There has been quite a discussion regarding Google’s recent introduction of .zip, .mov, .phd (and other variations) as top-level domains (TLDs). The opinions in the cybersecurity community can be distilled into two camps. A fair number of experts assume that this move from Google will likely cause even more confusion for non-tech savvy users navigating the internet. The second camp thinks otherwise. That it basically is a difficult realm to navigate in already and that users rarely pay attention to the URL and its components. When digging into this topic and our data, we identified that cybercriminals have already started abusing .zip domains to mislead users into thinking they are downloadable files, instead of URLs. Our research shows that out of the top 30 .zip domains blocked by our threat detection engines, one third abuses names of leading tech companies such as Microsoft, Google, Amazon and Paypal, to trick people into thinking that they are files of trusted companies.
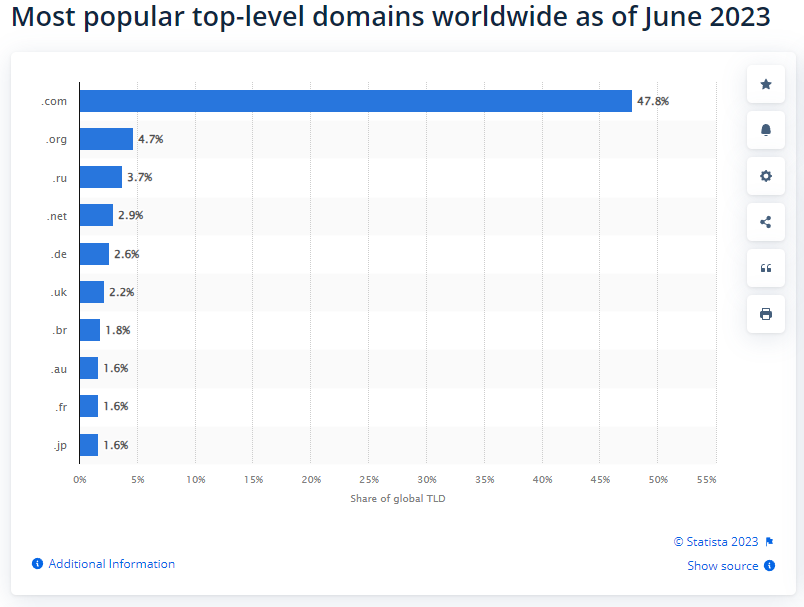
In the early days of the internet, TLDs were introduced to streamline the process of browsing and sorting through online content. The main reason for using domain names and TLDs was to make navigation around the web more user friendly. Also, at the time geographical location was also important. The well.sf.ca.us, originally pointed out by Ars Technica, is a great example of using the TLD to denote its geographical location, in this case San Francisco, California, in the United States of America. It also helps us distinguish the basic nature of the server we are visiting. .com, associated with the commercial nature of a website, and .org, associated with nonprofits, are probably the most common TLDs used to denote the characteristics of a domain. According to Statista, .org and .com account for 50% of all TLDs worldwide.
The purpose of TLDs has become much more blurred recently (past several years). They can also serve as part of branding efforts now, such as the .lidl or .edeka TLD or other exotic TLDs that come to my mind. For example, .beer, .motorcycles, .plumbing, .soccer, .taxi, and so on. There’s little that isn’t achievable. When the Internet Corporation for Assigned Names and Numbers (ICANN), the non-profit which oversees and manages unique Internet identifiers, like IP addresses and domains, last expanded the scope of TLDs, they set the evaluation fee at $185,000, limiting applicants to only established entities, whether public or private. It’s undeniably a high-priced venture.
So, what issues could arise with a .zip TLD? Personally, I see a significant concern in the potential for file confusion and the consequent difficulty distinguishing between local and remote sources, which could pose a security threat. For educational purposes I crafted a prototype email that leverages the fact that the attachment and the link can point to completely different locations.
