For some time now, we’ve been monitoring a new strain of malicious programs that we are referring to as “Meh” (we will explain why later on). It all started when we came across large amounts of files with randomly generated strings at their beginning, followed by a compiled AutoIt script… and what a ride it has been since. In this blog series, we will describe how we peeled away at Meh’s obfuscation and what we found thereafter.
Analysis
Meh is composed of two main parts. The first part is a crypter, we named MehCrypter, that consists of multiple stages, and is distributed as a compiled AutoIt script prepended with a randomly generated string sequence. This string sequence is skipped by the AutoIt interpreter that scans for the magic bytes that determine the file format and effectively obfuscates the file without influencing its functionality.
The second part is a password stealer, called Meh. The stealer is the core of the malware and holds many functionalities. It is capable of stealing clipboard contents, keylogging, stealing cryptocurrency wallets, downloading additional files via torrents, and much more. Nearly all of its functionalities are performed in subthreads, executed from injected processes. We will focus on the password stealer in our next blog post.
MehCrypter
First and foremost, Meh is a password stealer/keylogger. But to get there, we need to chew through several layers of the MehCrypter. First, let’s take a look at a snippet of what the actual crypter looks like from a high level view:
The string at the beginning of the file is randomly generated and its length varies as well. We have seen samples with several MB of data prepended in this area to samples with almost no data at all.
Upon a closer look, however, the file also contains code which is actually a compiled AutoIt script which can be interpreted by the AutoIt interpreter. The interpreter is designed in such a way that it searches the entire file content until it finds the string AU3!EA06. Thus, the whole prepended string is skipped completely and serves only as a confusion technique to avoid detection.
The decompilation yields a very readable script which serves a single purpose: concatenate hard coded hexadecimal strings, decode them, and load the result PE using reflective loading via a custom AutoIt PE loader.
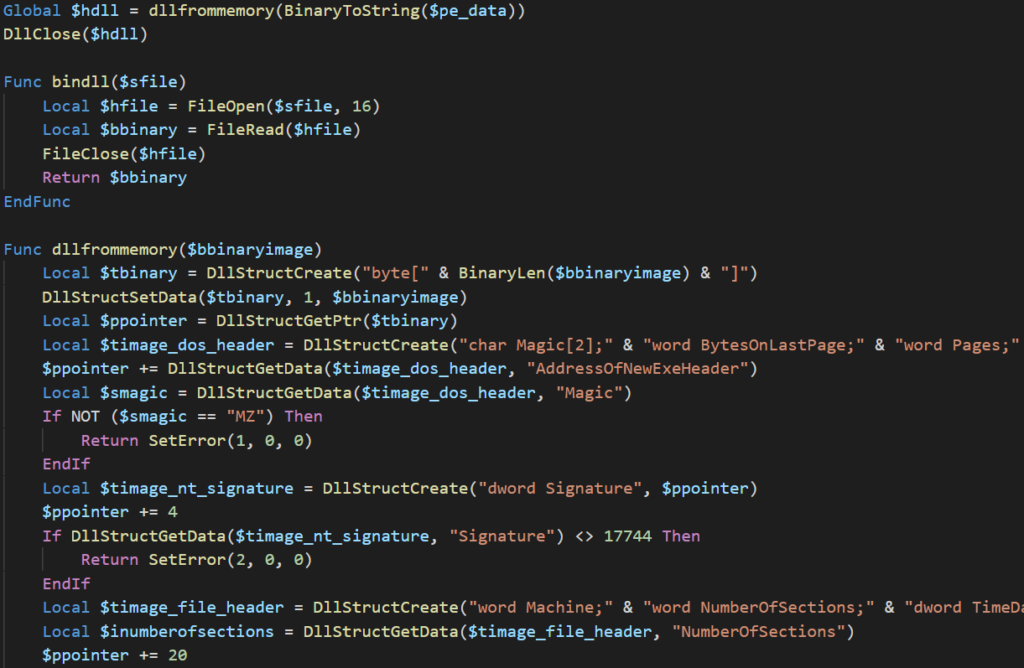
Note that up to this point, the crypter is very generic and we have seen at least five different families using it so far, with the most known being Agent Tesla and XMRig.
MehCrypter dropper
From the script described above, we can manually extract the binary. This binary is a very simple dropper written in Borland Delphi which makes several HTTP POST requests to the C&C server in order to download three additional files:
- http://83[.]171.237.233/s2/pe.bin
- http://83[.]171.237.233/s2/base.au3
- http://83[.]171.237.233/s2/autoit.exe
After these files are downloaded, they are saved into the C:\testintel2\ directory and the file base.au3 is executed (i.e. interpreted by autoit.exe). pe.bin is an encrypted Meh password stealer binary. But we will get to that later.
