I recently discovered a large campaign of HiddenAds on the Google Play Store, spreading via gaming apps. The initial discovery was made through an apklab.io automated detection that was based on similar features of a previous HiddenAds campaign that was present on the Play Store. Upon further analysis of the app through apklab.io, Avast’s mobile threat intelligence platform, I was able to identify a wider campaign by comparing similar activities, features, and network traffic. In total, I found 47 apps.
The apps’ poor reviews on the Play Store, combined with their capability to hide their icon and display ads outside the apps confirmed that they are part of the HiddenAds family.
One app leads to 47
Once I determined that the Dancing Run app I found belongs to the HiddenAds family, I utilized apklab.io to conduct a search for similar apps.
I started my search by looking at the app’s entry points, as apklab.io groups apps with the same activities, receivers and services. The ability to see how many apps share an entry point is a useful feature in identifying unique shared features, and helped me find a set of entry points created for the original app.
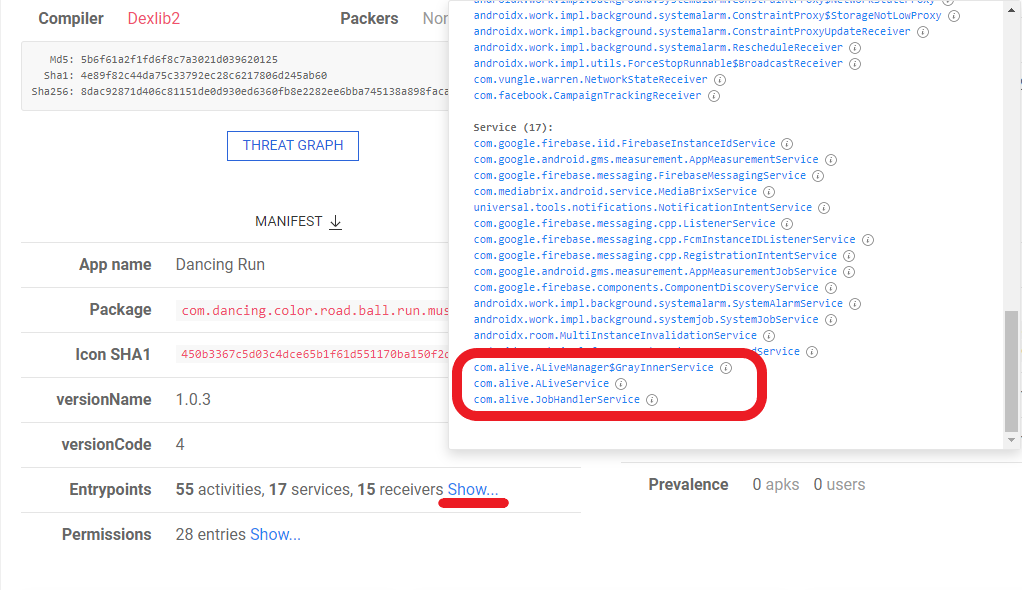
I then searched the apklab.io database for apps with these unique entry points by using service:com.alive.ALiveService. To further narrow down the search results, I added the is:PlayFrosting parameter to find similar apps on the Play Store.
