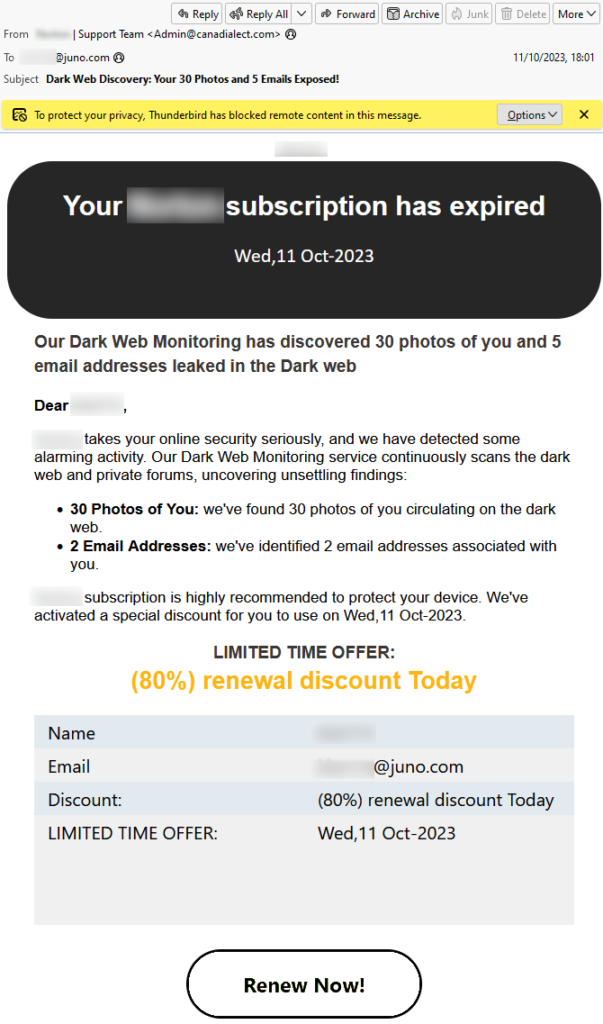
This scam email contains a few typical scam traits:
- Attention-Grabbing Subject Line: “Dark Web Discovery: Your 30 Photos and 5 Emails Exposed!” By creating a sense of immediate danger, the sender aims to provoke curiosity and urgency.
- Impersonation of a Legitimate Entity: The email is supposedly from a “Support Team”, which sounds official and trustworthy. However, the domain ‘@canadialect.com‘ raises eyebrows. Always double-check the authenticity of the domain.
- Urgency and Fear: The email highlights that the recipient’s “subscription has expired,” implying prior engagement or services with them. It also claims a discovery of personal photos and email addresses on the Dark Web.
- Detailed Alarming Findings: The message dives deeper into the ‘findings’, mentioning “30 photos of you” and “2 email addresses” associated with the recipient found in dark web forums. Providing specifics makes the scam seem more credible.
- A Tempting Offer: Following the alarming statements, there is a solution offered – a “(80%) renewal discount Today” on their service. This discount plays on the human tendency to seek quick resolutions when faced with threats.
- Clear Call to Action: The bold “Renew Now!” button at the end of the email serves as a clear directive for the panicked reader. Clicking on such links often leads to phishing sites or direct financial scams.
As a parting word of advice, always be skeptical of unsolicited emails, especially those that invoke fear and urgency. Verify claims independently and avoid clicking on links or downloading attachments from unknown senders.
Phishing
Phishing is a type of online scam where fraudsters attempt to obtain sensitive information including passwords or credit card details by posing as a trustworthy entity in an electronic communication, such as an email, text message, or instant message. The fraudulent message usually contains a link to a fake website that looks like the real one, where the victim is asked to enter their sensitive information.