Furthermore, the dropper also tries to clean up the environment from previous installations of the Meh password stealer, which we’ll discuss in depth in the next part of this blog series. Specifically, it attempts to terminate several processes:
- notepad.exe
- werfault.exe
- vbc.exe
- systeminfo.exe
- calc.exe
These processes are used by Meh for later PE injections. At this stage it also removes its installation folder C:\programdata\intel\wireless.
We would like to mention one file that is also created by the Meh dropper:C:\testintel2\a.txt
This file contains only three bytes: meh. This was so hilarious upon the first look that we decided to name the whole family Meh, including its crypter, MehCrypter.
base.au3 uses the same crypter (MehCrypter) as the original sample. However, it contains a shellcode only instead of a whole PE binary. Thus, it omits the PE loader part and it is executed using the CallWindowProc API function.
base.au3 shellcode
base.au3 shellcode has two parts. In the first part, the shellcode constructs yet another shellcode on the stack. We can see its beginning at the address 0x00000025. The second shellcode is executed later via an indirect jump.
The second part is an unencrypted binary file. The MZ header starts at the address 0x0000168A.
As we might guess, the second (constructed) shellcode is in fact another PE loader that just loads and executes the hardcoded binary file. This binary is the last stage of the crypter’s envelope and is a stager for the Meh password stealer.
Meh stager
After the long journey of peeling away MehCrypter’s layers, we finally reach the Meh stager, written in Borland Delphi. This stager is the third (and final) PE loader, which decrypts the aforementioned pe.bin file using a very simple XOR cipher.
pe.bin decryption
The decryption function takes two inputs – a base64-encoded ciphertext and a key. Fortunately, both of these are contained in the pe.bin.
The contents of the pe.bin file can look like this:
As can be seen in the screenshot above there is a randomly generated string at the beginning of the file, similarly to the initial AutoIt script. After a series of random letters, however, we can see a string delimited by pipes, followed by a base64 string. These are exactly the parameters the decryption function needs. A corresponding decryptor written in Python can be found below.
The key, as shown above, is not used in this exact form. The malware replaces the first character of the key-string with “a” and omits the last letter. Thus, the actual key is asUzmbiYd.
After that, the base64 string is decoded and a one-byte key is derived from the XOR key string:
The bit-negated version of this one-byte key is then used to decrypt the content of the file. As mentioned before, the cipher is a simple XOR cipher:
Due to a bad key-derivation procedure, the actual size of the key-space is just 256 keys. Therefore, an analyst can bruteforce the decryption key, e.g. by trying to decrypt the PE file header looking for MZ magic bytes.
The whole decryptor written in Python can be found here.
Campaign overview
The surge of Meh and MehCrypter infections started mid-June where we were counting several thousands infections per day. The malware is most prevalent in Spain where Avast blocked infection attempts on more than 80,000 of our users. The second most targeted country is Argentina with more than 2,000 attacked users.
Summary
In this post, we looked into a MehCrypter family that is used to obfuscate many malware families circulating in the wild. One of these families is the Meh password stealer, which we will describe in detail in the next part of the series, so stay tuned!
IoCs
| File name | Hash |
| Initial AutoIt script | 94c2479d0a222ebdce04c02f0b0e58ec433b62299c9a537a31090bb75a33a06e |
| Stage 1 – Dropper | 43bfa7e8b83b54b18b6b48365008b2588a15ccebb3db57b2b9311f257e81f34c |
| Stage 2 – Shellcode | 34684e4c46d237bfd8964d3bb1fae8a7d04faa6562d8a41d0523796f2e80a2a6 |
| Stage 3 – Shellcode 2 | 2256801ef5bfe8743c548a580fefe6822c87b1d3105ffb593cbaef0f806344c5 |
| Stage 4 – Meh stager | 657ea4bf4e591d48ee4aaa2233e870eb99a17435968652e31fc9f33bbb2fe282 |
| pe.bin | 66de6f71f268a76358f88dc882fad2d2eaaec273b4d946ed930b8b7571f778a8 |
| base.au3 | 75949175f00eb365a94266b5da285ec3f6c46dadfd8db48ef0d3c4f079ac6d30 |
| autoit.exe | 1da298cab4d537b0b7b5dabf09bff6a212b9e45731e0cc772f99026005fb9e48 |
| URL |
| http://83[.]171.237.233/s2/pe.bin |
| http://83[.]171.237.233/s2/base.au3 |
| http://83[.]171.237.233/s2/autoit.exe |
Repository: https://github.com/avast/ioc/tree/master/Meh