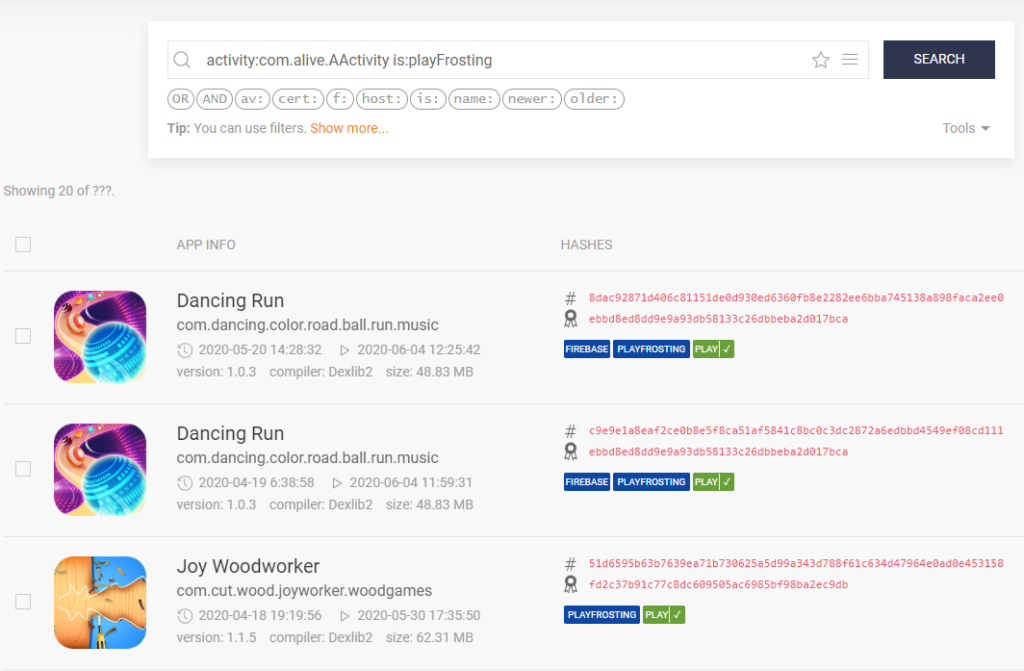
Apklab.io allows various filtering criteria in its search. I conducted another search with f:HideApplicationIconFromLauncher to identify apps that hide their icon from the launcher.
Continuing the search, I was able to discover more similar apps using the network dump dynamic feature. It collects information on the app network activity and in this case a specific URL was accessed by several of these apps.
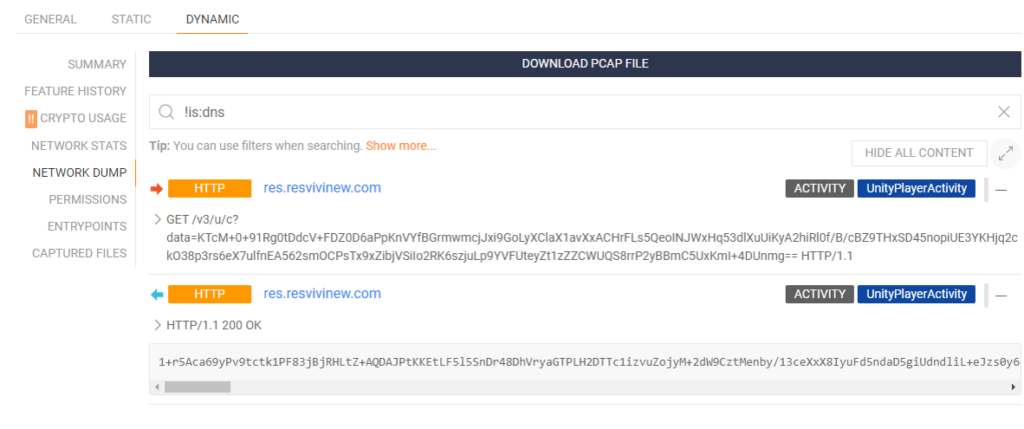
I used the URL search filter host:”res.resvivinew.com” and found additional HiddenAds apps that shared this URL connection.