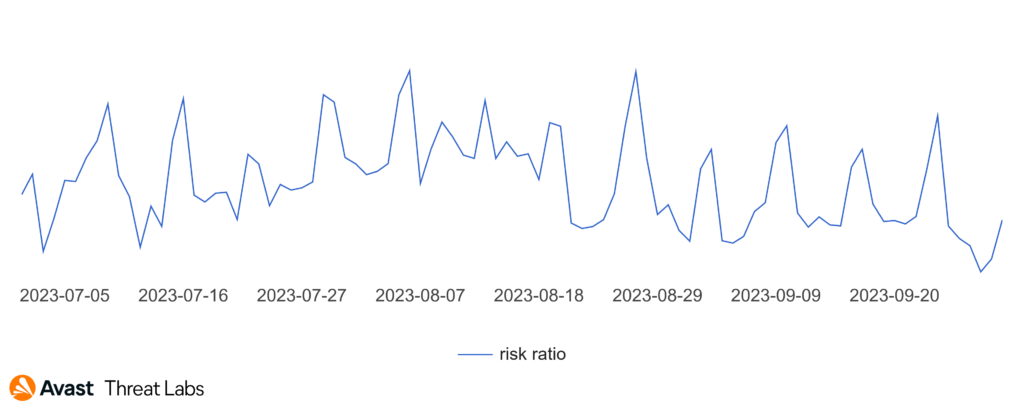
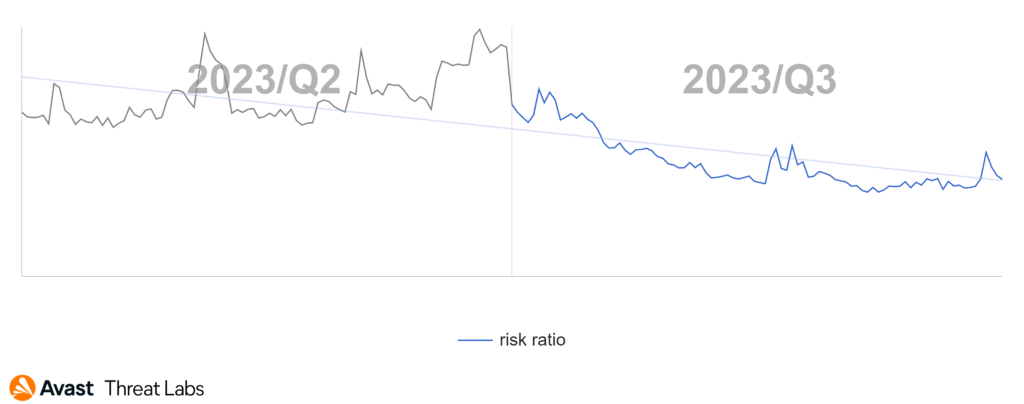
In the Q2/2023 Threat Report, we pointed out that phishing activity was picking up. Now we can confidently confirm that our estimates were correct and after a dip in mid-July, a wave of new samples arrived in August, which then represents a big jump on the chart.
The following graph illustrates the activity of phishing threats across two quarters.
Furthermore, we have observed an emerging trend in phishing delivery methods. Over the past few months, there has been a notable uptick in the use of InterPlanetary File System (IPFS) to disseminate phishing content. This decentralized protocol, designed for storing and sharing files, has become an attractive avenue for cybercriminals.
In addition to IPFS, we have also witnessed cybercriminals turning to the CAR file format, which poses a unique challenge for traditional HTML scanners, allowing it to potentially bypass detection. This exclusive preference for such hosting methods among hackers can be attributed to their ease of deployment and the added complexity in takedown procedures, providing an advantageous environment for malicious activities.
Campaigns that are running on IPFS infrastructure quite often use some type of obfuscation. In most cases these are very basic types and their deobfuscation is very simple.
In this prevalent example you can see that the HTML code itself has been encoded to make it unreadable. Therefore, the JavaScript feature unescape() is used. Despite the fact that the use of this function is not recommended, because it has been deprecated, it often appears in IPFS samples.