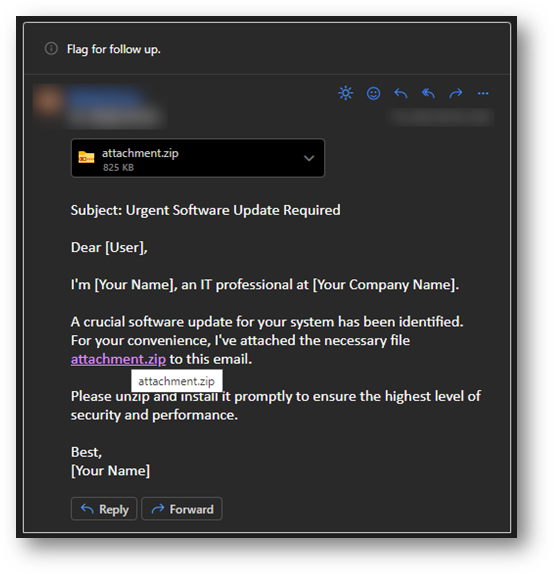
It appears that using a .zip domain to deceive users can be remarkably easy. Moreover, the link preview can be manipulated to hide the protocol used, such as HTTP(S). This definitely helps the attacker to lure the user where they want.
It seems that we have reached a point where the original purpose of making URLs understandable to the public is gradually deteriorating over time. Which address seems more suspicious to you: https://52.144.44[.]169 or latestupdate[.]zip (which resolves to that IP)? I have my doubts as well. I do not imply that most of the .zip domains are or will be inherently malicious. However, I foresee a certain number of domains that, if not registered by entities closely related to their respective products, are very unlikely to be used for legitimate purposes. Looking at the top blocked domains by Avast with a .zip TLD we see that there are many mimicking legitimate companies. Also, there is a second group that tries to imitate files.
The most interesting domains are those that are closely related to large service providers, which are well known to the public. These include microsoft-office[.]zip, microsoft[.]zip, csgo[.]zip, google-drive[.]zip, microsoftonedrive[.]zip, googlechrome[.]zip, and amazons3[.]zip. Other perfect examples that I would describe as well designed are those with a pdf keyword combined with a subdomain. Namely 226x227.pdf[.]zip, 2023-05.pdf[.].zip, cv3.pdf[.]zip, temp1_rsbu_12m2021.pdf[.]zip. Checking on who.is yields expected results.
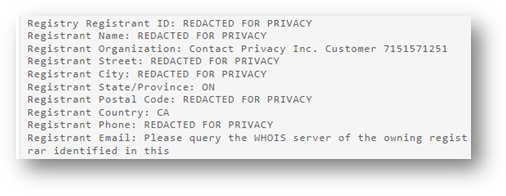
Most of the time, when a registrant’s information is redacted from the WHOIS database, it clearly raises suspicions. It’s definitely not the most important red flag, but it’s a piece of the puzzle. When combined with the domain name, we can be fairly certain that there might be some shady activities going on with a high degree of certainty.
Another perfect example of taking advantage of these domains is the usage of @ in a URL. The @ character is part of the authentication scheme (user:password@host), and it holds a special significance in the URL. Since this method is strongly discouraged nowadays and rarely used the chance of a user spotting a malicious URL is greatly diminished. Sending your username and password unencrypted over the internet is also not considered the best practice :-). As mentioned in RFC 3986, this technique can obscure the landing page from the user if utilized in a certain manner.
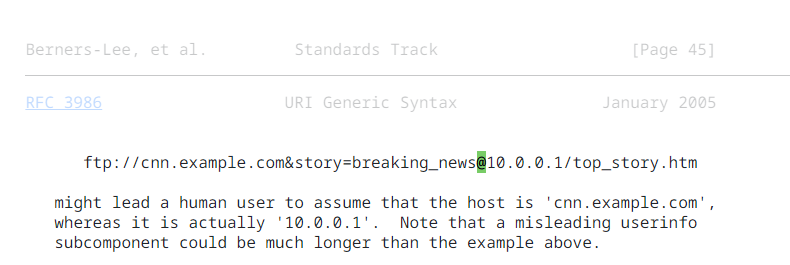
The URL will take user straight to 10.0.0.1 under a username of cnn.example.com&story=breaking_news for the ftp server to the /top_story.html path. This method can also be further refined by employing another technique, as highlighted in this article.
The / character, also known as the forward slash, plays a special role in defining path segments in a URL. If a URL contains a forward slash, all subsequent characters are considered part of the path segment. However, if the forward slash is replaced by a similar-looking character, everything before the @ is discarded. This is because browsers discourage this authentication method. Thus, an attacker’s goal is to use a character closely resembling the forward slash. This tactic ensures that everything before the @ is disregarded by the browser, directing the user to a potentially malicious domain after the @ character.