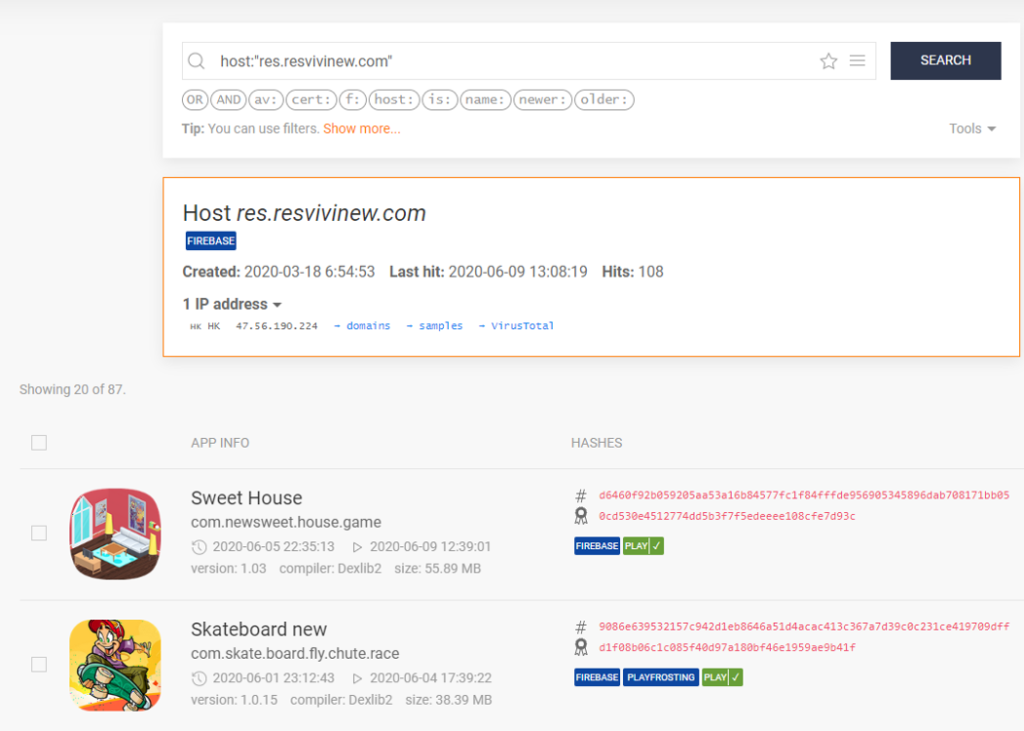
I combined these methods of searching with other accessed URLs and activities. I was able to detect over 200 HiddenAds APKs. Of these, 47 apps were active on the Play Store. Apklab.io is a great tool for initial discovery and assessment of how widespread a particular family of apps is.
Taking a closer look
When diving deeper into the apps’ code, it became apparent that the apps are in fact repackaged games with an added layer of HiddenAds code. The newer versions of these apps only had slightly different code, but overall the apps all have nearly identical HiddenAds code. The added code is intentionally obfuscated and contains the ability to hide the icon from the launcher. The apps wait for a period of time after installation, then initiate the hide icon process.
In Throw Master, one of the apps I analyzed, a ten minute delay execution timer starts as soon as the app is installed. This allows enough time to play the first three free levels of the game. The game regularly checks the timer while in use. Meanwhile, a broadcast receiver monitors the USER_PRESENT broadcasts which indicates if the phone is unlocked. If it is, it resets the timer. Once the ten minute delay is reached, the hide icon job is triggered.
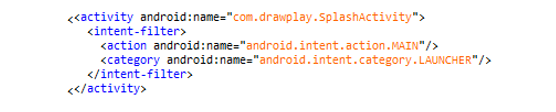
The process starts by disabling the main launcher activity, in this case SplashActivity is the main launcher activity.
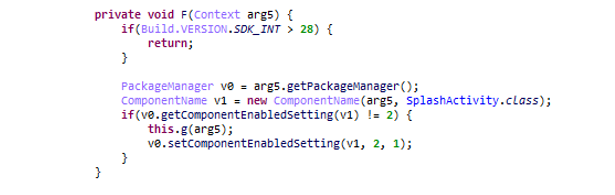
PackageManager is used to hide the icon from the launcher through setComponentEnabledSetting. This setting disables the main launcher activity and as a side effect hides the app’s launcher icon.
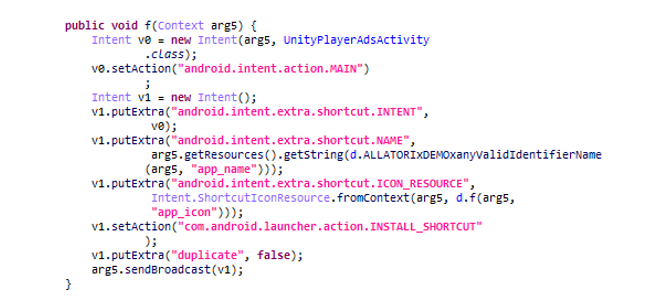
The app then creates a shortcut on the home screen using the INSTALL_SHORTCUT launcher action. The shortcut differs from a launcher icon in that, even if deleted, it doesn’t remove the application from the device.