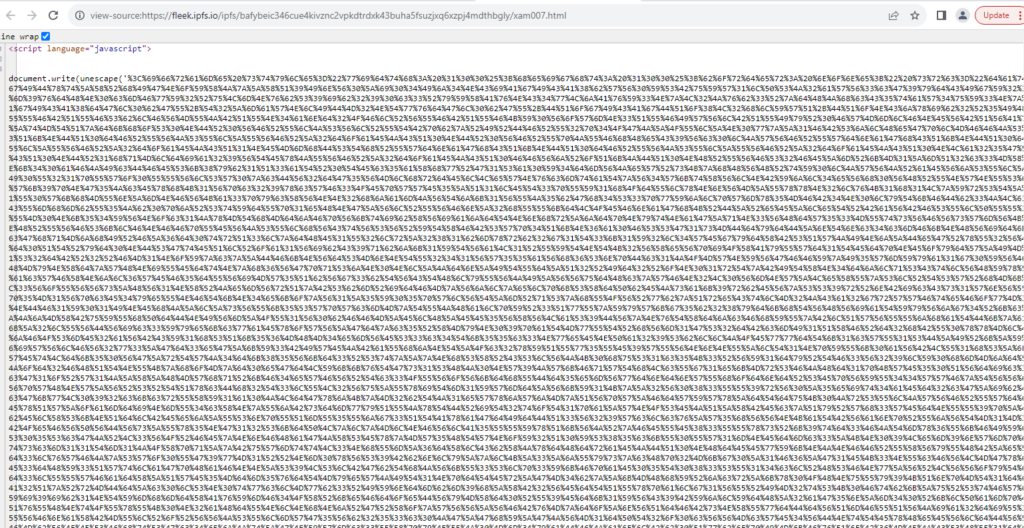
In decoded HTML source code, you can see that scammers are using submit-form.com endpoint for credentials submission.
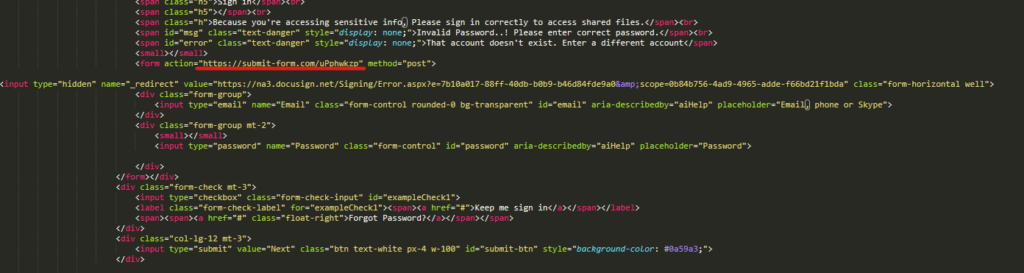
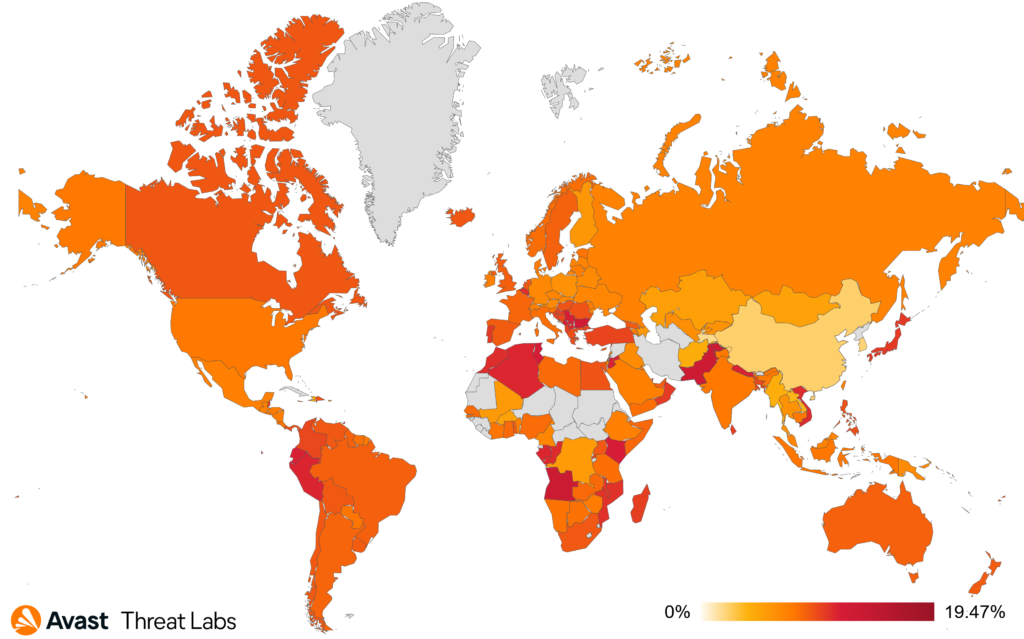
Analyzing the data for Q3/2023 Argentina, Brazil, Mexico, and Spain are countries with a significant increase in Q/Q risk ratio for phishing. Countries with the highest overall risk ration are Macao with 19.47%, Angola with 13.14% or Pakistan with risk ratio of 12.8%.