Let’s take an example from our most recent data and, for instance, let’s consider csgo.zip domain that showed up in our telemetry. We can modify it in a way that, while appearing legitimate, it leads the user straight to a malicious domain according to VirusTotal. The address segment before the @ character will be discarded.
Forward Slash (U+002F): https://www.steampowered.com/downloads/latest/@csgo[.]zip
We have replaced the forward slash with the Fullwidth Solidus. If we had used a normal forward slash, we would have ended up with an incorrectly formatted URL, which would not have worked as expected. The Fullwidth Solidus is predominantly used in East Asian languages as a date separator, or in situations where a fixed-width separator is necessary.
It is almost indistinguishable from forward slash. And with the help of current AI, we can generate quite a lot of visually similar Unicode characters effortlessly.
URL Variations Using Different Slash Characters:
- Forward Slash (U+002F):
https://www.steampowered.com/downloads/latest/@csgo[.]zip
- Fullwidth Solidus (U+FF0F):
https:⁄⁄www.steampowered.com⁄downloads⁄latest⁄@csgo[.]zip
- Division Slash (U+2215):
https:∕∕www.steampowered.com∕downloads∕latest∕@csgo[.]zip
- Fraction Slash (U+2044):
https:⁄⁄www.steampowered.com⁄downloads⁄latest⁄@csgo[.]zip
- Mathematical Slash (U+27CB):
https:⟋⟋www.steampowered.com⟋downloads⟋latest⟋@csgo[.]zip
All of these variants, with the exception of the forward slash, will direct us to csgo.zip. At the time of our research, the link found on the website leads to a benign zip file, which contains an image of a CS:GO player. However, since we don’t know who operates this domain, there’s no guarantee that the content will remain the same in the future.
To share some insights, we examined the three domains most frequently blocked by our systems to understand the dynamics of the threat. These domains, listed in alphabetical order, are 42.zip, attachments.zip, and download.zip. Each of them has a significantly high ‘score’ on VirusTotal, and all registrant information has been redacted. As can be seen in the graph below, the number of protected users skyrocketed at the beginning of June, only to fall sharply thereafter.
Another graph focused on the number of unique users and total submits daily paints the same picture.
What is the reasoning behind this? Even though the zip domains are appealing and certainly tempting for cybercriminals to use, they leave an audit trail and can be easily blocked. This is evident from the graph provided. It is definitely more elusive to take advantage of insecure webservers or outdated WordPress installations than to register a domain. This is also the reason why the number of blocked attacks was lower than I personally expected.
Last but not least, let’s put the threats posed by .zip domains into a broader context. I’ve aggregated the number of users protected under specific domains to evaluate the share of .zip compared to the rest. In short, the .zip domains didn’t make it to the list. The largest share blocked by our web shield belongs to .com, which is understandable given the high number of registered .com domains. However, when we examine the remainder, a few domains stand out.
As we can see, there is a certain discrepancy between the number of registered domains under certain TLDs (graph below) and the connections that we block under these TLDs every day (graph above). Threats are not evenly distributed among the TLDs. There are a few TLDs that I encounter almost daily that consistently raise some suspicion. These include .xyz, .online, .biz, .info, .ru, .life, .site, among others. While visiting these and many other domains, I would urge extra caution. However, this doesn’t mean that you are entirely safe when encountering a .com domain. It’s all part of a larger picture, and users need to be vigilant when opening emails or navigating through the vastness of the internet. To aid in this, we have prepared a list of points that should assist you.
What to do:
- Be wary of .zip TLDs: Treat any
.zipTop-Level Domains (TLDs) with caution, as they could potentially host malicious content.
- Monitor company traffic: Keep a close eye on your company’s web traffic, specifically looking out for any unusual activities related to
.zipTLDs.
- Consider introducing special email filters: To further protect against potential threats, consider implementing special filters for emails that contain
.zipTLDs in their content.
- Keep your antivirus software updated: Always ensure your antivirus software is up to date to maximize its effectiveness against the latest threats.
- Stay informed about new threats: Regularly read security bulletins and reports about emerging threats to stay ahead of potential dangers.