The user may figure out the app is the source of the ads and delete the newly created shortcut, however, this will not remove the app from the device. To the users’ frustration, the ads will continue until the app is removed via the device app settings.
Once the icon is hidden, the apps start to display ads outside of the apps. The apps have the ability to display intrusive ads over other apps via banners and notifications. Several apps even open the browser to display additional ads.
Play Store warning signs
Another shared attribute of these apps is that the developer only has a single app on their developer profile with a generic email address. Similarly, the Terms of Service are identical for all of the apps, likely pointing to an organized campaign by one actor. These warning signs could potentially be recognized by users.
The developers likely spread out the apps under different developer profiles to avoid detection and to make the adware removal more difficult.
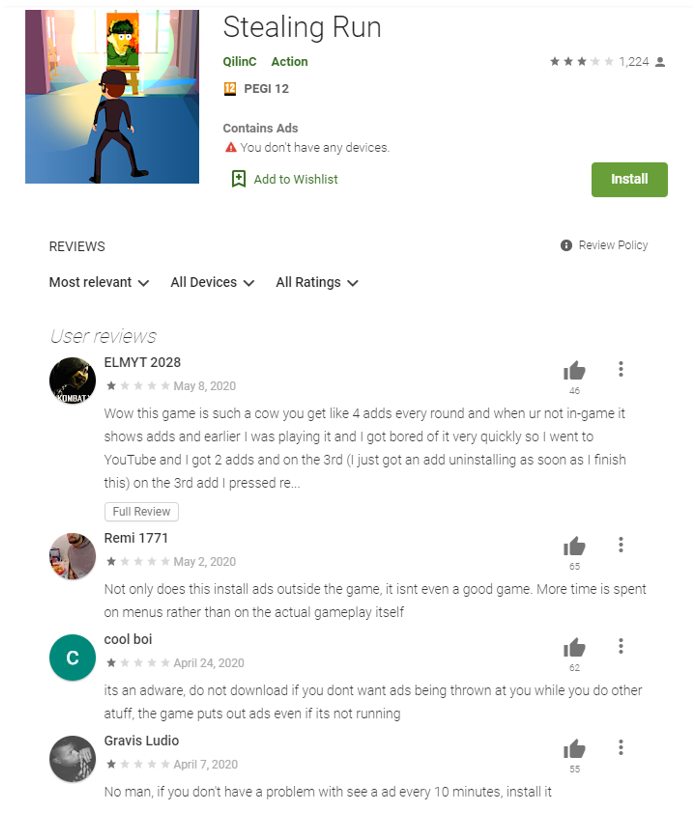
The app reviews are a potential telltale sign for the regular user as they showcase the frustration and malicious features present in the app.
Spread
Combined, the apps have been downloaded more than 15 million times. Several of these apps have been on the Play Store since early May, contributing to their high downloads.
| App Name | Downloads |
| Draw Color by Number | 1,000,000 |
| Skate Board – New | 1,000,000 |
| Find Hidden Differences | 1,000,000 |
| Shoot Master | 1,000,000 |
| Spot Hidden Differences | 500,000 |
| Dancing Run – Color Ball Run | 500,000 |
| Find 5 Differences | 500,000 |
| Joy Woodworker | 500,000 |
| Throw Master | 500,000 |
| Throw into Space | 500,000 |
| Divide it – Cut & Slice Game | 500,000 |
| Tony Shoot – NEW | 500,000 |
| Assassin Legend | 500,000 |
| Stacking Guys | 500,000 |
| Save Your Boy | 500,000 |
| Assassin Hunter 2020 | 500,000 |
| Stealing Run | 500,000 |
| Fly Skater 2020 | 500,000 |
| Disc Go! | 500,000 |
Most downloaded HiddenAds discovered on Play Store.
It appears the campaign initially targeted users in India and South East Asia. Based on previous HiddenAds campaigns, the apps likely spread through game ads focused in these regions. Due to the generic developer details and Terms of Service, I cannot pinpoint where the developers of these apps are from. The map below indicates the initial 200 downloads of the Find 5 Differences app recorded by Avast Mobile Security. The other investigated apps share a similar trend of initial downloads.