Phishing has long been the classic and primary way to steal valuable data from users. A growing trend points out that although this is a relatively old method, it is far from being obsolete.
Alexej Savčin, Malware Analyst
Martin Chlumecký, Malware Researcher
Branislav Kramár, Malware Analyst
Bohumír Fajt, Malware Analysis Team Lead
Jan Rubín, Malware Researcher
Mobile-Related Threats
Another quarter, another set of varied and interesting developments hitting the mobile threat landscape. Related to the escalating situation between Israel and Palestine, a spyware mimics a missile warning application used in Israel with the intent of stealing victim data. Also of note is the Xenomorph banker that has added new features and is spreading alongside a Windows info-stealer.
A new strain of Invisible Adware displays and clicks on adverts while the device screen is off, raking in fraudulent ad revenue and draining victim’s batteries and data allowances. We also observed several new versions of SpyNote this quarter, with one breaching the border between spyware and banker malware.
Popular messenger application mods such as Telegram, Signal and WhatsApp continue to be abused to serve spyware. And finally, SpyLoans continue to spread on PlayStore and threaten vulnerable victims with extortion.
Web-Threats Data in the Mobile Landscape
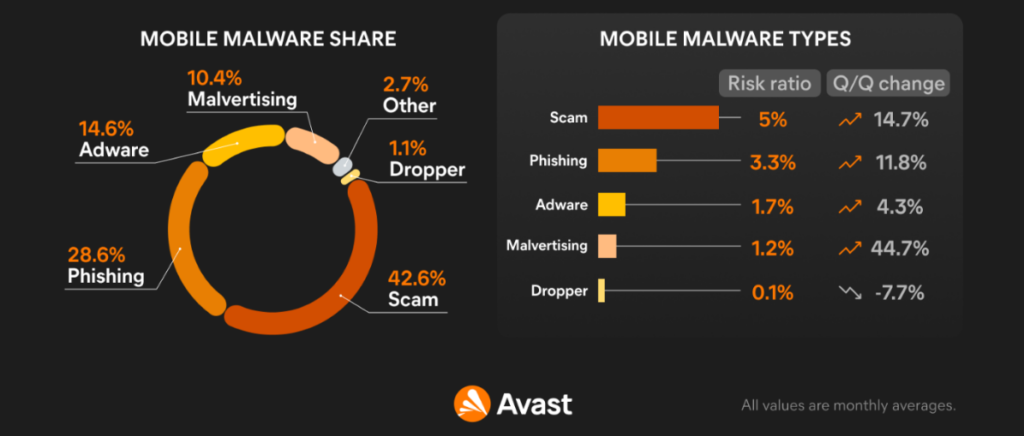
Like on Desktop, we have introduced web-threat related data into our mobile threat report this quarter. This added data reflects a re-shuffle of the most prevalent threats facing mobile users today. As evidenced by the graphic below, scams, phishing and malvertising are responsible for the majority of blocked attacks on mobile.
It makes sense that web-based threats will account for the majority of blocked attacks on mobile as well as desktop. With any malicious app on Android, user action is required to install it and, in most cases, the malware requires the user to enable some permissions for it to activate its malicious functionality. Contrary to this, web-based scams, phishing and malvertising can be encountered through normal browsing activity which most mobile users do every day. These web threats may also be contained in private messages, email, SMS, and others.
Adware Becomes Nearly Invisible
Adware threats on mobile phones refer to applications that display intrusive out-of-context adverts to users with the intent of gathering fraudulent advertising revenue. This malicious functionality is often delayed until sometime after installation and coupled with stealthy features such as hiding the adware app icon to prevent removal. Adware mimics popular apps such as games, camera filters, and wallpaper apps, to name a few.