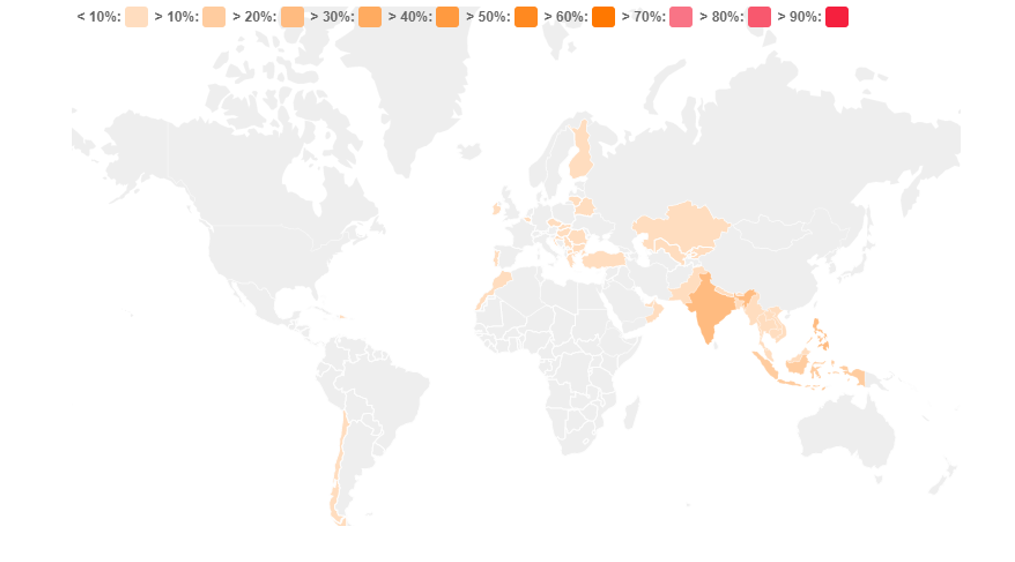
I believe that the initial spread across other regions that can be seen in the map above, is likely “collateral damage” caused by the apps’ presence on the Play Store.
While this gives us a snapshot of the initial spread, the current prevalence of these apps differs. Based on Avast’s internal statistics, this HiddenAds campaign is currently most prevalent in Brazil, India and Turkey.
| Country | Share |
| Brazil | 21% |
| India | 8.10% |
| Turkey | 6.30% |
| Argentina | 5.60% |
| Mexico | 3.70% |
Percentage spread of Avast users who have downloaded at least one of the HiddenAds apps in the last two weeks by country.
The HiddenAds campaign was able to spread globally due to its presence on the Play Store. Once the apps are removed from the Play Store, the user numbers will likely go down rapidly.
Summary
Thanks to apklab.io, we were able to find 47 apps violating Google’s developer Ads and Spam policies, in addition to the original app we found. We have reported these to Google, and at the time of posting, Google removed 30 of the apps. Campaigns like HiddenAds apps may slip into the Play Store through obfuscating their true purpose or through incremental version updates that introduce intrusive ads and hide icon features once they have been downloaded by users. It is difficult to prevent future campaigns from making their way onto the Play Store, as the actors behind the campaign use one-off developer accounts for each uploaded app. Avast will monitor further developments of the HiddenAds campaigns through apklab.io features, as well as via automated detections.
Samples
Due to the number of samples, we’ve only selected the APKs that were present on the Play Store and put them into this spreadsheet.
Tips on avoiding adware
- Install a trustworthy antivirus app. Antivirus acts as a safety net and can protect you from adware.
- Exercise caution when downloading apps. Read app reviews before installing a new app, carefully reading both positive and negative reviews. Notice if reviewers comment on whether or not the app does what it says it will do. If an app’s review includes comments like “this app doesn’t do what it promises” or “this app is packed with adware,” – think twice about downloading the app! Reviews like this are a sign that something isn’t right.
- Always carefully check app permissions, closely looking to see if they make sense. Granting incorrect permissions can send sensitive data to cybercriminals, including information such as contacts stored on the device, media files and insights into personal chats. If anything seems out of the ordinary or beyond what seems appropriate, the app should not be downloaded.