Despite the addition of web threats data, adware remains one of the most prevalent threats on mobile and retains its top spot among traditional malware apps. Serving intrusive advertisements to its victims with the intent of gathering fraudulent ad revenue, these apps pose a danger and annoyance to both users and advertisers alike.
At the top of the adware list is HiddenAds, followed by MobiDash and FakeAdBlock strains. While both MobiDash and FakeAdBlock have seen over 40% decrease in protected users, HiddenAds is on the rise again with a bump of 15% in protected users. All three strains share some features such as hiding their icon and displaying out-of-context full screen ads that annoy victims. HiddenAds has historically relied on the PlayStore as a mode of spread, while the others generally rely on 3rd party app stores, malicious redirects, and advertisements. Of note is a recent addition to the stealth features of these adware apps; once installed, they display a fake error stating the app is not available in the victim’s region or country with an ‘installation failed’ message. Coupled with hiding its icon, the adware conducts its malicious behavior in the background while the victim remains unaware of the source of the fraudulent ads.
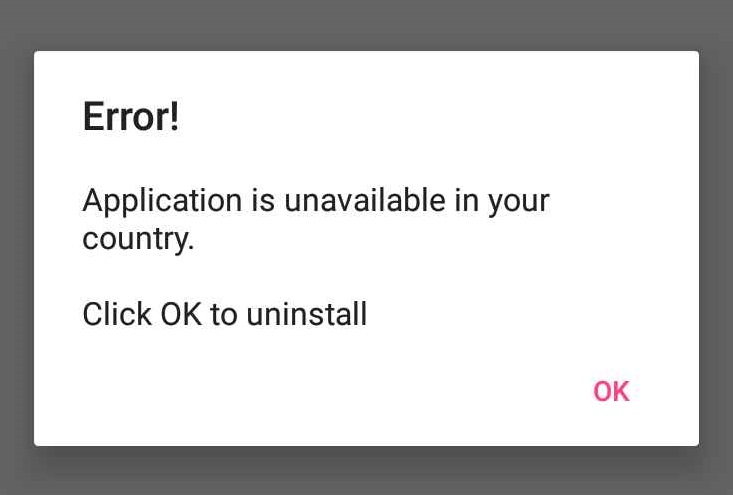
This quarter a new batch of adware dubbed Invisible Adware has snuck onto the PlayStore and gathered over two million downloads. True to their name, these applications try and display advertisements while the device screen is off. In essence, the victim would be unaware their phone is displaying ads while the malicious actors gather revenue through fake clicks and ad views. However, this will likely impact the device battery and potentially incur data charges, while at the same time contributing to ad fraud. The applications request permissions to run in background and ignore battery optimization to conduct their activity. While observed behavior is that of ad fraud, there is also potential for installing other malware or visiting malicious websites.
The average daily protected users slightly increased when compared to last quarter. MobiDash and FakeAdBlock strains have gone down while HiddenAds continue to increase in popularity. Another campaign on PlayStore contributes to the steady numbers this quarter.
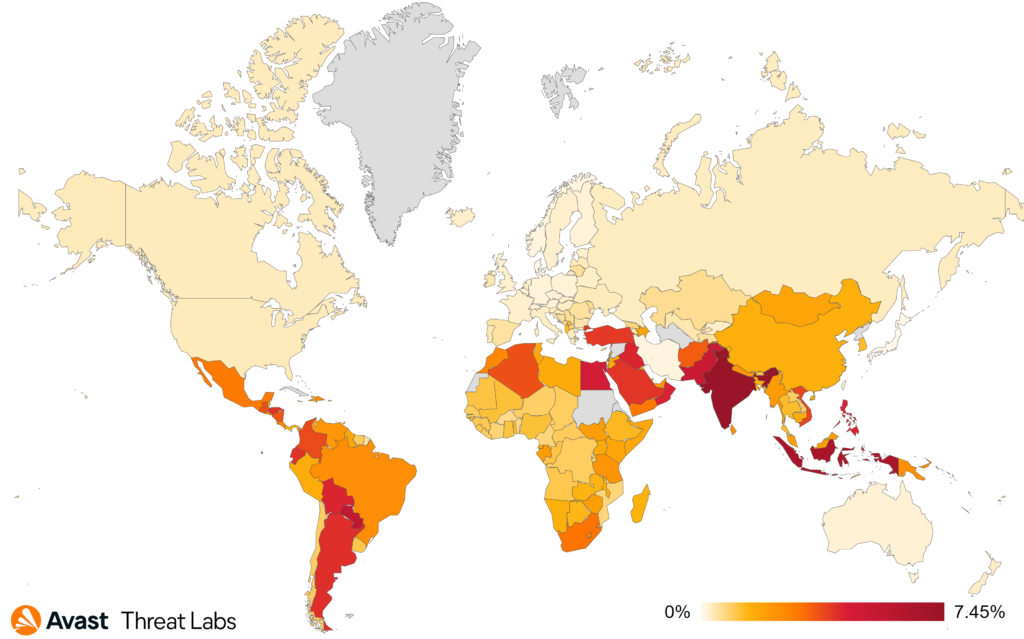
Brazil, India, and Argentina are again at the top of the most affected users by adware this quarter. Argentina saw a 14% increase in monthly affected users. India, Indonesia, and Paraguay have the highest risk ratio this quarter, meaning users is these countries are most likely to encounter adware.
Bankers Welcome SpyNote into the Fold
Bankers are a sophisticated type of mobile malware that targets banking details, cryptocurrency wallets, and instant payments with the intent of extracting money. Generally distributed through phishing messages or fake websites, Bankers can take over a victim’s device by abusing the accessibility service. Once installed and enabled, they often monitor 2FA SMS messages and may display fake bank overlays to steal login information.
Banker evolution continues this quarter with several new strains alongside updates to existing ones. Xenomorph makes a return with some new features, GoldDigger makes an entrance and SpyNote breaches the divide between spyware and bankers. Despite the new arrivals and updates, bankers overall have been on a steady decline in terms of protected users in our telemetry for the last few quarters. Cerberus/Alien maintains its top spot this quarter, trailed by Coper and Hydra strains. We observe an over 20% decrease in monthly average protected users this quarter on all top three banker strains.
Xenomorph is back after a few months hiatus and has evolved again with several added features and a new method of spread. It appears that this new campaign mainly targets bank users in Spain, US and Portugal as well as adding crypto wallets to its repertoire. Using tailored phishing websites disguised as chrome updates, Xenomorph tricks victims into downloading its malicious APK. Once installed, it uses the accessibility service to take over the device, monitoring 2FA messages and can display hundreds of fake bank overlays to its victim to steal login credentials. New features include keeping the device awake, a mimic mode that disguises the malware further and hides its icon, and lastly it can click anywhere on the device’s screen. Interestingly, Xenomorph was observed to be served alongside RisePro, a Windows based info stealer that also targets banking details and crypto wallets. This may point to a coordinated effort between various actors or a single actor behind multiple strains of malware.
A banker targeting victims in Vietnam pretending to be a government portal or a local energy company has been discovered and codenamed GoldDigger. It uses Virbox Protector, a publicly available software that can obfuscate code and prevent both dynamic and static analysis. This appears to be a growing trend in Southeast Asia in recent years, as the use of advanced obfuscation can mean the malware goes undetected for longer. GoldDigger uses fake websites that imitate the PlayStore or phishing in private messages to spread itself. Once on the device, it can steal 2FA SMS as well as personal information and banking credentials.
In an unusual twist, SpyNote has further evolved to the point of breaching into the banking sphere. Recent samples that we have observed are starting to use the spy features of this strain to extract 2FA messages as well as banking credentials and logins. Spreading through smishing and actual phone calls, victims are encouraged to update to a latest version of their banking application, which unfortunately is the SpyNote malware. This version of SpyNote uses the Accessibility service to key log victim’s entries, record the screen and extract confidential information. It also features a defense module that is intended to prevent its removal. As mentioned in previous quarterly reports, we are seeing more spyware strains being re-used in the banking sphere and we anticipate this merging of strains will continue going forward.
Despite continued activity, updated strains and new bankers entering the market, we observe a steady decline in attacked users for several quarters in a row. We estimate that this is due to threat actors using more tailored approaches as of late as we observe less widespread SMS campaigns that were signature of FluBot and others a few quarters ago.
Turkey continues to hold top place with the most protected users, closely followed by Spain, France, and the UK. Most of the banker focus appears to be on Europe, with a few exceptions such as Brazil, Japan, and Australia.
Spyware Telegram Mods Are on the Rise
Spyware is used to spy on unsuspecting victims with the intent of extracting personal information such as messages, photos, location, or login details. It uses fake adverts, phishing messages, and modifications of popular applications to spread and harvest user information. State backed commercial spyware is becoming more prevalent and is used to target individuals with 0-day exploits.
Spyware presence has slightly declined this quarter as Spymax maintains its top spot among the spyware strains with SexInfoSteal and FaceStealer trailing closely behind. New additions to the spyware family this quarter include several new trojanized modifications of popular messenger applications and SpyNote making another appearance. We note the spread of a fake spyware missile alert app in Israel and Spyloans continue their reign as several new samples have been spotted on the PlayStore.
Another version of SpyNote/Spymax was used as part of a short campaign targeting users in Japan with fake SMS messages about unpaid utility or water bills. Containing a sense of urgency, these messages led victims to a series of phishing sites which downloaded the SpyNote onto their devices. Once installed, the malware would direct users to open settings and enable the accessibility service to allow it install further malware and hide itself on the device. It then spied on victim’s personal data and was able to access authenticator apps on the device and steal social media credentials.
In relation to recent escalating situation between Israel and Palestine, it is worth highlighting a spyware Red Alert missile warning app that was distributed through a phishing website. The original app is used by many in Israel to monitor missile warnings. The fake Red Alert spyware app contained identical features with added abilities that allow it to spy on its victims. This included extracting the call log, SMS lists, location, and emails, among others. The malware also features anti-debugging and anti-emulation that attempts to prevent detection. While not documented, it is possible this malware could also be used to deliver fake warning messages, as has happened with other breached missile warning apps.

As noted in the past quarterly reports, mods for WhatsApp, Telegram and Signal are becoming a more popular target for threat actors. We observe another case of Trojanized Telegram mods discovered on the PlayStore, this time targeting Chinese speaking victims. This version appears like the Telegram app at face value, but harvests user information, messages, calls and contact lists in the background. These are then exfiltrated to a cloud service to be further used by malicious actors. Similarly, BadBazaar samples have been spread through trojanized Signal and Telegram apps. Using fake websites to lure victims in, this strain appears to be targeting the Uyghur population. It contains a similar spyware feature set as the trojanized telegram mods. These malicious modifications are around to stay, and users are advised to avoid modifications for popular messaging apps.
Spyloan applications continue to spread on the PlayStore. As reported on by Zimperium, these apps remain mostly unchanged and offer loans to unsuspecting victims in various Asian and South American countries. Once the user installs the application, it requests various invasive permissions under the guise of a credit check. If the victim allows these, the actors behind the spy loans will harvest victim data such as messages, contact lists and photos to name a few. These are then used to extort victims into often paying more than the agreed amount and this harassment may continue even after the debt is paid. Users are advised to avoid unofficial sources of loans to avoid this type of extortion.
This quarter brings a slight decrease in the prevalence of spyware in the mobile sector. While several strains of malicious mods snuck onto the PlayStore, we see an overall decrease in activity and spread of spyware this quarter.
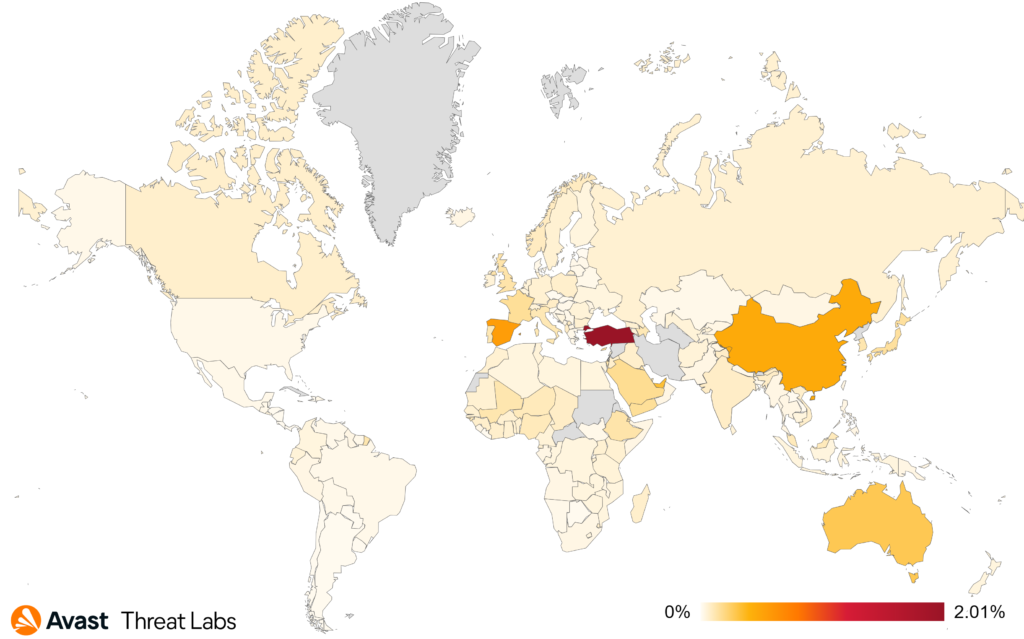
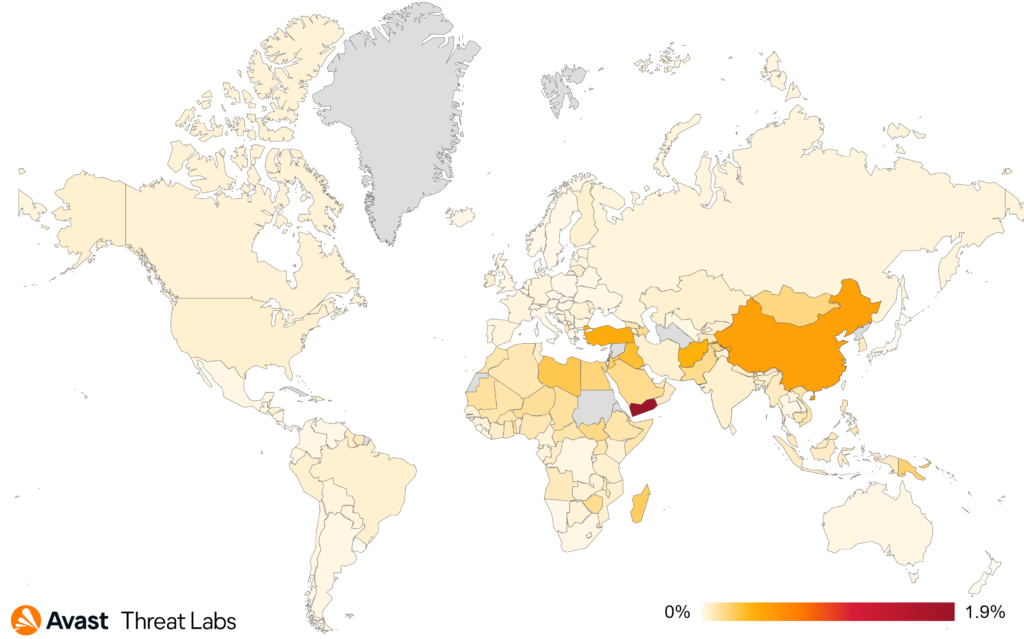
Brazil continues to have the highest number of protected users this quarter, followed by Turkey, US, and India. Yemen has the highest risk of encountering mobile malware in comparison to the rest of the world.
Jakub Vávra, Malware Analyst
Acknowledgements / Credits
Malware researchers
Adolf Středa
Alexej Savčin
Bohumír Fajt
Branislav Kramár
David Álvarez
Igor Morgenstern
Jakub Křoustek
Jakub Vávra
Jan Rubín
Jan Vojtěšek
Ladislav Zezula
Luigino Camastra
Luis Corrons
Martin Chlumecký
Matěj Krčma
Michal Salát
Ondřej Mokoš
Data analysts
Pavol Plaskoň
Filip Husák
Lukáš Zobal
Communications
Brittany Posey
Emma McGowan